📖🔍 Documents of the NKN Name Service.
NKN is the next generation of peer to peer network infrastructure built upon blockchain technology backed by Cellular Automata theory aiming at revolutionizing the Internet with true decentralization and native token incentive mechanism. NKN introduced the concept of Decentralized Data Transmission Network (DDTN). DDTN combines multiple independent and self-organized relay nodes to provide clients with connectivity and data transmission capability.
NKN introduces Proof of Relay as consensus mechanism and incentive model which encourages people to join the network to share and enhance network connectivity and data transmission. In short, the reward is depending on the data amount of a node relays. It makes whole network retain high efficiency as well. The "mining" is redefined as contributing to the data transmission layer, and the only way to get more rewards is providing more transmission power.
BNS – or blockchain name system – is the protocol on the internet that turns human-comprehensible decentralized website names such as ‘website.xem’ or ‘mywebsite.xem’ into addresses understandable by decentralized network machines.
NNS is the NKN Name Service, a distributed, open, and extensible naming system based on the NKN blockchain.
The NKN technical stacks show the abstractions in different layers, and the layers in the picture below start from the top and constructed down along with the y-axis.
For example, the identity component in the component layer is built upon on the state layer which is NKN core.
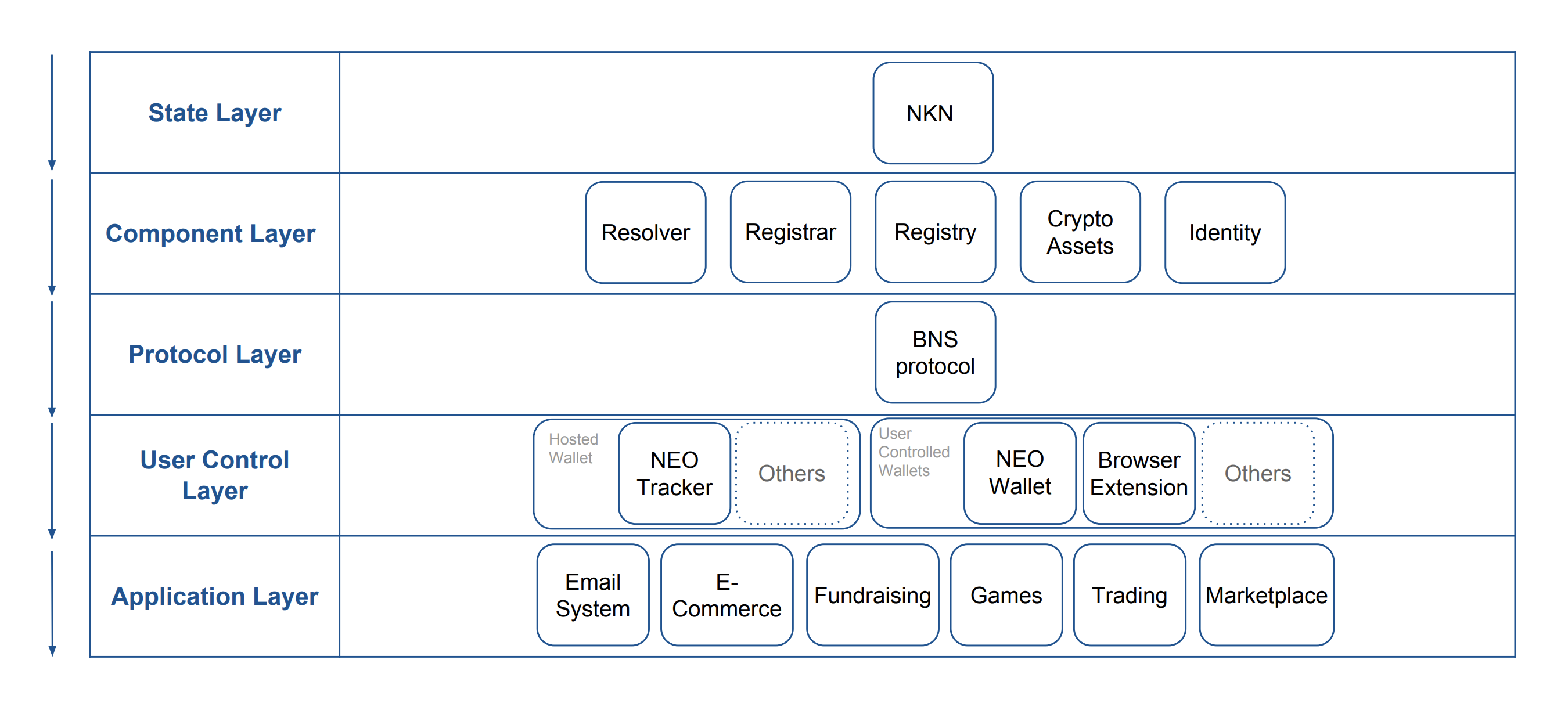
The decentralized network stores the state information of each digital identity which usually based on different PKI system, every transactions and behavior can be stored and owned by the users. NKN core serves the fundamental infrastructure of the state layer. From this layer down each layer is built based on this infrastructure network.

The component layer is the abstraction of certain smart contract patterns or standards. Such as non-fungible assets which have some basic interfaces and many metadata describing the associated object. Those implementations behind the scenes are certain persistent scripts running on the core which provided by the state layer.

NKN name service utilizes BNS protocol containing the specifications towards registrar, registry and resolver, it can greatly ease the development obstacles and allow more possibilities built upon on the interfaces.

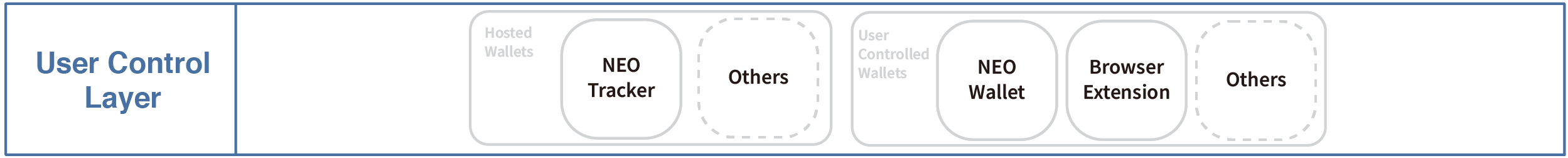
The user control layer describes the key of user adoption, if no well-designed interface for users to manage their wallet and sign transactions, a user will have to interact with the decentralized services and applications with command line interface. There are many solutions to make the user adoption growth, such as the NEO wallet, browser extension and so on.
Applications built on the NKN decentralized network stacks unleased unlimited use cases and capacities. Such as fund rasing, trading, and game fields, each participants can control their data and experience the services at the same time. There will be more powerful services coming out as the stack matures.

PoR is a useful proof of work, it redefines mining as relaying data. PoR's implementation is basded on a special signature chain. In simple terms, the PoR signature chain is a hash chain that relay nodes sign in turn when relaying data packets.
A signature chain is a chain of signature, signed by data relayers sequentially when relaying NKN packet. Each element of the chain consists of the following fields:
- Relayer NKN address and public key.
- Next relayer NKN address.
- Signature(signature of the previous element on chain, relayer NKN address, next relayer NKN address) signed with relayer private key.
The first element of the signature chain is signed by source, and the signature field is replaced by signature(payload hash, payload size, source NKN address and public key, destination NKN address and public key, next relayer NKN address). Signature chain cannot be forged because each element contains the NKN address and public key of the next node. If a malicious node is on the route and intends to modify some previous elements on the chain when generating his signature, the chain is no longer valid.
New block is added to the blockchain by first selecting a “leader” that proposes the new block. The leader selection is uncontrollable but verifiable. The expected probability that a node is elected as leader is proportional to the data relayed by the node on secure paths.
Leader is selected by first selecting a signature chain on a secure path. The signature chain being selected is the one that has the lowest last signature value. To select the signature chain with lowest last signature, each node who signs the last signature checks if the last signature is smaller than a threshold. If the last signature is smaller than the threshold, the node sends out the signature chain to the network as a candidate for the lowest last signature.
Block is proposed by the selected leader in each round. Proposed block is sent to all nodes for verification and consensus. During consensus phase, each node sends to its neighbors the hash of the block (in case the leader sends out different blocks to different neighbors) and if it is accepted or not.
In the PoR algorithm, the bookkeeper candidate vote is not a vote of a person or IP address, but a vote of a signature chain. If any malicious node wants to control NKN, it must have enough active channels (signature chain) under control. The larger scale of NKN the more difficult it is to control.
- Clone NKN project.
git clone https://github.com/nknorg/nkn.git
Dockerinstalled.
- Change current directory to
nknproject.
cd nkn
- Build dokcer image.
docker build -t nkn .
- After docker image built successfully, we need to prepare a configuration file for starting a node. There are two default configuration files in
nknproject:
config.testnet.json: used to join the testnet.config.local.json: create and join a private chain on your localhost. In this tutorial, we want to make our own node become part of the testnet, so we will chooseconfig.testnet.jsonas configuration file.And open thecp config.testnet.json config.jsonconfig.jsonfile: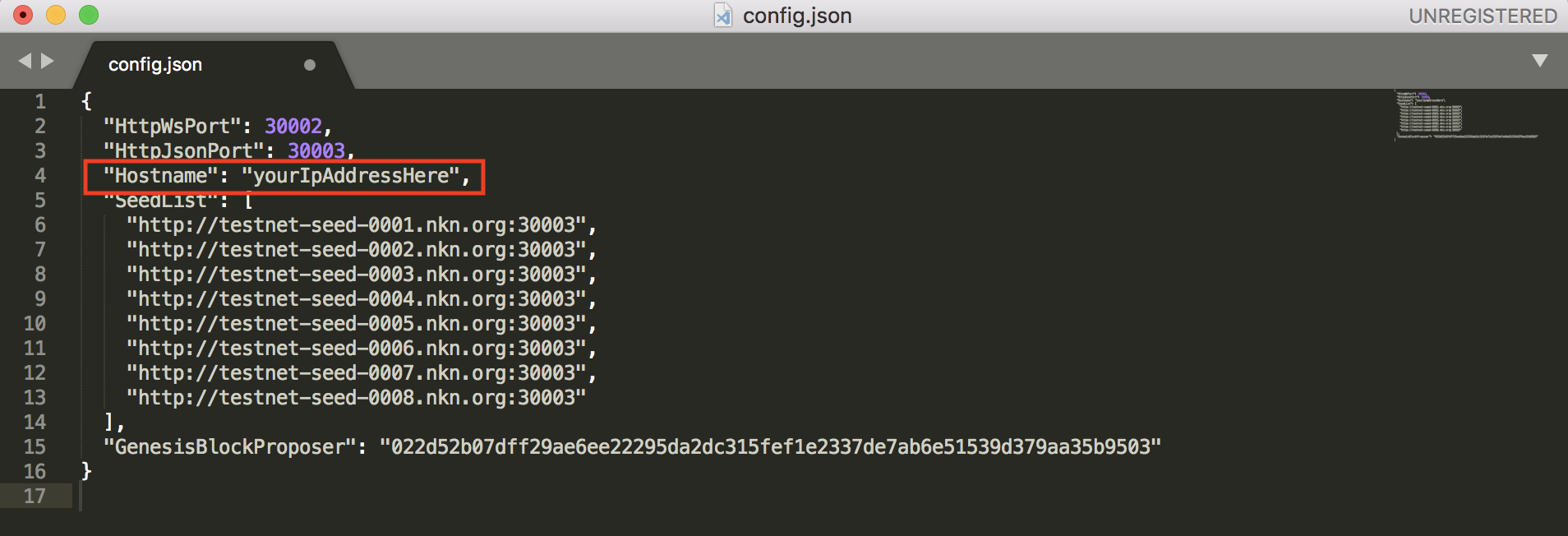
- Replace
Hostnamewith your IP address.
- Replace
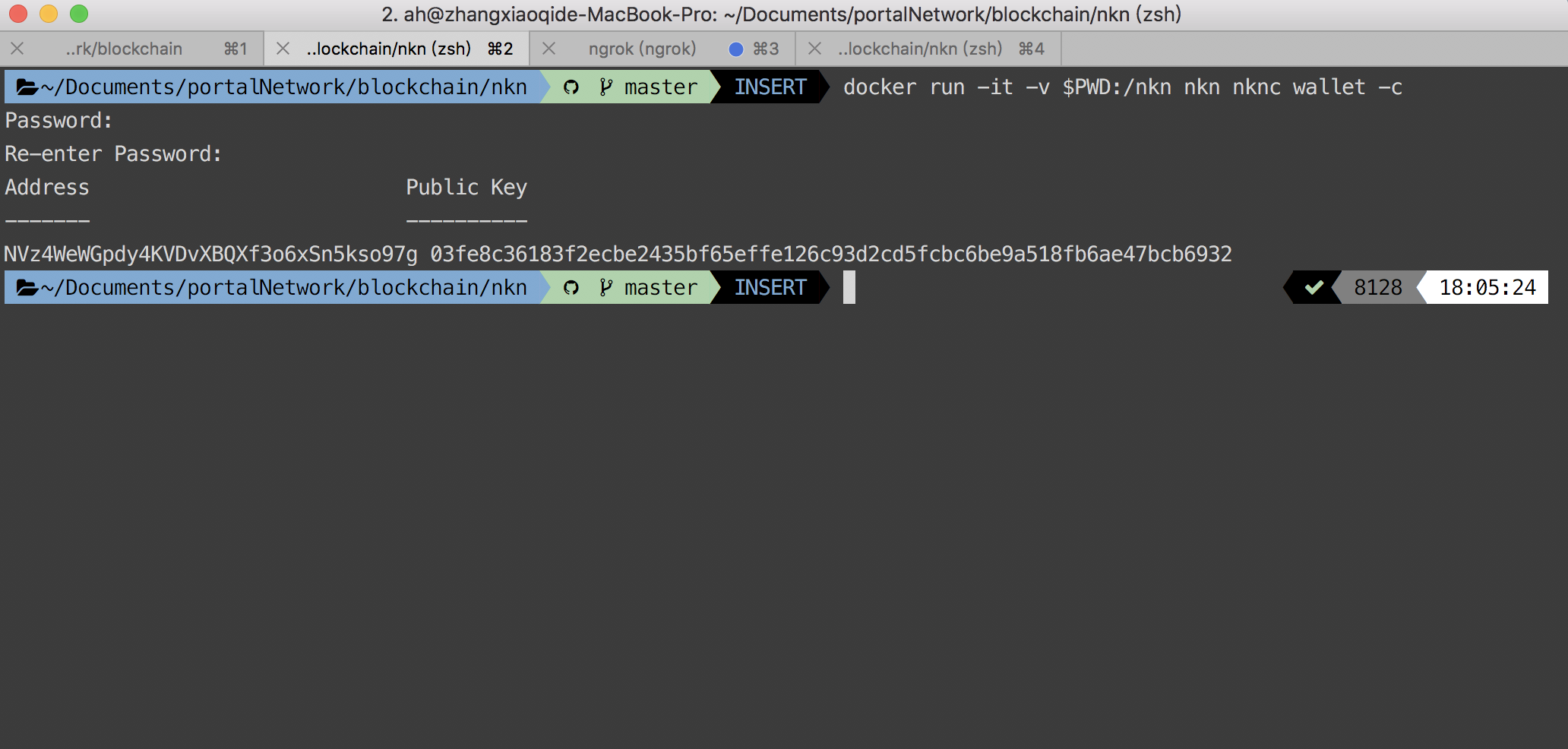
- Before starting the node, we need to create a new wallet first:
docker run -it -v $PWD:/nkn nkn nknc wallet -c
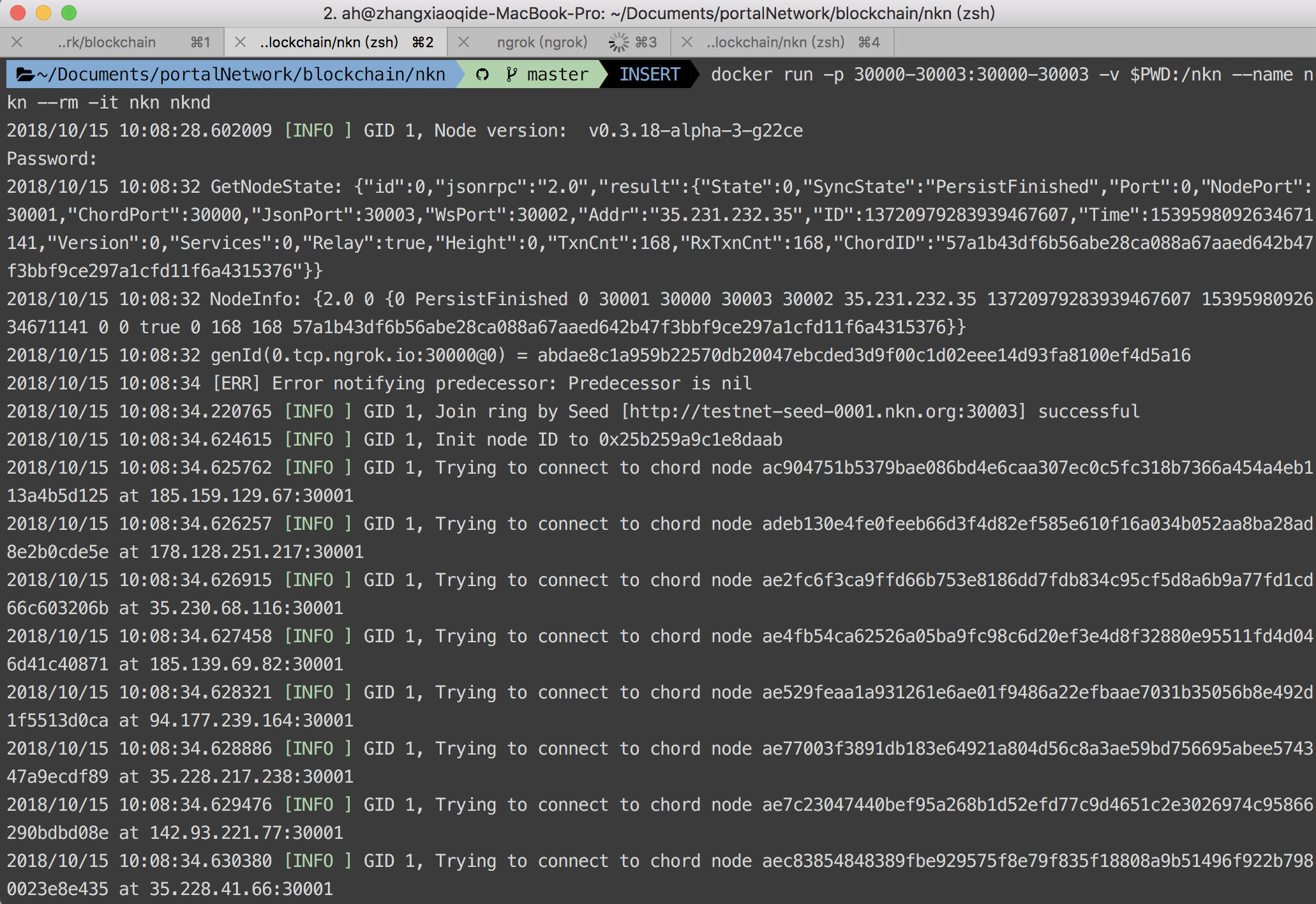
- After wallet created, we can start to deploy local node:
docker run -p 30000-30003:30000-30003 -v $PWD:/nkn --name nkn --rm -it nkn nknd
-
Go 1.10+ installed.
-
$GOROOTand$GOPATHenvironment variable configured.export GOROOT=$(go env GOROOT) export GOPATH=$(go env GOPATH) export GOBIN=$GOPATH/bin export PATH=$PATH:$GOBIN -
Create directory $GOPATH/src/github.com/nknorg/ if not exists.
mkdir -p $GOPATH/src/github.com/nknorg
- Clone nkn project to
$GOPATH/src/github.com/nknorg/.
cd $GOPATH/src/github.com/nknorg/
git clone https://github.com/nknorg/nkn.git
- Install package management tool
glide.
cd nkn
make glide
- Download dependency module and build project.
make vendor
make
- After source code built successfully, we need to prepare a configuration file for starting a node. There are two default configuration files in
nknproject:
config.testnet.json: used to join the testnet.config.local.json: create and join a private chain on your localhost. In this tutorial, we want to make our own node become part of the testnet, so we will chooseconfig.testnet.jsonas configuration file.And open thecp config.testnet.json config.jsonconfig.jsonfile:
- Replace
Hostnamewith your IP address.
- Replace
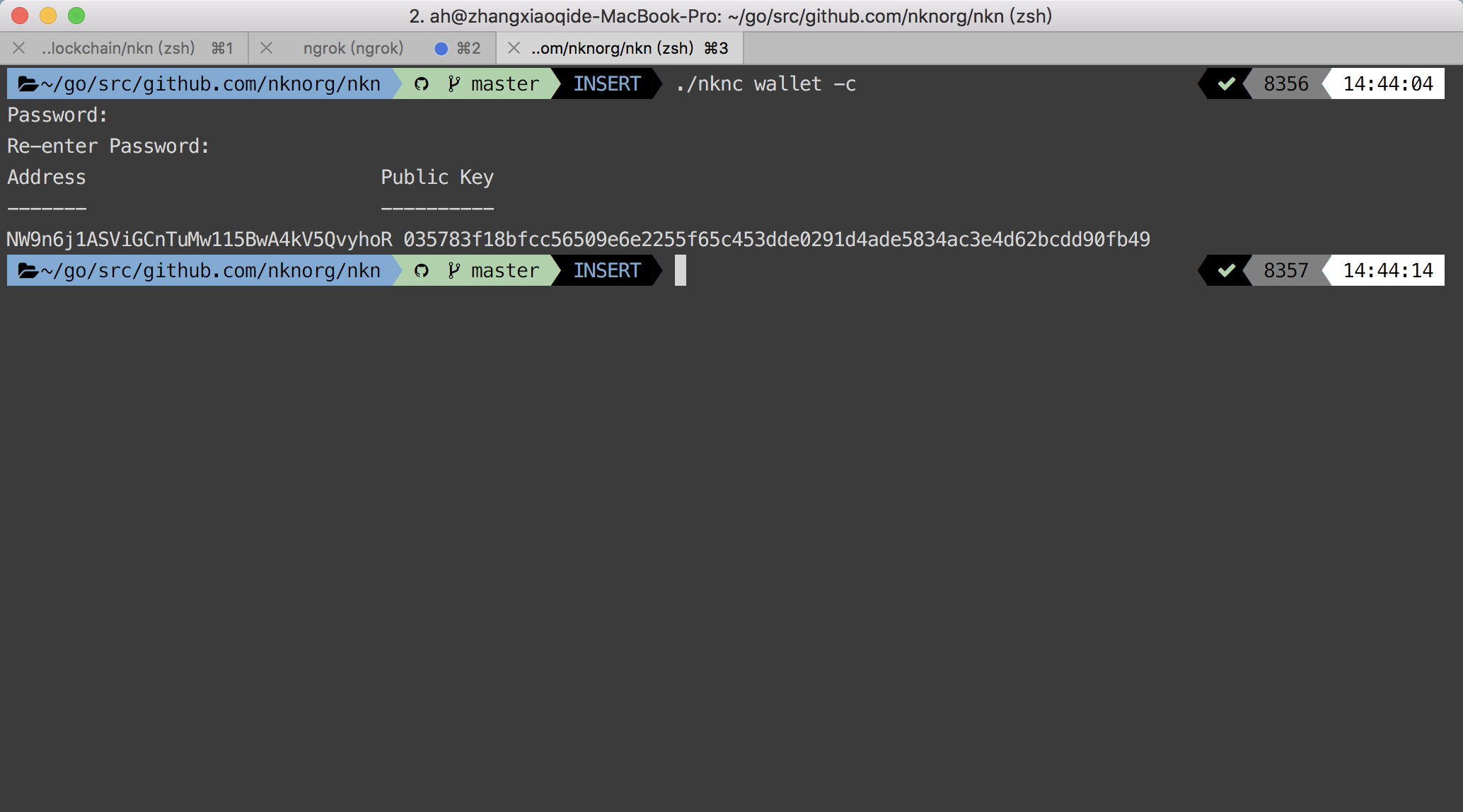
- Before starting the node, we need to create a new wallet first:
./nknc wallet -c
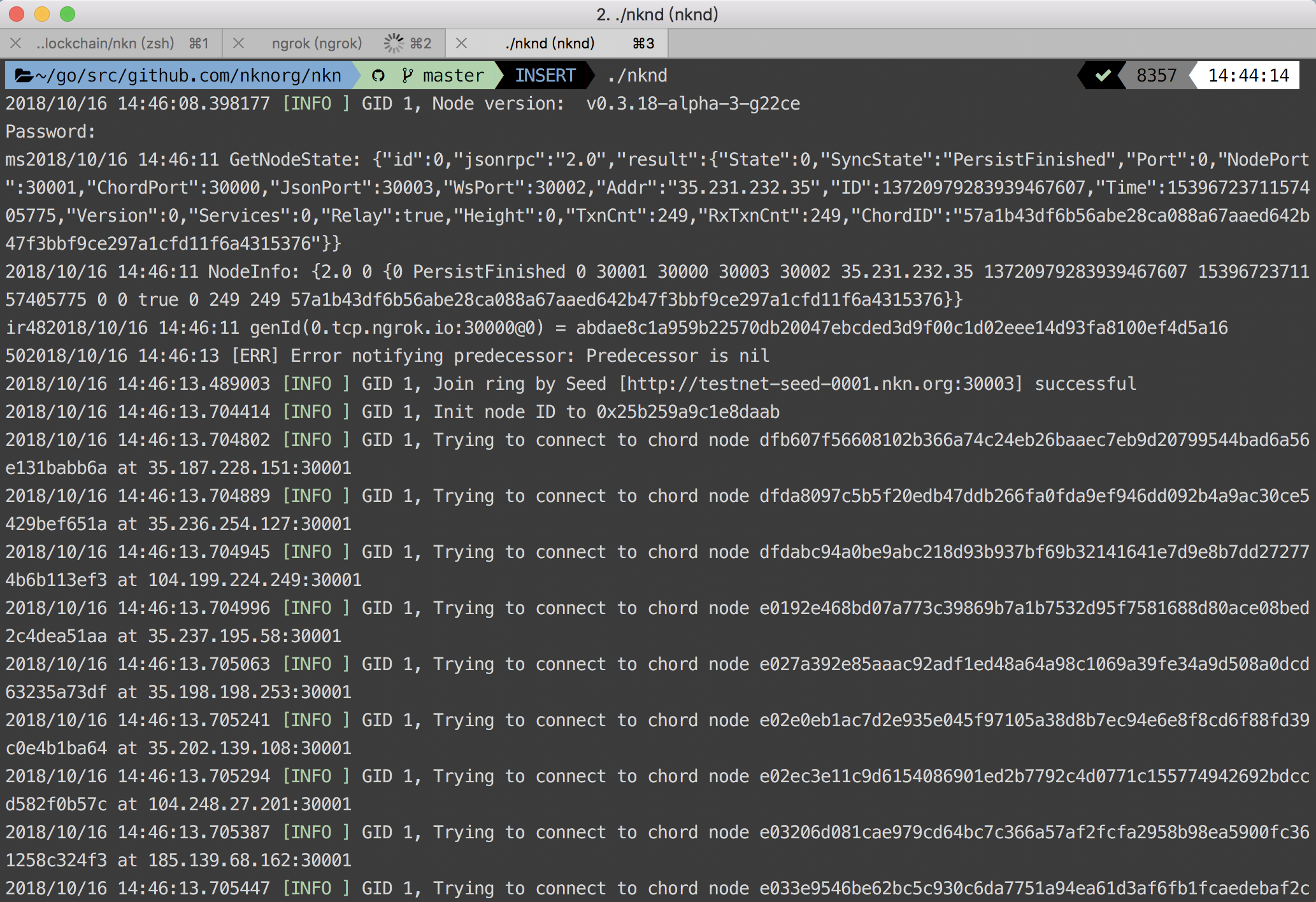
- After wallet created, we can start to deploy local node:
./nknd
See CONTRIBUTING.md for how to help out.
See LICENSE for details.