Warning: Information found from this repository is mostly my notes. This means that info might be really scattered and not that clear for other users!
- You have to run a Virtual Machine with the Linux OS of your choice in the hypervisor of your choice.
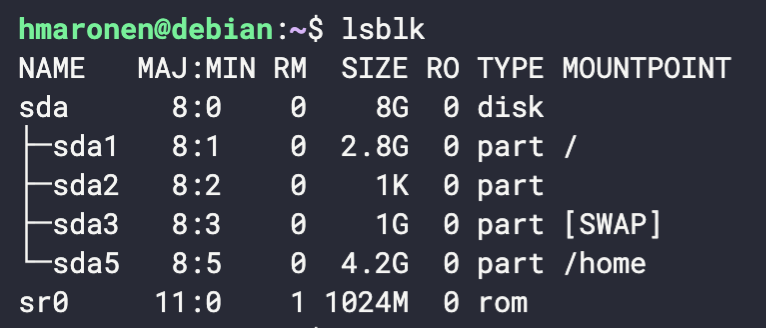
- Disk size has to be 8GB
- At least one 4.2 GB partition.
OS: Debian
Hypervisor: Virtual Box
Partitions for the Virtual Machine are easiest to do when you are installing VM for the first time. The partition can also be done afterward, but it can be a little bit cumbersome.
How to check partitions from the terminal:
lsblk
Updating packages
apt-get update
apt-get upgrade
Create a non-root user to connect to the VM.
useradd <name>
Give this user access rights to
sudocommands.
Install sudo package:
apt install sudo
sudo vim /etc/sudoers
<username> ALL=(ALL) NOPASSWD:ALL
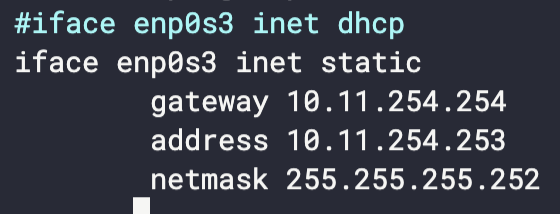
Configure VM so it does NOT use DHCP. It also needs to use static IP and a Netmask \30
apt install vim (Because nobody does use nano.)
sudo vim /etc/network/interfaces
Change the default port to one of your choice.
SSH access HAS TO be done with publickeys. SSH root access SHOULD NOT be allowed directly, but with a user who can be root.
sudo vim /etc/ssh/sshd_config
Port 2021
PubkeyAuthentication yes
PasswordAuthentication no
PermitRootLogin no
sudo systemctl restart sshd
"Please note that port numbers 0-1023 are reserved for various system services"
You have to set the rules of your firewall on your server only with the services used outside the VM.
sudo apt install ufw
sudo ufw default deny incoming
sudo ufw default allow outgoing
Enable ports for services that we need:
HTTP
sudo ufw allow 80/tcp
HTTPS
sudo ufw allow 443
SSH
sudo ufw allow 2021/tcp
Enable UFW on startup:
sudo vim /etc/ufw/ufw.conf
ENABLED=yes
sudo ufw enable
sudo ufw verbose
You have to set a DOS (Denial Of Service Attack) protection on the open ports of your VM.
Installing needed packages:
sudo apt-get install iptables apache2 fail2ban
Create a copy from jail.conf and rename it to jail.local, because jail.conf can be overwritten by an update.
cp /etc/fail2ban/jail.conf /etc/fail2ban/jail.local
Command for checking what IP:s has been updated:
sudo fail2ban-client status <name of jail>
| File Name | Description |
|---|---|
/etc/fail2ban/fail2ban.conf |
Main config file |
/etc/fail2ban/filter.d/http-get-dos.conf |
Filter file |
Resources for configurations:
Fail2Ban Port 80 to protect sites from DOS Attacks
Install fail2ban to protect your site from DOS attacks
How to unban an IP in fail2ban
You have to set protection against scans on your VM’s open ports.
Resource:
How to block port scan attacks with psad
The command for seeing all open ports:
sudo lsof -i -P -n | grep LISTEN
Commands:
| Command | Description |
|---|---|
sudo psad -S |
Show PSAD status |
sudo psad -F |
Unban everyone |
sudo psad --fw-rm-block-ip <IP-Address> |
Allow particular addresses |
Stop the services you don’t need for this project.
Disable certain services:
sudo systemctl disable <SERVICE_NAME>
Show status of all services:
sudo service--status-all
Create a script that updates all the sources of the package, then your packages, and which logs the whole in a file named /var/log/update_script.log. Create a scheduled task for this script once a week at 4 AM and every time the machine reboots.
Resource:
A command for setting systemwide cron tasks:
sudo crontab -e
#!bin/bash
#
# Updates all source packages. Log saved to /var/log/update_script.log
sudo echo "--------------------------" >> /var/log/update_script.log
sudo echo "Date $(date)" >> /var/log/update_script.log
sudo apt-get update -y >> /var/log/update_script.log
sudo apt-get upgrade -y >> /var/log/update_script.log
echo "--------------------------" >> /var/log/update_script.log
Different commands for Cron:
| Command | Description |
|---|---|
crontab -e |
Edits crontab entries to add, delete, or edit cron jobs |
crontab -l |
List all the cron jobs for the current user. |
crontab -u username -e |
Edit another user's crons |
Make a script to monitor changes of the /etc/crontab file and sends an email to the root if it has been modified. Create a scheduled script task every day at midnight.
Resources:
Setting up local mail delivery on Ubuntu
How to Create a Simple Login Page Using HTML and CSS
Resource:
How To Create a Self-Signed SSL Certificate for Apache in Debian 10 | DigitalOcean