Decrypt Whatsapp crypt12 sqlite database files
-
AES GCM mode encryption using 128 bit block size and 16 bytes IV (nonce)
-
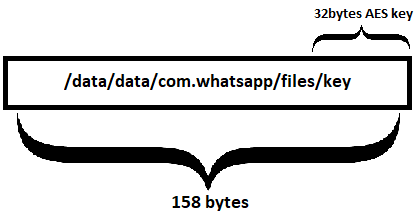
key file must be 158 byte long (only last 32bytes represent the key)
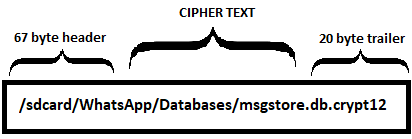
- crypt12 file includes 67 byte header and 20 byte trailer which needs to be removed
-
the resulted plain bytes need to be decompressed in order to obtain the final SQLite .db file
-
for more information you can check A Systems Approach to Cyber Security: Proceedings of the 2nd Singapore Cyber-Security R&D Conference (SG-CRC 2017)
- Ensure you have the key file (key) and crypt12 file (msgstore.db.crypt12) in the same directory with the go entrypoint. You can use the existing key and msgstore files in the repo for testing.
- Run using GO:
go run crypt12-decrypt
- Or run Windows executable:
crypt12-decrypt.exe
- Otherwise use the necessery arguments:
go run crypt12-decrypt.go -h
Usage of crypt12-decrypt.exe:
-crypt12file string
crypt12 file path (default "msgstore.db.crypt12")
-keyfile string
decryption key file path (default "key")
-outputfile string
decrypted output file path (default "msgstore.db")
go get github.com/CanciuCostin/crypt12-decrypt
go build crypt12-decrypt -> built with go version 1.14.4