A hacking challenge for use in an escape room for programmers
The src/ folder contains a hacking challenge (with its own README). It is intended to be one of many puzzles in an escape room.
Solving the challenge doesn't require much coding - It's more about reading the README and solving the puzzle by modifying the provided code.
An internet connection is not needed to solve this puzzle.
If you're looking to give this challenge to someone, follow these instructions to set it up.
- Copy the
src/folder to the desktop. Open a terminal in that folder. - In the copied
src/folder, add a file calledsecret.txt. - In
secret.txt, write your next clue (eg. The vault's passcode is 8369). - Generate a password-encrypted zip archive containing the secret.txt file:
zip -e secret.zip secret.txt.- This will ask you to enter a password. Make that password a combination of 5 of the bolded words in the
README(eg.spiffy1979spencerhemmingwooddoctor). - You can verify it works with
unzip secret.zipand entering the password.
- This will ask you to enter a password. Make that password a combination of 5 of the bolded words in the
- Delete
secret.txt:rm secret.txt. - Open the
src/folder in an editor (eg. VS Code) and leave it open on theREADMEfile. - Open a terminal and run
python3 decryptzip.py. Example setup: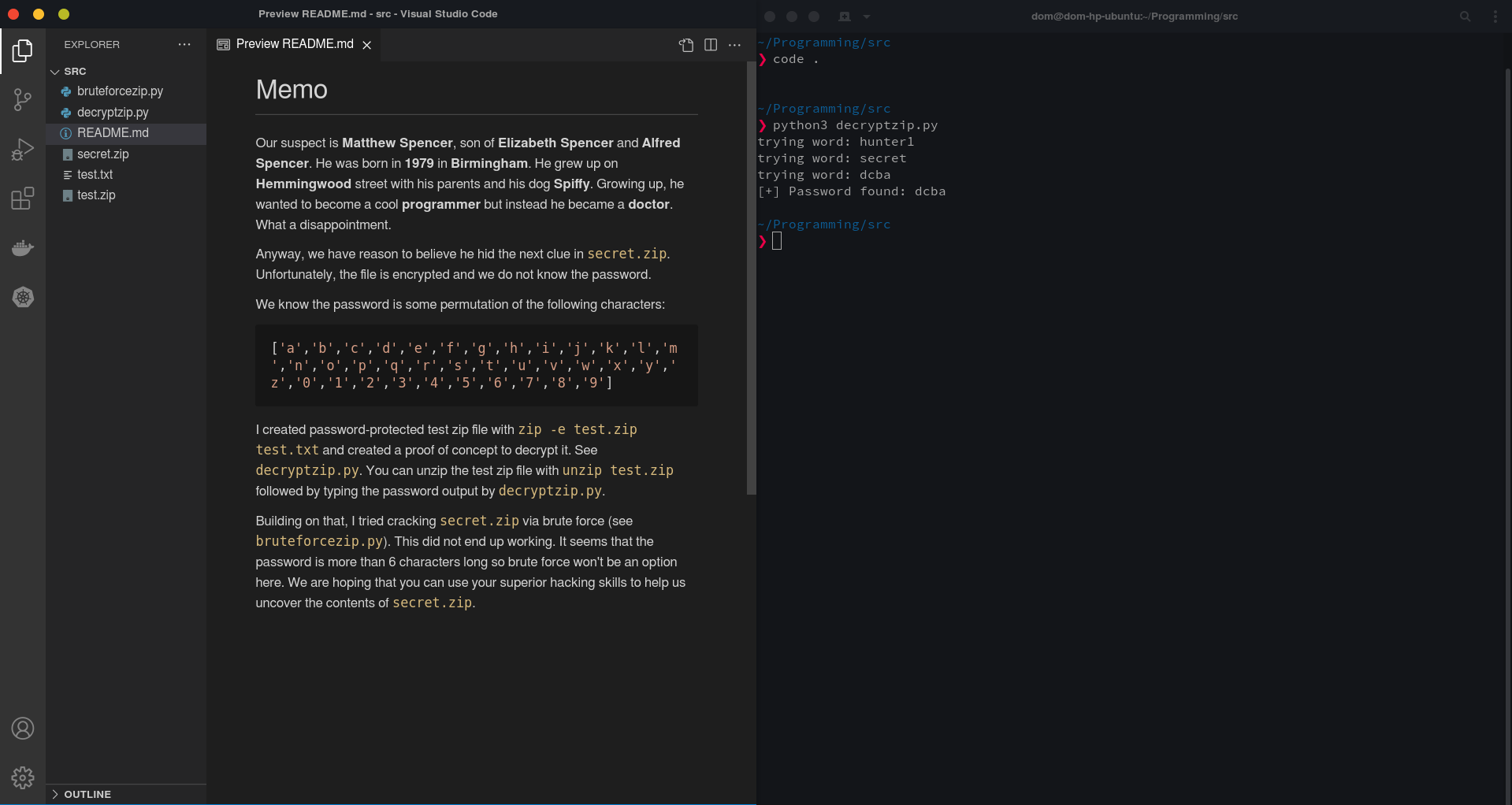
This project is licensed under the MIT License - see the LICENSE file for details.