BoopSuite is an up and coming suite of wireless tools designed to be easy to use and powerful in scope, that support both the 2 and 5 GHz spectrums. Written purely in python. A handshake sniffer (CLI and GUI), a monitor mode enabling script and a deauth script are all parts of this suite with more to come.
The sniffer is easier to use, and has a more targeted approach. Capture Handshakes, no frills.
The script is just as easy to use and quite a bit faster in its method of putting cards into monitor mode. With as much usability as well.
While boopstrike can't compare to aireplay-ng due to the amount of options present in it. BoopStrike can compare to Dan McInerney's wifijammer script as boopstrike accomplishes the same things, albeit with more grace. This script wont waste deauths on noiseless clients, but will surely jam those that are using their respective wifi's, also my tool supports the 5ghz frequency if you have a card that can do so.
Don't mistake me, aircrack is an amazing suite of tools and I understand the thought of "why use a different tool when you know airodump", and the answer is because you have the freedom to do so and I hope my project can aid everyone in their pentesting needs, and this project is going to continue to grow as I add new handlers for additional packet types.
The project has a CLI and GUI handshake sniffer, a monitor mode enabling script, and a deauthentication script!
Changelog located in CHANGELOG file.
Hopefully others find it useful. If you do please email me and let me know I would love to hear about it.
I am going to add scripts to do the following:
- BoopCoil - Deauth attack detector
- BoopDate - A script to update boopsuite
More ideas are welcome. Email me @: jacobsin1996@gmail.com
boopsniff -i wlan1mon
boopsniff -i wlan1mon -c 6
boopsniff -i wlan1mon -f 5
boopsniff -i wlan1mon -k
boopsniff -i wlan1mon -u
boopsniff -i wlan1mon -a xx:xx:xx:xx:xx:xx
boopstrike -i wlan1mon
boopstrike -i wlan1mon -f 5
boopstrike -i wlan1mon -a xx:xx:xx:xx:xx:xx
boopstrike -i wlan1mon -s xx:xx:xx:xx:xx:xx
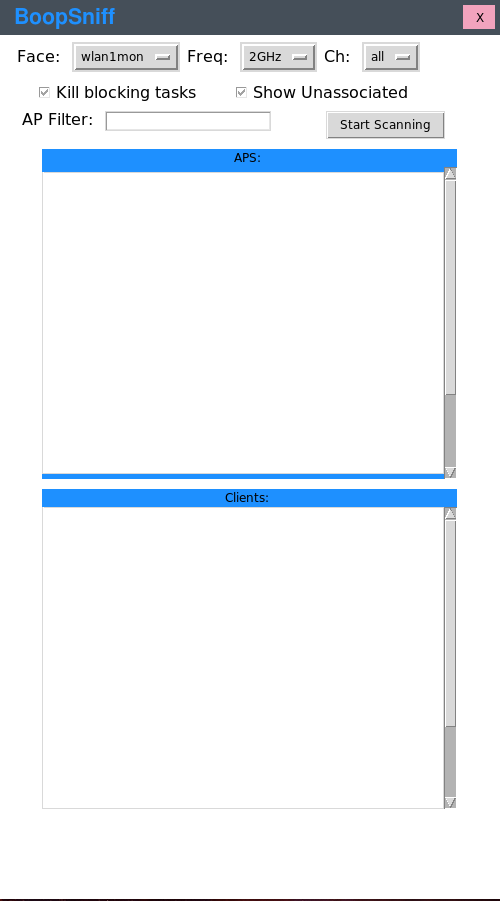
boopsniff_gui
boop -i wlan1
boop -i wlan1mon
boop -i wlan1 -n boop1
note: will enable or disable monitor mode accordingly.
boop -i wlan1 -c 11
Note: Will do error checking if you specify a channel the card doesnt support and is ready for cards supporting the 5GHz network.
boop -i wlan1 -k
boop -i wlan1 -n boop1 -c 11 -k
NOTE: boop will always switch the mode from managed to monitor and vice versa.
I'm working on updating the GUI so it will be much cleaner and way better looking, stay tuned.
Note: all pcap files will be saved in the directory ~/pcaps
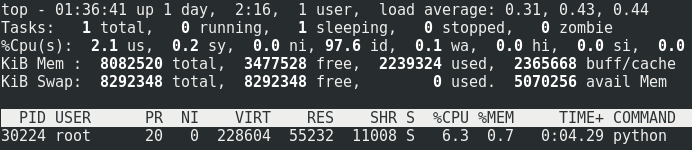
The sniffer which is the heaviest CPU part uses really low CPU and memory, memory which is going to shrink in upcoming versions.
git clone https://github.com/M1ND-B3ND3R/BoopSuite.git
cd BoopSuite
pip install -r requirements.txt
chmod +x install.py
./install.py
The setup includes creating symbolic links for the tool so it can be run from anywhere.
Root is dangerous so always check packages before running them as root. My code is not malicious, however, you should always be wary.
git clone https://github.com/M1ND-B3ND3R/BoopSuite.git
cd BoopSuite
chmod +x install.py
./install.py
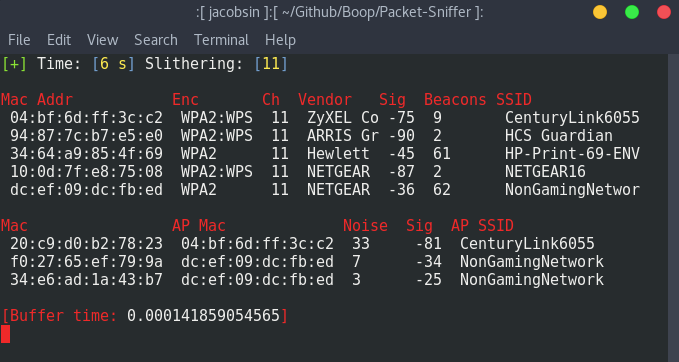
The top line is formatted as follows for the sniffer:
[+] Time: TIME_ELAPSED Slithering: [CHANNEL] - [boopstrike: RECENT HANDHAKE CAPTURED] - [AMOUNT OF HANDSHAKES]
Next line is the start of the Access Point table and is formatted as follows:
[Mac address] [Encryption] [Channel] [Vendor] [Signal] [Beacons] [SSID]
The Line that starts the client table is formatted as follows:
[Mac address] [AP Mac address] [Noise] [Signal] [AP SSID]
- M1ND-B3ND3R
- Sean Bangerter - Proofing my readme
- Boop - My pet ball python
I am motivated by the want to be better. To prove others wrong and to prove to myself that I can do things that were previously impossible to me.
-
Wireless card discovery in VM for kali.
-
Code Fixes will be happening.
MIT License