Curated Intelligence is working with analysts from around the world to provide useful information to organisations in Ukraine looking for additional free threat intelligence. Slava Ukraini. Glory to Ukraine. (Blog | Twitter | LinkedIn)
- 2022-02-25
- Creation of the initial repository to help organisations in Ukraine
- Added Threat Reports section
- Added Vendor Support section
- 2022-02-26
- Additional resources, chronologically ordered (h/t Orange-CD)
- Added Vetted OSINT Sources section
- Added Miscellaneous Resources section
- 2022-02-27
- Additional threat reports have been added
- Added Data Brokers section
- Added Access Brokers section
- 2022-02-28
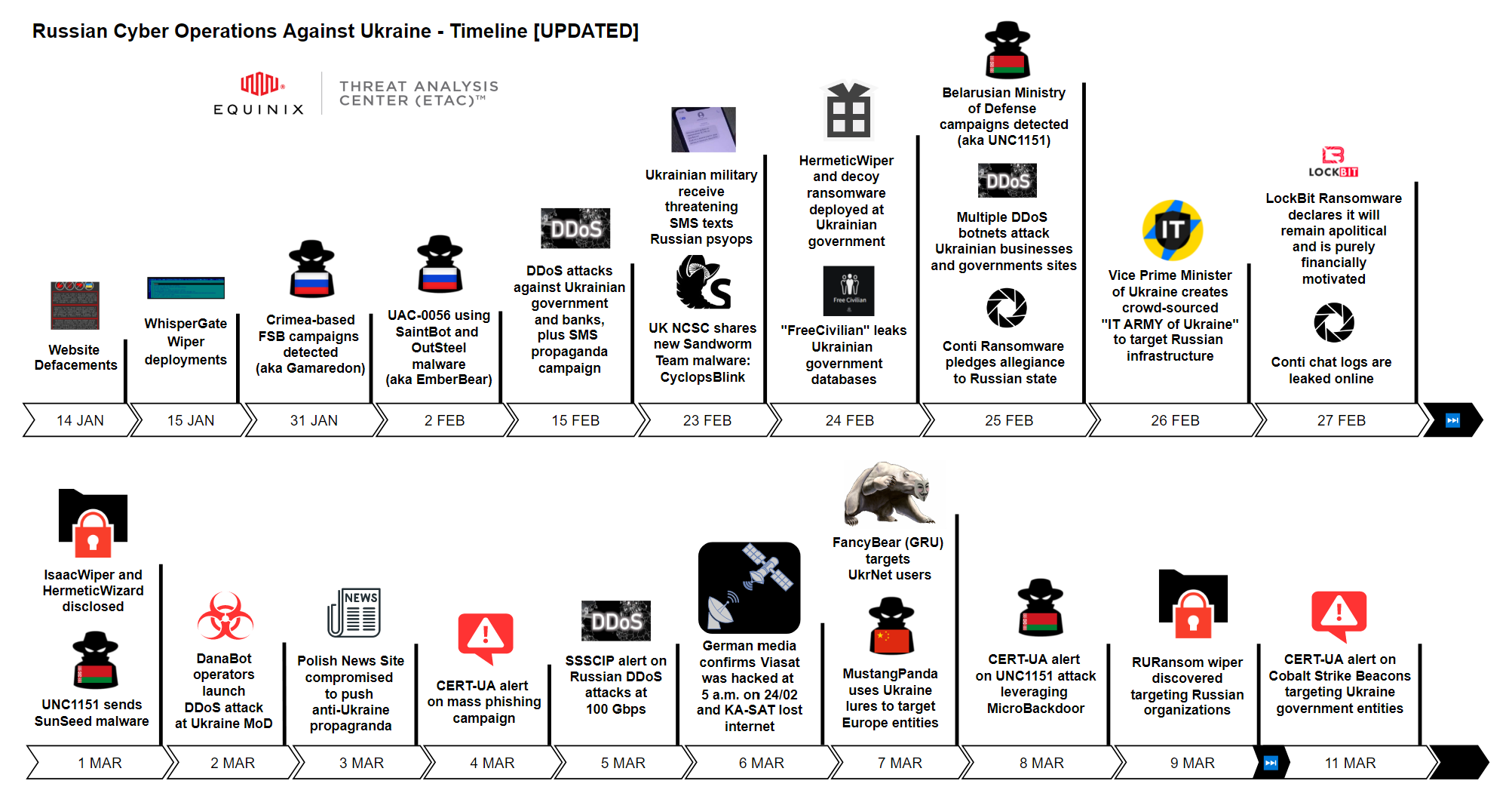
- Added Russian Cyber Operations Against Ukraine Timeline by ETAC
- Added Vetted and Contextualized Indicators of Compromise (IOCs) by ETAC
- 2022-03-01
- Additional threat reports and resources have been added
- 2022-03-02
- Additional IOCs have been added
- Added vetted YARA rule collection from the Threat Reports by ETAC
- Added loosely-vetted IOC Threat Hunt Feeds by KPMG-Egyde CTI (h/t 0xDISREL)
- IOCs shared by these feeds are
LOW-TO-MEDIUM CONFIDENCEwe strongly recommend NOT adding them to a blocklist - These could potentially be used for
THREAT HUNTINGand could be added to aWATCHLIST - IOCs are generated in
MISP COMPATIBLECSV format
- IOCs shared by these feeds are
- 2022-03-03
- Additional threat reports and vendor support resources have been added
- Updated Log4Shell IOC Threat Hunt Feeds by KPMG-Egyde CTI; not directly related to Ukraine, but still a widespread vulnerability.
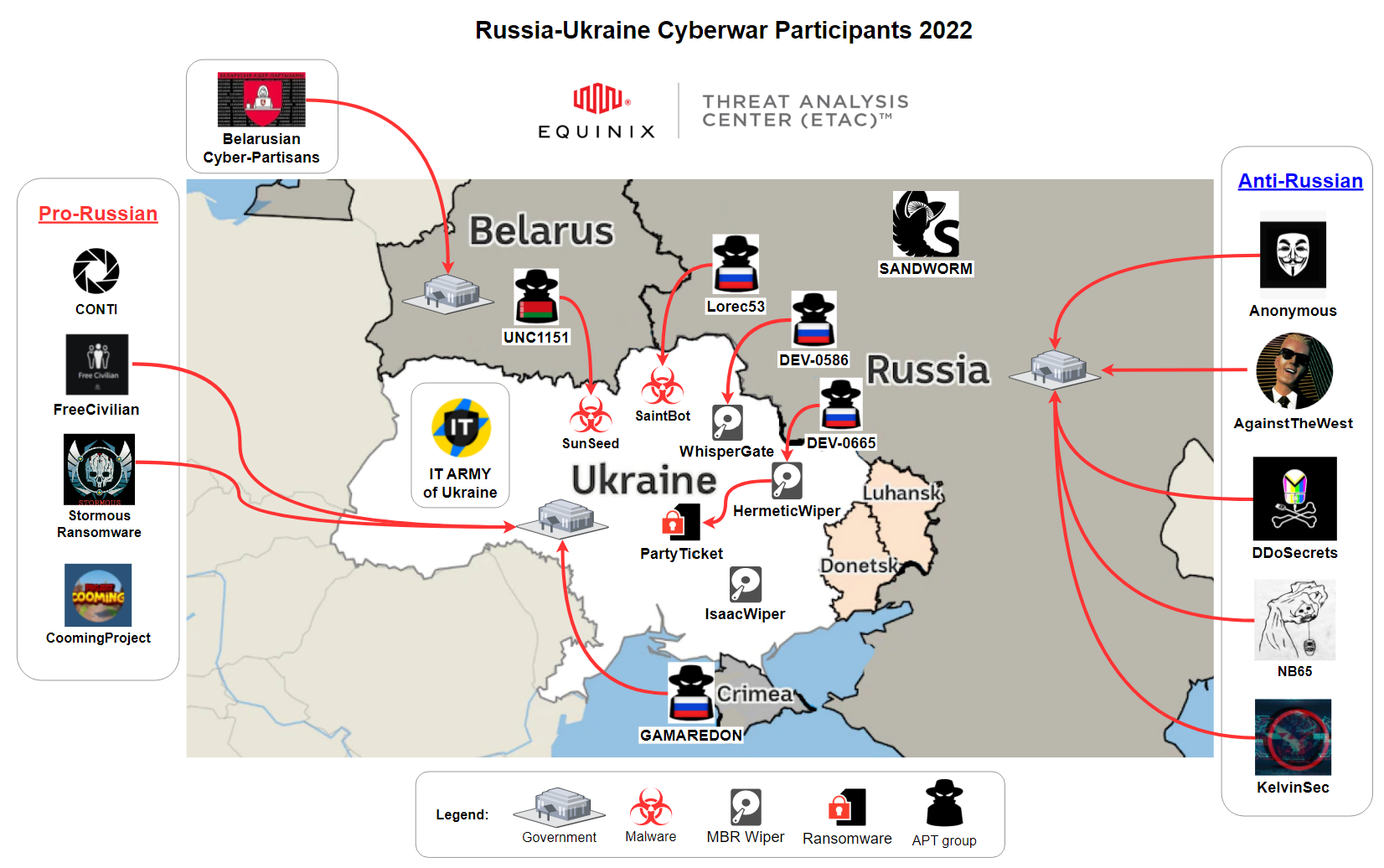
- Added diagram of Russia-Ukraine Cyberwar Participants 2022 by ETAC
- Additional IOCs have been added
- 2022-03-04
- Additional Threat Hunt Feed for recently registered Ukrainian domain names (h/t DomainTools)
- Additional Threat Hunt Feed for threat groups targeting Ukraine (h/t RecordedFuture)
- 2022-03-05
- Additional threat reports have been added
- 2022-03-06
- Additional Miscellaneous Resources for understanding the Ukraine-conflict (h/t UT CREEES)
- 2022-03-07
- Additional Threat Reports have been added
- Additional IOCs have been added
- 2022-03-08
- Additional Threat Reports have been added
- Additional IOCs have been added
- 2022-03-09
- Additional Threat Reports have been added
- Additional YARA rules have been added
- 2022-03-14
- An updated Timeline of attacks has been added
- Additional Threat Reports have been added
- Additional IOCs have been added
- Additional YARA rules have been added
- 2022-03-15
- Additional Threat Reports have been added
- Additional IOCs have been added
- 2022-03-18
- Additional Threat Reports have been added
- Additional IOCs have been added to the master CSV file
- A new CSV for CERT-UA IOCs specifically has been created - see here
- 2022-03-19
- Additional Threat Reports have been added
- Additional IOCs have been added
- 2022-03-20
- Additional YARA rules have been added (h/t Arkbird_SOLG)
- 2022-03-21
- An Additional Threat Report has been added
- Additional YARA rules have been added
- 2022-03-23
- Additional Threat Reports have been added
- Additional IOCs have been added
- 2022-03-25
- Additional Threat Reports have been added
- Additional IOCs have been added
- 2022-03-28
- Additional Threat Reports have been added
- Additional IOCs have been added
- 2022-03-30
- Additional Threat Reports have been added
- Additional YARA rules have been added
- 2022-04-01
- Additional Threat Reports have been added
- Additional Vendor Support have been added
- 2022-04-04
- Additional Threat Reports have been added
- Additional YARA rules have been added
| Date | Source | Threat(s) | URL |
|---|---|---|---|
| 14 JAN | SSU Ukraine | Website Defacements | ssu.gov.ua |
| 15 JAN | Microsoft | WhisperGate wiper (DEV-0586) | microsoft.com |
| 19 JAN | Elastic | WhisperGate wiper (Operation BleedingBear) | elastic.github.io |
| 31 JAN | Symantec | Gamaredon/Shuckworm/PrimitiveBear (FSB) | symantec-enterprise-blogs.security.com |
| 2 FEB | RaidForums | Access broker "GodLevel" offering Ukrainain algricultural exchange | RaidForums [not linked] |
| 2 FEB | CERT-UA | UAC-0056 using SaintBot and OutSteel malware | cert.gov.ua |
| 3 FEB | PAN Unit42 | Gamaredon/Shuckworm/PrimitiveBear (FSB) | unit42.paloaltonetworks.com |
| 4 FEB | Microsoft | Gamaredon/Shuckworm/PrimitiveBear (FSB) | microsoft.com |
| 8 FEB | NSFOCUS | Lorec53 (aka UAC-0056, EmberBear, BleedingBear) | nsfocusglobal.com |
| 15 FEB | CERT-UA | DDoS attacks against the name server of government websites as well as Oschadbank (State Savings Bank) & Privatbank (largest commercial bank). False SMS and e-mails to create panic | cert.gov.ua |
| 23 FEB | The Daily Beast | Ukrainian troops receive threatening SMS messages | thedailybeast.com |
| 23 FEB | UK NCSC | Sandworm/VoodooBear (GRU) | ncsc.gov.uk |
| 23 FEB | SentinelLabs | HermeticWiper | sentinelone.com |
| 24 FEB | ESET | HermeticWiper | welivesecurity.com |
| 24 FEB | Symantec | HermeticWiper, PartyTicket ransomware, CVE-2021-1636, unknown webshell | symantec-enterprise-blogs.security.com |
| 24 FEB | Cisco Talos | HermeticWiper | blog.talosintelligence.com |
| 24 FEB | Zscaler | HermeticWiper | zscaler.com |
| 24 FEB | Cluster25 | HermeticWiper | cluster25.io |
| 24 FEB | CronUp | Data broker "FreeCivilian" offering multiple .gov.ua | twitter.com/1ZRR4H |
| 24 FEB | RaidForums | Data broker "Featherine" offering diia.gov.ua | RaidForums [not linked] |
| 24 FEB | DomainTools | Unknown scammers | twitter.com/SecuritySnacks |
| 25 FEB | @500mk500 | Gamaredon/Shuckworm/PrimitiveBear (FSB) | twitter.com/500mk500 |
| 25 FEB | @500mk500 | Gamaredon/Shuckworm/PrimitiveBear (FSB) | twitter.com/500mk500 |
| 25 FEB | Microsoft | HermeticWiper | gist.github.com |
| 25 FEB | 360 NetLab | DDoS (Mirai, Gafgyt, IRCbot, Ripprbot, Moobot) | blog.netlab.360.com |
| 25 FEB | Conti [themselves] | Conti ransomware, BazarLoader | Conti News .onion [not linked] |
| 25 FEB | CoomingProject [themselves] | Data Hostage Group | CoomingProject Telegram [not linked] |
| 25 FEB | CERT-UA | UNC1151/Ghostwriter (Belarus MoD) | CERT-UA Facebook |
| 25 FEB | Sekoia | UNC1151/Ghostwriter (Belarus MoD) | twitter.com/sekoia_io |
| 25 FEB | @jaimeblascob | UNC1151/Ghostwriter (Belarus MoD) | twitter.com/jaimeblasco |
| 25 FEB | RISKIQ | UNC1151/Ghostwriter (Belarus MoD) | community.riskiq.com |
| 25 FEB | MalwareHunterTeam | Unknown phishing | twitter.com/malwrhunterteam |
| 25 FEB | ESET | Unknown scammers | twitter.com/ESETresearch |
| 25 FEB | BitDefender | Unknown scammers | blog.bitdefender.com |
| 25 FEB | SSSCIP Ukraine | Unkown phishing | twitter.com/dsszzi |
| 25 FEB | RaidForums | Data broker "NetSec" offering FSB (likely SMTP accounts) | RaidForums [not linked] |
| 25 FEB | Zscaler | PartyTicket decoy ransomware | zscaler.com |
| 25 FEB | INCERT GIE | Cyclops Blink, HermeticWiper | linkedin.com [Login Required] |
| 25 FEB | Proofpoint | UNC1151/Ghostwriter (Belarus MoD) | twitter.com/threatinsight |
| 25 FEB | @fr0gger_ | HermeticWiper capabilities Overview | twitter.com/fr0gger_ |
| 25 FEB | Netskope | HermeticWiper analysis | netskope.com |
| 26 FEB | BBC Journalist | A fake Telegram account claiming to be President Zelensky is posting dubious messages | twitter.com/shayan86 |
| 26 FEB | CERT-UA | UNC1151/Ghostwriter (Belarus MoD) | CERT_UA Facebook |
| 26 FEB | MHT and TRMLabs | Unknown scammers, linked to ransomware | twitter.com/joes_mcgill |
| 26 FEB | US CISA | WhisperGate wiper, HermeticWiper | cisa.gov |
| 26 FEB | Bloomberg | Destructive malware (possibly HermeticWiper) deployed at Ukrainian Ministry of Internal Affairs & data stolen from Ukrainian telecommunications networks | bloomberg.com |
| 26 FEB | Vice Prime Minister of Ukraine | IT ARMY of Ukraine created to crowdsource offensive operations against Russian infrastructure | twitter.com/FedorovMykhailo |
| 26 FEB | Yoroi | HermeticWiper | yoroi.company |
| 27 FEB | LockBit [themselves] | LockBit ransomware | LockBit .onion [not linked] |
| 27 FEB | ALPHV [themselves] | ALPHV ransomware | vHUMINT [closed source] |
| 27 FEB | Mēris Botnet [themselves] | DDoS attacks | vHUMINT [closed source] |
| 28 FEB | Horizon News [themselves] | Leak of China's Censorship Order about Ukraine | techarp.com |
| 28 FEB | Microsoft | FoxBlade (aka HermeticWiper) | blogs.microsoft.com |
| 28 FEB | @heymingwei | Potential BGP hijacks attempts against Ukrainian Internet Names Center | twitter.com/heymingwei |
| 28 FEB | @cyberknow20 | Stormous ransomware targets Ukraine Ministry of Foreign Affairs | twitter.com/cyberknow20 |
| 1 MAR | ESET | IsaacWiper and HermeticWizard | welivesecurity.com |
| 1 MAR | Proofpoint | Ukrainian armed service member's email compromised and sent malspam containing the SunSeed malware (likely TA445/UNC1151/Ghostwriter) | proofpoint.com |
| 1 MAR | Elastic | HermeticWiper | elastic.github.io |
| 1 MAR | CrowdStrike | PartyTicket (aka HermeticRansom), DriveSlayer (aka HermeticWiper) | CrowdStrike |
| 2 MAR | Zscaler | DanaBot operators launch DDoS attacks against the Ukrainian Ministry of Defense | zscaler.com |
| 2 MAR | Infoblox | Ukrainian Support Fraud | blogs.infoblox.com |
| 2 MAR | Trellix | Digging into HermeticWiper | trellix.com |
| 2 MAR | Port Swigger | Ukraine invasion: WordPress-hosted university websites hacked in ‘targeted attacks’ | portswigger.net |
| 3 MAR | @ShadowChasing1 | Gamaredon/Shuckworm/PrimitiveBear (FSB) | twitter.com/ShadowChasing1 |
| 3 MAR | @vxunderground | News website in Poland was reportedly compromised and the threat actor uploaded anti-Ukrainian propaganda | twitter.com/vxunderground |
| 3 MAR | @kylaintheburgh | Russian botnet on Twitter is pushing "#istandwithputin" and "#istandwithrussia" propaganda (in English) | twitter.com/kylaintheburgh |
| 3 MAR | @tracerspiff | UNC1151/Ghostwriter (Belarus MoD) | twitter.com |
| 3 MAR | Trustwave | Gorenie Fundraising Email Scams | trustwave.com |
| 3 MAR | Trend Micro | Prominent Cyber Attacks in Russia-Ukraine Conflict | trendmicro.com |
| 3 MAR | U.S. DoT | Press Releases: Treasury Sanctions Russians Bankrolling Putin and Russia-Backed Influence Actors | treasury.gov |
| 3 MAR | Microsoft MSTIC | DEV-0586 (aka WhisperGate), DEV-0665 (aka FoxBlade/HermeticWizard/HermeticWiper), SonicVote (aka HermeticRansom & PartyTicket), Lasainraw (aka IsaacWiper) | twitter.com/MalwareRE |
| 4 MAR | Interfax | CERT-UA warns about mass mailings of malicious software | interfax.com.ua |
| 4 MAR | eln0ty | HermeticWiper/FoxBlade Analysis (in-depth) | eln0ty.github.io |
| 4 MAR | Mandiant | Sandworm, UNC2589 (aka Lorec53/UAC-0056/EmberBear), UNC3715 (aka DEV-0665/HermeticWiper), and potentially TEMP.Isotope (aka BerserkBear/EnergeticBear/Dragonfly) | mandiant.com |
| 5 MAR | SSSCIP Ukraine | Russian DDos attacks (100 Gbps at their peak) primarily aimed at the resources of Verkhovna Rada, Cabinet of Ministers, President of Ukraine, Defense Ministry and Internal Affairs Ministry | twitter.com/dsszzi |
| 6 MAR | @shakirov2036 | Notice Russian Government Websites To move to domestic hosting thread | twitter.com/shakirov2036 |
| 7 MAR | ReverseMode | SATCOM terminals under attack in Europe: plausible analysis | reversemode.com |
| 7 MAR | Google TAG | FancyBear (aka APT28) targeted users of UkrNet (a Ukrainian media company), Ghostwriter (aka UNC1151), Mustang Panda (aka Temp.Hex), DDoS attacks | blog.google |
| 7 MAR | CERT-UA | UAC-0051 (aka UNC1151), MicroBackdoor, CVE-2019-0541 | cert.gov.ua |
| 8 MAR | Cluster25 | UNC1151/Ghostwriter (Belarus MoD) | cluster25.io |
| 8 MAR | Trend Micro | RURansom - a data wiper targeting Russian organizations | trendmicro.com |
| 9 MAR | ReversingLabs | HermeticWiper and IsaacWiper | blog.reversinglabs.com |
| 11 MAR | CERT-UA | UAC-0056 (aka Lorec53, EmberBear) push fake antivirus updates containing Cobalt Strike Beacons, GrimImplant, and GraphSteel malspam against state authorities of Ukraine | cert.gov.ua |
| 11 MAR | Infosec Magazine | pro-Ukrainian actors should be wary of downloading DDoS tools to attack Russia, as they may be booby-trapped with info-stealing malware | infosecurity-magazine.com |
| 11 MAR | @cyberknow20 | "Xahnet" shared a video they allegedly left a message and defaced the main page of Ukraine's capital bank [unvalidated] | twitter.com/cyberknow20 |
| 13 MAR | Spiegel | German Anonymous hacktivists target Rosneft Germany, allegedly stole 20TB of data, deleted 59 Apple devices remotely, and left "Slava Ukraini" on wiped systems | spiegel.de |
| 13 MAR | BeeHive | Twitter user "BeeHive" allegedly exploited a vulnerability in the open-source ADS-B radar reporting feeds and digital transponders to manipulate Russian airlines, causing Aeroflot planes to erroneously squawk "7700" (for emergencies) and display anti-Russian callsigns on flight radars | twitter.com/BeeHiveCyberSec |
| 14 MAR | Cisco Talos | Opportunistic cybercriminals take advantage of Ukraine invasion | blog.talosintelligence.com |
| 14 MAR | ESET | Another wiper was discovered targeting Ukraine, dubbed CaddyWiper, which was delivered via GPO, indicating the adversary had prior control of the target's network beforehand. CaddyWiper is seeminginly not connected to other the wipers targeting Ukraine, including Whispergate, HermeticWiper, or IsaacWiper | twitter.com/ESETresearch |
| 15 MAR | VICE | The Security Service of Ukraine (SBU) detained a “hacker” who provided assistance to Russian troops in Ukraine by routing phone calls on their behalf, and sent text messages to Ukrainian security forces suggesting they surrender | vice.com |
| 15 MAR | SentinelOne | Threat Actor UAC-0056 Targeting Ukraine with Fake Translation Software | sentinelone.com/blog |
| 16 MAR | CERT-UA | QR code phishing posing as UKR.NET linked to UAC-0028 group (APT28/FancyBear/GRU) | cert.gov.ua |
| 17 MAR | CERT-UA | UAC-0020 (Vermin) cyberattack on Ukrainian state organizations using the SPECTR malware, whose activities are associated with the so-called security agencies of the so-called "Luhansk People's Republic" | cert.gov.ua |
| 18 MAR | CERT-UA | UAC-0035 (InvisiMole) cyberattack on State Organizations of Ukraine | cert.gov.ua |
| 22 MAR | CERT-UA | UAC-0088 deploys DoubleZero wiper | cert.gov.ua |
| 22 MAR | CERT-UA | UAC-0026 cyberattack using HeaderTip malware, linked to Scarab APT | cert.gov.ua |
| 23 MAR | Interfax UA | Datagroup, a provider of fiber-optic infrastructure and digital services, resolved more than 350 DDoS attacks on the country's telecommunications network during the month of the war. The largest attack was 103.6 Gbps, 28.0 Mpps; the most powerful attack was 27.6 Gbps, 43.0 Mpps; the longest attack was 24 days. | interfax.com.ua |
| 23 MAR | BalkanInsight | Croatian police are probing the hacking of the ‘Slobodna Dalmacija’ website, where hackers replaced content with pro-Russian articles on Ukraine. “Western Deception Machine”, “Which Side Are You On?”, and “The United States of America Admitted They Have Hidden Laboratories in Ukraine”, are just some of the fake articles that the hackers posted online. | balkaninsight.com |
| 23 MAR | CERT-UA | UAC-0051 group (UNC1151/GhostWriter), Cobalt Strike Beacons | cert.gov.ua |
| 24 MAR | SentinelOne | Ukraine CERT (CERT-UA) has released new details on UAC-0026, which SentinelLabs confirms is associated with the suspected Chinese threat actor known as Scarab. Scarab has conducted a number of campaigns over the years, making use of a custom backdoor originally known as Scieron, which may be the predecessor to HeaderTip. | sentinelone.com |
| 24 MAR | Lab52 | Quasar RAT spear-phishing campaign | lab52.io |
| 25 MAR | SSSCIP Ukraine | Who is behind the Cyberattacks on Ukraine's Critical Information Infrastructure: Statistics for March 15-22 | cip.gov.ua |
| 25 MAR | SSSCIP Ukraine | Statistics of Cyber Attacks on Ukrainian Critical Information Infrastructure: 15-22 March | cip.gov.ua |
| 26 MAR | @n0p | Analysis of a Caddy Wiper Sample | n0p.me |
| 28 MAR | CERT-UA | Cyberattack on Ukrainian state authorities using pseudoSteel malware linked to UAC-0010 (Armageddon/Gamaredon) | cert.gov.ua |
| 28 MAR | Cyber, etc | Ukraine's largest fix-line telecommunications operator hit by cyber attack | Cyber, etc |
| 28 MAR | SSSCIP Ukraine | Cyberattack against Ukrtelecom IT-infrastructure and recovery | twitter.com/ dsszzi |
| 28 MAR | CERT-UA | GraphSteel and GrimPlant, UAC-0056 | cert.gov.ua |
| 29 MAR | Newsweek | U.S. Airport hit with Cyberattack over Ukraine | Newsweek |
| 29 MAR | ZDnet | The Security Service of Ukraine (SBU) has destroyed five "enemy" bot farms engaged in activities to frighten Ukrainian citizens. In a March 28 release, the SBU said that the bot farms had an overall capacity of at least 100,000 accounts spreading misinformation and fake news surrounding Russia's invasion of Ukraine | zdnet.com |
| 30 MAR | Viasat | Viasat is providing an overview and incident report on the cyber-attack against the KA-SAT network, which occurred on 24 February 2022, and resulted in a partial interruption of KA-SAT's consumer-oriented satellite broadband service. | viasat.com |
| 30 MAR | CrowdStrike | EMBER BEAR (aka UAC-0056, Lorec53, Lorec Bear, Bleeding Bear, Saint Bear) | crowdstrike.com |
| 30 MAR | CERT-UA | MarsStealer, UAC-0041 | cert.gov.ua |
| 30 MAR | Google TAG | Curious Gorge (APT from China), COLDRIVER (APT from Russia), Ghostwriter (APT from Belarus) | blog.google |
| 30 MAR | Viasat | KA-SAT Network cyber attack overview | viasat.com |
| 30 MAR | InQuest | CloudAtlas APT group linked to a maldoc impersonating the United States Securities and Exchange Commission | inquest.net |
| 31 MAR | ReverseMode | VIASAT incident: from speculation to technical details | reversemode.com |
| 31 MAR | SentinelLabs | AcidRain IoT Wiper (ELF MIPS), connected to the VPNFilter stage 3 destructive plugin | sentinelone.com |
| 1 APR | Malwarebytes | UAC-0056 (aka SaintBear, UNC2589 and TA471) is a cyber espionage actor that has been active since early 2021 and has mainly targeted Ukraine and Georgia | blog.malwarebytes.com |
| 3 APR | me | Low-detect BlackGuard infostealer uploaded to AnyRun from Ukraine | twitter.com/BushidoToken |
| 4 APR | CERT-UA | UAC-0010 (Armageddon) cyberattack on Ukrainian state organizations, phishing w/ RAR -> HTA -> VBS | cert.gov.ua |
| Date | Threat(s) | Source |
|---|---|---|
| 23 JAN | Access broker "Mont4na" offering UkrFerry | RaidForums [not linked] |
| 23 JAN | Access broker "Mont4na" offering PrivatBank | RaidForums [not linked] |
| 24 JAN | Access broker "Mont4na" offering DTEK | RaidForums [not linked] |
| 27 FEB | KelvinSecurity Sharing list of IP cameras in Ukraine | vHUMINT [closed source] |
| 28 FEB | "w1nte4mute" looking to buy access to UA and NATO countries (likely ransomware affiliate) | vHUMINT [closed source] |
| Threat Actor | Type | Observation | Validated | Relevance | Source |
|---|---|---|---|---|---|
| aguyinachair | UA data sharing | PII DB of ukraine.com (shared as part of a generic compilation) | No | TA discussion in past 90 days | ELeaks Forum [not linked] |
| an3key | UA data sharing | DB of Ministry of Communities and Territories Development of Ukraine (minregion[.]gov[.]ua) | No | TA discussion in past 90 days | RaidForums [not linked; site hijacked since UA invasion] |
| an3key | UA data sharing | DB of Ukrainian Ministry of Internal Affairs (wanted[.]mvs[.]gov[.]ua) | No | TA discussion in past 90 days | RaidForums [not linked; site hijacked since UA invasion] |
| CorelDraw | UA data sharing | PII DB (40M) of PrivatBank customers (privatbank[.]ua) | No | TA discussion in past 90 days | RaidForums [not linked; site hijacked since UA invasion] |
| CorelDraw | UA data sharing | DB of "border crossing" DBs of DPR and LPR | No | TA discussion in past 90 days | RaidForums [not linked; site hijacked since UA invasion] |
| CorelDraw | UA data sharing | PII DB (7.5M) of Ukrainian passports | No | TA discussion in past 90 days | RaidForums [not linked; site hijacked since UA invasion] |
| CorelDraw | UA data sharing | PII DB of Ukrainian car registration, license plates, Ukrainian traffic police records | No | TA discussion in past 90 days | RaidForums [not linked; site hijacked since UA invasion] |
| CorelDraw | UA data sharing | PII DB (2.1M) of Ukrainian citizens | No | TA discussion in past 90 days | RaidForums [not linked; site hijacked since UA invasion] |
| CorelDraw | UA data sharing | PII DB (28M) of Ukrainian citizens (passports, drivers licenses, photos) | No | TA discussion in past 90 days | RaidForums [not linked; site hijacked since UA invasion] |
| CorelDraw | UA data sharing | PII DB (1M) of Ukrainian postal/courier service customers (novaposhta[.]ua) | No | TA discussion in past 90 days | RaidForums [not linked; site hijacked since UA invasion] |
| CorelDraw | UA data sharing | PII DB (10M) of Ukrainian telecom customers (vodafone[.]ua) | No | TA discussion in past 90 days | RaidForums [not linked; site hijacked since UA invasion] |
| CorelDraw | UA data sharing | PII DB (3M) of Ukrainian telecom customers (lifecell[.]ua) | No | TA discussion in past 90 days | RaidForums [not linked; site hijacked since UA invasion] |
| CorelDraw | UA data sharing | PII DB (13M) of Ukrainian telecom customers (kyivstar[.]ua) | No | TA discussion in past 90 days | RaidForums [not linked; site hijacked since UA invasion] |
| danieltx51 | UA data sharing | DB of Ministry of Foreign Affairs of Ukraine (mfa[.]gov[.]ua) | No | TA discussion in past 90 days | RaidForums [not linked; site hijacked since UA invasion] |
| DueDiligenceCIS | UA data sharing | PII DB (63M) of Ukrainian citizens (name, DOB, birth country, phone, TIN, passport, family, etc) | No | TA discussion in past 90 days | RaidForums [not linked; site hijacked since UA invasion] |
| Featherine | UA data sharing | DB of Ukrainian 'Diia' e-Governance Portal for Ministry of Digital Transformation of Ukraine | No | TA discussion in past 90 days | RaidForums [not linked; site hijacked since UA invasion] |
| FreeCivilian | UA data sharing | DB of Ministry for Internal Affairs of Ukraine public data search engine (wanted[.]mvs[.]gov[.]ua) | No | TA discussion in past 90 days | RaidForums [not linked; site hijacked since UA invasion] |
| FreeCivilian | UA data sharing | DB of Ministry for Communities and Territories Development of Ukraine (minregion[.]gov[.]ua) | No | TA discussion in past 90 days | RaidForums [not linked; site hijacked since UA invasion] |
| FreeCivilian | UA data sharing | DB of Motor Insurance Bureau of Ukraine (mtsbu[.]ua) | No | TA discussion in past 90 days | RaidForums [not linked; site hijacked since UA invasion] |
| FreeCivilian | UA data sharing | PII DB of Ukrainian digital-medicine provider (medstar[.]ua) | No | TA discussion in past 90 days | RaidForums [not linked; site hijacked since UA invasion] |
| FreeCivilian | UA data sharing | DB of ticket.kyivcity.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of id.kyivcity.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of my.kyivcity.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of portal.kyivcity.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of anti-violence-map.msp.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of dopomoga.msp.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of e-services.msp.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of edu.msp.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of education.msp.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of ek-cbi.msp.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of mail.msp.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of portal-gromady.msp.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of web-minsoc.msp.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of wcs-wim.dsbt.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of bdr.mvs.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of motorsich.com | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of dsns.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of mon.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of minagro.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of zt.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of kmu.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of mvs.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of dsbt.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of forest.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of nkrzi.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of dabi.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of comin.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of dp.dpss.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of esbu.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of mms.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of mova.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of mspu.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of nads.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of reintegration.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of sies.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of sport.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of mepr.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of mfa.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of va.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of mtu.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of cg.mvs.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of ch-tmo.mvs.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of cp.mvs.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of cpd.mvs.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of hutirvilnij-mrc.mvs.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of dndekc.mvs.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of visnyk.dndekc.mvs.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of dpvs.hsc.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of odk.mvs.gov.ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of e-driver[.]hsc[.]gov[.]ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of wanted[.]mvs[.]gov[.]ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of minregeion[.]gov[.]ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of health[.]mia[.]solutions | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of mtsbu[.]ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of motorsich[.]com | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of kyivcity[.]com | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of bdr[.]mvs[.]gov[.]ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of gkh[.]in[.]ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of kmu[.]gov[.]ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of mon[.]gov[.]ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of minagro[.]gov[.]ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| FreeCivilian | UA data sharing | DB of mfa[.]gov[.]ua | No | TA discussion in past 90 days | FreeCivilian .onion [not linked] |
| Intel_Data | UA data sharing | PII DB (56M) of Ukrainian Citizens | No | TA discussion in past 90 days | RaidForums [not linked; site hijacked since UA invasion] |
| Kristina | UA data sharing | DB of Ukrainian National Police (mvs[.]gov[.]ua) | No | TA discussion in past 90 days | RaidForums [not linked; site hijacked since UA invasion] |
| NetSec | UA data sharing | PII DB (53M) of Ukrainian citizens | No | TA discussion in past 90 days | RaidForums [not linked; site hijacked since UA invasion] |
| Psycho_Killer | UA data sharing | PII DB (56M) of Ukrainian Citizens | No | TA discussion in past 90 days | Exploit Forum .onion [not linked] |
| Sp333 | UA data sharing | PII DB of Ukrainian and Russian interpreters, translators, and tour guides | No | TA discussion in past 90 days | RaidForums [not linked; site hijacked since UA invasion] |
| Vaticano | UA data sharing | DB of Ukrainian 'Diia' e-Governance Portal for Ministry of Digital Transformation of Ukraine [copy] | No | TA discussion in past 90 days | RaidForums [not linked; site hijacked since UA invasion] |
| Vaticano | UA data sharing | DB of Ministry for Communities and Territories Development of Ukraine (minregion[.]gov[.]ua) [copy] | No | TA discussion in past 90 days | RaidForums [not linked; site hijacked since UA invasion] |
| Vendor | Offering | URL |
|---|---|---|
| Dragos | Access to Dragos service if from US/UK/ANZ and in need of ICS cybersecurity support | twitter.com/RobertMLee |
| GreyNoise | Any and all Ukrainian emails registered to GreyNoise have been upgraded to VIP which includes full, uncapped enterprise access to all GreyNoise products. There is a landing page for GreyNoise data at https://www.greynoise.io/viz/pulse |
twitter.com/Andrew___Morris |
| Recorded Future | Providing free intelligence-driven insights, perspectives, and mitigation strategies as the situation in Ukraine evolves | recordedfuture.com |
| Flashpoint | Free Access to Flashpoint’s Latest Threat Intel on Ukraine | go.flashpoint-intel.com |
| ThreatABLE | A Ukraine tag for free threat intelligence feed that's more highly curated to cyber | twitter.com/threatable |
| Orange | IOCs related to Russia-Ukraine 2022 conflict extracted from our Datalake Threat Intelligence platform. | github.com/Orange-Cyberdefense |
| FSecure | F-Secure FREEDOME VPN is now available for free in all of Ukraine | twitter.com/FSecure |
| Multiple vendors | List of vendors offering their services to Ukraine for free, put together by @chrisculling | docs.google.com/spreadsheets |
| Mandiant | Free threat intelligence, webinar and guidance for defensive measures relevant to the situation in Ukraine. | mandiant.com |
| Starlink | Satellite internet constellation operated by SpaceX providing satellite Internet access coverage to Ukraine | twitter.com/elonmusk |
| Romania DNSC | Romania’s DNSC – in partnership with Bitdefender – will provide technical consulting, threat intelligence and, free of charge, cybersecurity technology to any business, government institution or private citizen of Ukraine for as long as it is necessary. | Romania's DNSC Press Release |
| BitDefender | Access to Bitdefender technical consulting, threat intelligence and both consumer and enterprise cybersecurity technology | bitdefender.com/ukraine/ |
| NameCheap | Free anonymous hosting and domain name registration to any anti-Putin anti-regime and protest websites for anyone located within Russia and Belarus | twitter.com/Namecheap |
| Avast | Free decryptor for PartyTicket ransomware | decoded.avast.io |
| Recorded Future | Insikt Group’s list of indicators of compromise associated with threat actors and malware related to the Russian cyber actions against Ukraine | recordedfuture.com |
| CybelAngel | CybelAngel offers its services to interested NGOs active in the war at no cost, to minimize the risks of their missions being interrupted by cyber attacks. CybelAngel also offers Ukrainian companies an assessment of their digital exposure in the region at no charge. | cybelangel.com |
| Malware Patrol | Free 6 months DNS Firewall service subscription for Ukraine-based companies and goverment entities | www.linkedin.com |
| UnderDefense | UnderDefense is providing Managed Detection & Response services and incident repsonse support for Ukrainian critical infrastructure & government consulting in cybersecurity | underdefense.com |
| Handle | Affiliation |
|---|---|
| @KyivIndependent | English-language journalism in Ukraine |
| @IAPonomarenko | Defense reporter with The Kyiv Independent |
| @KyivPost | English-language journalism in Ukraine |
| @Shayan86 | BBC World News Disinformation journalist |
| @Liveuamap | Live Universal Awareness Map (“Liveuamap”) independent global news and information site |
| @DAlperovitch | The Alperovitch Institute for Cybersecurity Studies, Founder & Former CTO of CrowdStrike |
| @COUPSURE | OSINT investigator for Centre for Information Resilience |
| @netblocks | London-based Internet's Observatory |
| Source | URL | Content |
|---|---|---|
| PowerOutages.com | https://poweroutage.com/ua | Tracking PowerOutages across Ukraine |
| Monash IP Observatory | https://twitter.com/IP_Observatory | Tracking IP address outages across Ukraine |
| Project Owl Discord | https://discord.com/invite/projectowl | Tracking foreign policy, geopolitical events, military and governments, using a Discord-based crowdsourced approach, with a current emphasis on Ukraine and Russia |
| russianwarchatter.info | https://www.russianwarchatter.info/ | Known Russian Military Radio Frequencies |
| UT CREEES | https://liberalarts.utexas.edu/slavic/resources/ukraine-conflict-resources.php | Compiled resources to help understand the Russian invasion of Ukraine, with links to resources, action items, and academic sources |
Curated Intel does not support, encourage, partake, or condone hacking, attacking or targeting users of any kind. This information is clearly meant to help cybersecurity teams supporting Ukraine still doing their jobs while dealing with the Russian invasion.