A SimpleSAMLphp module adding support for the OpenID Connect protocol.
This module adds support for the OpenID Connect protocol through a SimpleSAMLphp module installable through Composer.
Installation can be as easy as executing:
composer require rediris-es/simplesamlphp-module-oidc
Edit your config/config.php and check you configured at least the next parameters from the database section:
'database.dsn' => 'mysql:host=server;dbname=simplesamlphp',
'database.username' => 'user',
'database.password' => 'password',
This module used the new twig template system, so you need to configure the next option in config/config.php:
'language.i18n.backend' => 'gettext/gettext',
Copy the template file to the config directory:
cp modules/oidc/config-template/module_oidc.php config/
and edit it. The options are self explained.
This module support the basic OIDC scopes: openid, email, address, phone and profile. You can add your own private scopes in the module_oidc.php config file:
<?php
$config = [
'scopes' => [
'private' => [
'description' => 'private scope',
'attributes' => ['national_document_id']
],
],
];We have a default translation table from SAML attributes to OIDC claims, based on this REFEDS wiki article: "Mapping SAML attributes to OIDC Claims".
You can change or extend this table from module_oidc.php config file:
<?php
$config = [
'translate' => [
// Overwrite default translation
'sub' => [
'uid', // added
'eduPersonPrincipalName',
'eduPersonTargetedID',
'eduPersonUniqueId',
],
// Remove default translation
'family_name' => [
],
// New claim created from SAML attribute
// Used in previus private scope
'national_document_id' => [
'schacPersonalUniqueId',
],
],
];This module requires cron module is active to remove old tokens.
The oidc library used generates Json Web Tokens to create the Access Tokens, so you need to create a public and private cert keys.
To generate the private key run this command on the terminal:
openssl genrsa -out cert/oidc_module.pem 1024
If you want to provide a passphrase for your private key run this command instead:
openssl genrsa -passout pass:myPassPhrase -out cert/oidc_module.pem 1024
Now you need to extract the public key from the private key:
openssl rsa -in cert/oidc_module.pem -pubout -out cert/oidc_module.crt
or use your passphrase if provided on private key generation:
openssl rsa -in cert/oidc_module.pem -passin pass:myPassPhrase -pubout -out cert/oidc_module.crt
If you use a passphrase remember to configure it in the module_oidc.php config file.
First, you need to create the database schema. The module detects if the schema is not created or updated.
Open the Federation tab from your SimpleSAMLphp installation and select the option OpenID Connect Installation inside the Tools section.
All you need to do is press the Install button and the schema will be created. If you have a legacy oauth2 module installed, the installation page will ask if you want to migrate the date.
This module offers a OpenID Connect Autodiscovery endpoint in the next url:
https://yourserver/simplesaml/module.php/oidc/openid-configuration.php
If you want to know all the module endpoints, check that url.
If you want to have a canonical https://yourserver/.well-known/openid-configuration url for this service you can add this to your nginx server configuration:
location = /.well-known/openid-configuration {
rewrite ^(.*)$ /simplesaml/module.php/oidc/openid-configuration.php break;
proxy_pass https://localhost;
}
This module is based on Oauth2 Server from the PHP League and only supports implicit and explicit tokens.
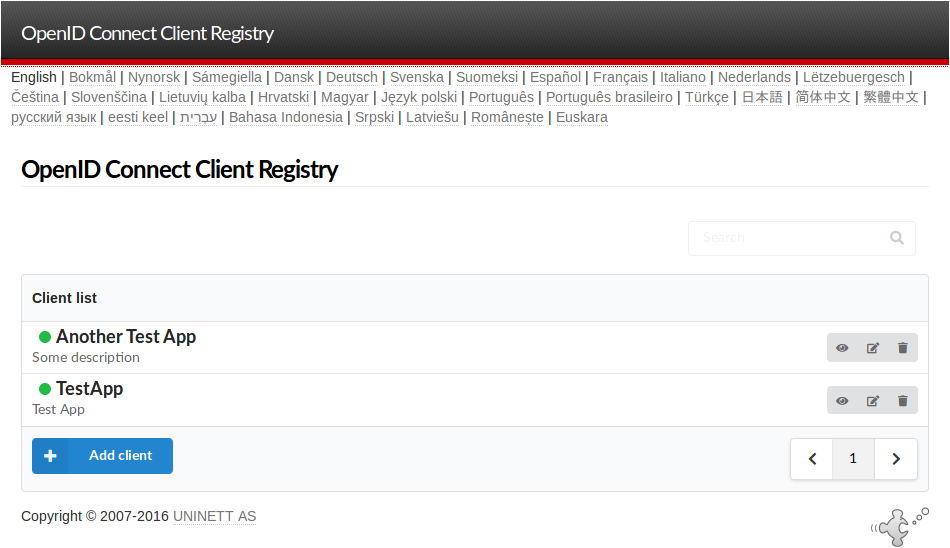
Once the database schema has been created, you can open the Federation tab from your SimpleSAMLphp installation and select the option OpenID Connect Client Registry inside the Tools section.
The module lets you create, read, update and delete all the RP you want. To see the client id and the client secret press the show button.