##Contents
- Overview
- Architecture Diagram and Components
- Guidance and Recommendations
- NCSC Security Matrix Compliance
- Deployment Guide
- Deployment and Configuration Activities
- UK Governments Private Network Connectivity
- Cost
- Further reading
This article provides guidance and automation scripts to deliver a Microsoft Azure three-tier web based architecture appropriate for handling many workloads classified as OFFICIAL in the United Kingdom.
Using an Infrastructure as Code approach, the set of Azure Resource Manager (ARM) templates deploy an environment that aligns to the National Cyber Security Centre (NCSC) Cloud Security Principles and the Center for Internet Security (CIS) Critical Security Controls.
The NCSC recommend their Cloud Security Principles be used by customers to evaluate the security properties of the service, and to help understand the division of responsibility between the customer and supplier. We’ve provided information against each of these principles to help you understand the split of responsibilities.
This architecture and corresponding ARM templates are underpinned by the Microsoft whitepaper Azure Blueprint for the UK Government. This paper catalogue how Azure services align with the fourteen cloud security principles set forth in the CESG/NCSC publication Implementing the Cloud Security Principles" thereby enabling organisations to fast-track their ability to meet their compliance obligations using cloud-based services globally and in the UK on the Microsoft Azure cloud.
This template deploys the infrastructure for the workload. Application code and supporting business tier and data tier software must be installed and configured.
If you do not have an Azure subscription then you can sign up quickly and easily, Get Started with Azure.
The Azure templates deliver a three-tier web application architecture in an Azure cloud environment that supports UK-OFFICIAL workloads. The architecture delivers a secure hybrid environment that extends an on-premises network to Azure allowing web based workloads to be accessed securely by corporate users or from the internet.
The components of this architecture include -
-
On-premises network. A private local-area network implemented in an organization.
-
Production VNet. The Production VNet (Virtual Network) hosts the application and other operational resources running in Azure. Each VNet may contain several subnets which are used for isolating and managing network traffic.
-
Web tier. Handles incoming HTTP requests. Responses are returned through this tier.
-
Business tier: Implements business processes and other functional logic for the system.
-
Database tier: Provides persistent data storage, using SQL Server Always On Availability Groups for high availability. Customers may wish to consider using Azure SQL Database as a PaaS alternative
-
Gateway: The VPN Gateway provides connectivity between the routers in the on-premises network and the Production VNet.
-
Internet Gateway and Public IP Address: The internet gateway exposes application services to users through the internet. Traffic accessing these services is secured using an Application Gateway offering Layer 7 routing and load balancing capabilities with web application firewall (WAF) protection.
-
Management VNet: This VNet contains resources that implement management and monitoring capabilities for the workloads running in the Production VNet.
-
Jumpbox. Also, called a bastion host. A secure VM on the network that administrators use to connect to VMs in the Production VNet. The jumpbox has an NSG that allows remote traffic only from public IP addresses on a safe list. The NSG should permit remote desktop (RDP) traffic. Management of production resources is via RDP using a secured Jumpbox VM.
-
User defined routes (UDR). User defined routes are used to define the flow of IP traffic within Azure VNets.
-
Network Peered VNETs: The Production and Management VNets are connected using VNet Peering. They are still managed as separate resources, but appear as one for all connectivity purposes with virtual machines in these networks able to communicate with each other directly by using private IP addresses. VNet peering is subject to the VNets being in the same Azure Region
-
Network Security Groups: NSGs contain Access Control Lists that allow or Deny traffic within a VNet. NSGs can be used to secure traffic at a subnet or individual VM level.
-
Active Directory Domain Services (AD DS): This architecture provides a dedicated Active Directory Active Directory Domain Services deployment.
-
Logging and Audit: Azure Activity Log captures operations taken on the resources in your subscription such as who initiated the operation, when the operation occurred, the status of the operation and the values of other properties that might help you research the operation. Azure Activity Log is an Azure platform service that captures all actions on a subscription. Logs can be archived or exported if requried.
-
Network Monitoring and Alerting Azure Network Watcher is a platform service provides network packet capture, flow logging, topology tools and diagnostics for network traffics within your VNets.
High Availability: Server workloads are grouped in a Availability Set to ensure high availability of virtual machines in Azure. This configuration ensures that during a planned or unplanned maintenance event at least one virtual machine will be available and meet the 99.95% Azure SLA.
Monitoring: Azure Monitor is the platform service that provides a single source for monitoring the activity log, metrics, and diagnostic logs of all your Azure resources. Azure Monitor can be configured to visualize, query, route, archive, and act on the metrics and logs coming from resources in Azure. It is recommended that Resource Based Access Control is used to secure the audit trail to ensure that users don’t have the ability to modify the logs.
Activity Logs: Configure Azure Activity Logs to provide insight into the operations that were performed on resources in your subscription.
Diagnostic Logs: Diagnostic Logs are all logs emitted by a resource. These logs could include Windows event system logs, blob, table, and queue logs.
Firewall Logs: Application Gateway provides full diagnostics and access logs. Firewall logs are available for application gateway resources that have WAF enabled.
Log Archiving: Logs storage can be configured to write to a centralised Azure storage account for archival and a defined retention period. Logs can be processed using Azure Log Analytics or by third party SIEM systems
Active Directory Domain Services: This architecture delivers an Active Directory Domain Services deployment in Azure w For specific recommendations on implementing Active Directory in Azure, see the following articles -
Extending Active Directory Domain Services (AD DS) to Azure.
Guidelines for Deploying Windows Server Active Directory on Azure Virtual Machines.
Active Directory Integration: As an alternative to a dedicated AD DS architecture, customers may wish to use Azure Active Directory integration or Active Directory in Azure joined to an on-premises forest.
Management Security: This pattern allows administrators to connect to the management VNET and Jumpbox using RDP from a trusted source. Network traffic for the management VNET is controlled using NSGs to restrict access port 3389 to only traffic from a trusted IP range access to the subnet containing the Jumpbox.
Customers may also consider using an enhanced security administrative model to secure the environment when connecting to the Management VNET and Jumpbox. It is suggested that for enhanced security customers use a Privileged Access Workstation and RDGateway configuration. The use of Network Virtual Appliances and public/private DMZs will offer further security enhancements.
Securing the network: Network Security Groups (NSG) are recommended for each subnet to provide a second level of protection against inbound traffic bypassing an incorrectly configured or disabled gateway. Example - ARM Template for deploying an NSG.
Securing public endpoints: The internet gateway exposes application services to users through the internet. Traffic accessing these services is secured using an Application Gateway which provides a Web Application Firewall and HTTPS protocol management
IP Ranges: The IP ranges in the architecture are suggested ranges, customers are advised to consider their own environment and use appropriate ranges.
Hybrid connectivity: The cloud based workloads are connected to the on-premises datacentre through IPSEC VPN using the Azure VPN Gateway. Customers should ensure that they are using an appropriate VPN Gateway to connect to Azure. Example VPN Gateway ARM Template. Customers running large-scale, mission critical workloads with big data requirements may wish to consider a hybrid network architecture using ExpressRoute to ensure private network connectivity to Microsoft cloud services
Separation of concerns: This pattern separates the VNets for Management operations and business operations. Separate VNets and subnets allow traffic management and traffic ingress and egress restriction using NSGs between network segments following Microsoft cloud services and network security best practices.
Resource Management: Azure resources such as VMs, VNets, and load balancers are managed by grouping them together into Azure Resource Groups. Resource Based Access Control roles can then be assigned to each resource group to restrict access to only authorized users.
Access control restrictions: Use Role-Based Access Control (RBAC) to manage the resources in your application using custom roles
Internet Access: This pattern has utilised Azure Application Gateway as the internet facing gateway and load balancer. Some customers may also consider the use of third party vendor Network Virtual Appliances for additional layers of networking security as an alternative to the Azure Application Gateway.
Azure Security Center: The Azure Security Center provides a central view of the security status of resources in the subscriptions, and provides recommendations that help prevent compromised resources. It can enable more granular policies (for example, applying policies to specific resource groups that allow the enterprise to tailor their posture to the risk they are addressing). It is recommended that customers enable Azure Security Center in their Azure Subscription.
RBAC can be used to restrict the operations that DevOps can perform on each tier. When granting permissions, use the principle of least privilege. Log all administrative operations and perform regular audits to ensure any configuration changes were planned.
This UK-OFFICIAL Azure template aligns to the 14 cloud security principles are documented in the (NCSC) Cloud Security Principles paper to ensure an environment that supports workloads classified as UK-OFFICIAL.
The following matrix provides a high level alignment of the 14 cloud security principles the Microsoft Azure security model, a detailed mapping of the 14 principles can be found in Microsoft's Azure Blueprint for the UK Government whitepaper.
Data in transit protection: Consumer data transiting networks should be adequately protected against tampering and eavesdropping via a combination of network protection and encryption.
Azure uses the industry-standard Transport Layer Security (TLS) 1.2 protocol with 2048-bit RSA/SHA256 encryption keys to encrypt communication internally and between customers and the cloud.
Asset protection and resilience: Consumer data, and the assets that store or process it, should be protected against physical tampering, loss, damage, and seizure.
Most Azure services are deployed regionally, and customers can configure certain Azure services to store customer data only in a single region. Each facility is designed to run 24x7x365 and employs various industry-standard measures to help protect operations from power failure, physical intrusion, and network outages. These datacenters comply with industry standards (such as ISO 27001) for physical security and availability. They are managed, monitored, and administered by Microsoft operations personnel. Azure offers a wide range of encryption capabilities, giving customers the flexibility to choose the solution that best meets their needs. When customers delete data or leave Azure, Microsoft follows strict standards for overwriting storage resources before reuse.Upon a system's end-of-life, Microsoft operational personnel follow rigorous data handling procedures and hardware disposal processes to help assure that no hardware that may contain customer data is made available to untrusted parties.
To ensure data resiliency Azure asynchronously replicates data from a primary location to a secondary location within the same region. For applications resiliency, Microsoft Azure patterns ensure that at least one virtual machine will be available and meet the 99.95% Azure SLA.
Separation between consumers: Separation should exist between different consumers of the service to prevent one malicious or compromised consumer from affecting the service or data of another.
Because all customer cloud servers are virtual, the physical separation paradigm no longer applies. Microsoft Azure was designed to help identify and counter risks inherent in a multitenant environment. Data storage and processing is logically segregated among consumers of Azure using Active Directory and functionality specifically developed for multitenant services, which aims to ensure that consumer data stored in shared Azure data centers is not accessible by another organisation.
Governance framework: The service provider should have a security governance framework that coordinates and directs their overall approach to the management of the service and information within it.
The Microsoft compliance framework includes the following activities:
- Identify and integrate requirements
- Assess and remediate gaps.
- Test effectiveness and assess risk.
- Attain certification and attestations.
- Improve and optimize.
Operational security: The service provider should have processes and procedures in place to ensure the operational security of the service.
Operational Security Assurance (OSA) is a framework that incorporates the knowledge gained through a variety of resources that are unique to Microsoft, such as the Microsoft Security Response Center (MSRC), and incorporates deep awareness of the cybersecurity threat landscape. OSA helps make Microsoft cloud-based services' infrastructure more resilient to attack by decreasing the amount of time needed to prevent, detect, contain and respond to real and potential Internet-based security threats, thereby increasing the security of those services for customers.
Personnel security: Service provider staff should be subject to personnel security screening and security education appropriate for their role.
Microsoft Azure Operations and Customer Support personnel and data center staff, who operate Azure services and provide customer support (or Microsoft subcontractors who assist with platform operations, troubleshooting, and technical support) undergo a Microsoft standard background (or equivalent) check to evaluate employee education, employment, and criminal history. The background checks that are carried out are broadly in line with the requirements of the UK Government's BPSS / BS7858. They do not specifically include a formal identity check.
Secure development: Services should be designed and developed to identify and mitigate threats to their security.
The Microsoft Security Development Lifecycle (SDL) provides an effective threat-modelling process to identify threats and vulnerabilities in software and services. The STRIDE system (Spoofing, Tampering, Repudiation, Information disclosure, Denial of service, and Elevation of privilege) is used to help identify and resolve security threats early in the design process, before they can affect customers.
Supply chain security: The service provider should ensure that its supply chain satisfactorily supports all of the security principles that the service claims to implement.|
In Azure, security risks that relate to external parties, such as customers and vendors, are identified and addressed as follows:
- Third parties undergo a review process and an approved vendor list is established and used. These vendors are required to comply with Microsoft security policies and are audited.
- Additional risks that relate to granting access to facilities and information systems are controlled and managed by Microsoft teams, including physical and network level access to facilities and Microsoft resources.
Secure consumer management: Consumers should be provided with the tools required to help them securely manage their service.
Customers administer their Azure resources through the Azure portal, which provides access to all virtual machines, databases, cloud services, and other resources configured for the customer's account. Web access to the Azure portal is secured by industry-standard Transport Layer Security (TLS) 1.2 connections using 2048-bit RSA/SHA256 encryption keys, as recommended by CESG/NCSC . Role-based access controls are provided to enable customers to provide limited access to Azure management resources for specific users and groups.
Identity and authentication Access to all service interfaces (for consumers and providers) should be limited to authenticated and authorised individuals.
Azure provides services to help track identity as well as integrate it with identity stores that may already be in use. Azure AD is a comprehensive identity and access management service for the cloud that helps secure access to data in on-premises and cloud applications.
External interface protection: All external or less trusted interfaces of the service should be identified and have appropriate protections to defend against attacks through them.
Microsoft employs a method it calls 'Red Teaming' to improve Azure security controls and processes through regular penetration testing.
Secure service administration: The methods used by the service providers administrators to manage the operational service should be designed to mitigate any risk of exploitation that could undermine the security of the service.
Azure infrastructure operations personnel are required to use secure admin workstations (SAWs; also known as privileged access workstations, or PAWs). The SAW approach is an extension of the well-established recommended practice to use separate admin and user accounts for administrative personnel.
Audit information provision to consumers: Consumers should be provided with the audit records they need to monitor access to their service and the data held within it.
Azure Log Analytics collects records of the events occurring within an organisation's systems and networks as soon as they occur, before anyone can tamper with them, and allows different types of analysis by correlating data across multiple computers.
Secure use of the service by the consumer: Consumers have certain responsibilities when using a cloud service in order for this use to remain secure, and for their data to be adequately protected.
Azure Security Center helps consumers prevent, detect, and respond to threats with increased visibility into and control over the security of their Azure resources. It provides integrated security monitoring and policy management across Azure subscriptions, helps detect threats that might otherwise go unnoticed, and works with a broad ecosystem of security solutions.
The CSA published the Cloud Control Matrix to support customers in the evaluation of cloud providers and to identify questions that should be answered before moving to cloud services. In response, Microsoft Azure answered the CSA Consensus Assessment Initiative Questionnaire CSA CAIQ describe how Microsoft addresses the suggested principles.
The Crown Commercial Service (an agency that works to improve commercial and procurement activity by the government) renewed the classification of Microsoft in-scope enterprise cloud services to G-Cloud v6, covering all its offerings at the OFFICIAL level. Details of Azure and G-Cloud can be found in the Azure UK G-Cloud security assessment summary.
These templates automatically deploy the Azure resources for a multi-tier, Windows based three tier application with an Active Directory Domain architecture. As this is a complex deployment that delivers the full infrastructure and environment configuration deployment can take up to two hours. Progress can be monitored from the Resource Group blade and Deployment output blade in the Azure Portal.
Rather than develop the templates for this environment from scratch, some templates used are drawn from the Microsoft Patterns and Practices GitHub Repository Template Building Blocks and orchestrated through a an a master ARM template or PowerShell script. Other Azure architectural best practices and guidance can be found in Azure Reference Architectures. Supporting Microsoft Visio templates are available from the Microsoft download center with the corresponding ARM Templates found at Azure Reference Architectures ARM Templates.
As a pre-requisite to deployment users should ensure that they have -
-
An Azure Subscription
-
Admin or co-admin rights for the Subscription
-
The Azure Subscription ID has been noted
-
The latest version of PowerShell to execute the deployment script
| Activity | Configuration |
|---|---|
| Create Management VNet Resource Groups | Enter resource group name during deployment |
| Create Operational VNet Resource Groups | Enter resource group name during deployment |
| Deploy VNet network infrastructure | Enter resource group name during deployment |
| Create VNet Peerings | None required |
| Deploy VPN Gateway | The template deploys an Azure environment with a public facing endpoint and an Azure Gateway to allow VPN setup between the Azure environment and your on-premises environment. To complete this VPN connection, you will need to provide the Local Gateway (your on-premises VPN public IP address) and complete the VPN connection set up locally. VPN Gateway requires local gateway configuration in the /parameters/azure/ops-network.parameters.json template parameters file or through the Azure portal. |
| Deploying internet facing Application Gateway | For SSL termination, Application Gateway requires you SSL certificates to be uploaded. When provisioned the Application Gateway will instantiate a public IP address and domain name to allow access to the web application |
| Create Network Security Groups for VNETs | RDP access to the Management VNet Jumpbox must be secured to a trusted IP address range. It is important to amend the "sourceAddressPrefix" parameter with your own trusted source IP address range in the /parameters/azure/nsg-rules.parameters.json template parameters file. NSG configuration for the operational VNet can be found at /parameters/azure/ops-vent-nsgs.json |
| Create ADDS resource group | Enter resource group name during deployment and edit the configuration fields if required |
| Deploying ADDS servers | None required |
| Updating DNS servers | None required |
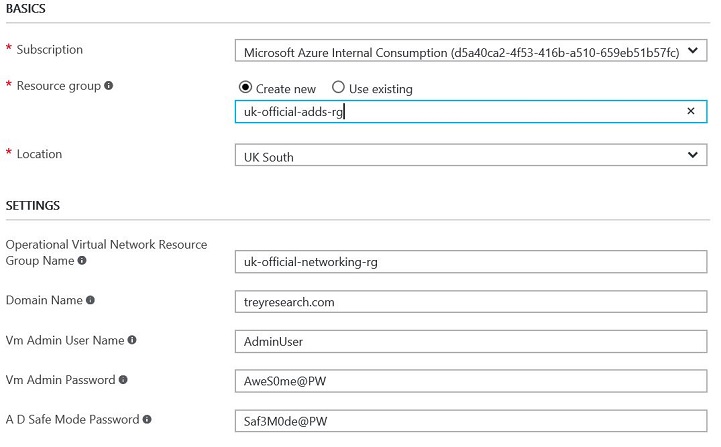
| Create ADDS domain | The provided templates create a demo 'treyresearch' domain. To ensure that the required Active Directory Domain is created with the desired domain name and administrative user the fields can be configured in the deployment screen or in the /parameters/azure/add-adds-domain-controller.parameters.json template parameters file must be edited with the required values |
| Create ADDS domain controller | None required |
| Create operational workload Resource Group | Enter resource group name during deployment |
| Deploy operational VM tiers and load balancers | None required |
| Set up IIS web server role for web tier | None required |
| Enable Windows Auth for VMs | None required |
| Deploy Microsoft Anti-malware to VMs | None required |
| Domain Join VMs | Domain joining the Virtual Machines is a post deployment step and must be manually completed |
A deployment for this reference architecture is available on GitHub. The templates can be cloned or downloaded if customisation of parameters are requried. The reference architecture is deployed in four stages. To deploy the architecture, follow these steps for each deployment stage -
For Virtual Machines The parameter files include a hard-coded administrator user names and passwords. These values can be changed in the parameter files if required. Tt is strongly recommended that you immediately change both on all the VMs. Click on each VM in the Azure portal then click on Reset password in the Support troubleshooting blade.


- Click on the Deploy to Azure button to begin the first stage of the deployment. The link takes you to the Azure Portal.
- Select Create New and enter a value such as
uk-official-networking-rgin the Resource group textbox. - Select a region such as
UKSouthfrom the Location drop down box (All Resource Groups required for this architecture should be in the same Azure region e.g.UKSouth - Some parameters can be edited in the deployment page. If greater customisation is requried this can be down through cloning and editing the templates directly, or in situ by editing the templates by clicking 'Edit template'.
- Review the terms and conditions, then click the I agree to the terms and conditions stated above checkbox.
- Click on the Purchase button.
- Check Azure portal notification for a message that the stage of deployment is complete and move on to the next if completed.
- If for some reason your deployment fails. To avoid incurring cost and orphan resources it is advisable to delete the resource group in its entirety, fix the issue and redeploy the resource groups and template.


- Click on the Deploy to Azure button to begin the first stage of the deployment. The link takes you to the Azure Portal.
- Select Create New and enter a value such as
uk-official-adds-rgin the Resource group textbox. - Select a region such as
UKSouthfrom the Location drop down box (All Resource Groups required for this architecture should be in the same Azure region e.g.UKSouth. - Some parameters can be edited in the deployment page. If greater customisation is requried this can be down through cloning and editing the templates directly, or in situ by editing the templates by clicking 'Edit template'.
- In the Settings textboxes, enter the networking resource group as entered when creating the networking infrastructure in deployment step 1.
- Enter the Domain settings and Admin credentials.
- Review the terms and conditions, then click the *I agree to the terms and conditions stated above checkbox.
- Click on the Purchase button.
- Check Azure portal notification for a message that the stage of deployment is complete and move on to the next if completed.
- If for some reason your deployment fails. To avoid incurring cost and orphan resources it is advisable to delete the resource group in its entirety, fix the issue and redeploy the resource groups and template.


- Click on the Deploy to Azure button to begin the first stage of the deployment. The link takes you to the Azure Portal.
- Select Create New and enter a value such as
uk-official-operational-rgin the Resource group textbox. - Select a region such as
UKSouthfrom the Location drop down box (All Resource Groups required for this architecture should be in the same Azure region e.g.UKSouth - Some parameters can be edited in the deployment page. If greater customisation is requried this can be down through cloning and editing the templates directly, or in situ by editing the templates by clicking 'Edit template'.
- In the Settings textboxes, enter the operational network resource group as entered when creating the networking infrastructure in deployment step 1.
- Enter the Virtual Machine Admin credentials.
- Review the terms and conditions, then click the I agree to the terms and conditions stated above checkbox.
- Click on the Purchase button.
- Check Azure portal notification for a message that the stage of deployment is complete and move on to the next if completed.
- If for some reason your deployment fails. To avoid incurring cost and orphan resources it is advisable to delete the resource group in its entirety, fix the issue and redeploy the resource groups and template.
##(Optional) PowerShell Deployment
To deploy this solution through PowerShell, you will need the latest version of the Azure CLI to run the PowerShell script that deploys the solution. To deploy the reference architecture, follow these steps
- Download or clone the solution folder from GitHub to your local machine.
- Open the Azure CLI and navigate to the local solution folder.
- Run the following command:
.\Deploy-ReferenceArchitecture.ps1 <subscription id> <location> <mode> - Replace
<subscription id>with your Azure subscription ID. - For
<location>, specify an Azure region, such asUKSouthorUKWest. - The
<mode>parameter controls the granularity of the deployment, and can be one of the following values:
Infrastructure: deploys the networking infrastructureADDS: deploys the VMs acting as Active Directory DS servers, deploys Active Directory to these VMs, and deploys the domain in Azure.Operational: deploys the web, business and data tier VMs and load balancersDeployAll: deploys all the preceding deployments.
Microsoft's customers are now able to use private connections to the company's UK data centres. Microsoft's partners are providing a gateway from PSN/N3 to ExpressRoute and into Azure - just one of the new services the group has unveiled since the company launched its Azure and Office 365 cloud offering in this country at launch (http://news.microsoft.com/en-gb/2016/09/07/not-publish-microsoft-becomes-first-company-open-data-centres-uk/). Since then, thousands of customers including the Ministry of Defence, the Met Police and parts of the NHS - have signed up to take advantage of the sites, which offer UK data residency, security and reliability.
Deploying this template will create one or more Azure resources. You will be responsible for the costs generated by these resources so it is important that you review the applicable pricing and legal terms associated with all resources and offerings deployed as part of this template. For cost estimates, you can use the Azure Pricing Calculator.
Further best practice information and recommendations for configuring and securing a multi-tier application in Azure can be found in Running Windows VMs for an N-tier architecture on Azure.
Best practices on Azure Network Security and a decision-making matrix can be found in Microsoft cloud services and network security.