The aim of this guide is to help users modding their BIOS using the existing features provided by the BIOS itself, such as unlocking the CFG Lock, setting a custom DVMT value, undervolt etc.
- I am not responsible for bricked devices, dead SSD drives, thermonuclear war,
- or you getting fired because your PC booting process failed. Please do some research
- if you have any concerns about this procedure
- before using it! YOU are choosing to make these modifications, and if
- you blame me in any way for what happens to your device, I will laugh at you.
- BOOM! goes the dynamite
- Dell
- Lenovo
- Other vendors may directly give the BIOS payload which can be opened directly from UEFITool (e.g. ASUS, MSI, Gigabyte).
- Drag the payload file (tip, it has the largest size among the other files) inside UEFITool window
- Press search key combination (
Ctrl + F, if on Windows, orCommand + F, if on Mac OS) - Select
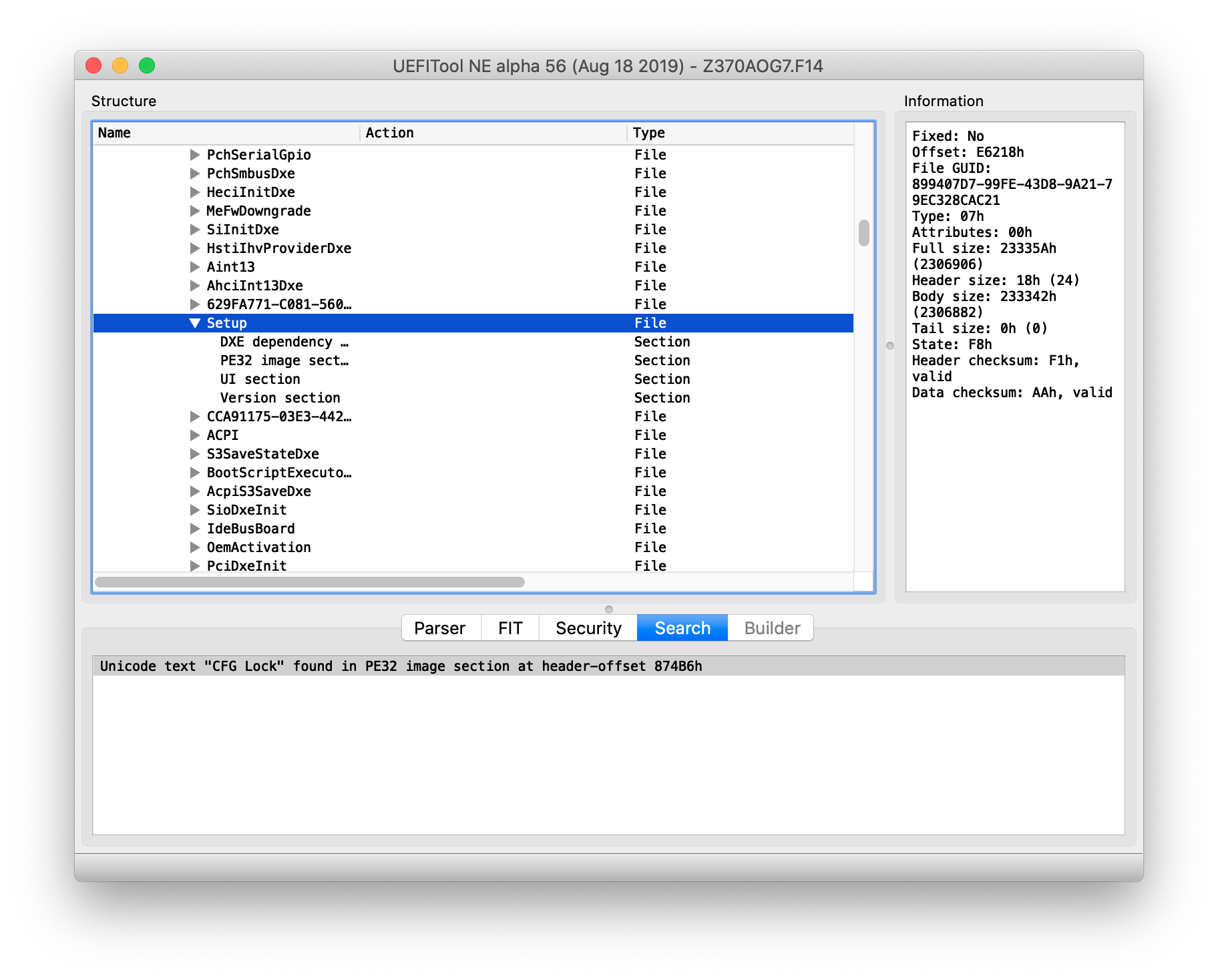
Textas search criteria and look forCFG Lock - If your BIOS supports CFG Lock functionality, you should have some results in the window as depicted below
-
On the bottom side of UEFITool you'll find a message such as:
Unicode text "CFG Lock" found in PE32 image section at header-offset XXYYZZ -
Double-click on the result to go straight to the section in which it was found.
-
Right click on
PE32 image section, selectExtract as isand save the file with.binextension.
With IFRExtract you can convert a .bin file in a .txt file.
On a terminal write:
<PATH IFRExtract> <PATH FILE.BIN> setup.txt
Let's suppose we wanna find the variable offset which corresponds to the CFG Lock setting in BIOS.
With a text editor open the previously converted file and look for CFG Lock
If anything is found, you'll find something as
CFG Lock, VarStoreInfo (VarOffset/VarName): 0xXYZ
0xXYZ is the offset of CFG Lock boolean bit.
Setting this variable value with 0x00 the CFG Lock will be disabled, granting access to MSR 0xE2 registry.
There are plenty different tools to set a certain value to a specific variable offset such as:
My favourite one - mainly because it's open source, has a good maintainer, and it's simple to use - is setup_var.efi but you're free to choose the tool you want.
Repeat Step 6 and instead of firing up modGRUBShell.efi, fire up ControlMsrE2.efi. It will produce an output such as:
This firmware has LOCKED MSR 0xE2 Register!if CFG Lock isn't unlocked (akaCFG Lock Offsetvalue is0x1)This firmware has UNLOCKED MSR 0xE2 Register!if CFG Lock is unlocked (akaCFG Lock Offsetvalue is0x0)
If the message produced is like the last one, then it means that CFG Lock is unlocked and you can proceed disabling from config.plist:
- OpenCore:
config.plist/Kernel/Quirks/AppleCpuPmCfgLockand/orconfig.plist/Kernel/Quirks/AppleXcpmCfgLock
as those patches maybe too instable and can cause sudden reboots on your rig.
If you encounter any issue, please file a bugreport here.
Don't forget to attach your BIOS executable file!
- Khronokernel for MSR 0xE2 unlocking guide
- theopolis for Python script
- Longsoft for PFSExtractor
- platomav for Dell Extraction script utility
- MacOS86 forum for giving us the italian repository. Check it out here
- dreamwhite for testing on different MOBO vendors and for contributing on different parts of original guide
- A23SS4NDRO for writing firstly this guide