For Burp Suite Enterprise Edition
Please note that extensions are written by third party users of Burp, and PortSwigger makes no warranty about their quality or usefulness for any particular purpose.
- Build the extension
- Load the extension into Burp Enterprise, and add the extension to your Site Details page
- Configure your session handling rule in Burp Suite Professional
- Import the scan configuration into Enterprise and add the scan configuration to your Site Details page
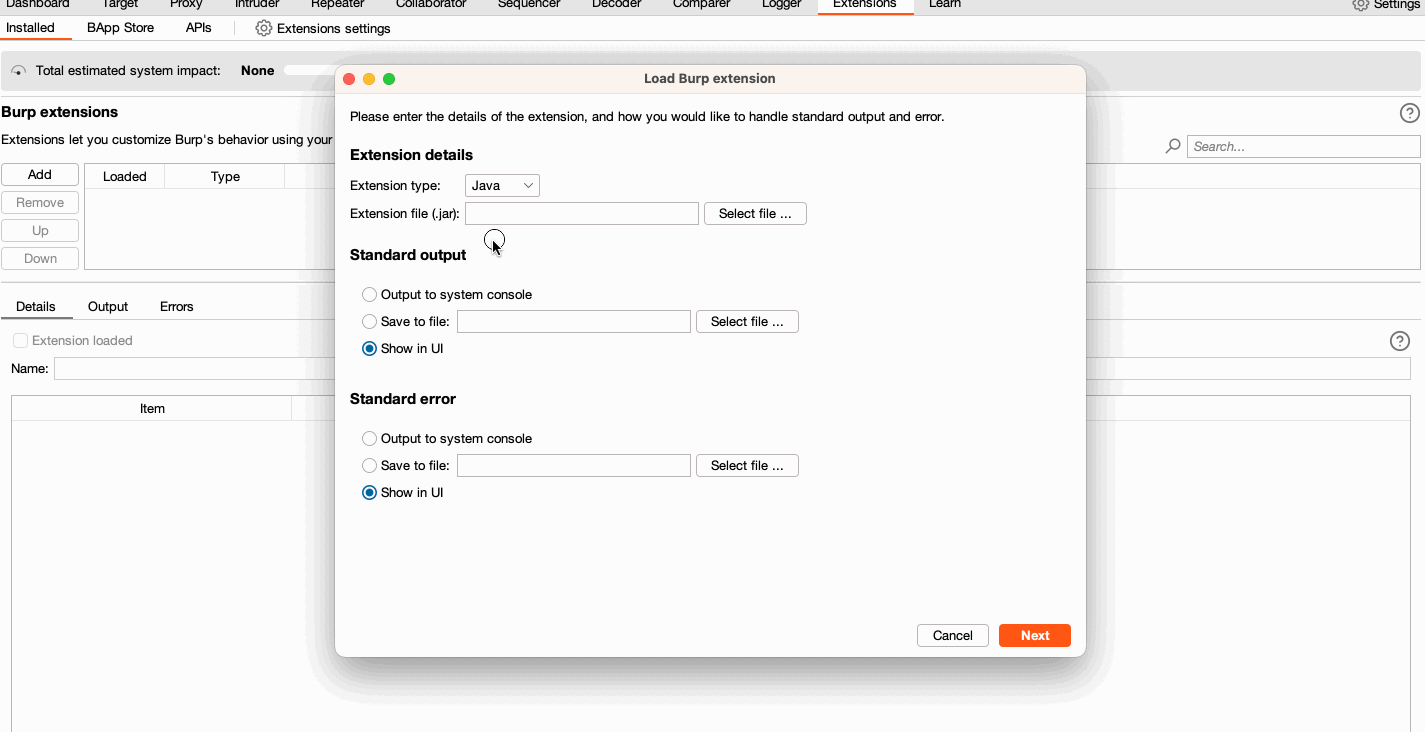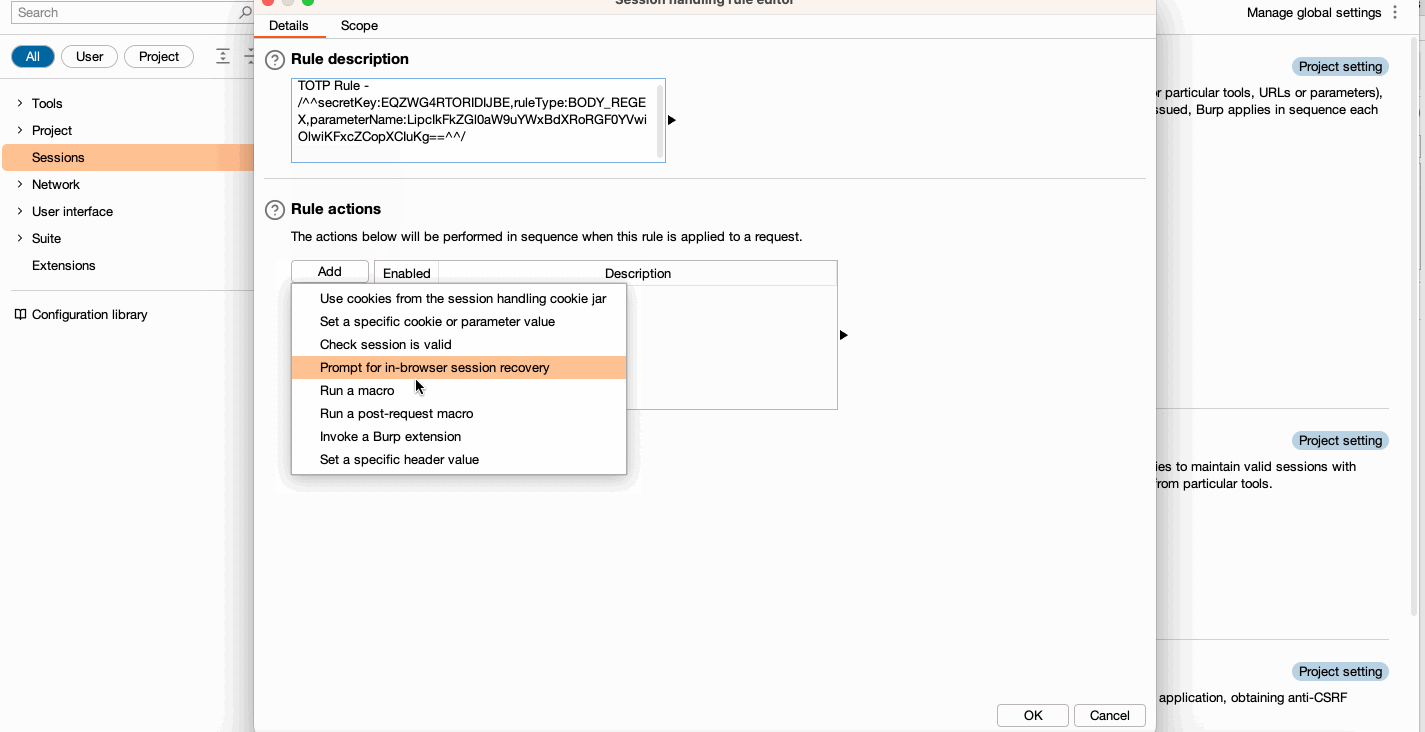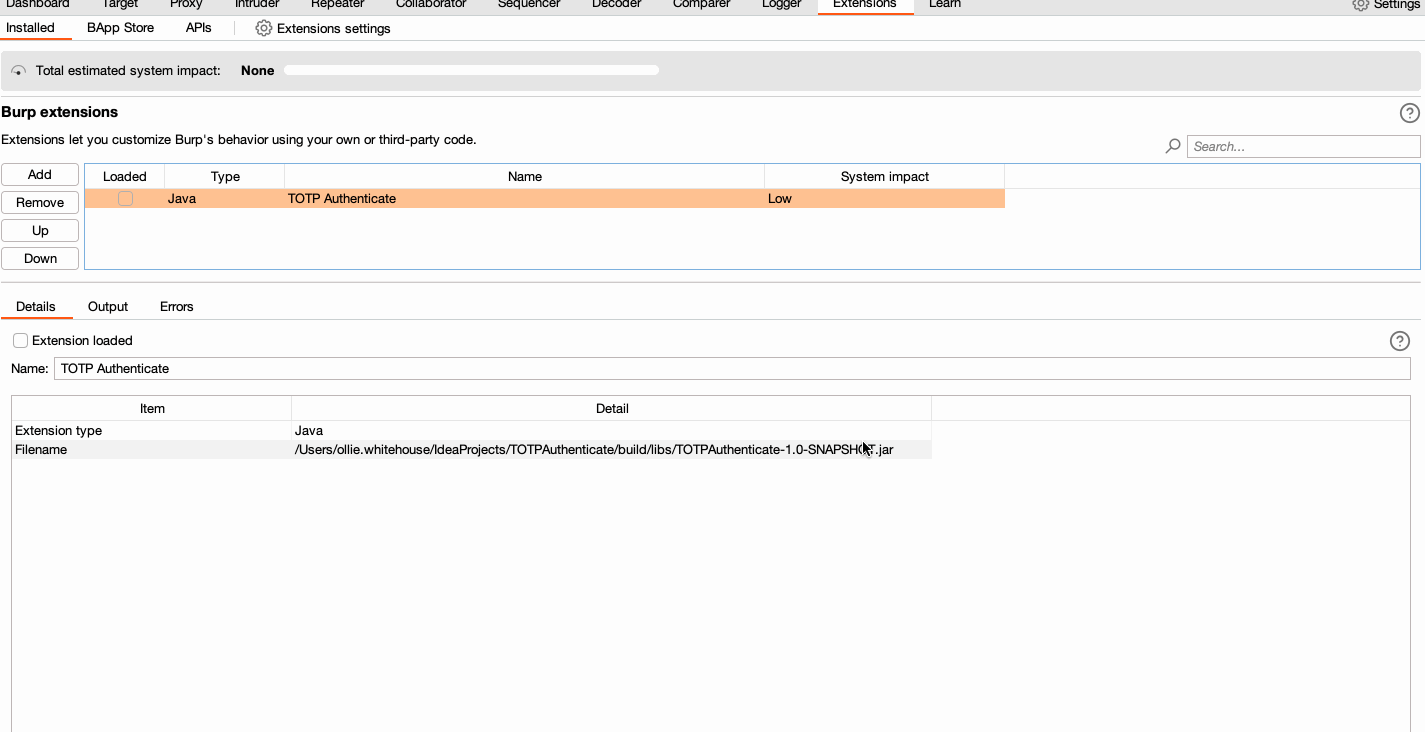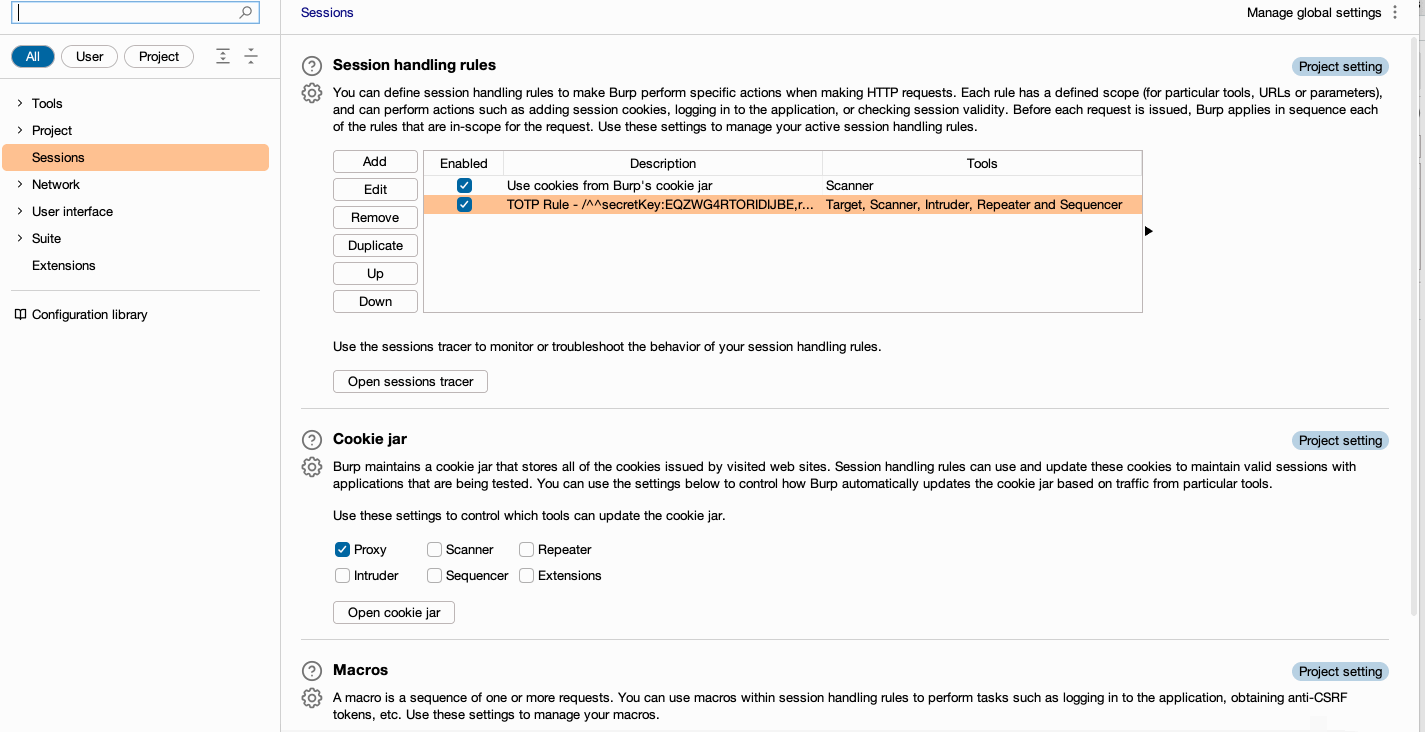
- Load the extension into
Extensions > Installed > Add - Go to
Settings > Search > Sessions - Under
Session handling rules, go toAdd > Rule actions > Add > Invoke a Burp extension, selectTOTP Authenticatefrom the dropdown list available and clickOK - Set your Rule description
- Click across to the
Scopetab, ensuring that theTools scope > Scannerbox is checked - Configure your URL scope appropriately
- Click
OK - Go to
Extensions > Installedand reload the extension (uncheck the TOTP Authenticate "Loaded" checkbox, and click it again) - Perform any testing in Burp Suite Professional/Community
- Export the session handling rule by going to
Session handling rules > Cog button > Save settings
- Only the first rule present will be applied
- Any rule changes will require extension reloads when testing in Burp Suite Professional or Community Edition
- Due to the frequency of logins by Burp Scanner, OTPs can end up getting reused, which can result in failing logins. To avoid this, you may need to use "Incy Wincy" mode or add a delay to your recorded login sequence. Please note that adding a delay to a recorded login sequence will heavily impact scan times.
/^^secretKey:BASE32,ruleType:TYPE,parameterName:NAME_OF_PARAMETER_VALUE_OR_BASE64_ENCODED_REGEX^^/
/^^delimiter to signify the start of the rulesecretKey:the BASE32 encoded OTP seedruleType:describes where to apply the ruleparameterName:- for
ruleTypeofBODY_REGEXit is the BASE64 encoded regular expression that defines where to update - for
ruleTypeofHEADER,URL,COOKIEorBODY_PARAMit is the literal name of the key:value pair to add or update
- for
^^/delimiter to signal the end of the rule
HEADERURLCOOKIEBODY_PARAMBODY_REGEX
The following example supplies the regex of .*\"AdditionalAuthData\":\"(\d*)\".* as its parameterName to identify the match expression and replace (\d*) with the generated OTP rolling code
/^^secretKey:EQZWG4RTORIDIJBE,ruleType:BODY_REGEX,parameterName:LipcIkFkZGl0aW9uYWxBdXRoRGF0YVwiOlwiKFxkKilcIi4q^^/
The following example adds or replaces a header named TEST with the value of the generated OTP rolling code
/^^secretKey:EQZWG4RTORIDIJBE,ruleType:HEADER,parameterName:TEST^^/
{
"project_options":{
"sessions":{
"session_handling_rules":{
"rules":[
{
"actions":[
{
"action_name":"TOTP Authenticate",
"enabled":true,
"type":"invoke_extension"
}
],
"description":"My OTP rule: /^^secretKey:EQZWG4RTORIDIJBE,ruleType:HEADER,parameterName:TEST^^/",
"enabled":true,
"exclude_from_scope":[],
"include_in_scope":[],
"named_params":[],
"restrict_scope_to_named_params":false,
"tools_scope":[
"Scanner"
],
"url_scope":"all",
"url_scope_advanced_mode":false
}
]
}
}
}
}We would recommend testing this extension out in Burp Suite Professional/Community before usage in Burp Suite Enterprise Edition.
To test this extension in Enterprise, you can configure an upstream proxy through Burp to ensure that your token has been added appropriately.
If using the following configuration, please make sure that an instance of Burp Suite Pro/Community is running and you are using a local agent.
{
"project_options":{
"connections":{
"upstream_proxy":{
"servers":[
{
"auth_type":"none",
"destination_host":"*",
"proxy_host":"127.0.0.1",
"proxy_port":8080,
"enabled":true
}
],
"use_user_options":false
}
}
}
}- If you do not have Gradle already installed, follow the installation instructions here.
- Once Gradle is installed, run
gradle fatJarfrom the installation directory using the command line. - Make sure you are using the latest version of Gradle.