API key based Authentication package for FastAPI, focused on simplicity and ease of use:
- Full functionality out of the box, no configuration required
- API key security with local
sqliteorpostgresdatabase backend, working with both header and query parameters - Default 15 days deprecation for generated API keys
- Key creation, revocation, renewing, and usage logs handled through administrator endpoints
- Username, Email address and password(hashing + salting) verification features.
- Lightweight, minimal dependencies required.
- Added partial support for mongodb database backend.
- Added support for environment variables through .env files.
- Added
example.envfile to show how to use environment variables. - Updated
README.mdto reflect changes. - Updated documentation to reflect changes.
- Working on adding support for
mysqldatabase backend.
pip install fastapi_auth2
from fastapi import Depends, FastAPI
from fastapi_auth import api_key_router, api_key_security
app = FastAPI(
description="FastAPI Auth is a package that provides authentication based API security with FastAPI and Postgres Database, SQLite Database or MongoDB Database",
title="FastAPI Auth Example",
version=1.0,
)
app.include_router(api_key_router, prefix="/auth", tags=["_auth"])
@app.get("/unsecure")
async def unsecure_endpoint():
return {"message": "This is a unsecure endpoint"}
@app.get("/secure", dependencies=[Depends(api_key_security)])
async def secure_endpoint():
return {"message": "This is a secure endpoint"}Resulting app is:
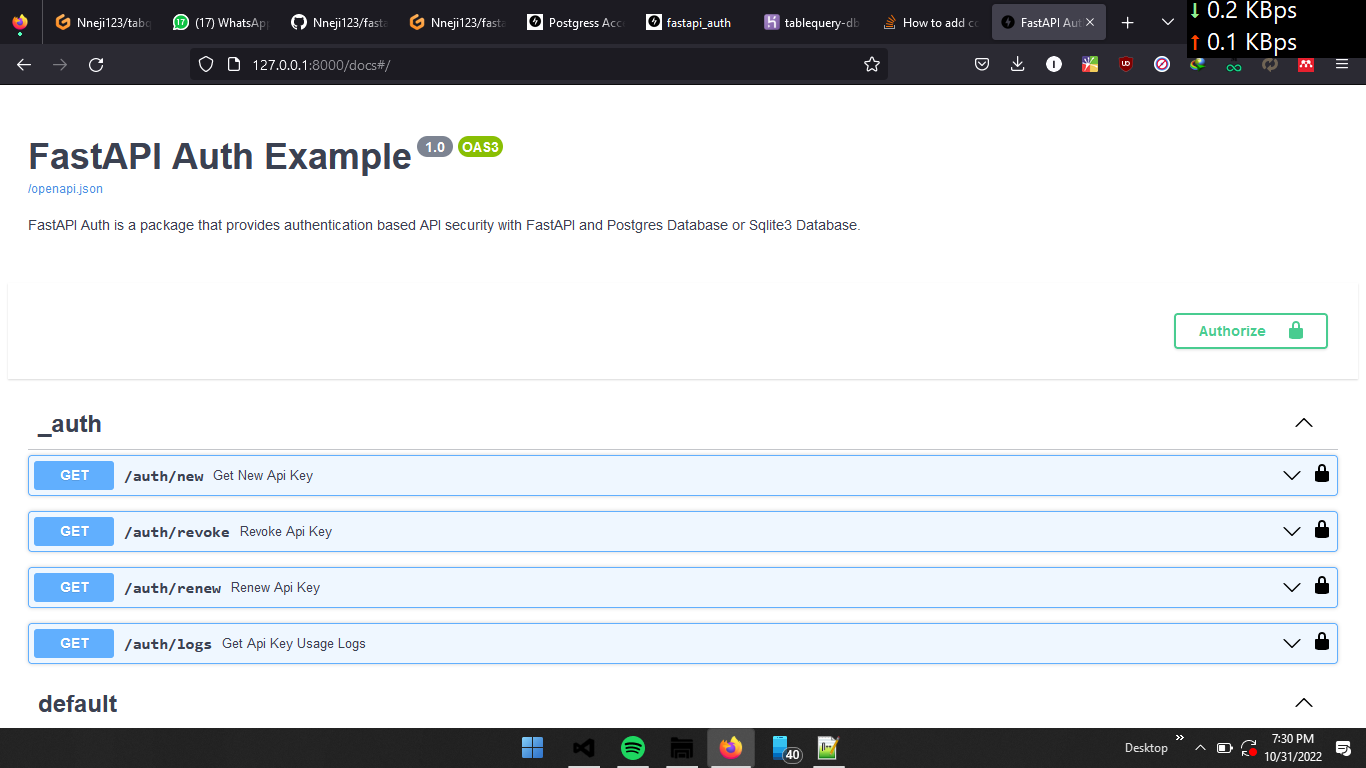
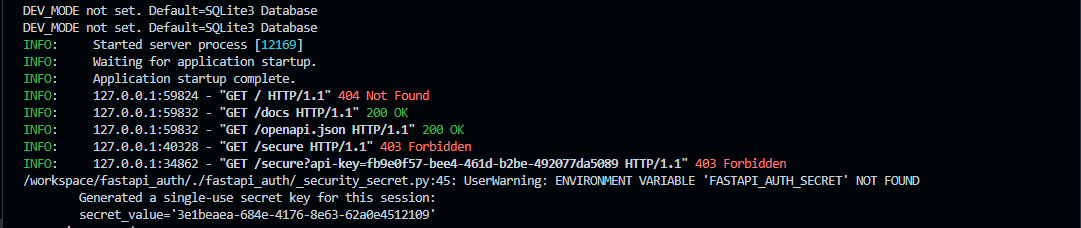
Start your API and check the logs for the automatically generated secret key if you did not provide one through environment variables.
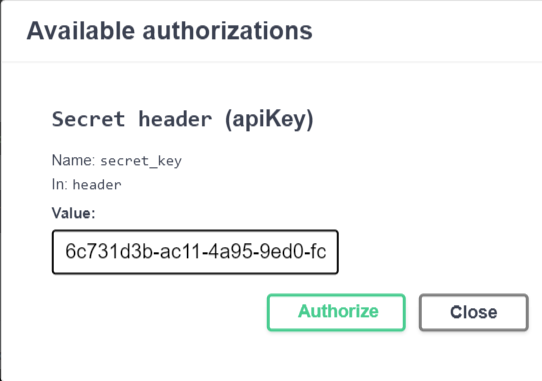
Go to /docs on your API and inform this secret key in the Authorize/Secret header box.
All the administrator endpoints only support header security to make sure the secret key is not inadvertently
shared when sharing an URL.
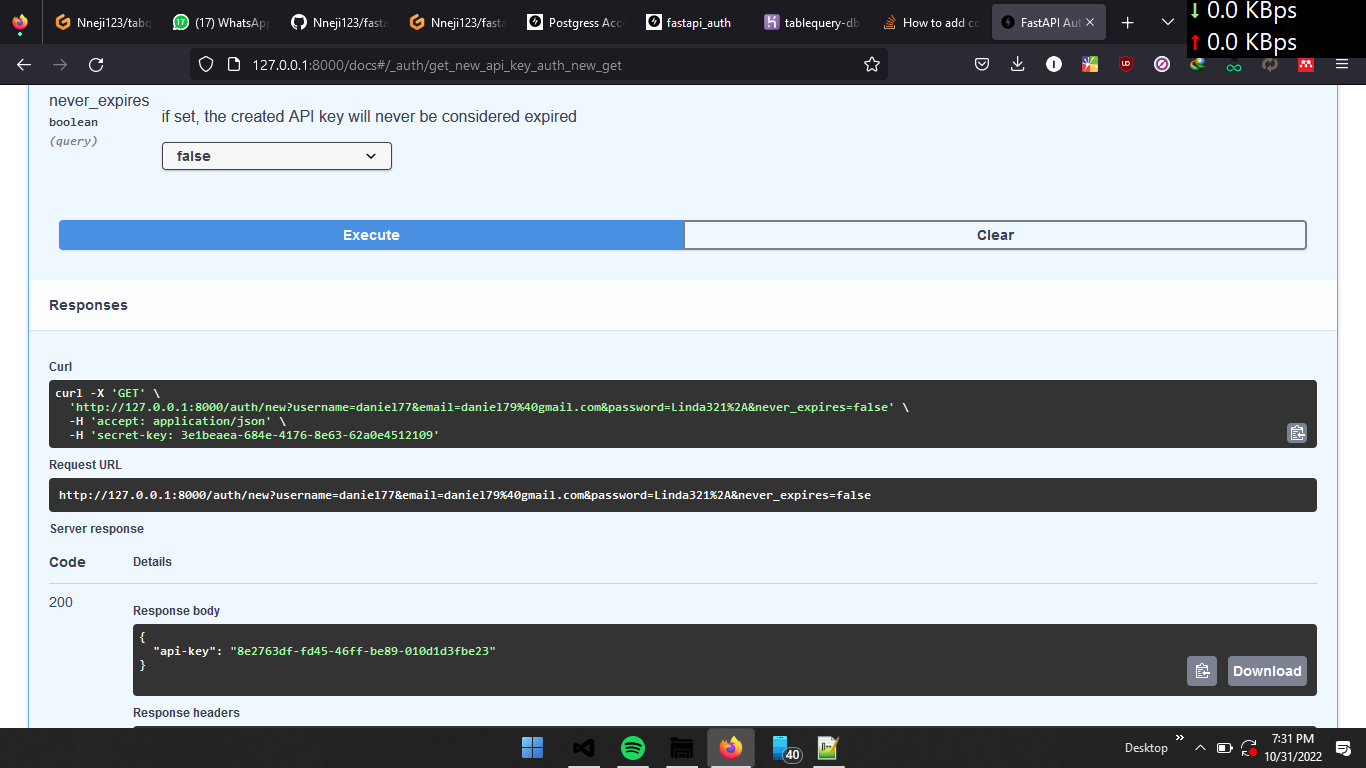
Then, you can use /auth/new to generate a new API key.
And finally, you can use this API key to access the secure endpoint.
You can of course automate API key acquisition through python with requests and directly querying the endpoints.
If you do so, you can hide the endpoints from your API documentation with the environment variable
FASTAPI_AUTH_HIDE_DOCS.
Environment variables:
-
FASTAPI_AUTH_SECRET: Secret administrator key- Generated automatically on server startup if not provided
- Allows generation of new API keys, revoking of existing ones, and API key usage view
- It being compromised compromises the security of the API
-
FASTAPI_AUTH_HIDE_DOCS: Whether or not to hide the API key related endpoints from the documentation -
FASTAPI_AUTH_DB_LOCATION: Location of the local sqlite database filesqlite.dbin the running directory by default- When running the app inside Docker, use a bind mount for persistence
-
FASTAPI_AUTH_AUTOMATIC_EXPIRATION: Duration, in days, until an API key is deemed expired- 15 days by default
-
DATABASE_MODE: If set topostgres, the package will use a postgres database instead of sqlite -
URI: Location of the postgres databasepostgresql://postgres:postgres@localhost:5432/postgresby default- Only used if
DEV_MODEis set toFalse
See CONTIBUTING.md for more information.
poetry install
poetry shellpre-commit installpytestThe attached docker image runs a test app on localhost:8080 with secret key TEST_SECRET. Run it with:
docker-compose build && docker-compose up- Add more tests
- Add more database backends
- Add more authentication methods