A way to get fake followers on Clubhouse
Clubhouse is aware of this issue.
I noticed that Clubhouse removed duplicates from all users with a one-time deduplication script. They haven't fixed the core problem so it's still reproducible(as of Feb 2021). This will probably be permanently fixed in a short while.
Clubhouse apparently does not check existing followers of a user when you send a new follow request. You can verify this behaviour by following the same user multiple times by using the different "Follow" buttons in the app.
When someone follows you, first press this:

So... we can just send the same follow request 1000 times and we will have 1000 followers. We just need to get that follow request.
mitmproxy can be used to listen to app traffic and replay requests. This works even for HTTPS requests by using mitmproxy's own certificate authority and trusting it on the mobile device.
However, Clubhouse is using ssl pinning so the approach above does not work. We have to disable ssl pinning first.
The easiest solution at this point is
- getting the Clubhouse IPA
- patching it with Objection
- signing the patched app with a development certificate
- installing the patched app to your phone
This approach is described in detail here: https://github.com/sensepost/objection/wiki/Running-Patched-iOS-Applications
That also does not work for Clubhouse because Clubhouse has an encrypted IPA which makes patching impossible without the encryption key.
At this point, only solution is jailbreaking the phone and hooking into Clubhouse app's runtime with Frida. Then, we can easily disable ssl pinning and extract the follow request with mitmproxy.
We won't need the follow request itself though, it's already built with send_follow_request function. We will just need to extract the auth token, it's not included on the repo.
- An iphone to be sacrificed for the cause - you will jailbreak it
- A computer that accepts incoming connections - no firewall
-
Have your computer and iphone ready. They should be in the same network.
-
First set up the proxy. Install mitmproxy and run it. It runs a proxy server on 8080.
-
Configure your iphone to connect to Wi-Fi over a proxy. Use your computer's local IP and 8080 port.
-
Install mitmproxy's CA certificate as described here: https://docs.mitmproxy.org/stable/concepts-certificates/#quick-setup
-
Test a few HTTPS urls and apps. mitmproxy window in your computer should be showing you the requests made by those websites and apps.
-
At this point, everything works except apps with ssl pinning. We need to jailbreak the phone. I used checkra1n for this purpose.
-
Download Cydia to the jailbroken iphone and then frida-server
-
Install the dependencies to the computer. This will make it possible to run the commands below.
pip install -r requirements.txt -
Get the app identifier
frida-ps -Uia | grep Clubhouse -
Run the app with objection
objection --gadget "co.alphaexploration.clubhouse" explore -
Disable pinning from the objection terminal
ios sslpinning disable -
We're set! Follow a person from the app. mitmproxy should be showing an HTTPS request.

-
At this point, you have what you need. Try pressing "r" after selecting the follow request. It should be replayed with an 200 response. You can verify the follower count increase by replaying multiple times.
-
Export the request as curl to a file. Pressing "e" lets you export a request in mitmproxy.
-
Copy config.json.template to
config.json -
From the curl request, copy these parameters below into
config.jsonat appropriate places.# This allows us to act as a user # You should fill both default_auth_token and auth_token fields with $AUTH_TOKEN -H 'Authorization: Token $AUTH_TOKEN' # User that is being followed '{"source_topic_id":null,"user_ids":null,"user_id":$TARGET_USER_ID,"source":6}' # The parameters below may not be needed, but I included them for consistency # User that performs the follow operation # Fill user_id field under users array with this -H 'CH-UserID: $USER_ID' # Fill cfduid field with this Cookie: __cfduid=$CFDUID # Fill device_id field with this -H 'CH-DeviceId: $DEVICE_ID -
Run the script
python main.pyYou should observe your follower count to increase.
-
Check the logs in detail:
tail -f history.log
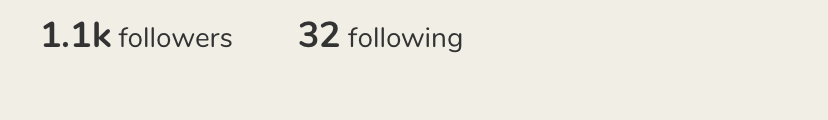 They are not shown except the number in the profile screen. You won't see duplicates of a user when you go into Followers.
They are not shown except the number in the profile screen. You won't see duplicates of a user when you go into Followers.
Clubhouse has a per-user rate limit for follow requests. It's 300 per each x hour, but I haven't figured out x yet. The script stops after hitting the rate limit.
If you hit another rate limit, you can change follow_interval in config.json.
This script supports running for multiple users in parallel. (Not following multiple users with a single user, but following a single user with multiple users) Just add each user as a separate item in "users" array inside config.json.
In case CH app changes the format of the request, you can update the request logic. After extracting the request from mitmproxy, convert it to python requests format:
uncurl.parse("curl -H 'Accept: application/json' ...")
Update the request builder code under request.py accordingly.