Sneaky Spikes: Uncovering Stealthy Backdoor Attacks in Spiking Neural Networks with Neuromorphic Data
Corresponding code for the paper: "Sneaky Spikes: Uncovering Stealthy Backdoor Attacks in Spiking Neural Networks with Neuromorphic Data", at Network and Distributed System Security (NDSS) 2024.
A guide to the code is available here.
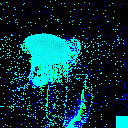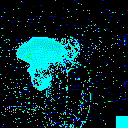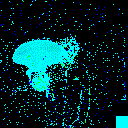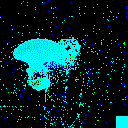
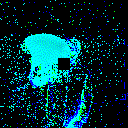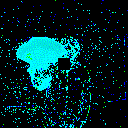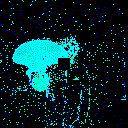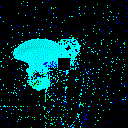
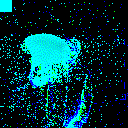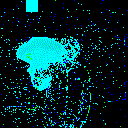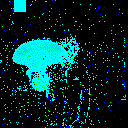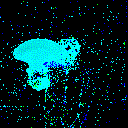
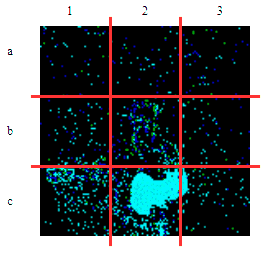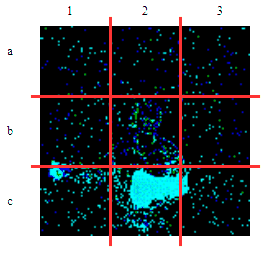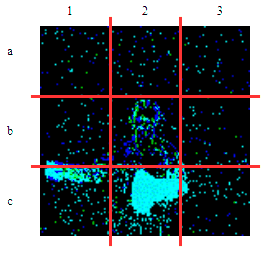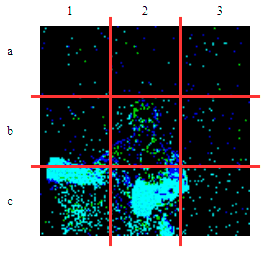
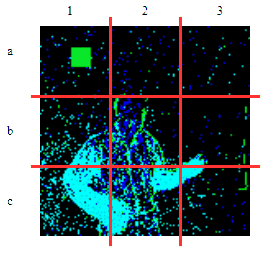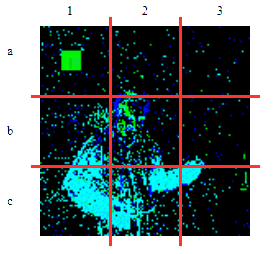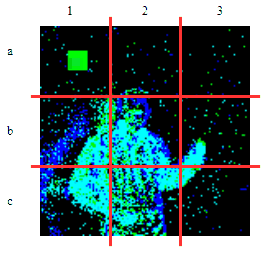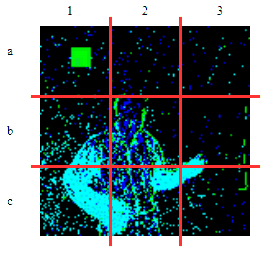
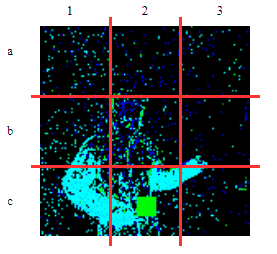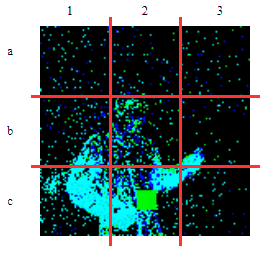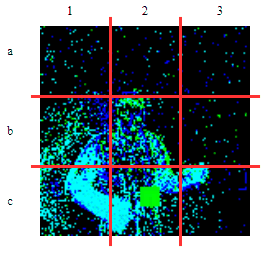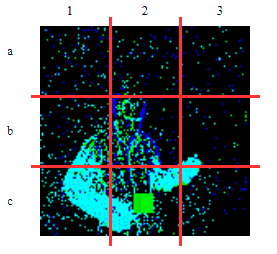
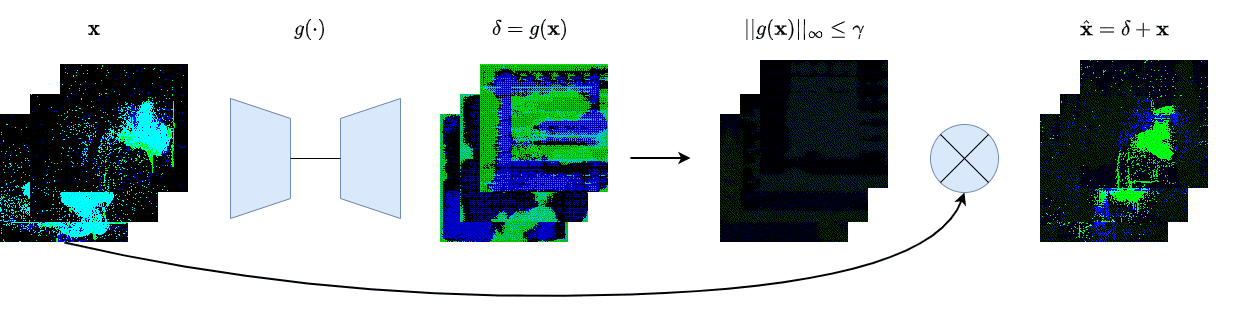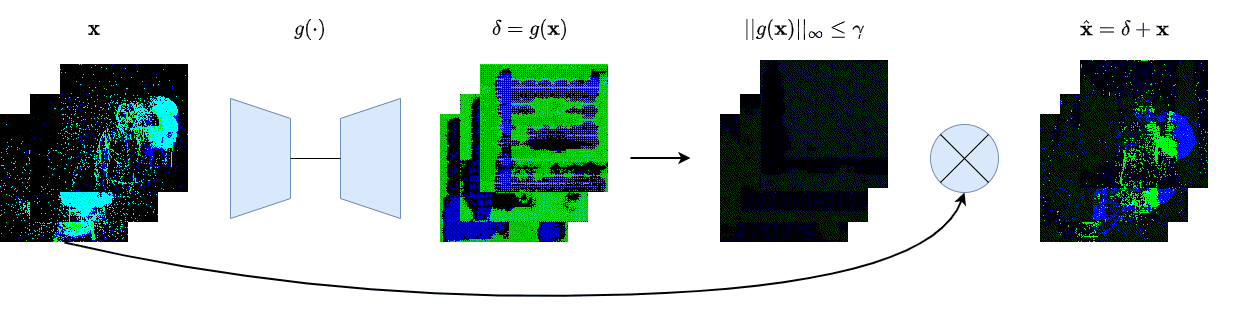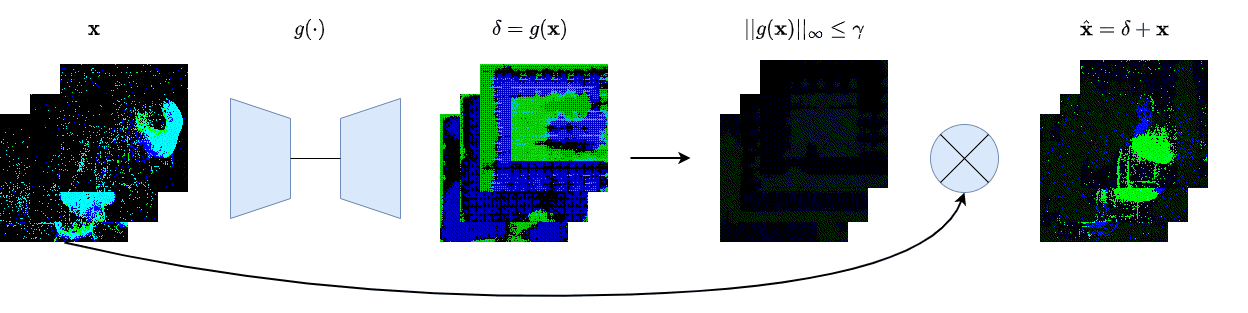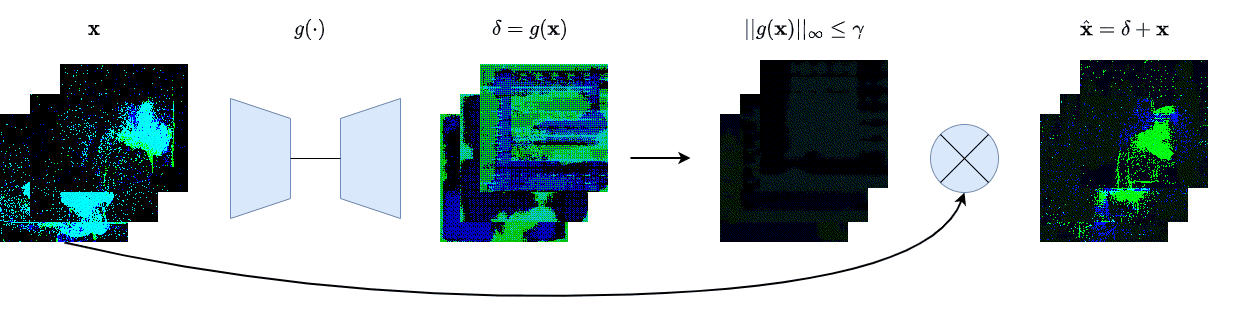
| γ | 0.1 | 0.05 | 0.01 |
|---|---|---|---|
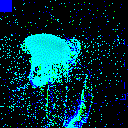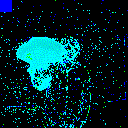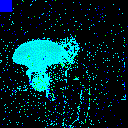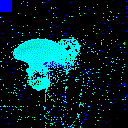
| Clean image |  |
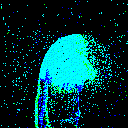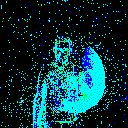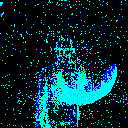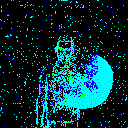 |
 |
| Noise |  |
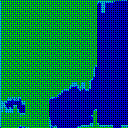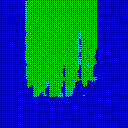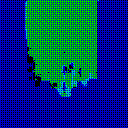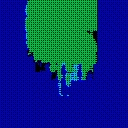 |
 |
| Projected Noise | 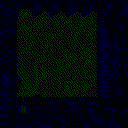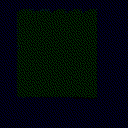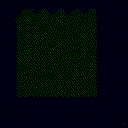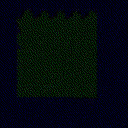 |
 |
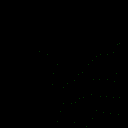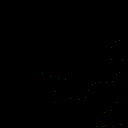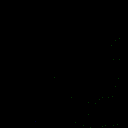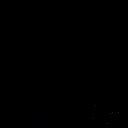 |
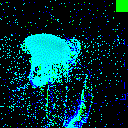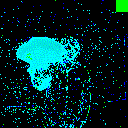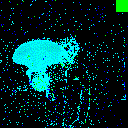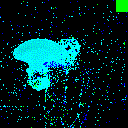
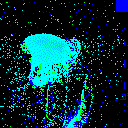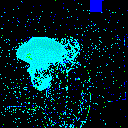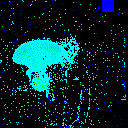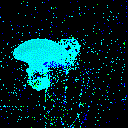
| Backdoor image | 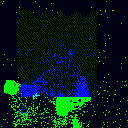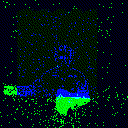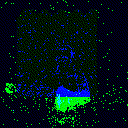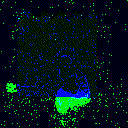 |
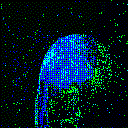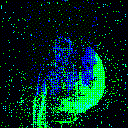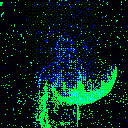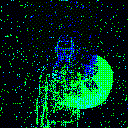 |
 |
Gorka Abad, Oguzhan Ersoy, Stjepan Picek, and Aitor Urbieta.
@inproceedings{abad2024sneaky,
title={Sneaky Spikes: Uncovering Stealthy Backdoor Attacks in Spiking Neural Networks with Neuromorphic Data.},
author={Abad, Gorka and Ersoy, Oguzhan and Picek, Stjepan and Urbieta, Aitor.},
booktitle={NDSS},
year={2024}
}
This project is licensed under the MIT License - see the LICENSE file for details.