Owner : Mr. Sup3rN0va | "06-07-2021"
Tags : #docker, #pentest, #mobile, #web, #network, #tool
"Dr0P"stands for"Docker for Pentesting"is a docker image builder for penetration testing- Dockerfile for
"Dr0P"currently have tools for"Mobile Pentesting"but we can add more related toNetworkandWeb - Current gist includes:
Dockerfiletoolsfolder where we need to download latestAndroid StudioandOWASP ZAP/Burp. It already has RASEv2 pre-loadedscriptsfolder from where all the startup scripts get copied insideDockerimage to ease functionality
-
Download the repo :
git clone https://github.com/m2sup3rn0va/Dr0P.git -
Download latest
Android StudioandOWASP ZAP/Burpsuiteas proxy of your choice. If you are usingZAP, download the package and not the installer -
Currently
Dockerfileis configured forZAPonly but you can tweak it as per your requirement -
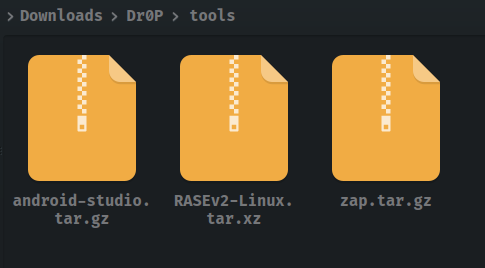
Make sure that you download and save both
Android StudioandOWASP ZAP/Burpintoolsfolder -
Also, make sure that you have renamed downloaded
Android Studioasandroid-studio.tar.gzandZAPaszap.tar.gz -
Thus the contents of
toolsfolder : -
Now, run :
chmod +x deploy_docker.shand./deploy_docker.sh -
This will install
dockerfor you. Once, the script completes, pleaselogoffandloginback and re-run the script -
The script works in two phases:
Phase-1: Installdockerand set it for logged in$USER. It also createsshareDrivefordocker containerPhase-2: Buildsdockerimage and createsdockercontainer
-
If you want you can save the image locally for future use as :
docker image save <image-id> -o dr0pv1.tar -
After when you clean the images and docker containers and you want to import back the image you saved locally :
docker load -i dr0pv1.tar. After that,docker tag <image-id> dr0p:v1 -
Now you can create the container with this image and run it for pentesting
-
Once you are inside the container, the first thing you need to run is :
sudo chown -R user:user /dev/kvm. Without this you will not be able to runAVDinside docker. Obviously to run this command successfully, you need to haveVT-x/AMD-Venabled atBIOSlevel -
While running the container,
RASEv2will help in building and rooting theAVDcreated usingAndroid Studio. So, make sure that you visitGithub-RASEv2(linked below) to understand how to installAndroid Studio. Once, installed, justcd RASEv2-Linuxandpython3 RASEv2.py -
You can refer to RASEv2 for more details