[YouTube - Get-UnJlaive - Jlaive Protector Reconstructor]
Get-UnJlaive is tool which is able to reconstruct Jlaive (.NET Antivirus Evasion Tool (Exe2Bat)) to original Assembly and stub Assembly.
It should defeat even the obfuscated form.
Jlaive - https://github.com/ch2sh/Jlaive
Author: Dump-GUY (@vinopaljiri)
Get-UnJlaive is tool which is able to reconstruct Jlaive (.NET Antivirus Evasion Tool (Exe2Bat)) to original Assembly and stub Assembly.
Jlaive is an antivirus evasion tool that can convert .NET assemblies into undetectable batch files https://github.com/ch2sh/Jlaive.
Get-UnJlaive PS module uses dnlib to parse assembly and .NET reflection to load dnlib.
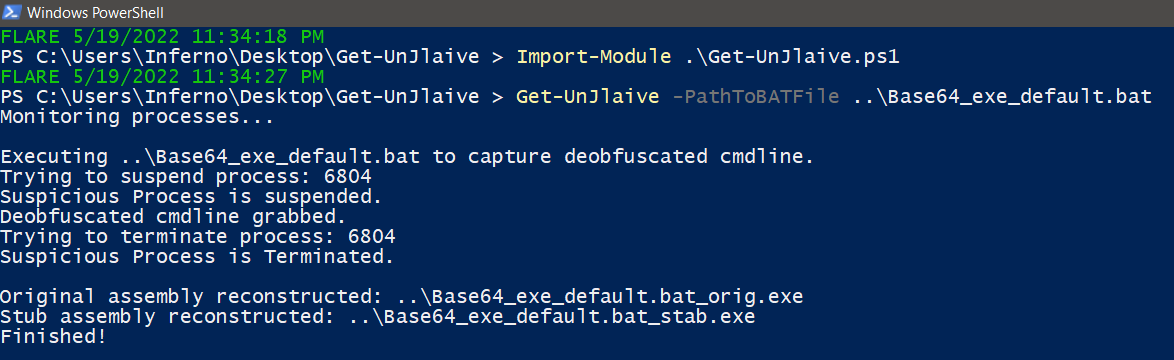
Jlaive protected .bat file is executed and immediately suspended-terminated to grab deobfuscated form of cmdline -
when obfuscation was used
Run ONLY in your VM - malicious code should not be executated but for sure
If you want to run .bat file as elevated process run this module elevated
Tested version Jlaive v0.2.3
Mandatory parameter.
Specifies the .bat file protected by Jlaive.
PS> Import-Module .\Get-UnJlaive.ps1
PS> Get-UnJlaive -PathToBATFile ..\malicious.bat
PS> Get-UnJlaive -PathToBATFile "C:\Users\XXX\Desktop\malicious.bat"
https://github.com/Dump-GUY/Get-UnJlaive
https://github.com/ch2sh/Jlaive