Provide efficient, stable and secure file distribution and image acceleration based on p2p technology to be the best practice and standard solution in cloud native architectures.
Dragonfly is an open source P2P-based file distribution and image acceleration system. It is hosted by the Cloud Native Computing Foundation (CNCF) as an Incubating Level Project. Its goal is to tackle all distribution problems in cloud native architectures. Currently Dragonfly focuses on being:
- Simple: Well-defined user-facing API (HTTP), non-invasive to all container engines;
- Efficient: Seed peer support, P2P based file distribution to save enterprise bandwidth;
- Intelligent: Host-level speed limit, intelligent flow control due to host detection;
- Secure: Block transmission encryption, HTTPS connection support.
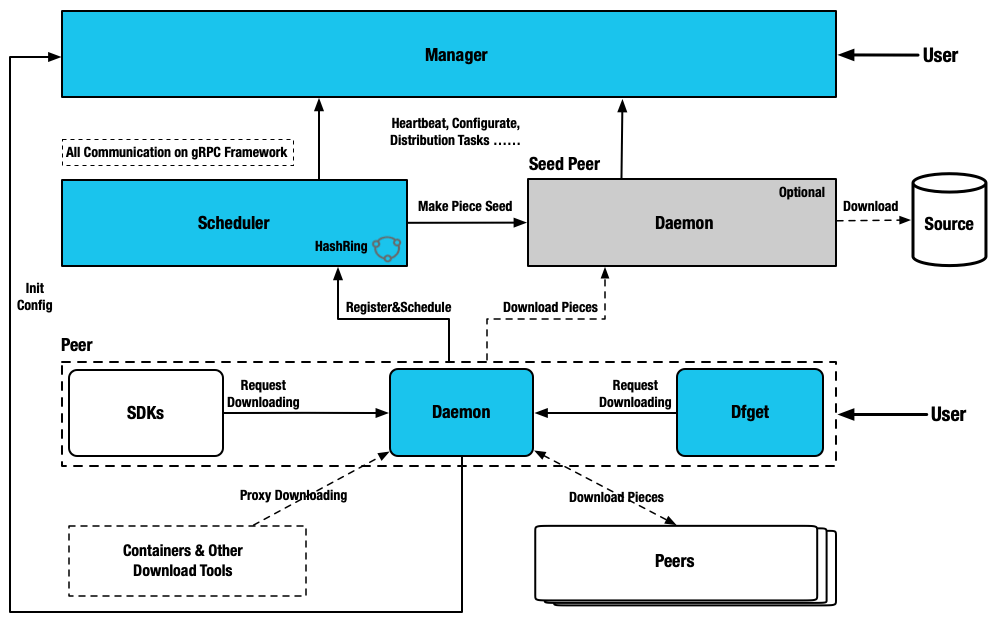
Manager: Maintain the relationship between each P2P cluster, dynamic configuration management and RBAC. It also includes a front-end console, which is convenient for users to visually operate the cluster.
Scheduler: Select the optimal download parent peer for the download peer. Exceptions control Dfdaemon's back-to-source.
Seed Peer: Dfdaemon turns on the Seed Peer mode can be used as a back-to-source download peer in a P2P cluster, which is the root peer for download in the entire cluster.
Peer: Deploy with dfdaemon, based on the C/S architecture, it provides the dfget command download tool,
and the dfget daemon running daemon to provide task download capabilities.
You can find the full documentation on the d7y.io.
A third party security audit was performed by Trail of Bits, you can see the full report here.
Join the conversation and help the community.
- Slack Channel: #dragonfly on CNCF Slack
- Discussion Group: dragonfly-discuss@googlegroups.com
- Developer Group: dragonfly-developers@googlegroups.com
- Github Discussions: Dragonfly Discussion Forum
- Twitter: @dragonfly_oss
- DingTalk: 22880028764
You should check out our CONTRIBUTING and develop the project together.
Please refer to our Code of Conduct.