| page_type | languages | products | name | urlFragment | description | ||||
|---|---|---|---|---|---|---|---|---|---|
sample |
|
|
Enable your Blazor Server app to sign-in users and call APIs with the Microsoft identity platform |
ms-identity-blazor-server |
This sample demonstrates how to enable your Blazor Server to sign-in users and call APIs with the Microsoft identity platform |
Tutorial: Enable your Blazor Server app to sign-in users and call APIs with the Microsoft identity platform
The Microsoft identity platform, along with Azure Active Directory (Azure AD) and Azure Azure Active Directory B2C (Azure AD B2C) are central to the Azure cloud ecosystem. This tutorial aims to take you through the fundamentals of enabling modern authentication for an ASP.NET Core Blazor Server, using the Microsoft Authentication Library and Microsoft.Identity.Web.
⚠️ This is a work in progress. Come back frequently to discover more samples.
- Either Visual Studio or Visual Studio Code
Please refer to each sample's README for sample-specific prerequisites.
- jwt.ms for inspecting your tokens.
- Fiddler for monitoring your network activity and troubleshooting.
- Follow the Azure AD Blog to stay up-to-date with the latest developments.
From your shell or command line:
git clone https://github.com/Azure-Samples/ms-identity-blazor-server.gitor download and extract the repository .zip file.
Please refer to each sample's README for sample-specific recommendations.
We recommend following the chapters in successive order. However, the code samples are self-contained, so feel free to pick samples by topics that you may need at the moment.
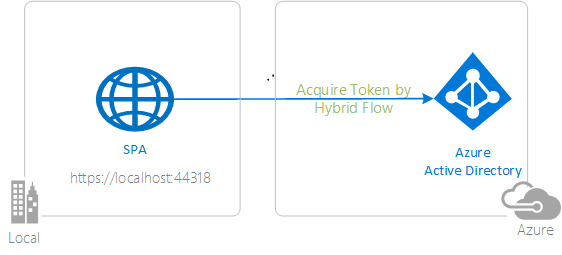 |
Sign-in with Azure AD Sign-in your users with the Microsoft Identity platform and learn to work with ID tokens. |
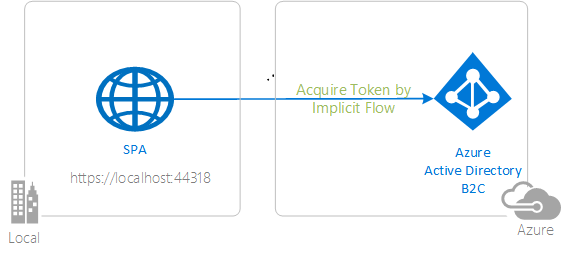 |
Sign-in with Azure AD B2C Sign-in your customers with Azure AD B2C. Learn to integrate with external social identity providers. Learn how to use user-flows and custom policies. |
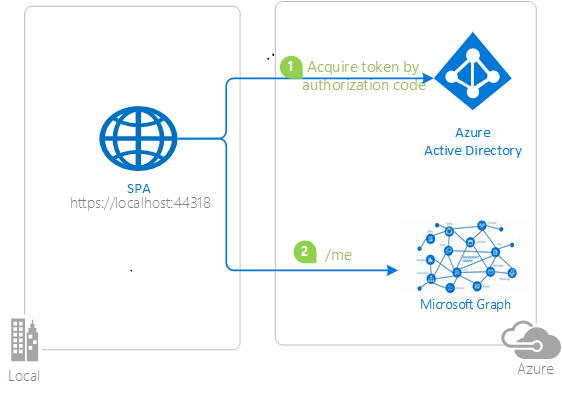 |
Acquire an Access Token from Azure AD and call Microsoft Graph Here we build on the concepts we built to authenticate users to further acquire an Access Token for Microsoft Graph and then call the Microsoft Graph API. |
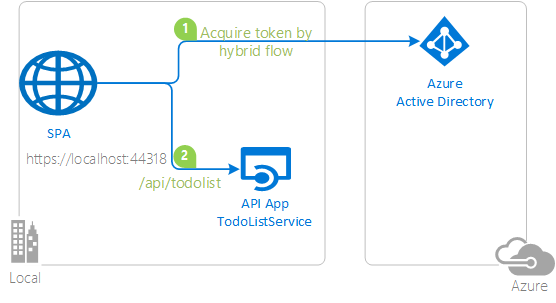 |
Protect and call a web API on Azure AD Protect your web API with the Azure AD. Use a client application to sign-in a user, acquire an Access Token for your web API and call your protected Web API. |
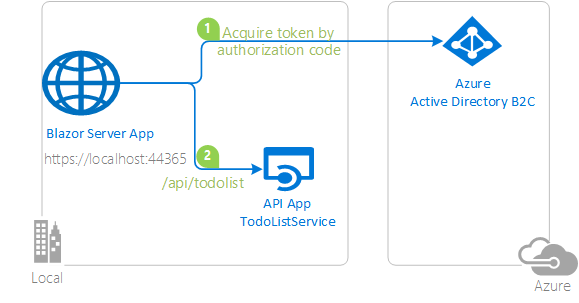 |
Protect and call a web API on Azure AD B2C Protect your web API with the Azure AD B2C. Sign-in a user using a client application, acquire an Access Token for your web API and call your protected Web API. |
 |
Deploy to Azure App Services Finally, we prepare your app for deployment to various Azure services. Learn how to package and upload files, Configure authentication parameters and use the various Azure services for managing your operations. |
Were we successful in addressing your learning objective? Do consider taking a moment to share your experience with us.
Learn more about the Microsoft identity platform:
- Microsoft identity platform
- Azure Active Directory B2C
- Overview of Microsoft Authentication Library (MSAL)
- Application types for Microsoft identity platform
- Understanding Azure AD application consent experiences
- Understand user and admin consent
- Application and service principal objects in Azure Active Directory
- Microsoft identity platform best practices and recommendations
See more code samples:
Use Stack Overflow to get support from the community.
Ask your questions on Stack Overflow first and browse existing issues to see if someone has asked your question before.
Make sure that your questions or comments are tagged with [azure-active-directory azure-ad-b2c ms-identity msal].
If you find a bug in the sample, raise the issue on GitHub Issues.
To provide feedback on or suggest features for Azure Active Directory, visit User Voice page.
If you'd like to contribute to this sample, see CONTRIBUTING.MD.
This project has adopted the Microsoft Open Source Code of Conduct. For more information, see the Code of Conduct FAQ or contact opencode@microsoft.com with any additional questions or comments.
This project has adopted the Microsoft Open Source Code of Conduct. For more information see the Code of Conduct FAQ or contact opencode@microsoft.com with any additional questions or comments.