两个月没更,主要为了西部计划和三支一扶,估计都要寄,害,无所谓了
openssl & bison & flex & libpcap & python-requests needed(maybe)
sqlmap needed
iptables or firewalld needed
rustup toolchain install nightly
make sure that you've been able to connect to the bak_server by ssh-key before using the restore module
This is a graduation project from School of Computer Science of THNU
Not yet completed, under development
Preliminary development completed 2023.02.18
Will be updated irregularly 2023.04.04
- 100%做到中英双语(注释)
- README.md
- main.rs
- 获取日期··········································································2023.04.06
- 获取时间··········································································2023.04.06
- 获取CPU负载·······································································2023.04.06
- 获取内存占用······································································2023.04.08
- 获取磁盘响应时间···································································2023.04.07
- 获取上传带宽占用···································································2023.04.08
- 获取下载带宽占用···································································2023.04.08
- 简单webshell检测··································································2023.07.03
- 备份·············································································2023.07.03
- 恢复·············································································2023.07.03
- 端口扫描、sql注入点检测、xss注入点检测··············································2023.07.03
- DOS类攻击检测
- 输出系统监测信息···································································2023.07.03
- 获取IP地址表······································································2023.05.12
- 解析IP地址表······································································2023.05.15
- 尽量剔除第三方功能实现,如py、shell等
- 获取日期··········································································2023.04.06
- 获取时间··········································································2023.04.06
- 获取CPU负载·······································································2023.04.06
- 获取内存占用······································································2023.04.08
- 获取磁盘响应时间···································································2023.04.07
- 获取上传带宽占用···································································2023.04.08
- 获取下载带宽占用···································································2023.04.08
- 简单webshell检测 尝试用rust重写检测函数,始终有问题,无法检测,也不报错
- 备份
- 恢复
- 端口扫描
- sql注入点检测
- xss注入点检测
- 获取IP地址表······································································2023.05.12
- 解析IP地址表······································································2023.05.15
- 恶意IP的记录/邮件,要加上国家或地区字段
- 自动反击需要规定反击程序的运行时间
- 监控信息获取时多线程运行,减少信息时间差
- 识别IP:境外自动反击+邮件,境内(含港澳台)与私有仅邮件,要求在邮件及数据库中写入对应的地区代码
- 备份过程加密传输 ssh
- 可指定时区,通过配置config文件实现
- 守护进程·············································································2023.02.18
- 写入数据库···········································································2023.02.17
- 优化反击模块·········································································2023.02.17
- 在响应记录数据库中,写入ban掉的ip及当时日期时间,手动恢复日期时间,手动反击日期时间目标ip···2023.02.17
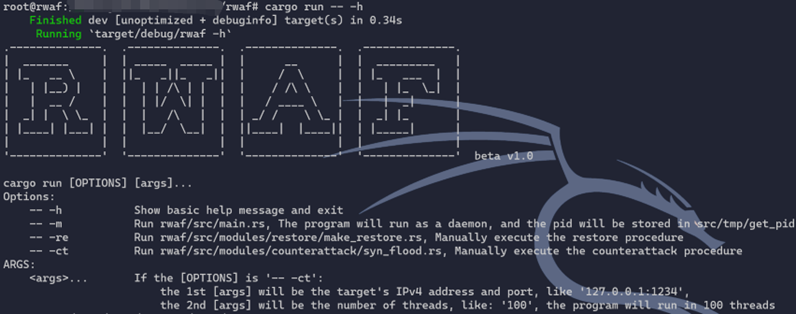
cargo run [OPTIONS] <args>...
Options:
-- -h Show basic help message and exit
-- -m Run rwaf/src/main.rs, and the pid will be stored in src/tmp/get_pid
-- -re Run rwaf/src/modules/restore/make_restore.rs, Manually execute the restore procedure
-- -ct Run rwaf/src/modules/counterattack/syn_flood.rs, Manually execute the counterattack procedure
ARGS:
<args>... If the [OPTIONS] is '-- -ct':
the 1st [args] will be the target's IPv4 address and port, like '127.0.0.1:1234',
the 2nd [args] will be the number of threads, like: '100', the program will run in 100 threads
cargo run -- -h