This project is used for demo purposes to highlight the use of File Storage Security on AWS/Azure with Trend Micro Cloud One. For more information on the product, please refer to the product page here or within product documentation here.
- Malware scanning of external or third-party ingested files before introducing to your business workflow
- Supports AWS S3 Bucket scanning, Azure Blob storage scanning
- Fully Cloud-native design, highly scalable
- No use of VM instances, OS patching, runs on Serverless functions on the Cloud
- Files do not leave your VPC/Network
- Files are not limited to file size or file extensions. See performance metrics by platforms here
- Deployed in minutes
- Wide variety and constantly evolving post-scan action workflow integrations, scan triggers and so on, here
- Great team behind the product!! ❤️
To use this script, you need the following dependencies -
You could install the Serverless framework dependency using NPM or as a standalone version using cURL on macOS/Linux and Chocolatey on Windows machines.
- NPM, to run
npm install- Optional to install the Serverless framework. Refer to the Get Started Guide for other standalone options.
- Serverless Framework CLI, like
npm install -g serverless
Finally, you need to run from within the code directory
$ serverless plugin install -n serverless-python-requirements
All configurable options are found in the serverless.yml file under .custom
| Fields | Description | Required? |
|---|---|---|
awscli_profile |
AWS CLI profile to use to deploy the Serverless CloudFormation stack | Yes |
aws_region |
AWS Region to deploy the CloudFormation stack to | Yes |
buckets |
Buckets that malware files need to be dropped. |
Yes |
time_interval_in_hours |
Regular intervals to upload malware to the said S3 buckets and trigger detections | Yes |
In order to deploy the example, you need to run the following command:
$ serverless deploy -s dev
After running deploy, you should see output similar to:
Serverless: Packaging service...
Serverless: Excluding development dependencies...
Serverless: Creating Stack...
Serverless: Checking Stack create progress...
........
Serverless: Stack create finished...
Serverless: Uploading CloudFormation file to S3...
Serverless: Uploading artifacts...
Serverless: Uploading service aws-python.zip file to S3 (711.23 KB)...
Serverless: Validating template...
Serverless: Updating Stack...
Serverless: Checking Stack update progress...
.................................
Serverless: Stack update finished...
Service Information
service: aws-python
stage: dev
region: us-east-1
stack: aws-python-dev
resources: 6
functions:
api: aws-python-dev-hello
layers:
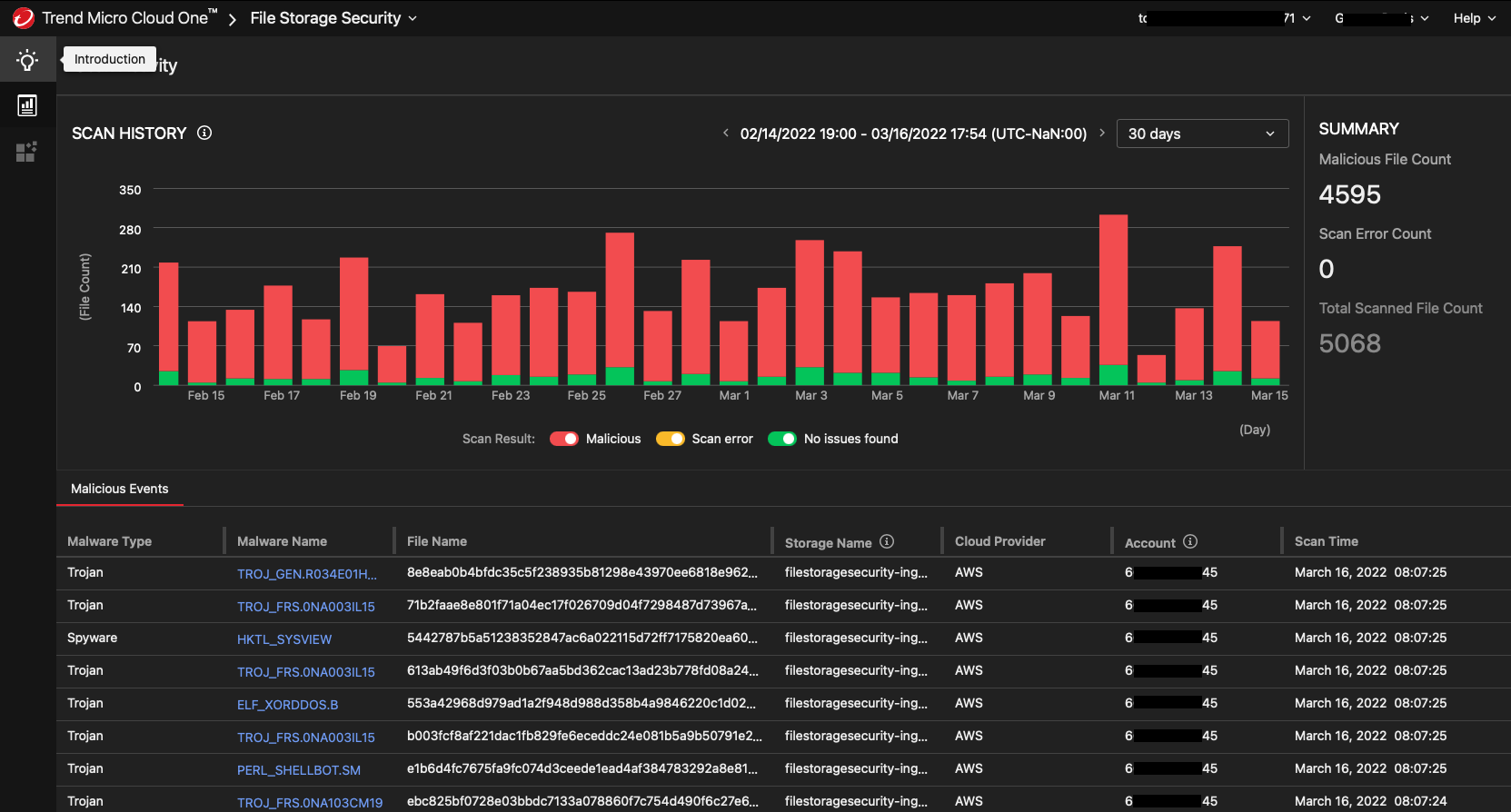
NoneAfter successful deployment, you can see the output on the File Storage Security dashboard on Trend Micro Cloud One.
The script is triggered every few hours, as configured in the serverless.yml file before deployment, under .custom.stages.<stage-name>.time_interval_in_hours (refer to the Configuration section below) or under .functions.main.events.schedule.rate.