This repo is created for the open-source of the paper Information Leakages in Code-based Masking: A Unified Quantification Approach, which would appear in TCHES 2021, issue 3. All the data and scripts would allow researchers to verify and reproduce our results.
- We recommend the Mathjax Plugin for Github on Chrome to have a better display of mathematical formulas.
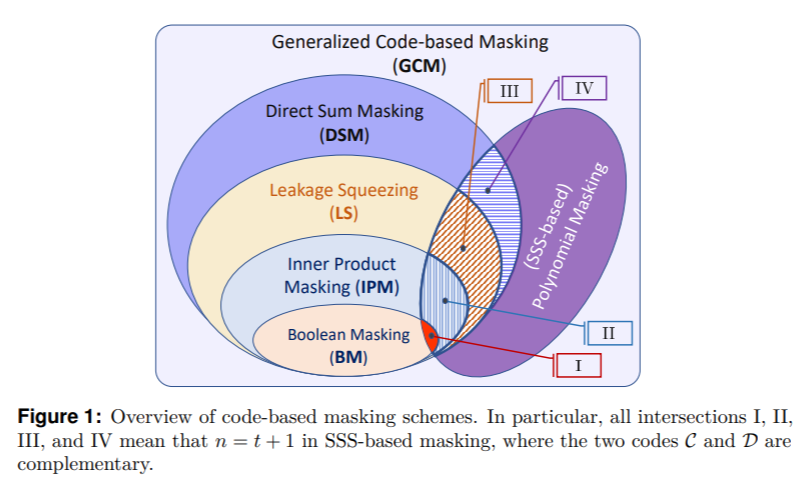
We present a unified framework for quantifying the side-channel resistance of the Generalized Code-based Masking (GCM). We call the GCM, which includes Direct Sum Masking (DSM), Leakage Squeezing (LS), Inner Product Masking (IPM), Shamir's Secret Sharing (SSS) based polynomial masking and also Boolean masking. Note that the Boolean masking is not a special case of SSS-based masking.
- A note of caution: the abbreviation GCM here should not be confused with the Galois/Counter Mode (GCM), which is a mode of operation for symmetric-key block ciphers (e.g., AES-GCM).
The overview of GCM is as follows.
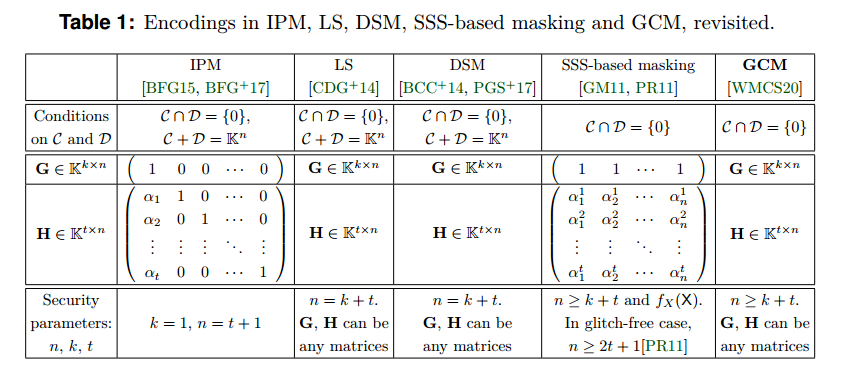
The uniform representation of encoding in GCM is:
As the applications, we present hereafter an exhaustive study of the linear codes for two cases of
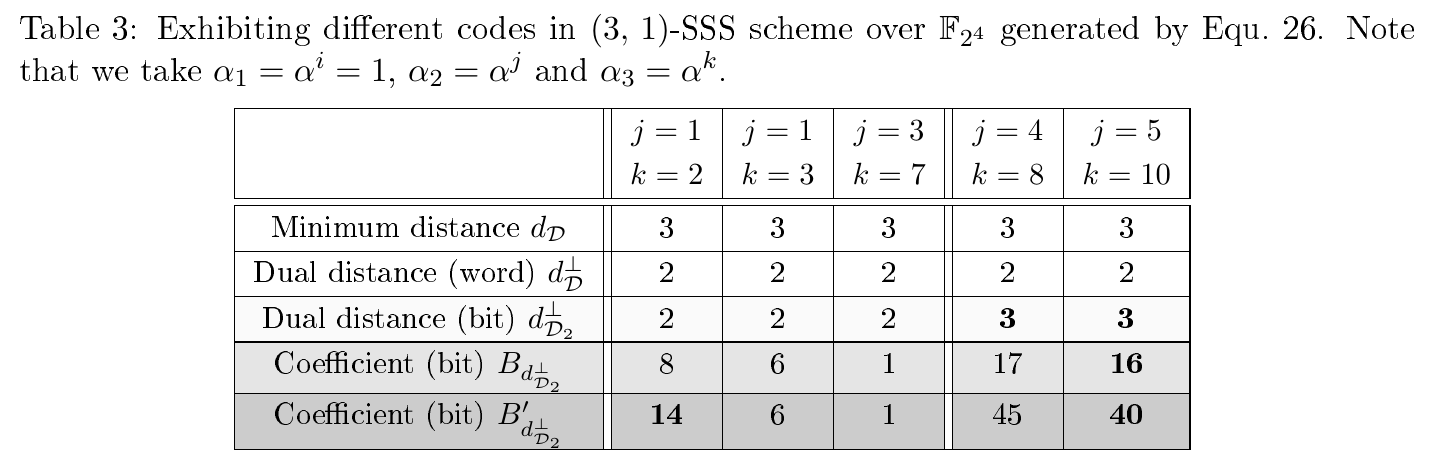
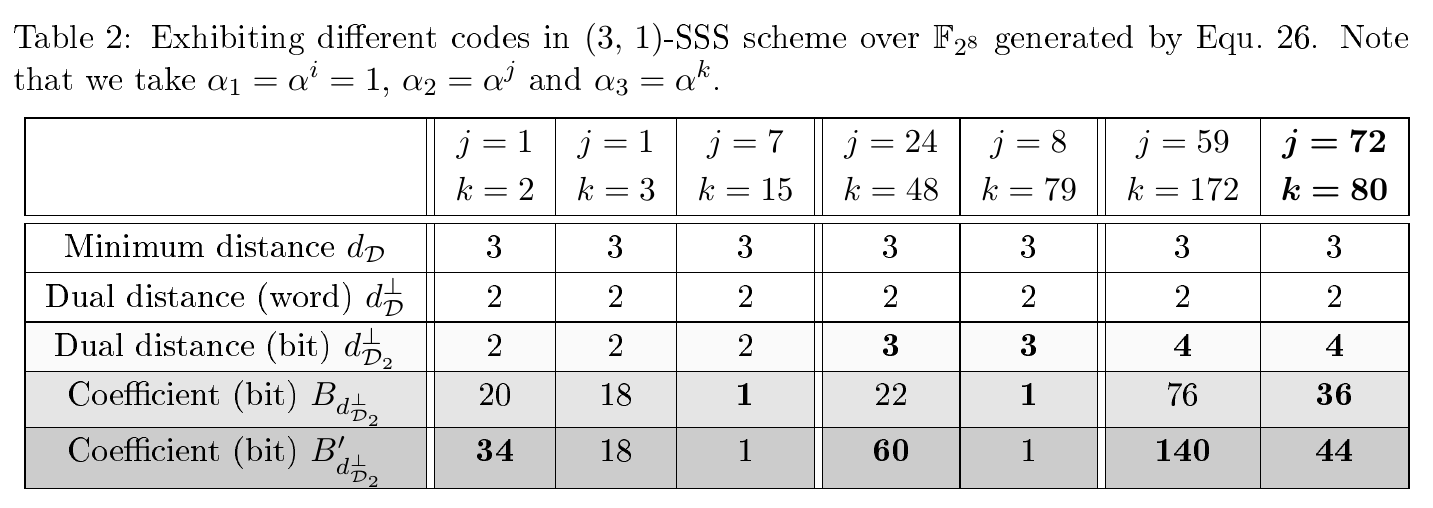
- (3,1)-SSS-based masking with
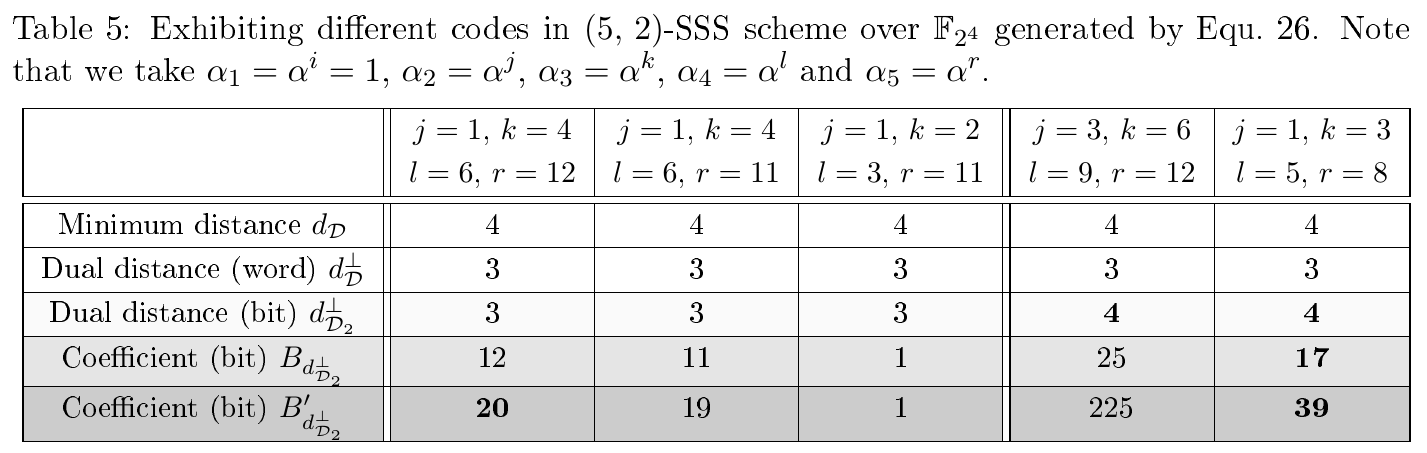
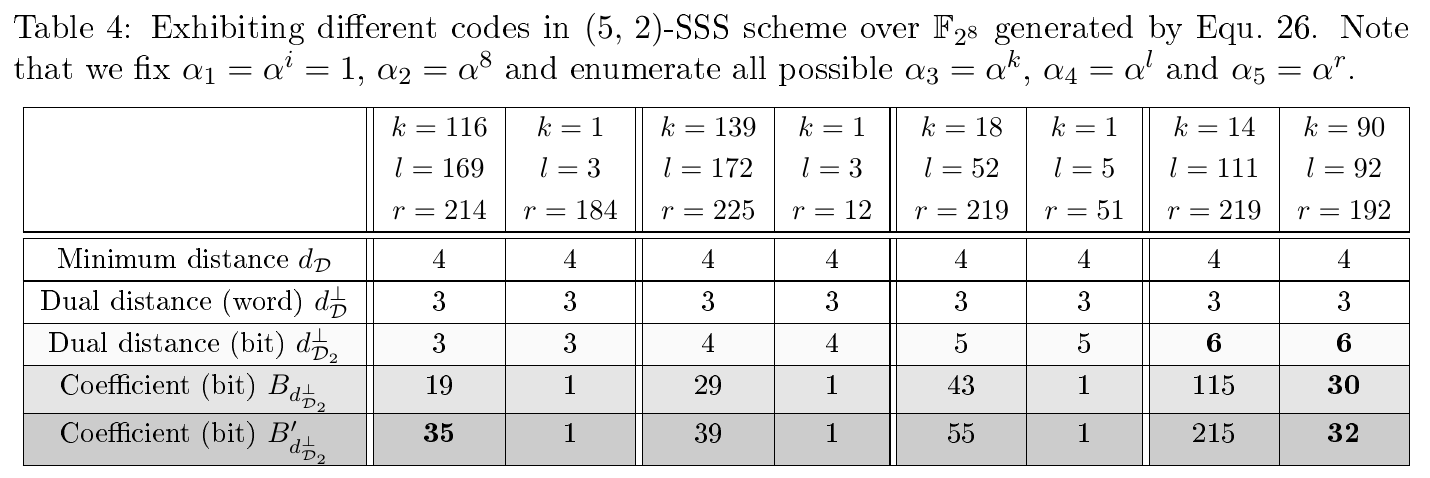
$n=3$ shares and$t=1$ - (5,2)-SSS-based masking with
$n=5$ shares and$t=2$
See here: Optimal codes for SSS-based masking ($l$=4).
The optimal codes are given in Tab. II in Section 2.
Some codes with different parameters are shown as follows.
See here: Optimal codes for SSS-based masking ($l$=8).
The optimal codes are given in Tab. II in Section 2.
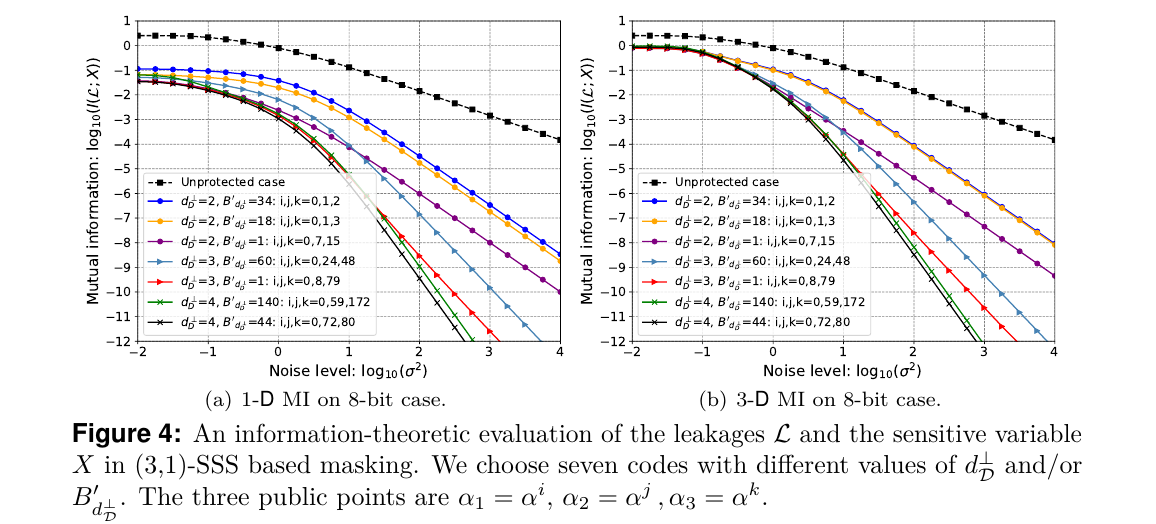
An information-theoretic investigation (by mutual information) of seven codes for (3,1)-SSS based polynomial masking are shown below. Note that one of the three optimal codes is the black curve in Fig. 4.
Some codes with different parameters are shown as follows.
See here: Optimal codes for SSS-based masking ($l$=4).
The optimal codes are given in Tab. II in Section 2.
Some codes with different parameters are shown as follows.
See here: Optimal codes for SSS-based masking ($l$=8).
Part of codes with the maximized dual distance d are given in Tab. II in Section 2. We also provide all possible values of
Some codes with different parameters are shown as follows.
We share the Magma scripts to easily check the validity of our results, see here: Magma scripts. The corresponding logs are also provided here: Magma logs for weight enumerators of the corresponding linear codes.
- Wei Cheng (wei.cheng AT telecom-paris.fr)
- Sylvain Guilley (sylvain.guilley AT secure-ic.com)
This repository is placed into the public domain. Anyone can redistribute it and/or modify it under the terms of the GNU General Public License version 3.0.
Copyright (C) 2020. All Rights Reserved to Authors.
[BFG+17] Josep Balasch, Sebastian Faust, Benedikt Gierlichs, Clara Paglialonga, François-Xavier Standaert. Consolidating Inner Product Masking. ASIACRYPT (1) 2017: 724-754.
[WMCS20] Weijia Wang, Pierrick Méaux, Gaëtan Cassiers, François-Xavier Standaert. Efficient and Private Computations with Code-Based Masking. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2020(2): 128-171 (2020).
[CGC+20] Wei Cheng, Sylvain Guilley, Claude Carlet, Sihem Mesnager and Jean-Luc Danger, Optimizing Inner Product Masking Scheme by A Coding Theory Approach. The IEEE Transactions on Information Forensics and Security, doi: 10.1109/TIFS.2020.3009609.