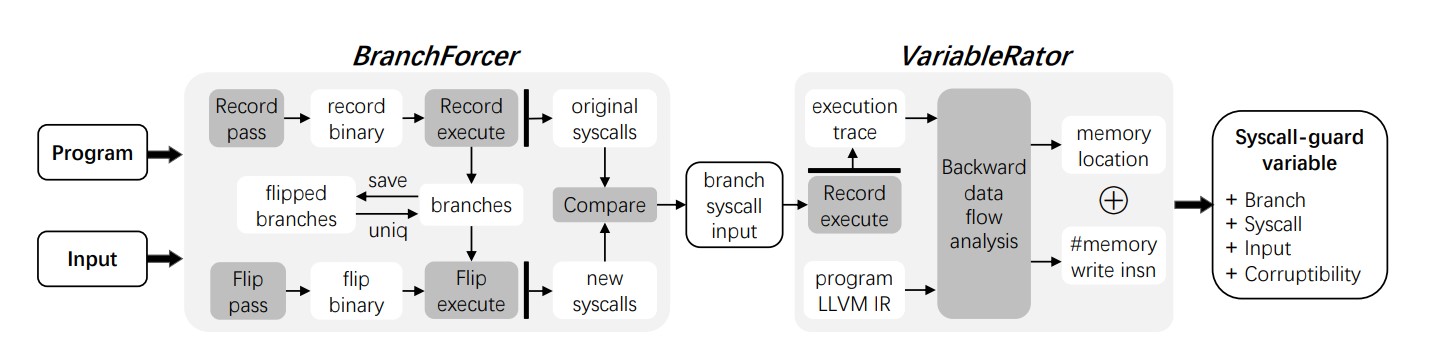
VIPER can automatically identify syscall-guard vairables for data-only attacks. It has two main components:
- BranchForcer (built on AFL) shortlists candidates of syscall-guard branches;
- VariableRator measures the feasibility of corrupting syscall-guard variables.
Please check our paper published on USENIX Security 2023 for more details.
clang 6.0- compiler (pre-built binaries, source code)graphviz- data-flow visualizer (source code)wllvm- whole-program-llvm IR generator (source code)
./build.sh
- Check test-sqlite.md for steps to test SQLite.
- Check repository viper-artifact to test more programs
- Check data-only attacks for four new data-only attacks
- Hengkai Ye hengkai@psu.edu
- Song Liu songliu@psu.edu
- Zhechang Zhang zbz5352@psu.edu
- Hong Hu honghu@psu.edu
VIPER: Spotting Syscall-Guard Variables for Data-Only Attacks
@inproceedings{ye:viper,
title = {{VIPER: Spotting Syscall-Guard Variables for Data-Only Attacks}},
author = {Hengkai Ye and Song Liu and Zhechang Zhang and Hong Hu},
booktitle = {Proceedings of the 32nd USENIX Security Symposium (USENIX 2023)},
month = {aug},
year = {2023},
address = {Anaheim, CA},
}We thank National Science Foundation (NSF) for supporting our work. This research is supported by NSF under grant CNS-2247652.