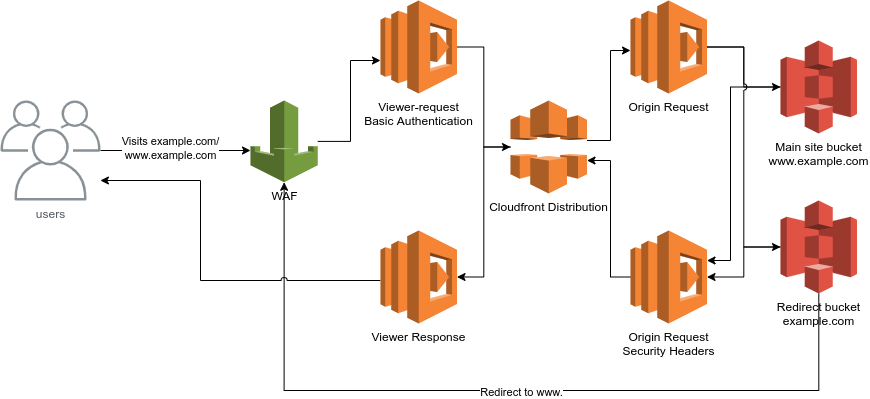
s3-cloudfront-website
Creates a cloudfront distribution website using s3 bucket website configuration for static file hosting.
Diagram
Upgrade notes
v1.x.x to v2.x.x upgrade
Take note of the breaking changes from AWS v4 upgrade guid e
You will have to run terraform import, e.g replace var.domain_name[0] with your host name terraform import aws_s3_bucket_logging var.domain_name[0] for each of the following.
aws_s3_bucket_aclaws_s3_bucket_loggingaws_s3_bucket_policyaws_s3_bucket_server_side_encryption_configurationaws_s3_bucket_versioningaws_s3_bucket_website_configuration
v3.x.x to v5.x.x upgrade
In order to remove the lambda redirection and fully rely on cloudfront and s3 to handle it, there needs to be a point the local provider is available during deletion, therefore you need to upgrade to v4.0.0 that removes the lambda successfully, before upgrading to v5.x.x that will handle redirects without lambda
Adding CSP headers
X headers are returned by default, to customise the content security policy, format it in terraform and provide the full string to the variable content_security_policy
locals {
default-src = join(" ", ["default-src", "'none'"])
connect-src = join(" ", ["connect-src", "https://*.example.com"])
font-src = join(" ", ["font-src", "'self'"])
img-src = join(" ", ["img-src", "'self'"])
script-src = join(" ", ["script-src", "'self'"])
style-src = join(" ", ["style-src", "'self'", "'unsafe-inline'"])
object-src = join(" ", ["object-src", "'none'"])
content_security_policy = join( "; ", [local.default-src, local.connect-src, local.font-src, local.img-src, local.script-src, local.style-src, local.object-src])
}
module "cloudfront" {
...
content_security_policy = local.content_security_policy
...
}
Requirements
| Name | Version |
|---|---|
| local | ~> 2.1 |
Providers
| Name | Version |
|---|---|
| aws | n/a |
| aws.us-east-1 | n/a |
Modules
No modules.
Resources
Inputs
| Name | Description | Type | Default | Required |
|---|---|---|---|---|
| cloudfront_origin_path | Origin path of CloudFront | string |
"" |
no |
| content_security_policy | Formatted CSP in string | string |
"default-src 'none';" |
no |
| cors_allowed_origins | CORS allowed origins | list(string) |
[] |
no |
| domain_names | domain names to serve site on | list(string) |
n/a | yes |
| enable_acm_validation | Validates ACM by updating route 53 DNS | bool |
false |
no |
| forward_query_string | forward query strings to origin | bool |
false |
no |
| lambda_function_associations | CloudFront Lambda function associations. key is CloudFront event type and value is lambda function ARN with version | map(string) |
{} |
no |
| main_default_ttl | default TTL of the main cloudfront distribution | number |
180 |
no |
| ordered_cache_behaviors | n/a | list(object({ |
[] |
no |
| permissions_boundary | If provided, all IAM roles will be created with this permissions boundary attached. | string |
"" |
no |
| redirect_domain_names | domain names to redirect to domain_names |
list(string) |
n/a | yes |
| route53_zone_id | Route53 Zone ID | string |
"" |
no |
| s3_logging_bucket | Bucket which will store s3 access logs | string |
"" |
no |
| s3_logging_bucket_prefix | Bucket which will store s3 access logs | string |
"" |
no |
| save_access_log | whether save cloudfront access log to S3 | bool |
false |
no |
| service_name | tagged with service name | any |
n/a | yes |
| web_acl_id | WAF ACL to attach to the cloudfront distribution | string |
"" |
no |