-
View help information
#python3 Night_of_19.py -h
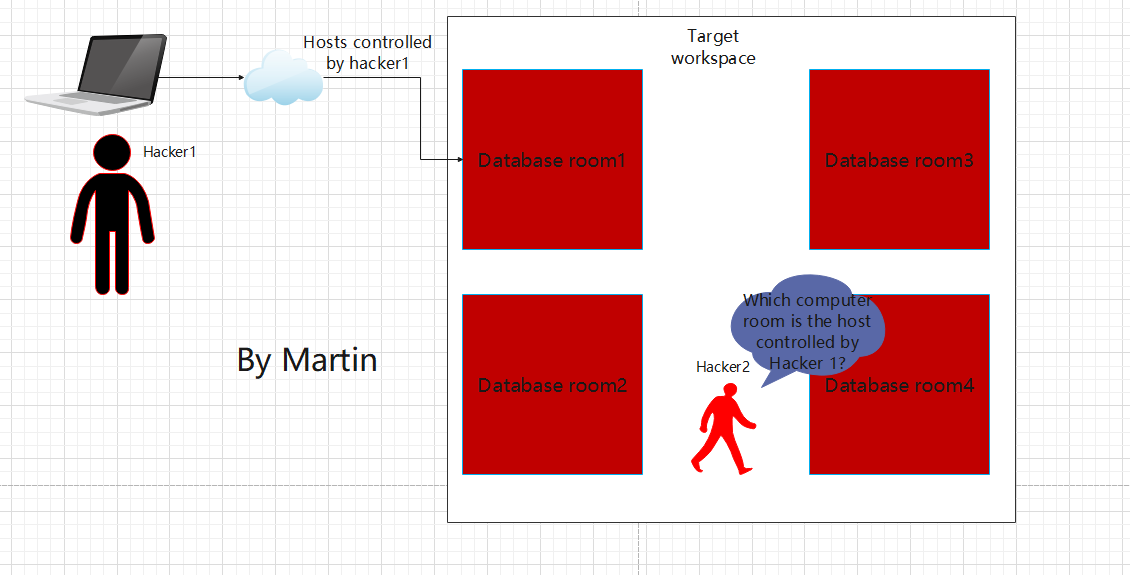
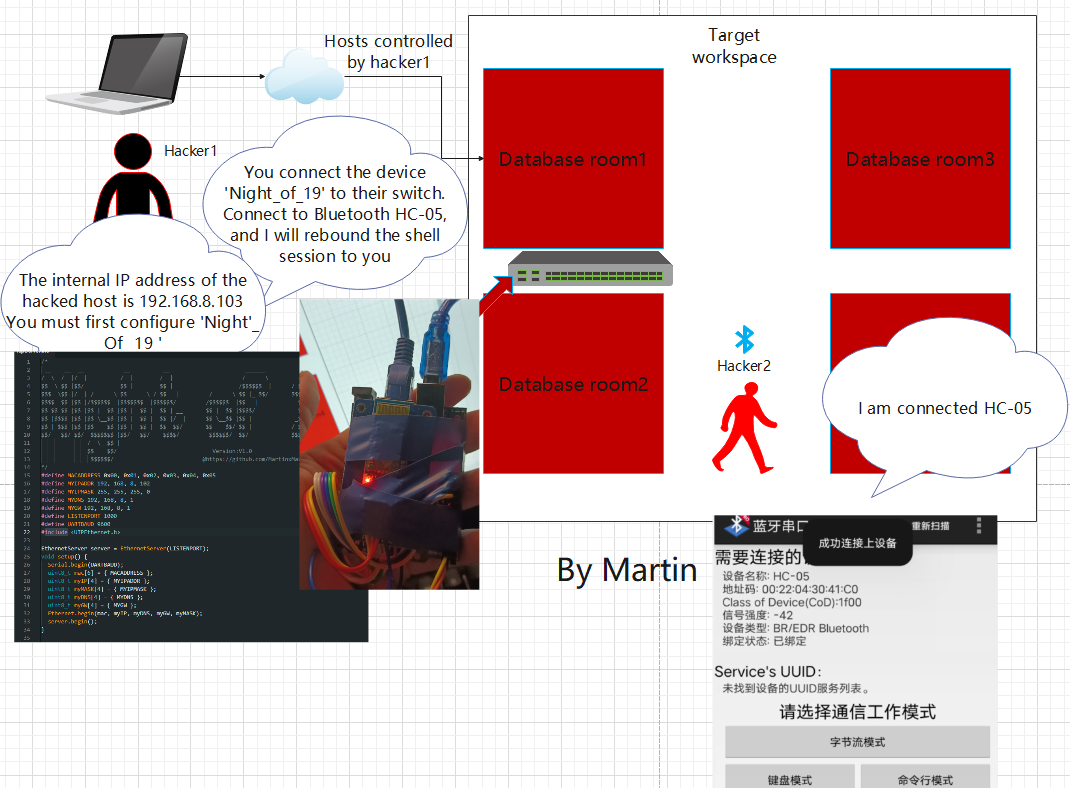
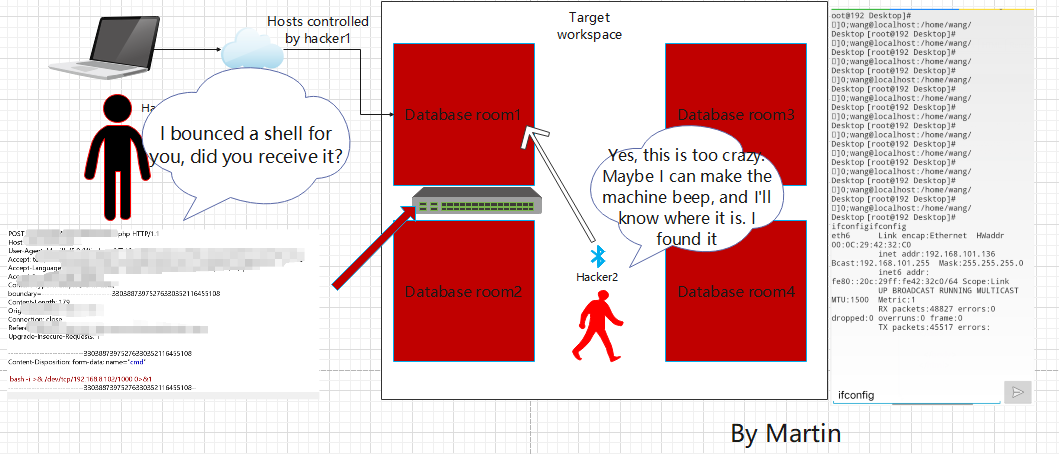
We will play the role of hacker perspective, as Hacker 1 and Hacker 2 are preparing to infiltrate the company offline. Due to the large number of target computer rooms, it is currently unclear which machine was hacked. What should we do?