Jiwen Yu1, Xuanyu Zhang1, Youmin Xu1, 2, Jian Zhang1
1 Peking University, 2 PCL
- News (2024-06-12): 🎉🎉🎉 Our Stego260 has been released here. The image-prompt pair can be downloaded here.
- News (2023-09-28): 🎉🎉🎉 Our code has been released!
- News (2023-09-22): 🎉🎉🎉 Congratulations on CRoSS being accepted by NeurIPS 2023! Our open-source project is making progress, stay tuned for updates!
Try the command:
pip install -r requirements.txtpython demo.py --image_path ./asserts/1.png --private_key "Effiel tower" --public_key "a tree" --save_path ./output --num_steps 50Feel free to try it on your own images and keys. More sampling steps usually lead to better results.
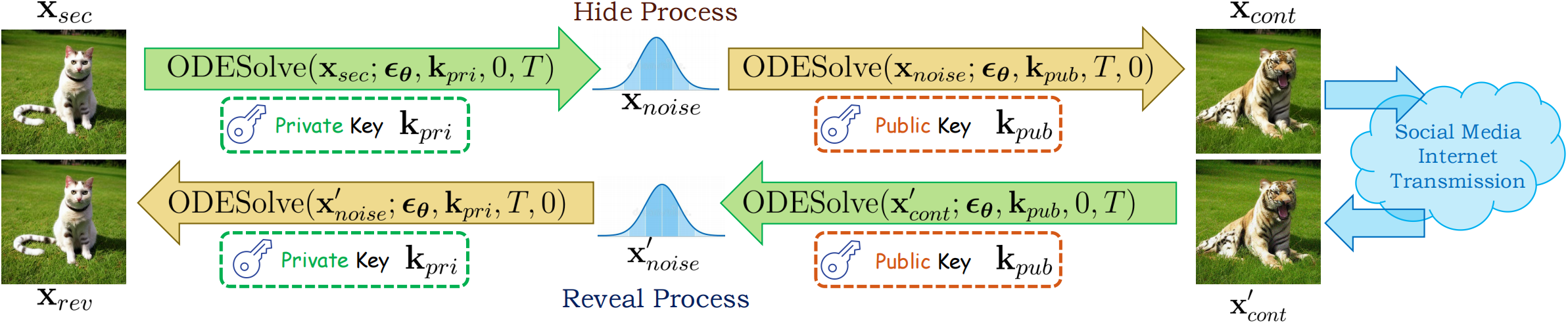
Inspired by recent developments in diffusion models, we propose a novel image steganography framework named Controllable, Robust, and Secure Image Steganography (CRoSS). This framework offers significant advantages in controllability over container images, robustness against complex degradation during transmission of container images, and enhanced security compared to cover-based image steganography methods. Importantly, these benefits are achieved without requiring additional training.
Following are visual comparisons of our CRoSS and other methods under two real-world degradations, namely WeChat and Shoot. Obviously, our method can reconstruct the content of secret images, while other methods exhibit significant color distortion or have completely failed.
Details and more results can be found in our paper.
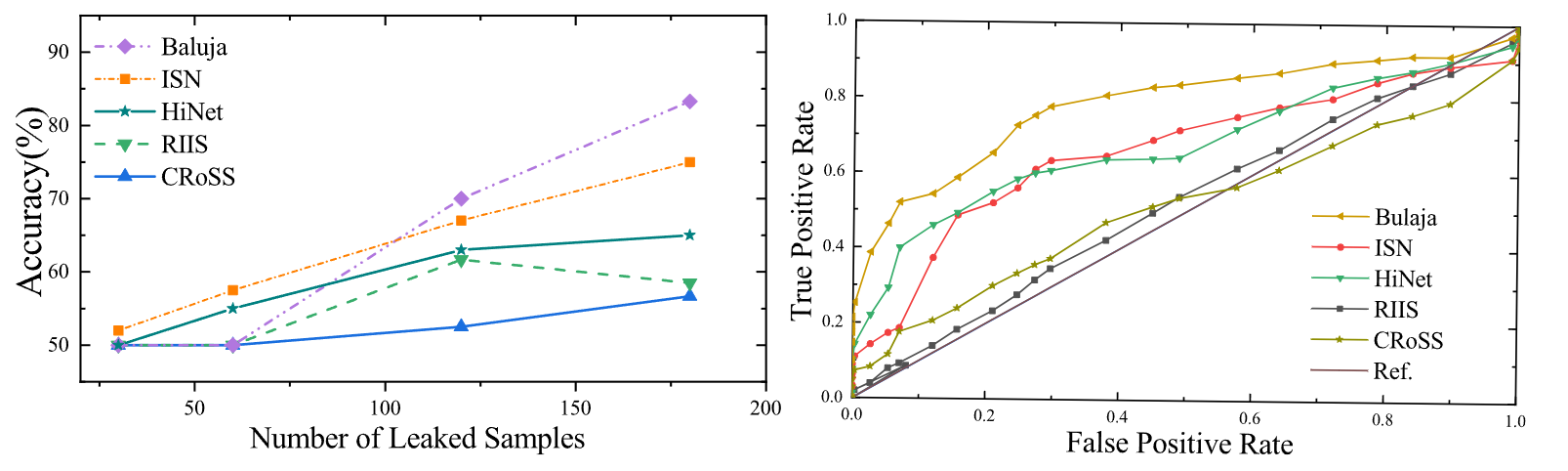
Following are deep steganalysis results by the latest SID. As the number of leaked samples increases, methods whose detection accuracy curves grow more slowly and approach
Details and more results can be found in our paper.
If this work is helpful for your research, please consider citing the following BibTeX entry.
@article{yu2023cross,
title={CRoSS: Diffusion Model Makes Controllable, Robust and Secure Image Steganography},
author={Yu, Jiwen and Zhang, Xuanyu and Xu, Youmin and Zhang, Jian},
journal={Advances in Neural Information Processing Systems (NeurIPS)},
year={2023}
}