Assess the security of your Active Directory with few or all privileges. This tool offers functionalities similar to PingCastle, ORADAD, or even PurpleKnight (with some bonuses).
ADcheck is developed in pure Python to bypass operating system constraints.
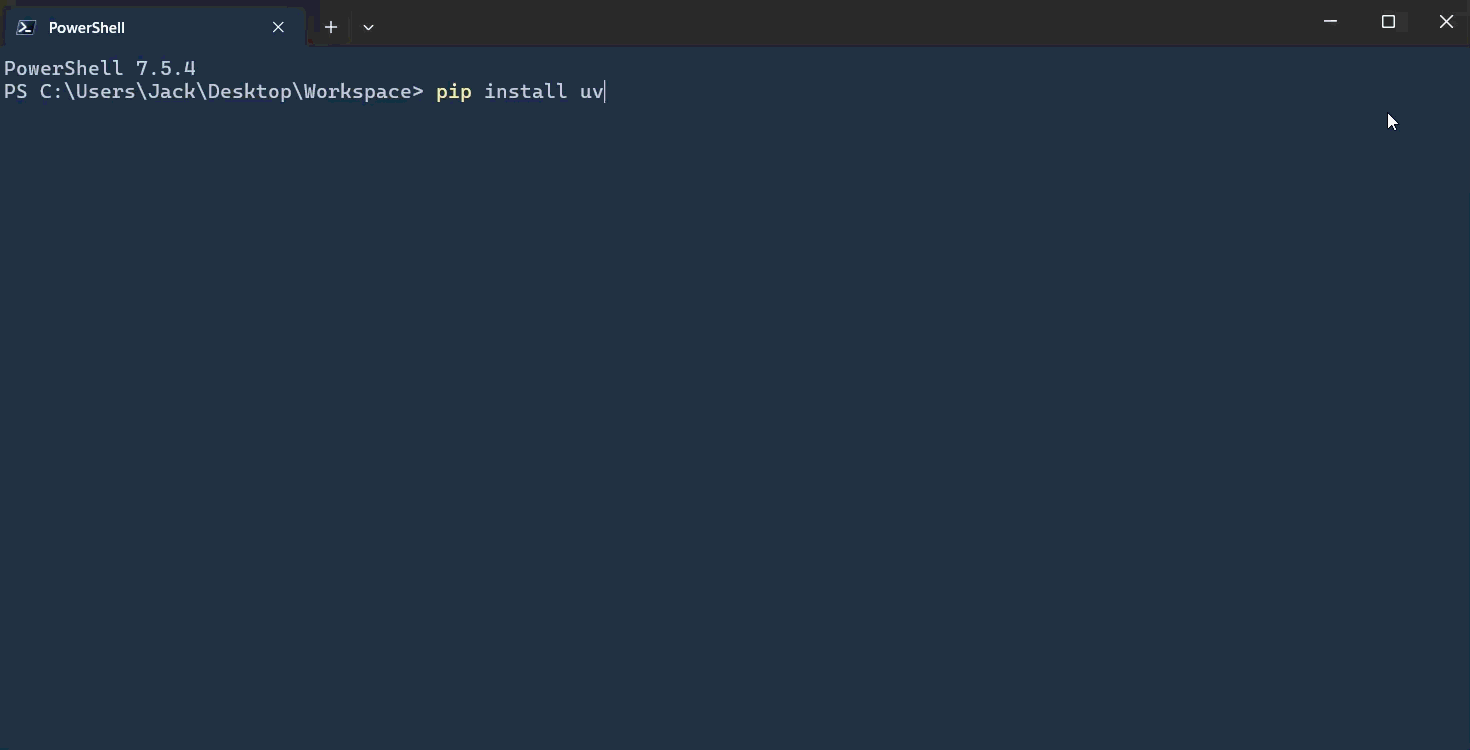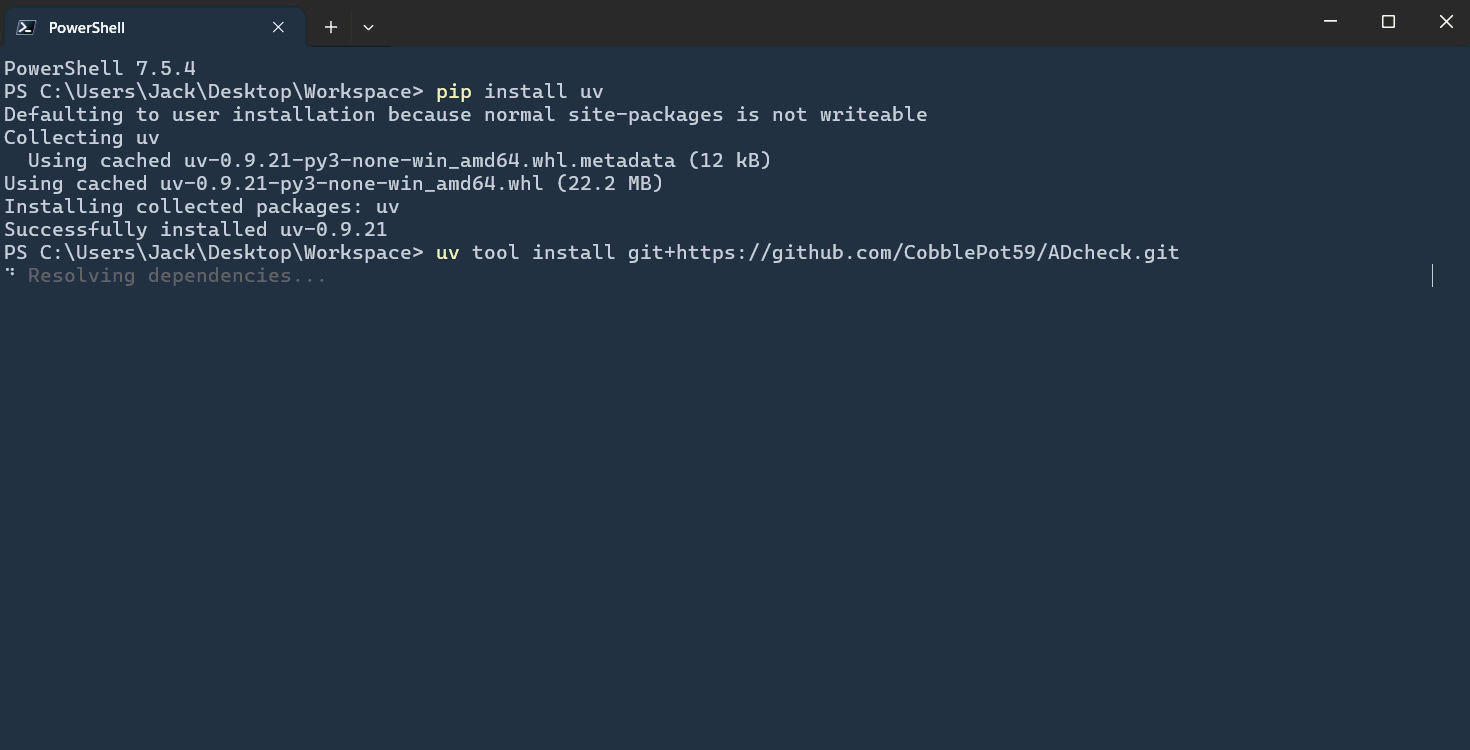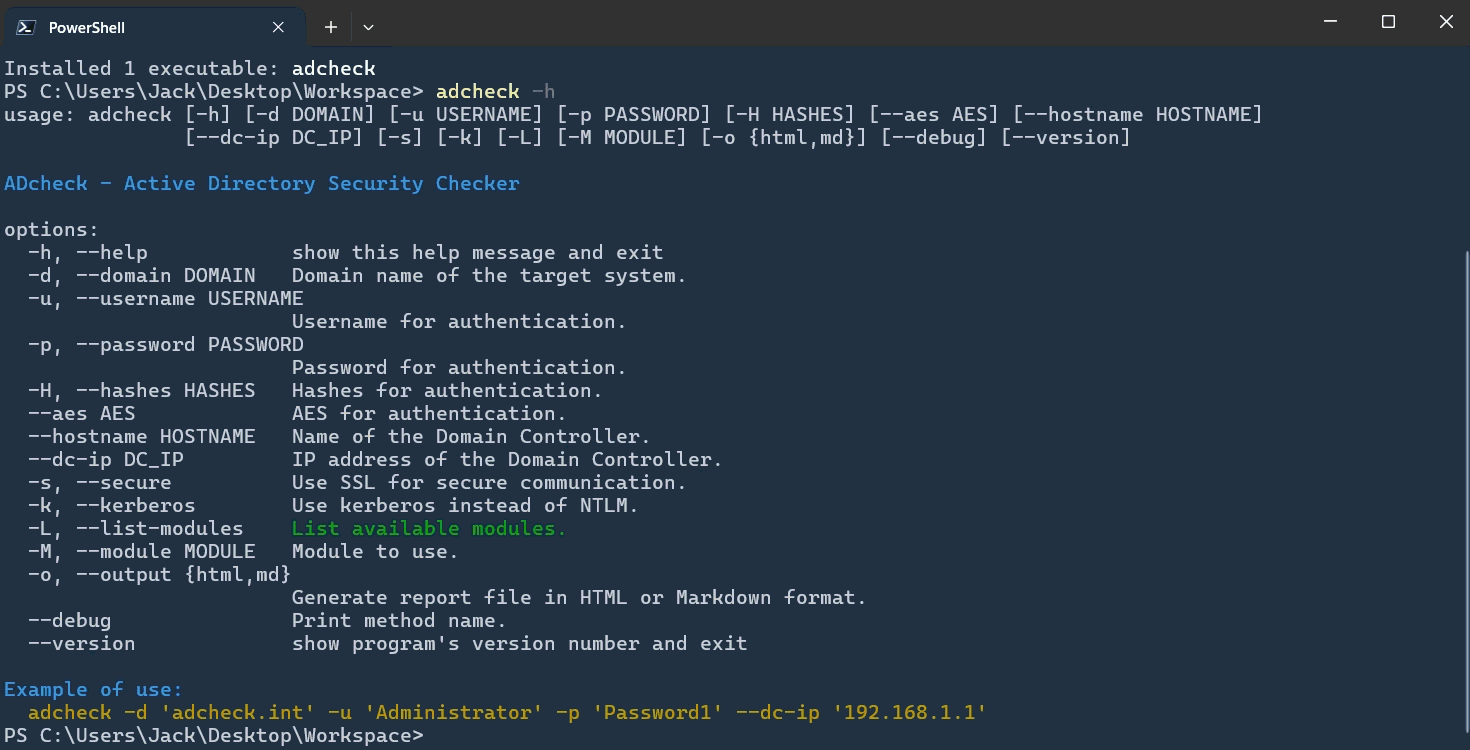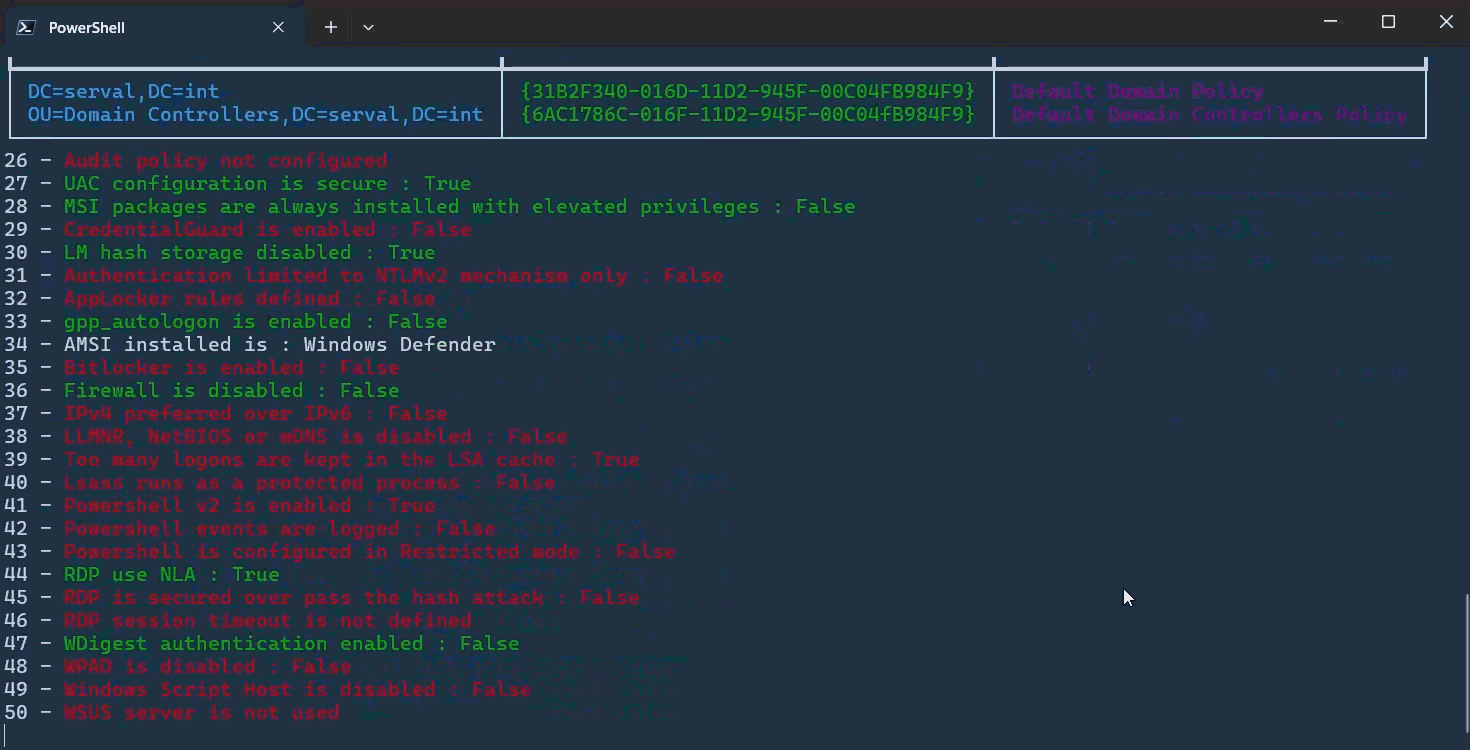
Although textual, a simple color scheme is used to navigate through the returned information (🔴 red for really bad, 🟢 green for okay, ⚪ white for purely informative). A sample report is available here.
Note
At present, this tool has 78 checks and more are to come (see the TODO).
The collected information includes :
-
User Account Management
- Admin accounts that can be delegated
- Admin accounts not in "Protected Users" group
- Accounts which can use DES authentication
- Accounts vulnerable to ASRepRoasting attack
- Accounts with
altSecurityIdentitiesattributes - Accounts with
userPasswordattributes - Accounts with
unixUserPasswordattributes - Accounts with
unicodePwdattributes - Accounts with
msDS-HostServiceAccountattribute - Accounts with blank password
- Accounts vulnerable to KerbeRoasting attack
- Locked accounts
- Number of accounts which have never expiring passwords
- Number of accounts with identical passwords
- Number of inactive accounts
- Number of accounts in "Schema Admins" group
- Accounts which have reversible passwords
- Accounts vulnerable to timeroasting attack
- Accounts that had admin rights in the past
- Accounts with password not required
- Name of Pre-Windows 2000 Compatible Access group members
- Get List of users in Privesc group
- Get Users with description
- Verify if The native administrator account has been used recently
- Get Group Managed Service Accounts
-
Audit and Policy Management
- Get Audit Policy
- Get Default password policy
- Get Group Policy Object by Organizational Unit
- Name of Group Policy containing a password
- Verify if Force logoff when logon hours expire
- Verify if MSI packages are always installed with elevated privileges
- Verify if CredentialGuard is enabled
- Verify if LM hash storage disabled
- Verify if Authentication limited to NTLMv2 mechanism only
- Verify if AppLocker rules defined
- Verify if gpp_autologon is enabled
- Verify if Bitlocker is enabled
- Verify if Firewall is disabled
- Verify if IPv4 preferred over IPv6
- Verify if LLMNR, NetBIOS or mDNS is enabled
- Verify if Too many logons are kept in the LSA cache
- Verify if Lsass runs as a protected process
- Verify if Powershell v2 is enabled
- Verify if Powershell events are logged
- Verify if Powershell is configured in Restricted mode
- Verify if RDP use NLA
- Verify if RDP is secured over pass the hash attack
- Verify if RDP session timeout is too short
- Verify if UAC configuration is secure
- Verify if WDigest authentication enabled
- Verify if WPAD is disabled
- Verify if Windows Script Host is disabled
- Verify if WSUS server is not used
- Get Name of AMSI installed
-
Computer and Domain Management
- Computers with bitlocker keys
- Get Domain Controllers
- Get Functional level of domain
- Get Kerberos config
- Verify if Non-admin users can add up to 10 computer(s) to a domain
- Get Supported Kerberos encryption algorithms
- Verify if Kerberos password last changed < 40 days
- Verify if LAPS is installed
- Get Password Settings Object
- Verify if Recycle Bin is enabled
- Verify if The computer was recently backed up
- Verify if The computer is up to date
- Get Supported encryption by Domain Controllers
- Verify if SMB signing is required
- Verify if Spooler service is enabled on remote target
- Verify if LDAP signature was required on target
-
Privilege and Trust Management
- Registry access rights
- Get Control delegations by container
- Get Privilege Rights (SeDebugPrivilege, SeBackupPrivilege, ...)
- Get Authentication policy silos
- Name of Trust accounts for the delegation
- Name of Computers with rbac
- Verify if User can create dns record
- Computers with constrained delegation
- Get Group policy folder/file rights
Warning
Currently, this tool is more geared towards penetration testers than auditors. If you intend to use it on Windows, it's necessary to exclude the project from the antivirus or Endpoint Detection and Response solution, as it utilizes Impacket, which is detected by these systems.
- Install the python pipx package manager :
python -m pip install pipx
- Add it to the PATH :
pipx ensurepath
- Install ADcheck project :
pipx install git+https://github.com/CobblePot59/ADcheck.git
- Run ADcheck, specifying the necessary parameters :
ADcheck -d 'adcheck.int' -u 'Administrator' -p 'Password1' --dc-ip '192.168.1.1'
- Download ADcheck project :
git clone https://github.com/CobblePot59/ADcheck.git
- Go to ADcheck project :
cd ADcheck
- Install poetry the python dependency manager :
python -m pip install poetry
- Install ADcheck project dependencies :
poetry install
- Run ADcheck, specifying the necessary parameters :
poetry run adcheck -d 'adcheck.int' -u 'Administrator' -p 'Password1' --dc-ip '192.168.1.1'
- Trusts
- Azure (Entra ID)
- Trusted Root Certification Authorities status
- Persistent attack trace (mimikatz, pywhisker, ticket, dsrm, acl)
- Ldap anonymous bind
- List of Named pipes
- DFSR SYSVOL
- WinRM authorization