- SNMP Asks for OID:
1.3.6.1.4.1.14988.1.1.18.1.1.2.X(Where last «X» is an SNMP ID number of a script in RouterOS\Mikrotik/system script) - RouterOS\Mikrotik automatically runs the script and returns a result to SNMP with 0 or 1 if IPsec Phase 2 Established with the IP
- Create a copy of the script (https://raw.githubusercontent.com/gitpel/routeros-ipsec-snmp/master/snmp-ipsec-ph2-probe) to your RouterOS/Mikrotik
system > scripts - Name it for example as "probe-ipsec-x.x.x.x"
- Enable SNMP on RouterOS\Mikrotik (we will use the version of SNMP v2c):
/snmp community set [ find default=yes ] addresses=0.0.0.0/0 write-access=yes
/snmp set contact="XXXXXXXXX" enabled=yes location="YYYYYYYYYY" trap-version=2
- Download https://www.paessler.com/tools/snmptester for SNMP debugging also you can use *nix
snmpgetandsnmpwalk(more info: https://wiki.mikrotik.com/wiki/Manual:SNMP#Run_Script) - Check OIDs of scripts that you have on your RouterOS\Mikrotik using SNMP walk and OID for scripts:
1.3.6.1.4.1.14988.1.1.8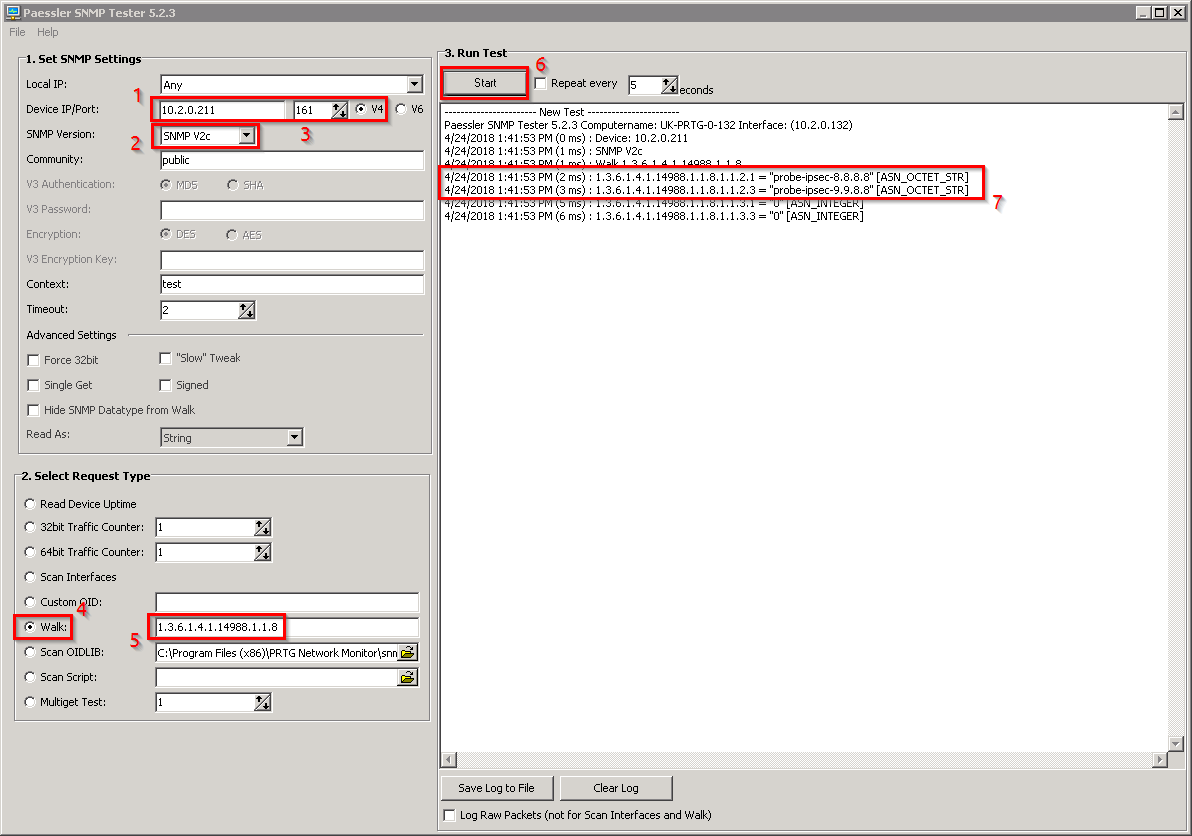
As you can see in my example I have 2 scripts with OIDs: 1.3.6.1.4.1.14988.1.1.8.1.1.2.1 and 1.3.6.1.4.1.14988.1.1.8.1.1.2.2, I will use the first one for example
- Change 8 to 18 in OID: 1.3.6.1.4.1.14988.1.1.8.1.1.2.1 to 1.3.6.1.4.1.14988.1.1.18.1.1.2.1 to execute the script via SNMP and get results
- Check result of the script that you have on your RouterOS\Mikrotik using SNMP get
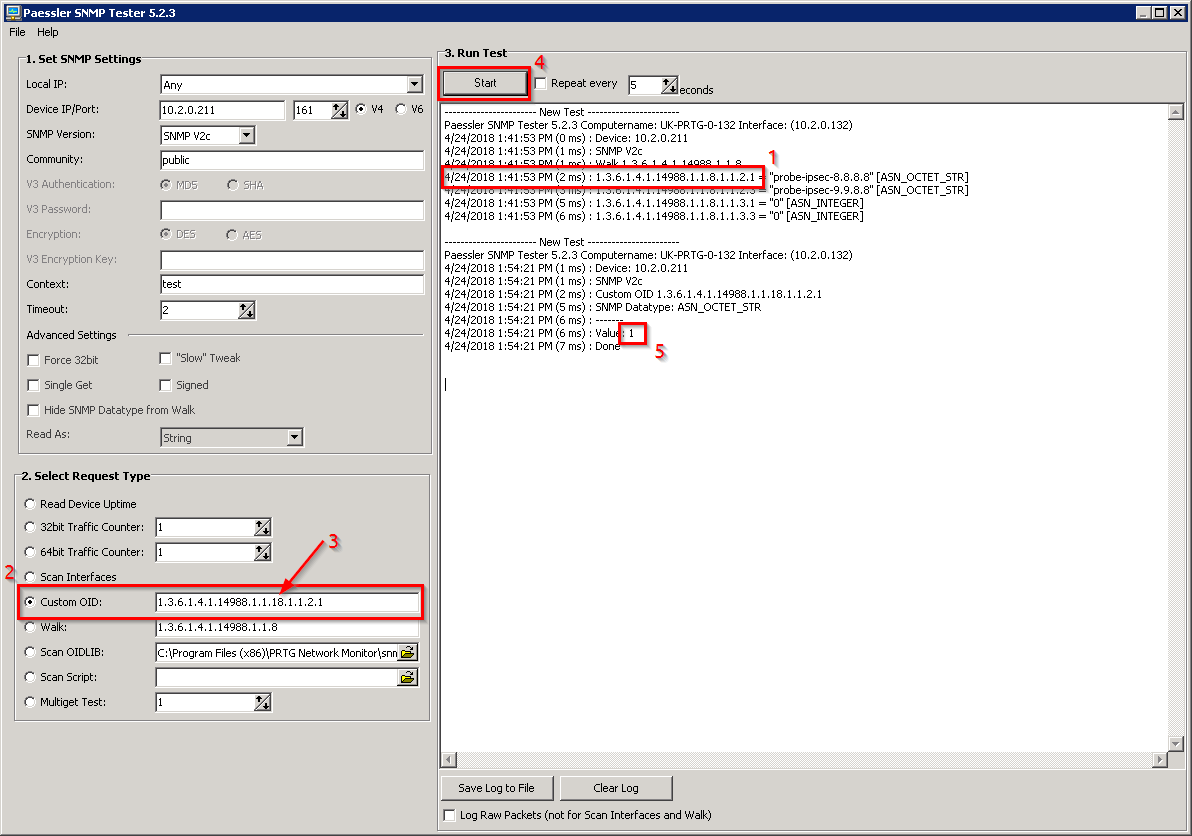
- Add the SNMP probe check to your SNMP Management System (In my case we will use PRTG)
- Done