Supports service listen in both host and bridge network modes, and includes an automatic network capture utility specifically designed for DNS traffic ,and extends go nmap to implement an efficient port scanner, supporting the following automatic scanning methods: UDP, TCP full connection, ICMP, FIN, ACK, SYN half-open, NULL, IP protocol layer, and feature-based scanning.
- micro container network listen
- micro dns packet capture
- micro nmap port detection
To use pretool, download the appropriate binary for your architecture:
- pretool_amd64
- pretool_arm64
Specifically designed for safe process scanning, that is, to retrieve information about non-system processes (PID greater than 1024 and without square brackets in the name), use the -c flag:
./pretool_amd64 -c
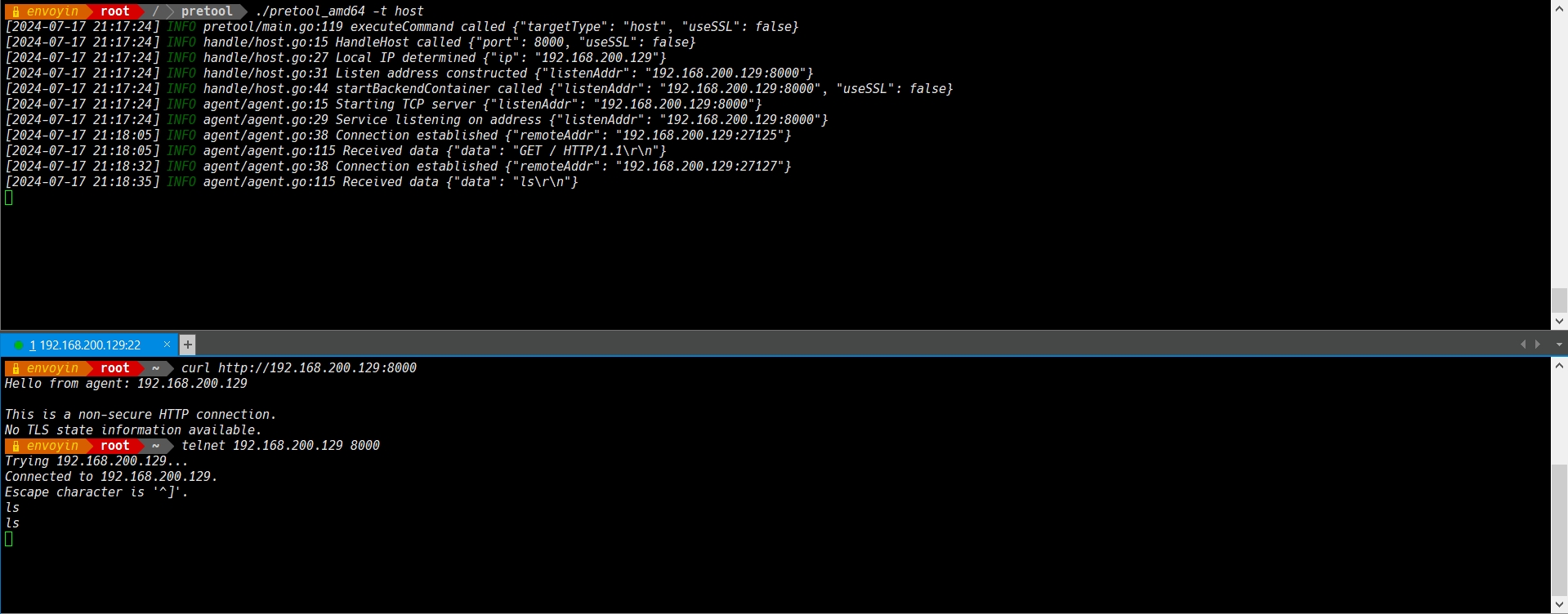
To listen services in a specific network mode (host or bridge) and customize the port number:
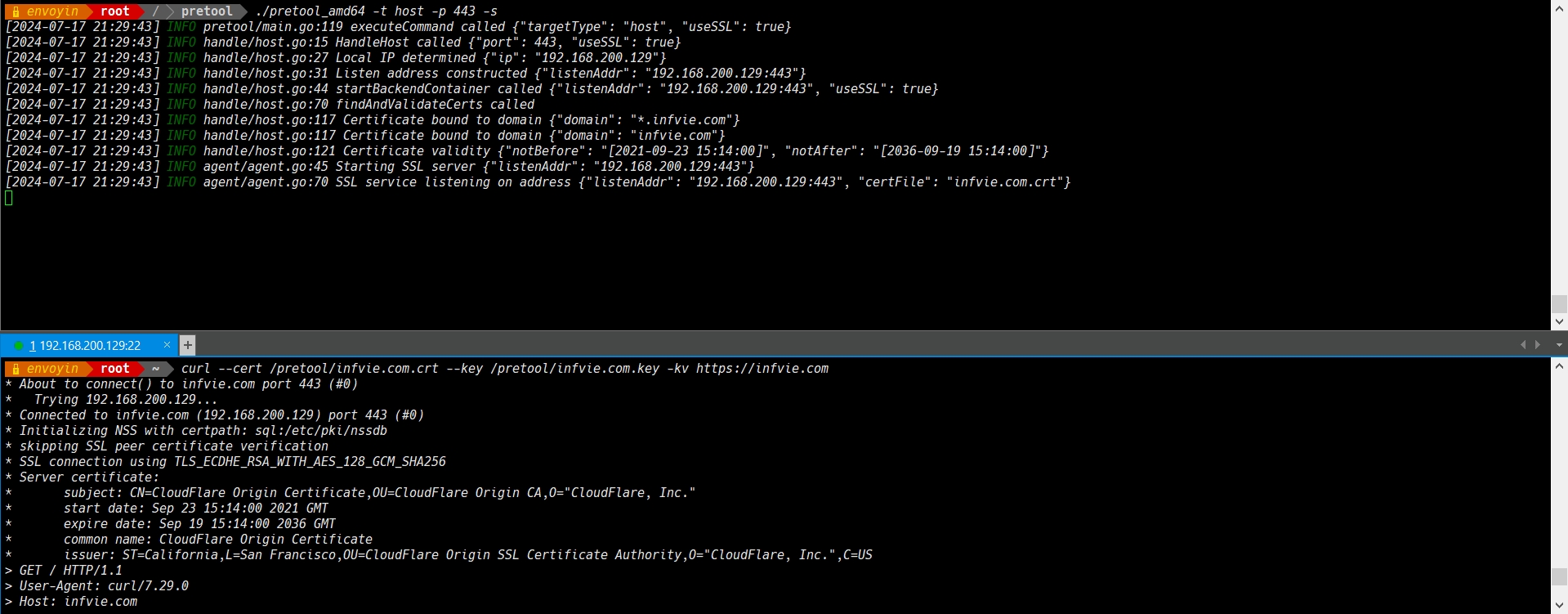
SSL/TLS can be enabled for the server only in host network mode. The certificate files must have .crt and .key extensions (e.g., domain.crt and domain.key).
./pretool_amd64 -t host -p 443 -s
Specify host mode with the default port 8000:
./pretool_amd64 -t host
Or, specify a custom port number (e.g., 9000):
./pretool_amd64 -t host -p 9000
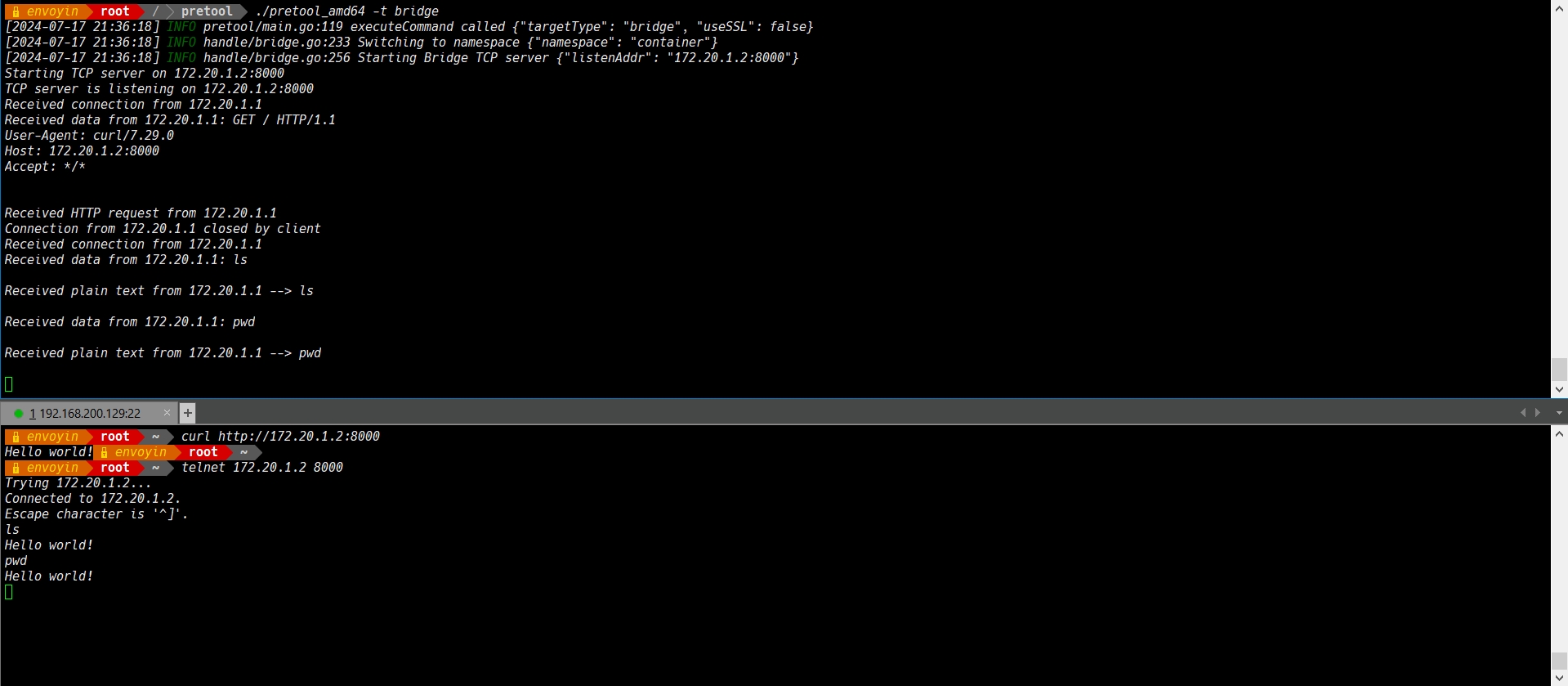
Specify bridge mode with the default port 8000:
./pretool_arm64 -t bridge
Or, specify a custom port number (e.g., 9000):
./pretool_arm64 -t bridge -p 9000
To capture DNS packets, specify the domain name:
./pretool_arm64 -d www.infvie.com
Extends go nmap to implement an efficient port scanner, supporting the following automatic scanning methods: UDP, TCP full connection, ICMP, FIN, ACK, SYN half-open, NULL, IP protocol layer, and feature-based scanning.
# pretool_amd64 -n <target_ip> <21-25,80> <tcp,udp> <threads> (default threads is 10000)
./pretool_amd64 -n 192.168.200.129 21-25,80 tcp,udp
-c, --check Get information on non-system processes.
-t, --type Specify the network mode (host or bridge).
-p, --port Specify the port number (default is 8000).
-s, --ssl Enable SSL/TLS for the server.
-d, --domain Specify domain for tcpdump filter.
-n, --nmap Enable an efficient port scanner, [-n <target_ip> <21-25,80> <tcp,udp> <threads>].
-v, --version Print the version number and MD5 hash of the tool.
-h, --help Show the help message and usage information.
ip link delete veth-host;
ip link set br0 down;
ip link delete br0;
ip netns delete container;
umount /var/run/netns;
rm -rf /var/run/netns;
ip addr show br0;
ip addr show veth-host;
ip netns list;
ip netns exec container ip a show;
ip netns exec container ss -tuln;
- System Processes: By default, system processes with PIDs less than 1024 and those containing square brackets in their names (e.g., [watchdog]) are filtered out.
- Customization: You can customize the tool's behavior by specifying the target type (host or bridge) and port number according to your requirements.
- Go Nmap: To implement an efficient port scanner, supporting the following automatic scanning methods: UDP, TCP full connection, ICMP, FIN, ACK, SYN half-open, NULL, IP protocol layer, and feature-based scanning.