XSSor is a semi-automatic reflected and persistent XSS detector extension for Burp Suite. The tool was written in Python by Barak Tawily, an application security expert. XSSor was designed to help security testers by performing semi-automatic reflected and persistent XSS detection tests.
-
Download Burp Suite (obviously): http://portswigger.net/burp/download.html -
Download Jython Standalone JAR: http://www.jython.org/downloads.html -
Open BurpàExtenderà Optionsà Python Environmentà Select Fileà Choose the Jython Standalone JAR -
To install XSSor follow these steps:
a. Download the XSSor.py file. b. Open BurpàExtenderà Extensionsà Addà Choose XSSor.py file. c. See the XSSor tab and enjoy semi-automatic reflected and persistent XSS detection J
-
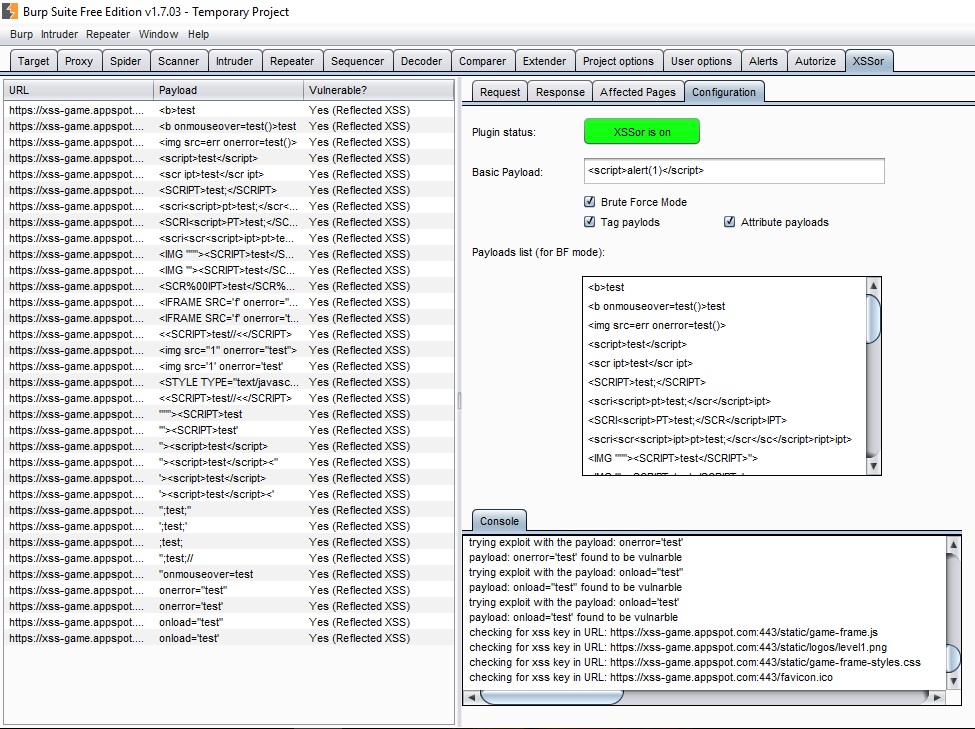
After installation, the XSSor tab will be added to Burp. -
Open the configuration tab (XSSorà Configuration) and turn XSSor on. -
Browse to the tested website and write the XSS keyword (the default is “xssme” in the tested parameter). -
XSSor will send the same request (or multiple requests if in ‘brute force’ mode) to the tested website with the defined payload (or multiple payloads in case of BT mode). -
XSSor will add a row for each payload, and the status; if it is vulnerable or not.
There are 3 options:
-
N - Not vulnerable -
Yes (Reflected XSS) - The malicious payload was found in the response of the tested page. -
Yes (Persistent XSS) - The malicious payload was found in the response of one of the affected pages.
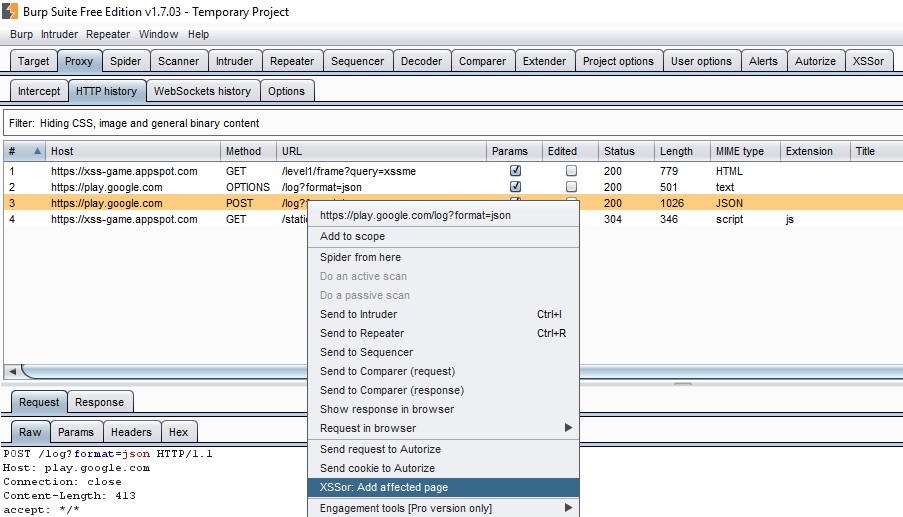
The ‘affected pages’ feature was designed in order to find persistent XSS flaws. By adding this feature, XSSor will check if the malicious payload is found in the affected page’s responses.
In order to add affected pages, right-click on the request and click on ‘XSSor: Add affected page’ as shown in the following image:
You can view the affected page response and the request containing the payload in the ‘affected pages’ tab under the XSSor tab.
- Barak Tawily, application security expert