Here you find several examples of Log Entry Query Language (LEQL) queries used by the rapid7 SIEM to fine tune their searches. 👽
Attention: This is an independent and voluntary tutorial and all the information described here can be studied and deepened at Rapid7 InsightIDR.
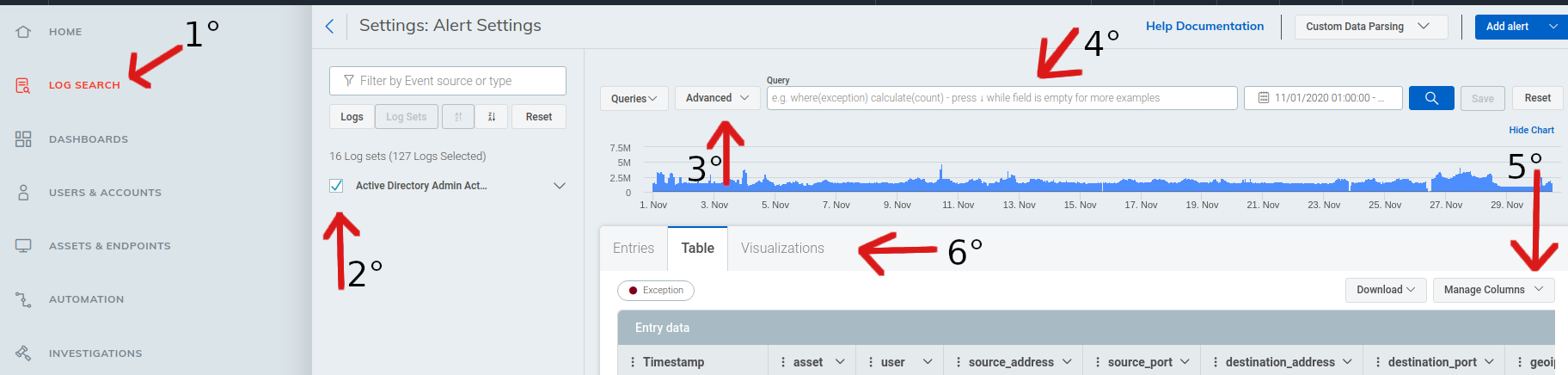
On InsightIDR home screen click on "Log Search" to access the SIEM queries screen.
This part allows you to select the servers whose logs are being
collected, this is interesting to fine-tune your searches, for example:
only AD logs and not firewalls.
In order to use advanced queries in Log Search you
must select the query type as advanced.
Here you must enter the desired query, note that the query must have
the appropriate environment information, for example login name of
the target user if this is what you are looking for.
Note: You must set the time window on the right side to get the desired logs.
At this stage, you should already have the result of your query and by
clicking on "Manage Columns" you can define the view only the
columns of your interest.
After your query is ready you can use this function to view and create graphs of various types , for example:
- Pie Chart
- Bar Chart
- Horizontal Bar Chart
where(source_user="grp adm" action="ACCOUNT_DISABLED")
where(source_user="grp adm" action="ACCOUNT_DISABLED") calculate(count)
where(asset="iphone_of_siem")
where(4725)
where(client_mac="11:22:33:aa:bb:cc")
destination_account="alice.winchester"
where("192.168.1.1")
where(source_ip="192.168.1.1")
Or
where(source_address="192.168.1.1")
where(destination_ip="192.168.1.1")
Or
where(destination_address="192.168.1.1")
where(source_port="22")
where(destination_port="443")
where(http_method="get")
where(http_method="post")
where(url="https://google.com/")
where(url_host="google.com")
where(direction="OUTBOUND")
where(direction="INTERNAL")
where(/Alice (?P<VARIABLE>\s*)/ )
where(/@domain.com/)