[Workshop] Bicep Infrastructure Developer
Requirements
- VS Code
- VS Code extensions:
- Bicep
- Azure Resource Manager (ARM) Tools
- Powershell
- Azure CLI version 2.53.0 or newer
- Bicep CLI version 0.22.6 or higher
- Powershell Core 7.2 or higher
Workshop
Preparation
- Create a ‘shared’ key vault with a secret
- Remember to check option
Azure Resource Manager for template deployment- it will be needed later - Available via the public network
- After deployment assign the role
Key Vault Secret Officerto your user - Add secret
MY-CUSTOM-SETTINGwith valueHELLO-WORLD
- Remember to check option
- Create two resource groups for training resources (one
devand oneprod) - (Optional) Create a folder for training files
- Here you should have a folder created for training purposes with a Bicep file created and connected to the main repo
[E01] Create storage account template (not parametrized, everything hardcoded)
[E02] Add a parameter for the location with a default value
Docs:
[E03] Add ARM JSON parameter file
[E04] Remove JSON parameter file and add .bicepparam parameter file (using keyword)
[E05] Add decorator for the description of the parameter and allowed values (when you go to the parameter file, then the tip with description and allowed values will be shown)
[E06] Add parameter with description, min length 5 and max length 15 characters for the application name
[E07] Create and use variable for storage account name which uses appName parameter as a part of the name.
Docs: Bicep variables.
Remember, that the storage account name must be unique, so add the unique suffix to the resource name.
- Using params/vars in string
- Functions:
substring,uniqueString - Getting info about resource group:
resourceGroup()
[E08] Change deployment mode to Complete
Docs:
[E09] Add blob container for storage as a child resource
Docs: Existing resources in Bicep
'default' blobServiceswithexistingkey word
[E10] Add additional two containers with loop
Docs: Iterative loops in Bicep
[E11] Extract container creation as separated resources
- Dependency between resources
- Loop on the resource level
[E12] Use parent reference to create containers
Docs: Set name and type for child resources in Bicep
[E13] Create Function app
- Consumption plan (
Y1/Dynamic) - Uses the existing storage account
- Runs on Windows & .NET
- Not all regions support Linux App Service Plans. Linux App Service Plan requires properties
kind: 'linux’andproperties: { reserved: true }- issue known from old times
- Not all regions support Linux App Service Plans. Linux App Service Plan requires properties
- Functions v4
- Enforces HTTPS connections
- Add enforcing HTTPS connection to storage account
- Quickstart: Create and deploy Azure Functions resources using Bicep
[E14] Parametrize blob container names (array)
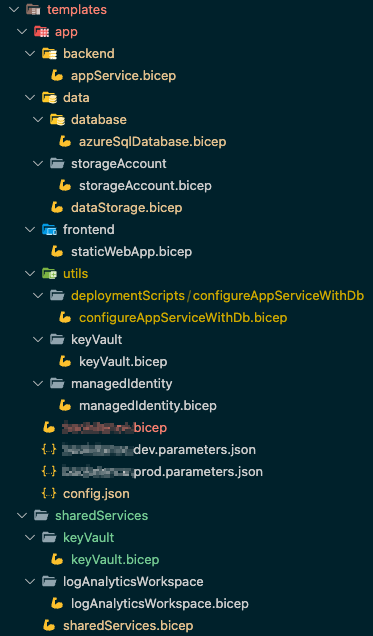
[E15] Extract storage creation to module
Docs:
- Create new file
templates/storage.bicep - Move storage-related codes to the new file
- Return storage name as output from the module deployment (
output) - Disclaimer - now the templates are not deployable due to loss of storage reference
Examples of the module structures
Example 1
Simple app infrastructure with a storage account and function app.
Example 2
Templates modularization for VM creation.
[E16] Call the storage module in the main file
- Deployment name - should be unique and max 64 characters in length
- The default basic deployment name is the file name of the main template
- Generate the main deployment name in a script: Azure/bicep#10129
[E17] Extract function app creation to module
- Create new file
templates/functionApp.bicep - Move function app-related codes to the new file
- Refer to the existing storage account deployed in another module (
existing) - Return function app URL as output from the module deployment
[E18] Call the function app module in the main file
- Deployment name - should be unique and max 64 characters in length
- Return function app URL as output from the deployment of the template (the URL should be visible in script output)
- Templates are deployable again
[E19] Add a new app setting in the function app where the value
The parameter in the module must be marked as @secure as it is taken from Key Vault.
[E20] Create a static config file
Docs:
- Shared variable file pattern
- Use Azure Key Vault to pass secure parameter value during Bicep deployment
- Resource group deployments with Bicep files
- Set scope for extension resources in Bicep
-
Use Shared Variable Pattern
-
Create
templates/staticConfig.jsonfile -
Add the content to the file with the below format (and fulfill your values):
{ "sharedKeyVault": { "resourceGroupName": "", "keyVaultName": "" } } -
Refer to the secret with a reference to the Key Vault (
existing,getSecretfunction) -
Remember about the indication of scope of the Key Vault (
resourceGroup) -
Difference between
scopeandtargetScope
[E21] Move secret reference to a parameter file
Docs:
- Reference-secrets-in-parameters-file
- Use Azure Key Vault to pass secure parameter value during Bicep deployment
Create manually container registry in a shared resources resource group
Publish the storage module to the created container registry
Docs:
az bicep publish --file ./templates/storage.bicep --target br:<cr_name>.azurecr.io/storage:1.0.0- Use tag 1.0.0
- Read more about semantic versioning: https://semver.org/
[E22] Replace the calling storage module in a file with calling module from a container registry
- Behind the scene
bicep restorecommand is called (to restore modules locally)
[E23] Add conditional deployment to storage module - if the parameter that contains blob container names is empty, then deploy the default container
Docs:
forloop doesn’t need to be changed - if an array contains zero elements, the loop will be done zero times- Do the required changes in the storage module
- Publish new module version (1.1.0)
- Update the main template to use the newest module version
- Complete deployment mode doesn’t work on the storage level - it shows where the responsibility for resource management should be placed
[E24] In a parameter file replace the hardcoded reference to KV with a reference taken from the staticConfig.json file
- Add a new field with the
subscriptionId - Store secret name as a variable in the parameter file