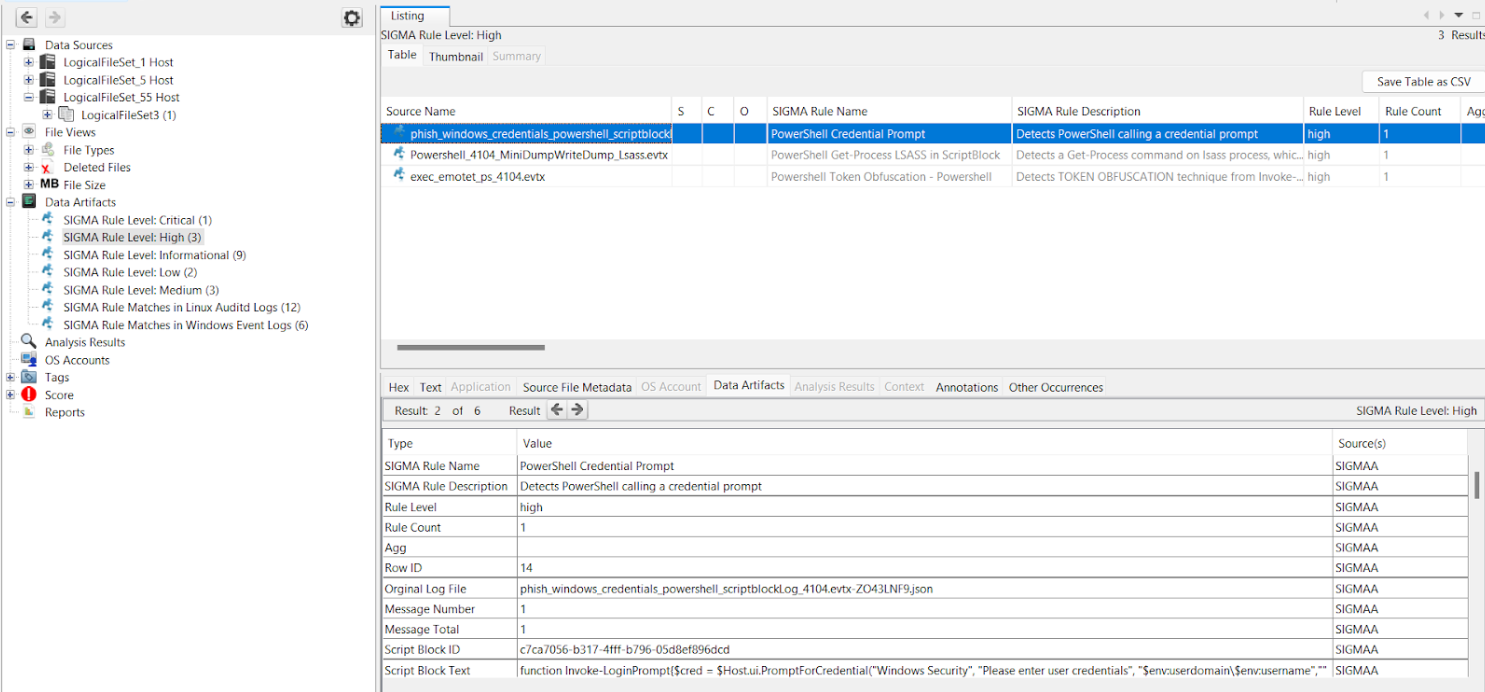
- Users can import Sigma rules via YAML files or its respective JSON format into Autopsy through the module
- Users have the option to run specific rule sets within the SIGMAA module
- Able to display analysis results according to log type and rule level under the Data Artifacts section in Autopsy
- SIGMA rules can be applied on EVTX logs for Windows and Auditd logs for Linux
This module can be used directly by cloning the repo and and place it in C:\Users\<username>\AppData\Roaming\autopsy\python_modules (Default Python Module path) in Autopsy
Alternatively, you can download the module in "Releases", unzip it, and place it in C:\Users\<username>\AppData\Roaming\autopsy\python_modules (Default Python Module path) in Autopsy
Installation of this module will be flagged by Antiviruses since some strings in the provided sample rules detects malicious attacks. This is the same with the Zircolite executable. If you wish to download the module without any sample Sigma rules or attack samples do download it at "Releases"
Users can import rule files in .yml format or its .json equivalent into the EvtxRule folder
Do note that if
.jsonfiles are used, only 1.jsonfile is accepted as input and it is prioritized from other.ymlrules
Users can import rule files in .yml format or its .json equivalent into the AuditdRule folder
Do note that if
.jsonfiles are used, only 1.jsonfile is accepted as input and it is prioritized from other.ymlrules
To convert these rule files from .yml to .json format using the sigma-cli tool, you have to leverage the sqlite backend and Zircolite mode.
sigma convert -t sqlite "yml_format_sigma_rule_path" -f zircolite -o output_file_name.jsonℹ️ Please note these rulesets are provided as an example you should generate your own rulesets but they can be very noisy or slow.
- EVTX Attack Samples: In
EVTXSamplesCollectionby sbousseaden
- Attack Samples: In
DEMO_SAMPLES - EVTX Logs Related Rule Sample: In
EvtxRule/powershell - Auditd Logs Related Rule Sample: In
AuditdRule/auditd
- Zircolite as the Sigma rule detection tool
- Jython for the Autopsy data source ingest module