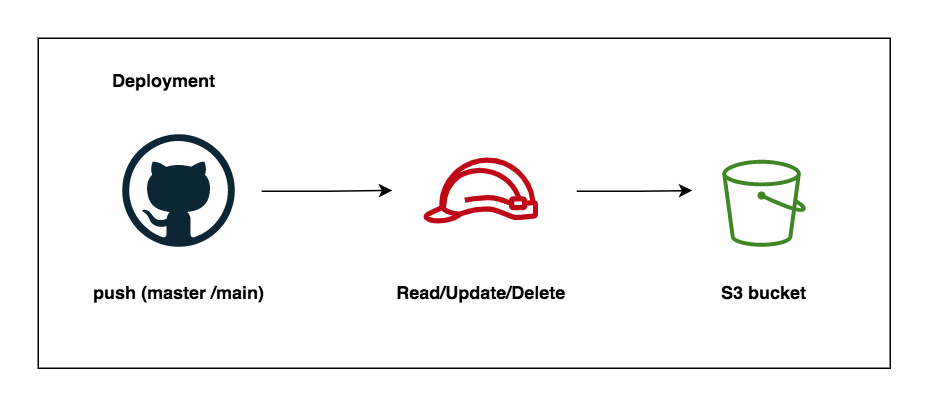
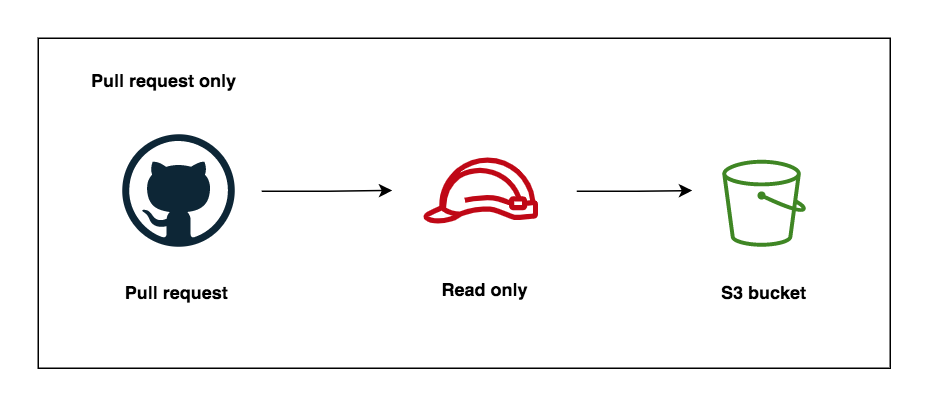
This is an example of Github Actions deployment to AWS with OpenID connect (OIDC) using terraform.
Building on our example. We address a few problems related to permissions where it works for all workflows (pull requests, all branches and forks).
We want more granularity, which is what we are doing here.
So, there are a few things we need to change:
- Create Separate the IAM roles (one for pull request, and deployment)
- Update our Subject filter and the condition operators
- Separate github actions workflows (pull request and deployment)
Full article available at jerrychang.ca - Security harden Github Action deployments to AWS with OIDC