With regard to the latest developments in the ISO/IEEE 11073 service-oriented device connectivity (SDC) its important to not leave possible security and safety risks of this new communication protocol out of consideration. Therefore the basic idea of this project (carried out during the author's bachelor thesis) was to improve the security as well as the safety of sdc connected medical devices with ML based anomaly detection.
The concept is illustrated in the following chart:

The necessary dependencies are listed in requirements.txt: use pip install -r requirements.txt to install all suitable versions.
Additionally wireshark or rather tshark has to be installed and added to the system path.
- code is based on the paper and implementation
- similiar project but blockchain based can be found here
- Survey of Network Intrusion Detection Methods from the Perspective of the Knowledge Discovery in Databases Process
- SOME/IP Intrusion Detection using Deep Learning-based Sequential Models in Automotive Ethernet Networks
- SOME/IP is automotive equivalente for service oriented communication
- Recurrent Neural Network
- synthetical dataset generator
- supervised learning, therefore not able to detect new unknown attacks
- A Distributed Multi-Approach Intrusion Detection System for Web Services
- static and dynamic anomaly detection (Hidden Markov Model)
- lightway NIDS that works directly on web servers
- system only inspects the payload (soap messages)
- A Method for Intrusion Detection in Web Services Based on Time Series
- statistical model predicts the range of coming soap message sizes
- if actual soap message size is out of this range its considered as an anomaly
- only one feature: soap message size
- Federated Learning for Internet of Things: A Federated Learning Framework for On-device Anomaly Data Detection
- Deep Autoencoders
- Framework to test it on a Raspberry Pi or Nvidia Jetson Nano
- An Intrusion Detection System for Internet of Medical Things
- polynomal regression on physiological sensor data to predict next datapoints
- if actual sensor data highly deviates from the predicted one it gets considered as anomaly
- model gets executed in distributed manner
- On Generating Network Traffic Datasets with Synthetic Attacks for Intrusion Detection
- code can be found here
- comparison of different packet crafting and sniffing libraries can be found here
- faster alternative to pyshark: Packet capture on Windows without a kernel driver
- different open source implementations of the ISO/IEEE 11073 SDC
offline and online NIDS
- run
NIDS_offline.pyto train and execute the model on a dataset - run
NIDS_online.pyto train the model on a trainingset and execute it on live captured data Kitsune.pyspecifies the training and execution structure of the model which is defined inKitNET
Tuning hyperparameter
hyperparaTune.pyis based on the library hyperopt which uses Bayesian optimization
Adjusting features
FeatureExtractor.py: uses scapy or tshark under the hood to extract meta data like srcIP, dstIP, etc. from the packetsnetStat.py: uses the extracted meta data to calculate statistical featuresAfterImage.py: is used to calculate basic statistical features
Synthetical data generation (data_sdc11073)
fictEnvironments.pyinitializes different clients and a provider (specified inmdib_OPtable.xml) as well as the communication between them- run
dataGen.pyto capture the data transmitted between clients and providers - the saved file can be labeld in
dataLabeling.pyto evaluate the model later
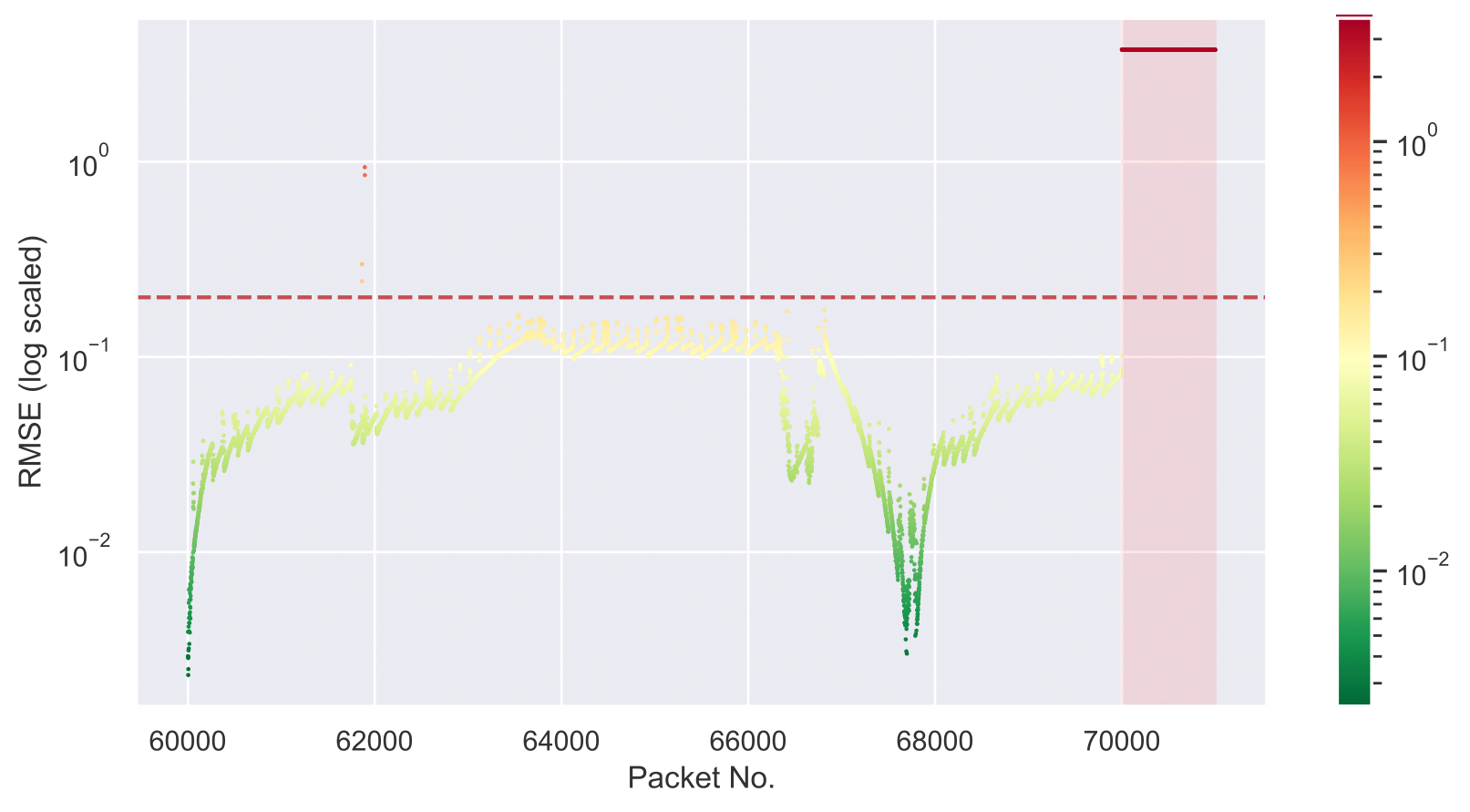
Root Mean Square Error and Threshold
Denial of Service Attack
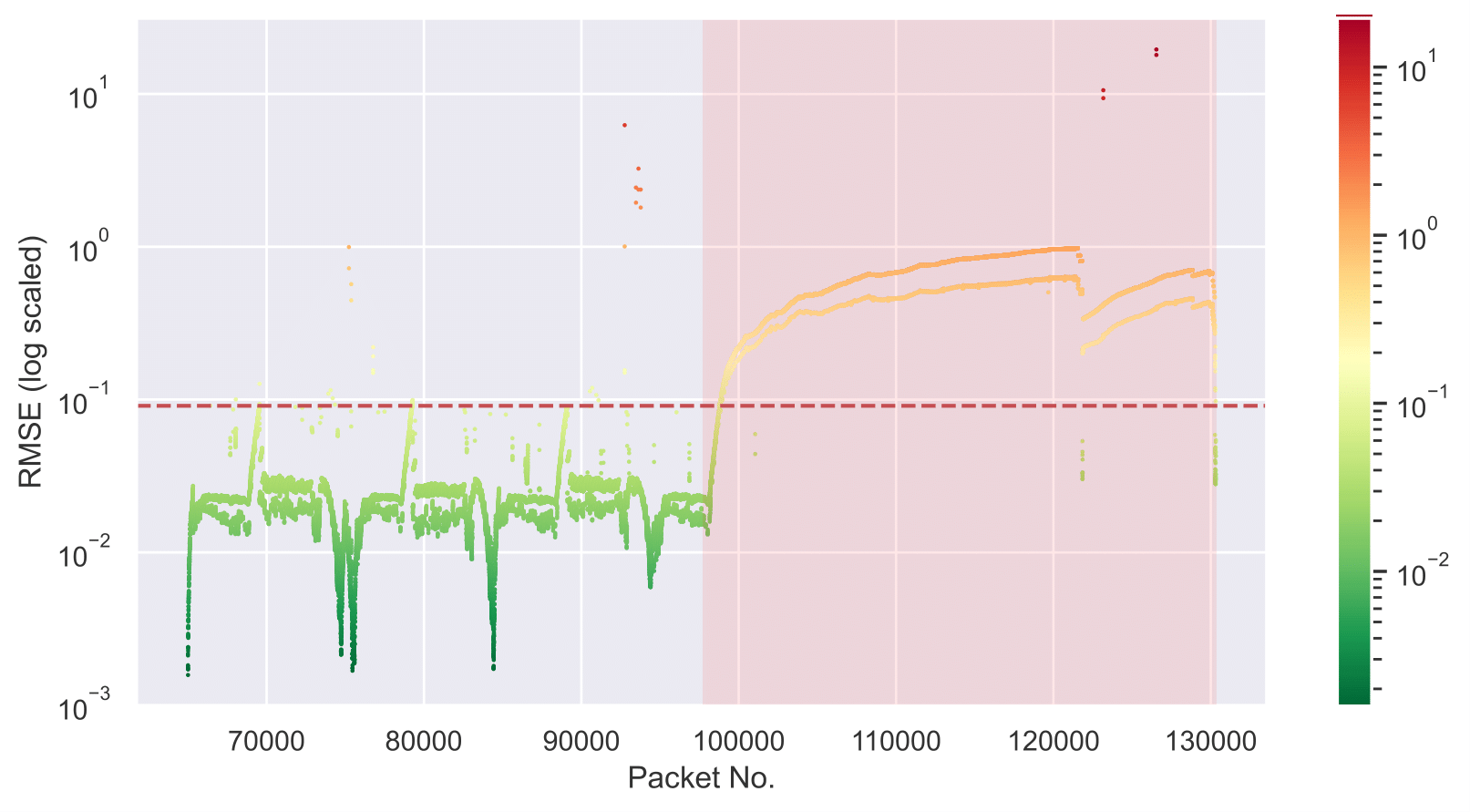 Portscan Attack
Portscan Attack
Metrics, runtime and required resources
| Metrics | Denial of Service Attack | Portscan Attack |
|---|---|---|
| TPR | 0.9952 | 0.9990 |
| FPR | 0.0019 | 0.0004 |
| F-Score | 0.9966 | 0.9975 |
- runtime (on CPU): 469 Pakets/s
- resources: 152 MB
For limitations and further improvements, see TODO.txt