Video Link : Image Steganography
csc ImageSteganographyHost.exe
Then, start the Client:
Directly from Visual Studio
Steganography is method of hiding data in the some medium which is called cover. It is like data is hidden under the cover which can be Image , Audio, Video, etc. Hiding in image is the most easy way for implementing the Steganography.
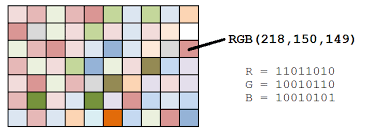
The reason behind is how the digital image is constructed.We can describe a digital image as a finite set of digital values, called pixels. Pixels are the smallest individual element of an image, holding values that represent the brightness of a given color at any specific point. So we can think of an image as a matrix (or a two-dimensional array) of pixels which contains a fixed number of rows and columns.
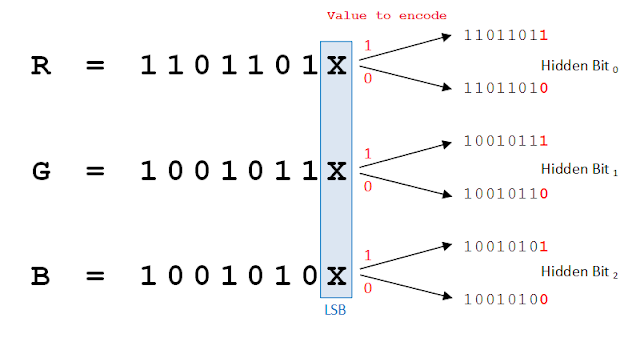
As digital image has three channels, so bits can be changed as per the data we want to hide. But changing any bits will impact the image in larger way and both original and encoded image can be differentiated. So the solution is to change only the last bit of each channel which contributes less in the image visualization.
So in total the bits that can be stored in image is limited to (Image_Height * Image_Width * 3) But we have compressed the message to certain extent so our steganography will be able to store more than above specified.
Here one of it is encoded with data, but they can't be differentiated as image is encoded using LSB(Least Significant bit) technique.
If someone knows that the current image is encoded then they can reverse the process and can know the data which is hidden. So to avoid such situation we have used data encryption standards like AES and DES which are much secure. So the image which is encoded has the data hidden in it is encrypted and can only be decrypted if the attacker knows the private Key.
The major use of this system is in the digital watermarking of images to stop getting pirated. Other usage are for secure communication over certain public channels.