Network policies can be created to control the traffic between network entities on the Kubernetes cluster. When we create a NetPol, we specify which pods we want to control the traffic of using the labels of the pod.
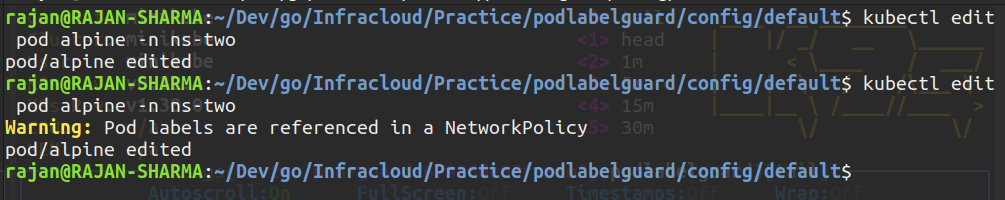
This is an application that makes sure that as soon as a pod's labels are edited and those labels are being referred in a NetPol, users should be warned that the labels are being used in a NetPol and the labels should not be edited.
kubebuilder init --domain secure.podlabel --repo github.com/Rajan-226/podlabelguard
kubebuilder create api --group core --version v1 --kind Pod --resource=false --controller=false
kubebuilder create webhook --group core --version v1 --kind Pod --programmatic-validation
openssl req -x509 -newkey rsa:4096 -keyout tls.key -out tls.crt -days 365 -nodes -subj "/CN=pod-guard.ns-two.svc" -addtext "subjectAltName=DNS:pod-guard.ns-two.svc"
#SAN is important for k8s certs ^
kubectl create secret tls podlabelguard-secret --cert=tls.crt --key=tls.key -n ns-two --dry-run=client -oyaml>podlabelguard-secret.yaml
docker build -t rajan226/podlabelguard:0.1.1 .
docker push rajan226/podlabelguard:0.1.1
build docker image -> push image to registry
- Create secret object using ssl certs with service X in SAN
- Create deployment Y with above image with secrets mounted
- Create service X for deployment Y
- Create clusterrole and clusterrolebinding for deployment Y's service account
- Create ValidatingWebhookConfiguration object with suitable webhook endpoint and service name of deployment Y
- Create test pod and coresponding test network policy
- Edit test pod's labels and play around
- go version v1.22.0+
- docker version 17.03+.
- kubectl version v1.11.3+.
- Access to a Kubernetes v1.11.3+ cluster.
Build and push your image to the location specified by IMG:
make docker-build docker-push IMG=<some-registry>/podlabelguard:tagNOTE: This image ought to be published in the personal registry you specified. And it is required to have access to pull the image from the working environment. Make sure you have the proper permission to the registry if the above commands don’t work.
Install the CRDs into the cluster:
make installDeploy the Manager to the cluster with the image specified by IMG:
make deploy IMG=<some-registry>/podlabelguard:tagNOTE: If you encounter RBAC errors, you may need to grant yourself cluster-admin privileges or be logged in as admin.
Create instances of your solution You can apply the samples (examples) from the config/sample:
kubectl apply -k config/samples/NOTE: Ensure that the samples has default values to test it out.
Delete the instances (CRs) from the cluster:
kubectl delete -k config/samples/Delete the APIs(CRDs) from the cluster:
make uninstallUnDeploy the controller from the cluster:
make undeployFollowing are the steps to build the installer and distribute this project to users.
- Build the installer for the image built and published in the registry:
make build-installer IMG=<some-registry>/podlabelguard:tagNOTE: The makefile target mentioned above generates an 'install.yaml' file in the dist directory. This file contains all the resources built with Kustomize, which are necessary to install this project without its dependencies.
- Using the installer
Users can just run kubectl apply -f to install the project, i.e.:
kubectl apply -f https://raw.githubusercontent.com/<org>/podlabelguard/<tag or branch>/dist/install.yaml// TODO(user): Add detailed information on how you would like others to contribute to this project
NOTE: Run make help for more information on all potential make targets
More information can be found via the Kubebuilder Documentation
Copyright 2024.
Licensed under the Apache License, Version 2.0 (the "License"); you may not use this file except in compliance with the License. You may obtain a copy of the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software distributed under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the License for the specific language governing permissions and limitations under the License.