- For your apps template (e.g.
ngp-v305-app-stage) and store the Lambda function for slack notifications.
- Your app repository must contain buildspec.yaml and ecs.sh files (please refer to ngp-nodejs app).
- You should generate GitHub Token with
admin:repo_hookandreposcopes to enable github changes to trigger this pipeline.
- Clone the repo
git clone https://github.com/microservices-today/ecs-cicd.git` cd ecs-cicd
- Export AWS credentials
export AWS_ACCESS_KEY_ID="accesskey" export AWS_SECRET_ACCESS_KEY="secretkey" export AWS_DEFAULT_REGION="ap-southeast-1"
- Run
bash bin/configure.sh
- Open the link at the end of the script to continue the installation.
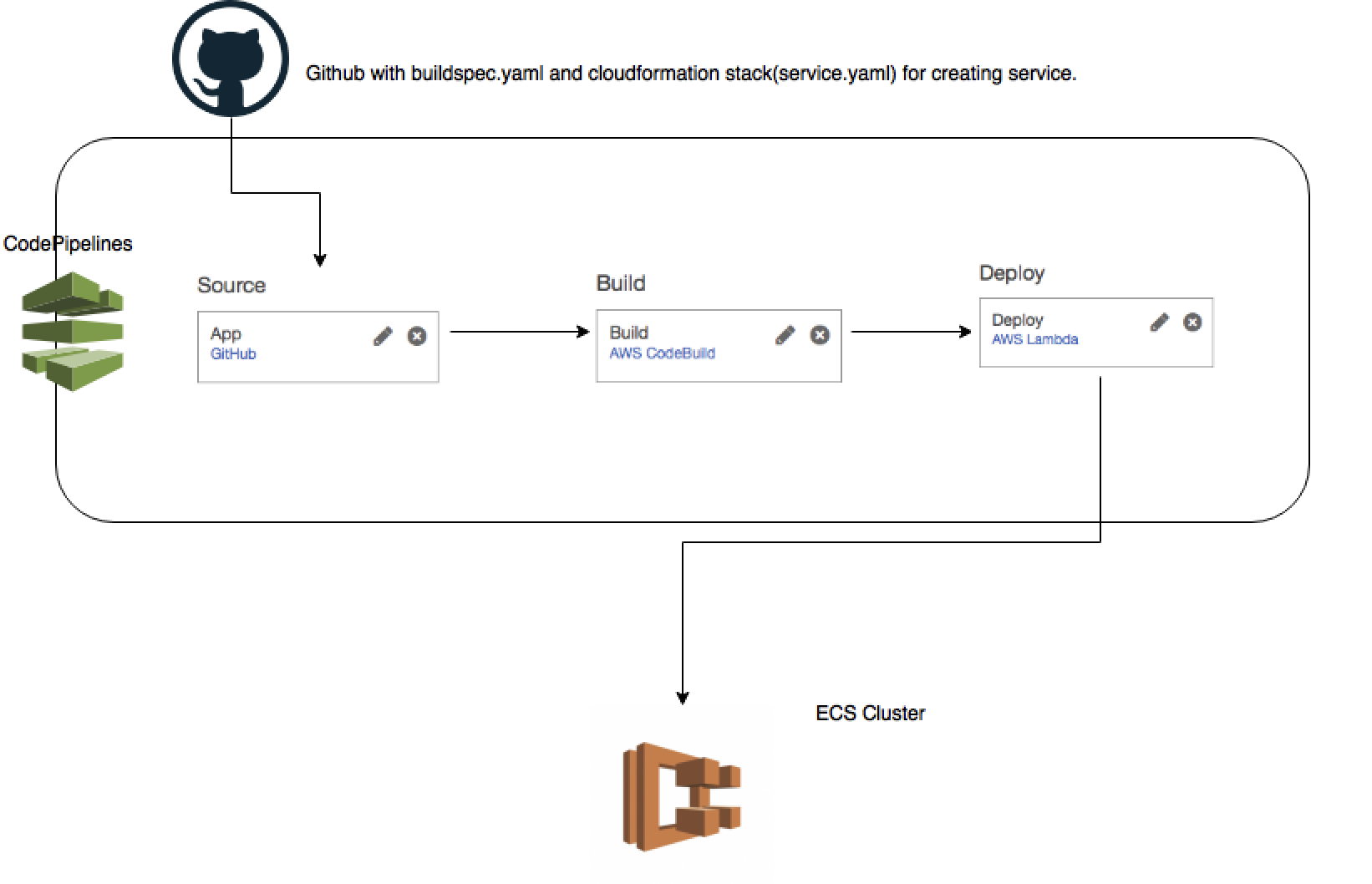
AWS CodePipeline uses GitHub repository as the source stage for your code.
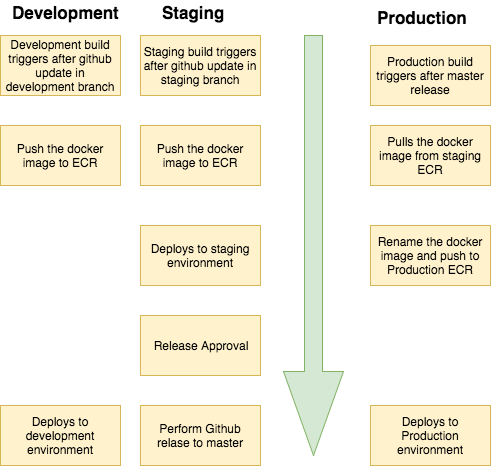
For Development and Staging CodePipeline, CodeBuild builds docker image from the source code and pushes it to ECR. For Production environment, CodeBuild pulls docker image from the Staging ECR and pushes it to Production ECR.
Also, CodeBuild updates the CloudFormation template (service.yaml) to deploy the ECS Service with environment specific information.
AWS CloudFormation creates/updates the CloudFormation stack to create/update the application Service in ECS.
aws ssm put-parameter --name /v305-Dev/XXX --value "XXX" --type SecureString
aws ssm put-parameter --name /v305-Dev/YYY --value "YYY" --type SecureString
aws ssm put-parameter --name /v305-Dev/ZZZ --value "ZZZ" --type SecureStringPlace your parameters keys (only keys, not actual secrets) in .env.sample
(please refer to ngp-nodejs app):
➜ ngp-nodejs git:(master) ✗ cat .env.sample
XXX=
ZZZ=
YYY=The ecs-cicd can be configured to run staging and production pipeline in different accounts.
Using this workflow, release can be triggered from the Staging pipeline and Production
pipeline with pull the ECR image from Staging AWS Account.