Adhrit is an open source Android APK reversing and analysis suite. The tool is an effort to find an efficient solution to all the needs of mobile security testing and automation. Adhrit has been built with a focus on flexibility and mudularization. Adhrit currently uses the Ghera benchmarks to identify vulnerability patterns in Android applications. The project is subject to continuous updations and will incorporate the latest available methodologies and tools. Adhrit has been presented at conferences like OWASP Seasides, ThreatCon and Cysinfo. Feature requests and bug reports are always welcome!
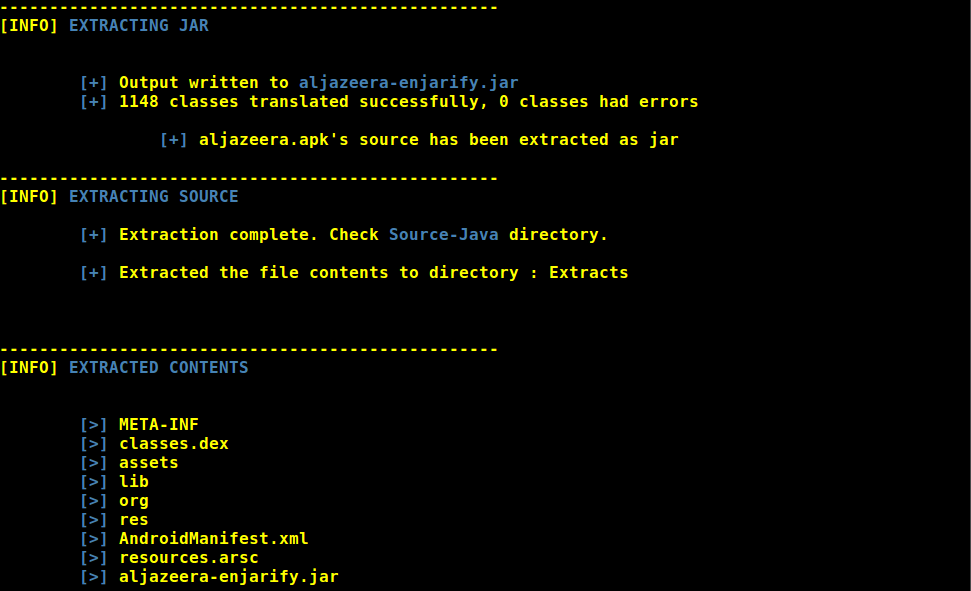
-
- assets
- classes.dex
- native libraries
- jar file from dex (integrated Enjarify)
-
- Certificate/signature
- Java source
- smali source
- Parsed XML resource files
- Parsed AndroidManifest
- Native library
-
-
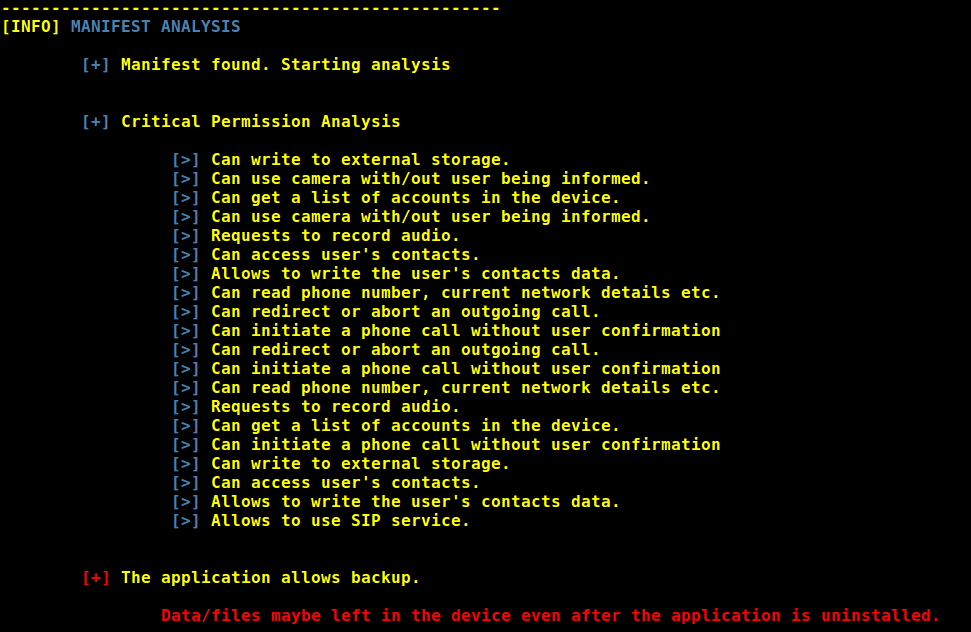
Manifest analysis
- Critical permission usage analysis
- MainActivity identification
- Backup status
- Exported activities
- Exported broadcast receivers
- Identify intent filters
- Identify embedded deeplinks
- Automated ADB payload generation for exported activities
-
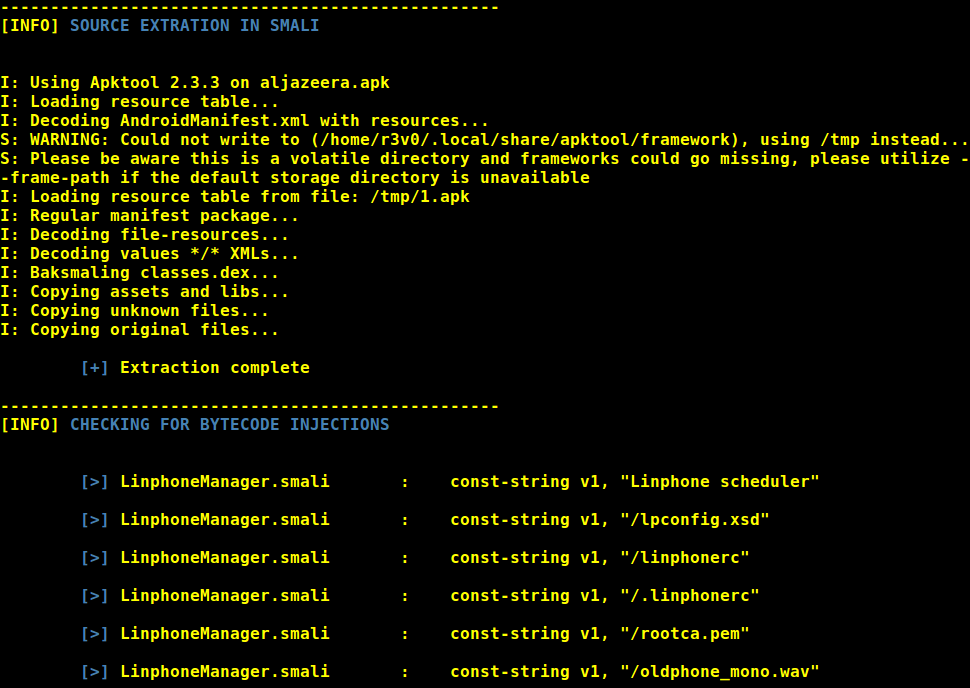
Bytecode analysis
-
ICC
- Dynamic Broadcast Receivers
- Empty Pending Intents
- Sticky Broadcasts
- Unprotected Broadcast Receivers
- Weak Dynamic Invocation Checks
-
Web Issues
- JavaScript Execution in WebViews
- HTTP Connections
- Unsafe Intent URL Resolving Implementation
- Overwritable Cookie
- File Access from URLs
- Content Provider Access from URLs
- Supressed SSL Warnings
-
Storage Issues
- Non-parameterized SQL queries
- Usage of External Storage for application data
-
Networking
- Missing Server Certificate Validity Check
- Insecure SSL Socket Factory
-
Crypto Issues
- Usage of ECB Block Cipher
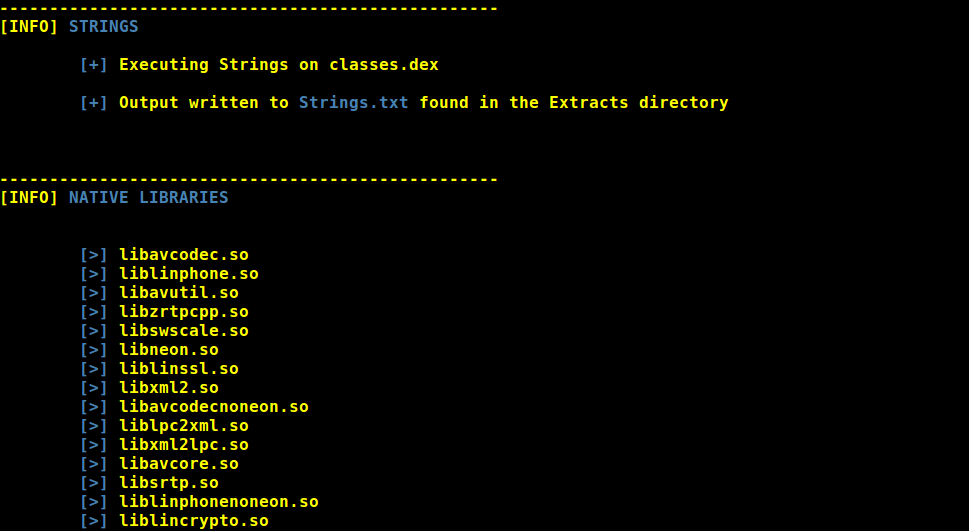
-
const-strings
-
CTF flags
-
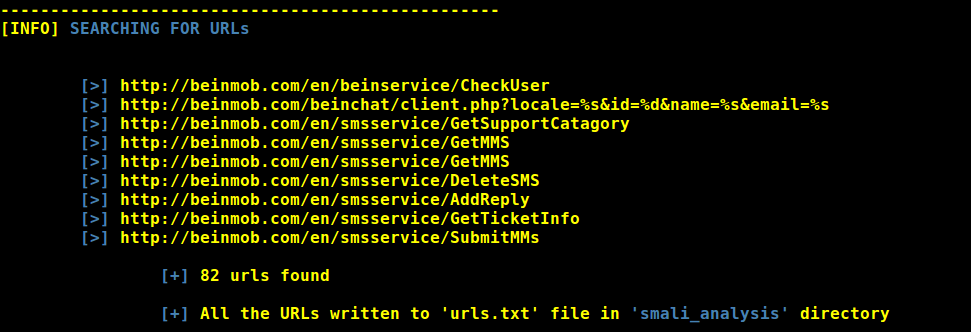
URLs
-
-
Native Library analysis
- Library info
- Sections
- Base64 Decoding of strings from .data
-
-
- Rebuilding the APK
- Signing the APK
- Linux or MAC
- Python3
- Java JDK
- Dowload the zip or clone the package and extract the tool (
git clone https://github.com/abhi-r3v0/Adhrit.git). - Open
configand input your VirusTotal API key without any quotes. (Click here to know how to obtain your VT API key) - Open a terminal and cd into the directory.
- Run the
installer scriptto install the necessary tools/dependencies:python3 installer.py
- Place the application (apk file) in the tool directory.
- Use
python3 adhrit.py -hfor usage help.
Example:
python3 adhrit.py -a myapp.apkpython3 adhrit.py -pen myapp.apkRefer to the detailed documentation for complete details
- Abhishek J M (jmabhishek4@gmail.com, @HawkSpawn)
- P S Narayanan (thepsnarayanan@gmail.com, @0xP5N_)
- Akhil Mahendra (akhilmahendra7991@gmail.com, @Akhil_Mahendra)
- Heeraj Nair (heeraj123@gmail.com, @heerajnair)
- Vaisakh (vaisakhjnr@gmail.com, @vaisakhjnr) (new)
- Loyd Jayme (loydjayme1996@gmail.com, @loydjayme25)
- Troopers
- Seclist
- DedSec
- Neonix
- Howucan.gr
- HackerTor
- tuicool
- Tuisec
- @androidtools on Twitter
- pcbbc
- Ethical Hacking Consultants
- Anonymoushacker
- Pax0r
- KitPloit
- ISEC
- Prodefence
- appscan.io
- Weixin
- blackhatsecdevteam
- 360doc
- Hackers Online Club
- Altervista
- Xaunwulab
- Prodefense
- Digital Munition
- Xenicom
- Filenames with two '.' may give an error. Please rename the apk in such cases.
For example, if your file name is
my.app.apk, rename it tomyapp.apk