In this tutorial, we observe various network traffic to and from Azure Virtual Machines with Wireshark as well as experiment with Network Security Groups.
- Microsoft Azure (Virtual Machines/Compute)
- Remote Desktop
- Various Command-Line Tools
- Various Network Protocols (SSH, RDP, DNS, HTTP/S, ICMP)
- Wireshark (Protocol Analyzer)
- Windows 10 Pro (22H2)
- Ubuntu Server 20.04
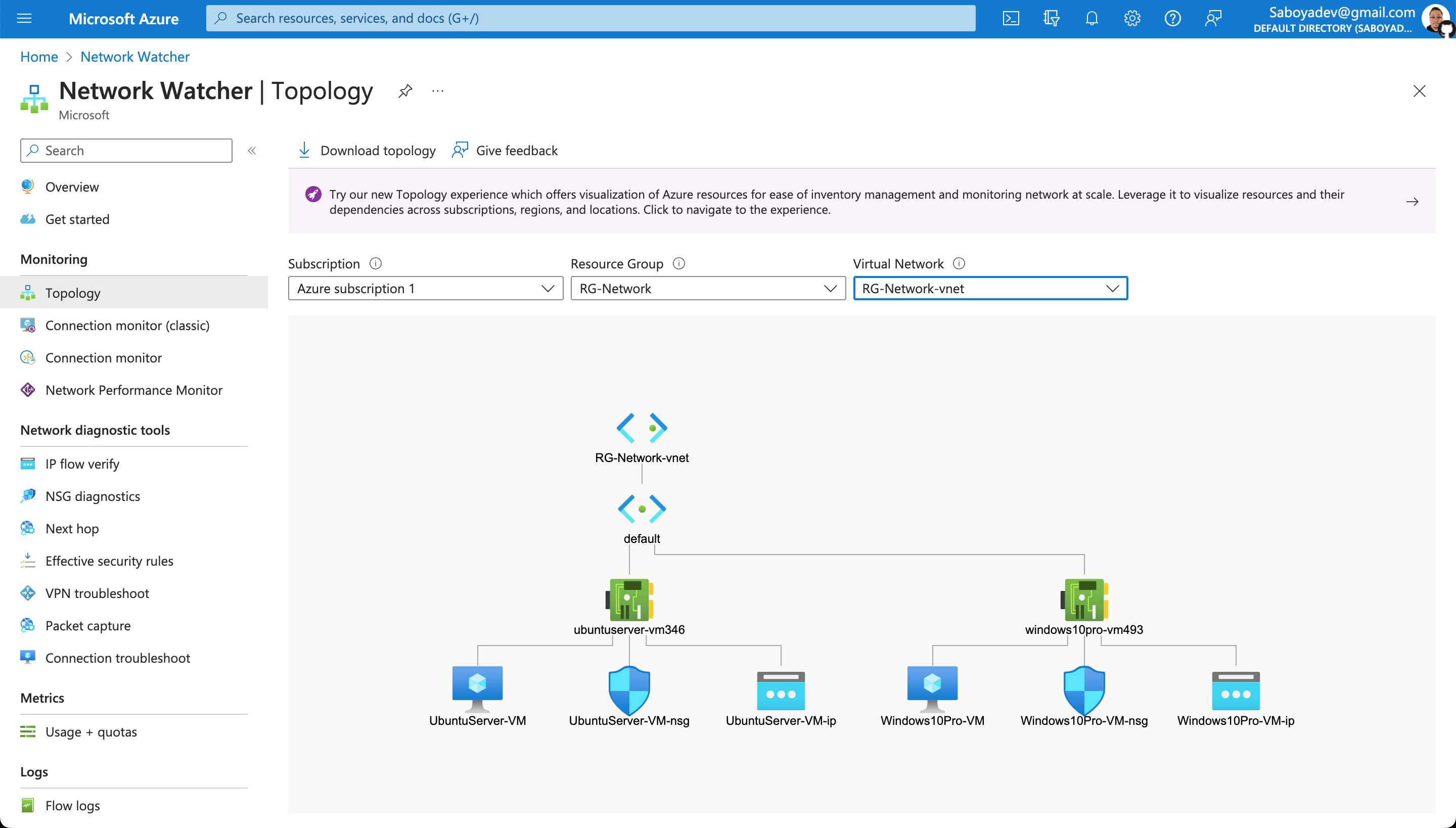
- Create Resources
- Observe ICMP Traffic
- Observe SSH Traffic
- Observe DHCP Traffic
- Observe DNS Traffic
- Observe RDP Traffic
- Observe HTTP/S Traffic
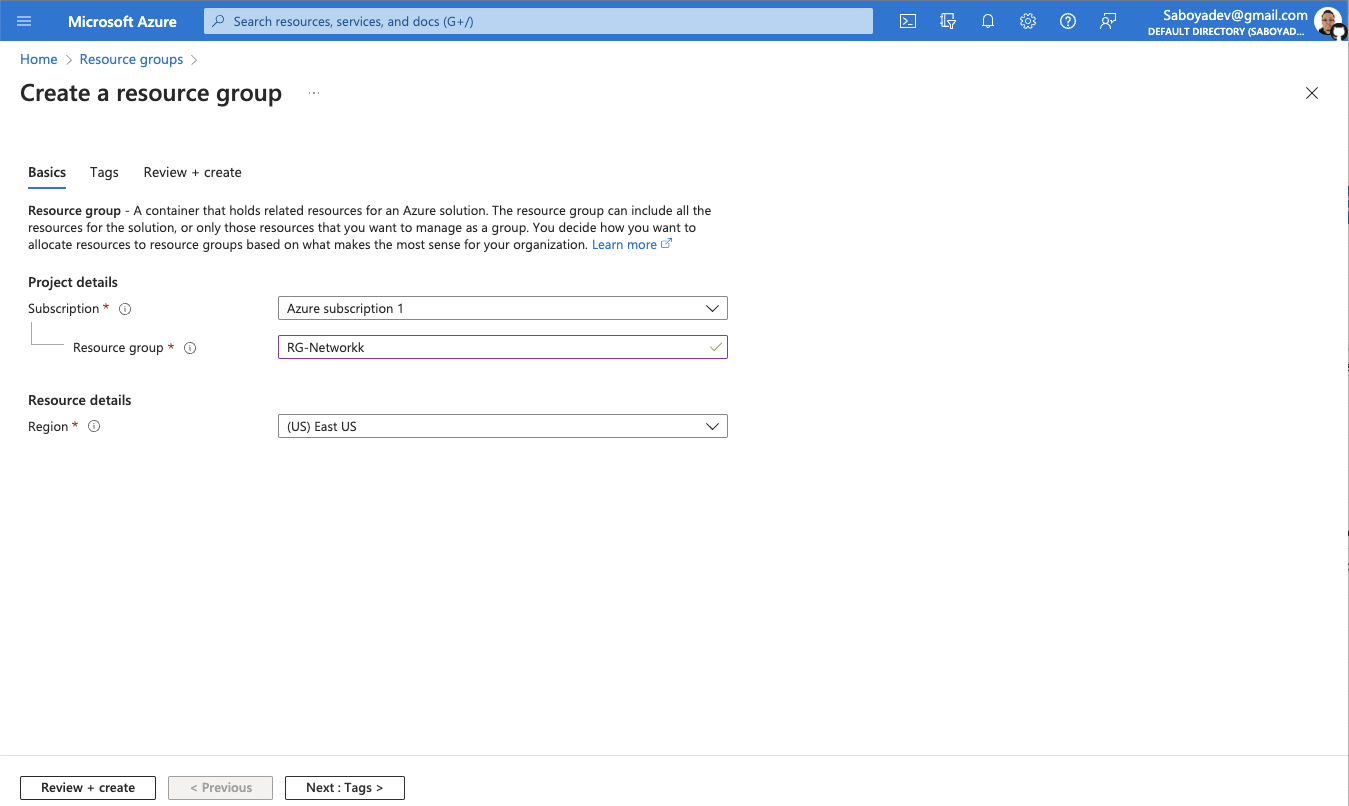
While creating the VM, select the previously created Resource Group and allow it to create a new Virtual Network (Vnet) and Subnet. Make sure to use the password option under the Administrator Account section (not seen in image):
***(You can also create your own custom Virtual Network)
While creating the VM, select the previously created Resource Group and Virtual Network (Vnet) and Subnet. Make sure to use the password option under the Administrator Account section (not seen in image)
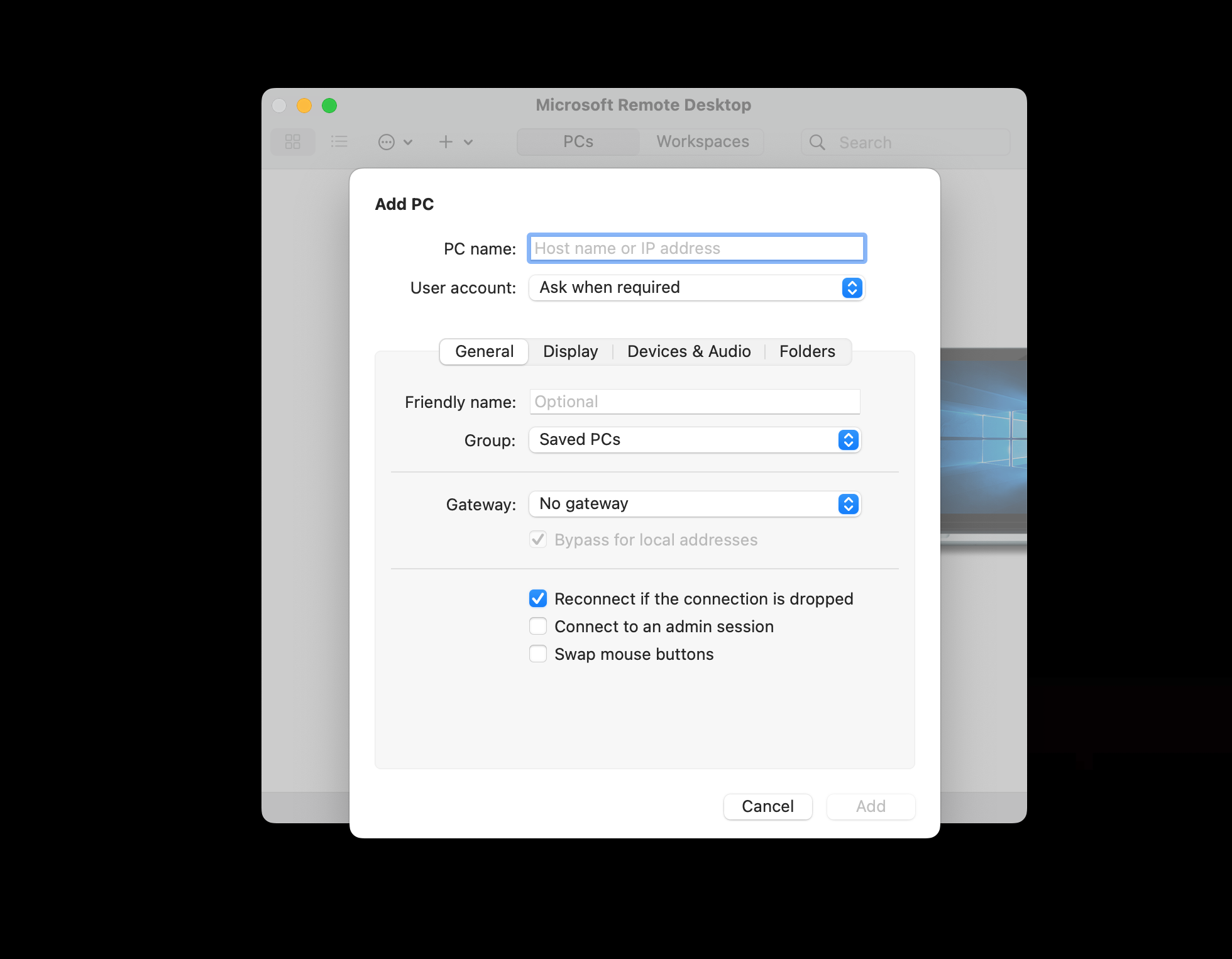
Remote into your Windows 10 Virtual Machine, install Wireshark, open it and filter for ICMP traffic only. If you are using a Mac like me, you'll have to download Microsoft Remote Desktop from the app store or install the cask via Homebrew:
Retrieve the private IP address of the Ubuntu VM
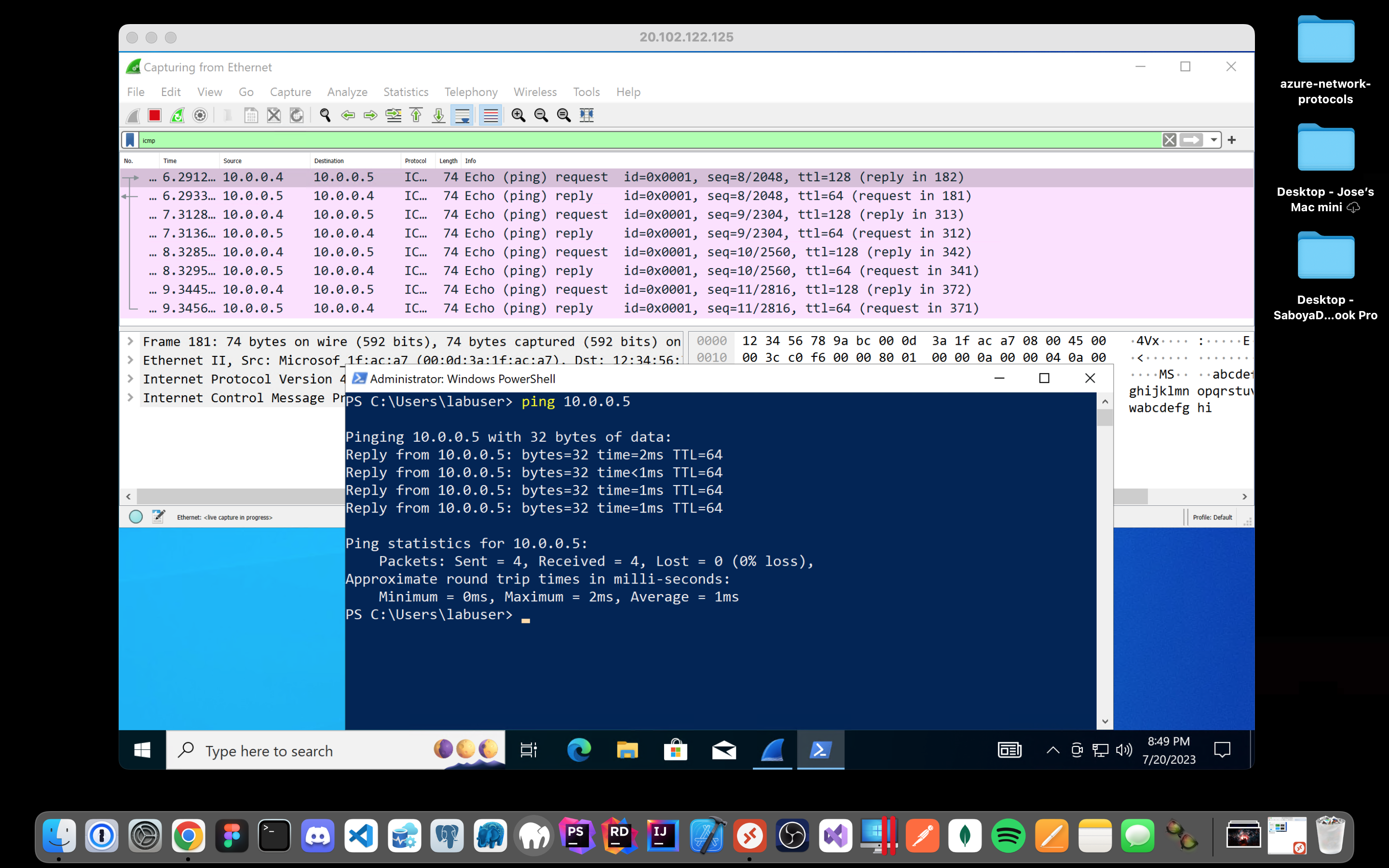
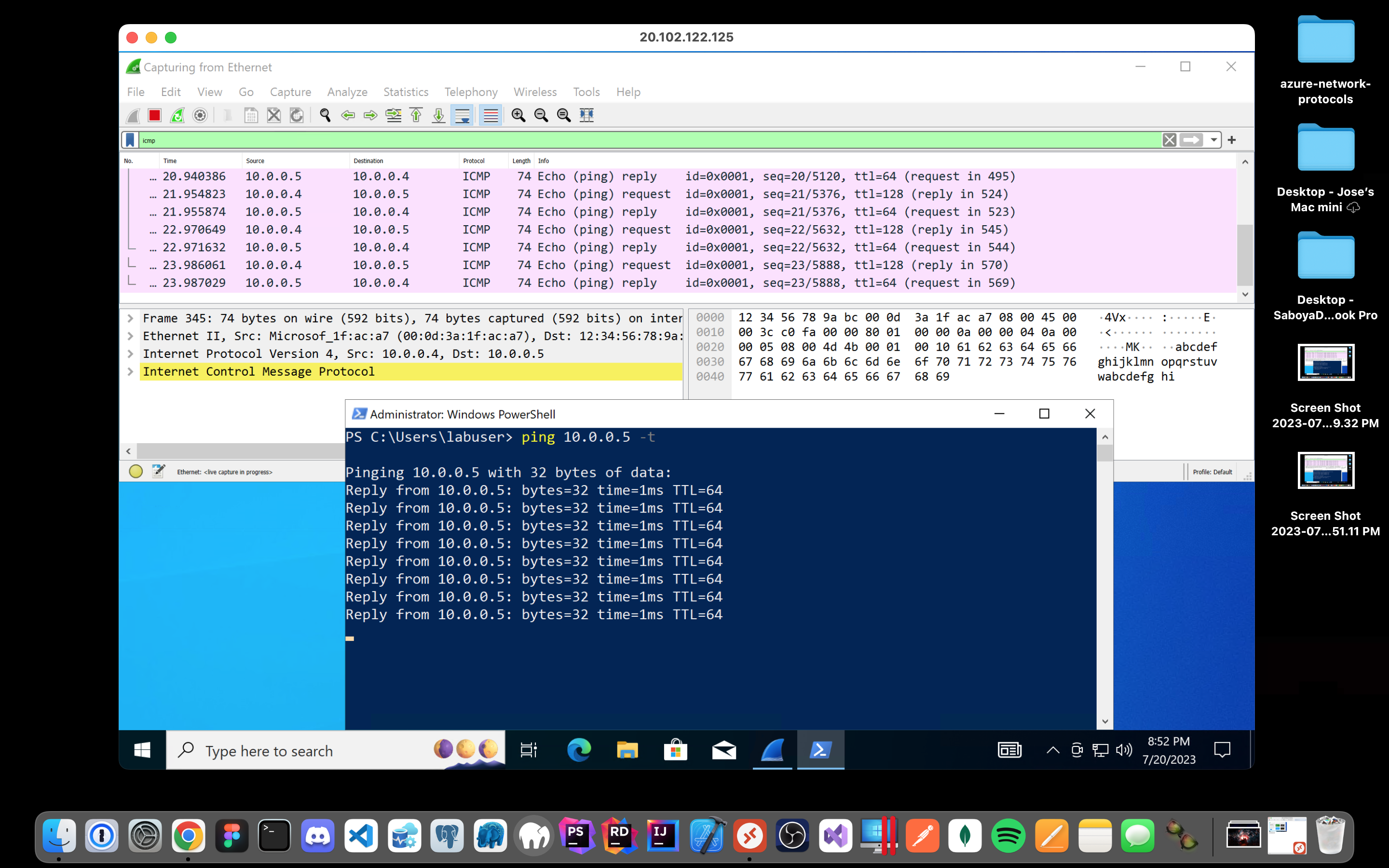
Attempt to ping it from within the Windows 10 VM. Observe ping requests and replies within Wireshark:
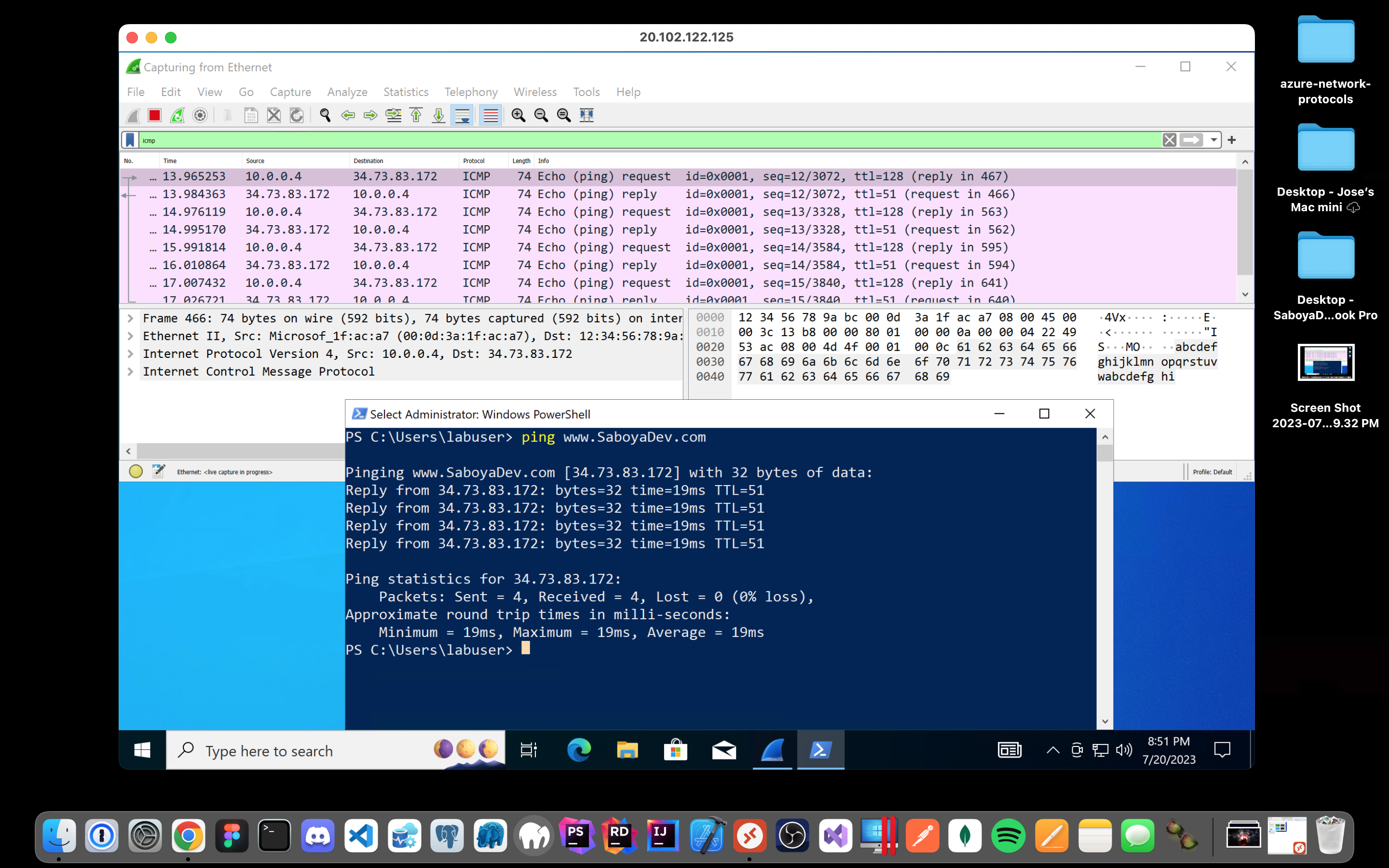
Attempt to ping a public website such as www.SaboyaDev.com and observe the traffic in Wireshark:
Initiate a perpetual/non-stop ping from your Windows 10 VM to your Ubuntu VM:
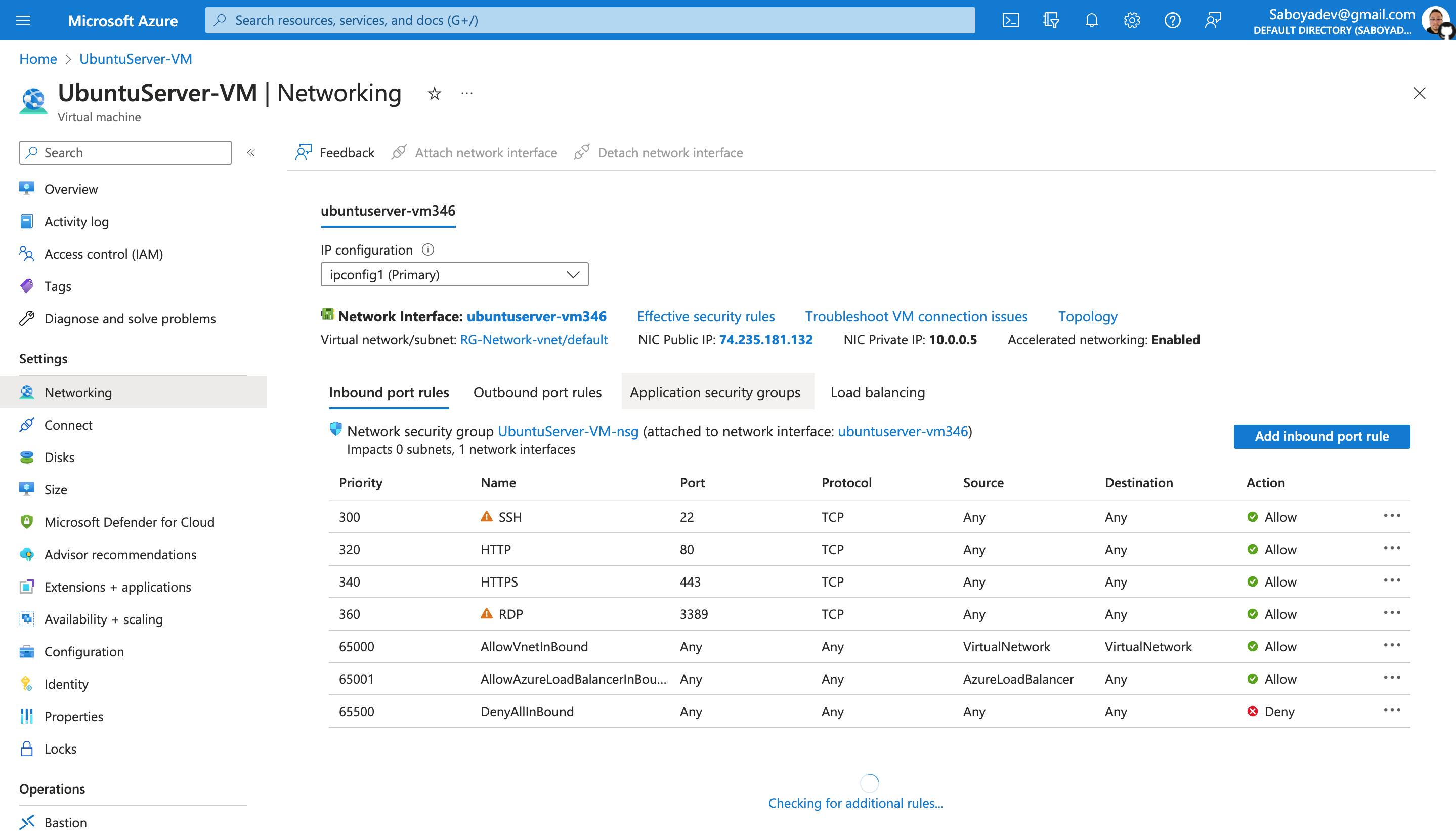
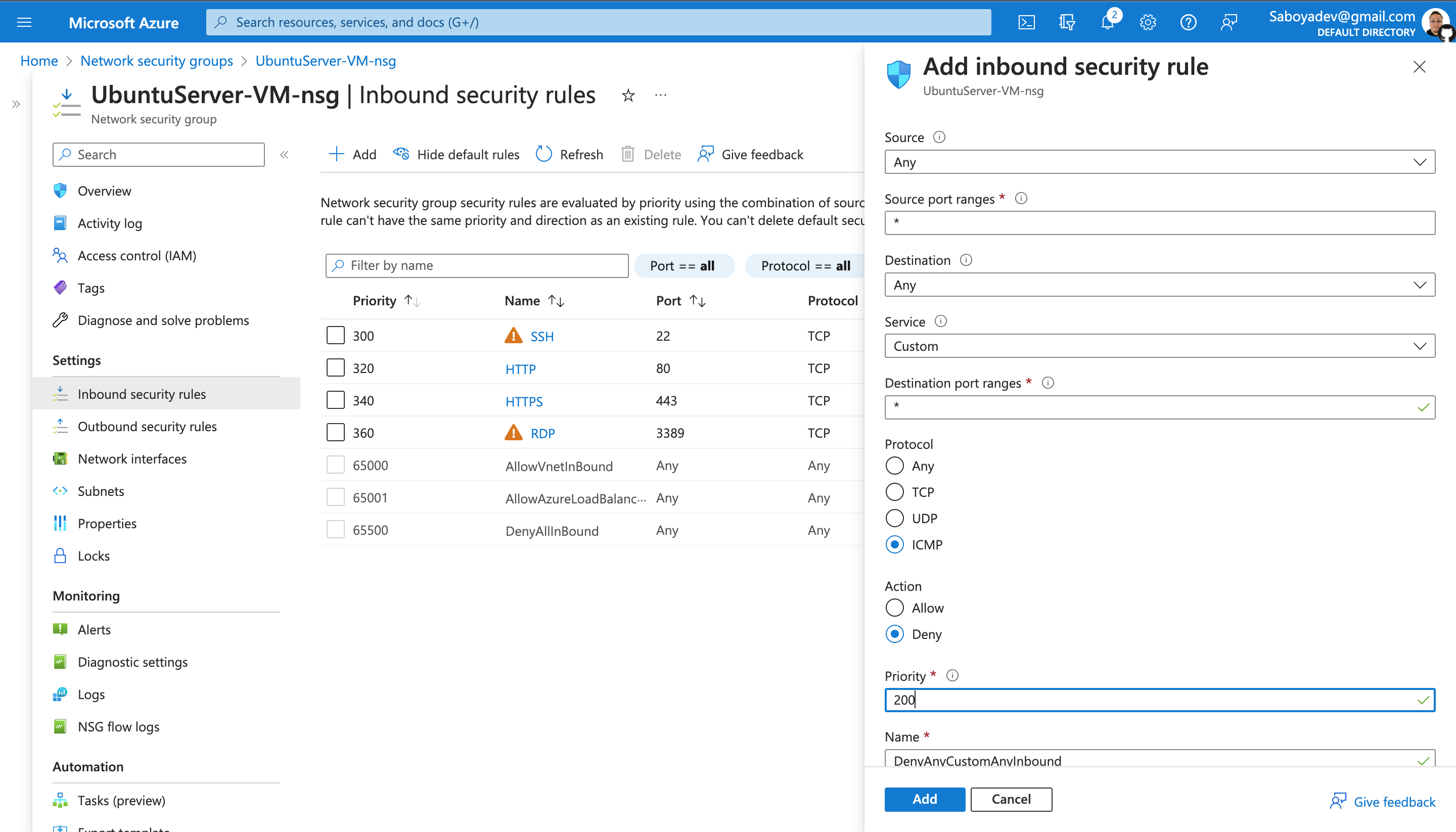
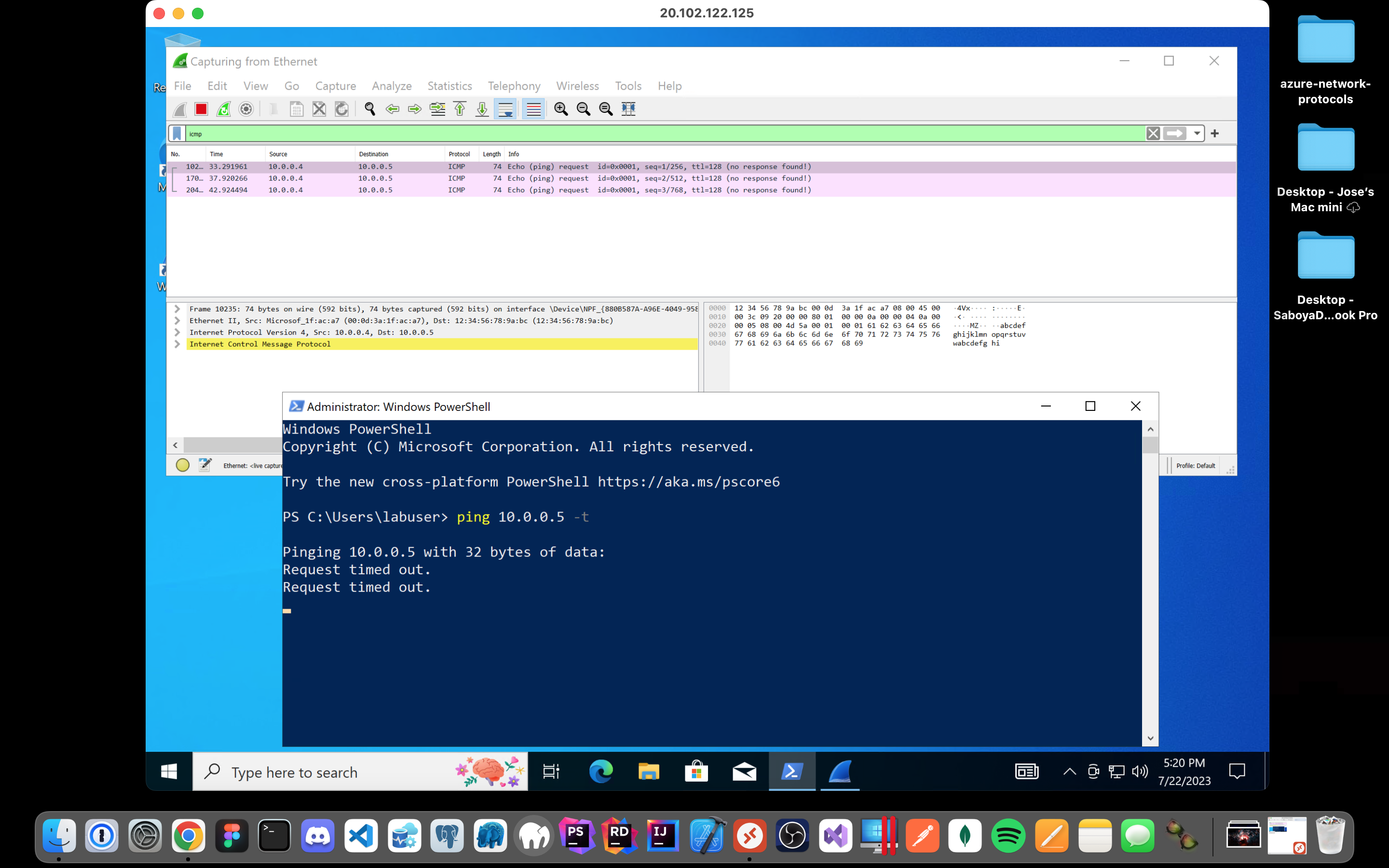
Open the Network Security Group your Ubuntu VM is using and disable incoming (inbound) ICMP traffic, while back in the Windows 10 VM, observe the ICMP traffic in Wireshark and the command line Ping activity. Afterwards re-enable ICMP traffic for the Network Security Group in your Ubuntu VM and back in the Windows 10 VM, observe the ICMP traffic in Wireshark and the command line ping activity (should start working again).Finally, stop the ping activity.
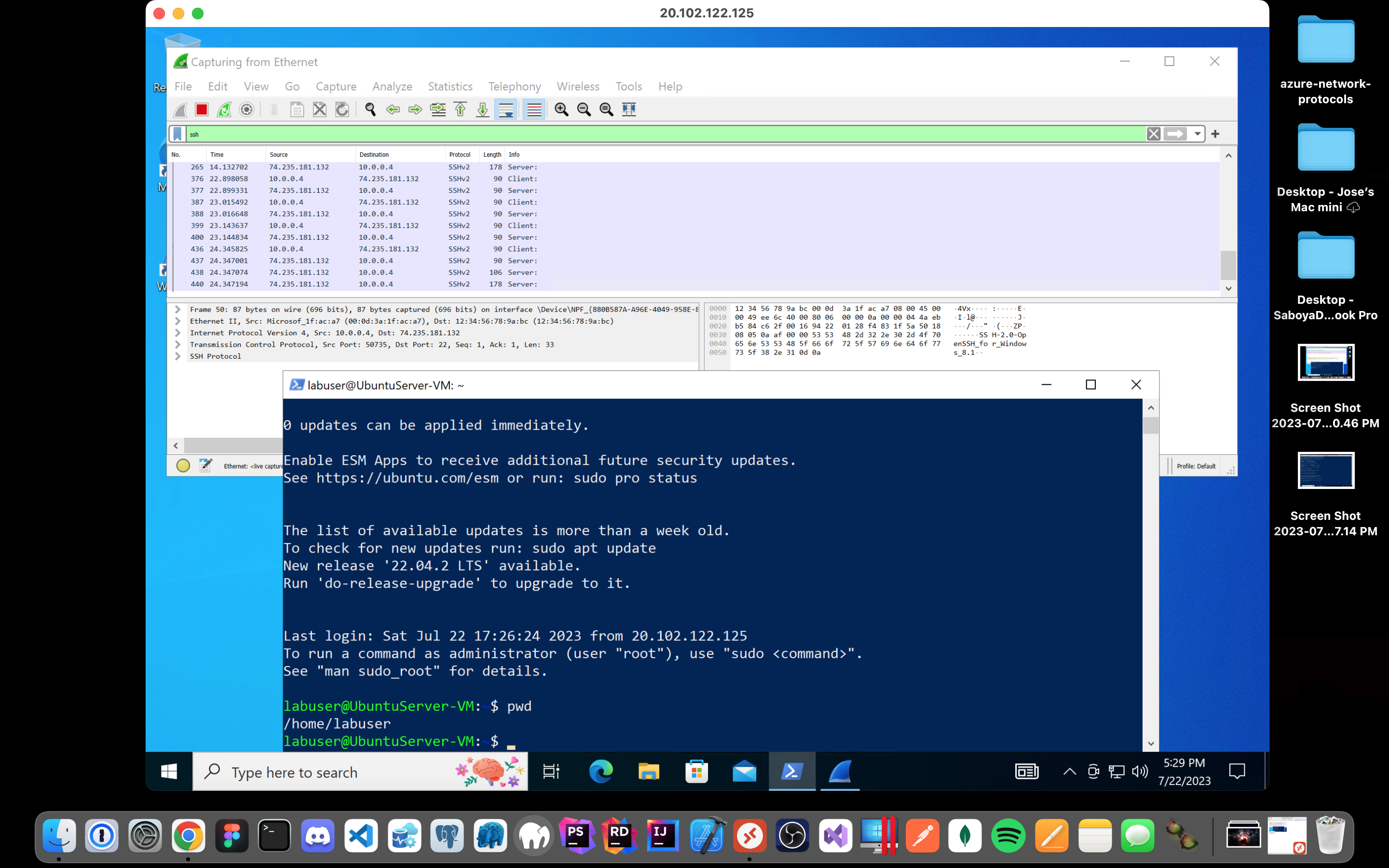
Back in Wireshark, filter for SSH traffic only and from your Windows 10 VM, “SSH into” your Ubuntu virtual machine (via its private IP address). Type commands (ls, pwd, etc) into the linux SSH connection and observe SSH traffic spam in Wireshark.
Exit the SSH connection by typing ‘exit’ and pressing [return]:
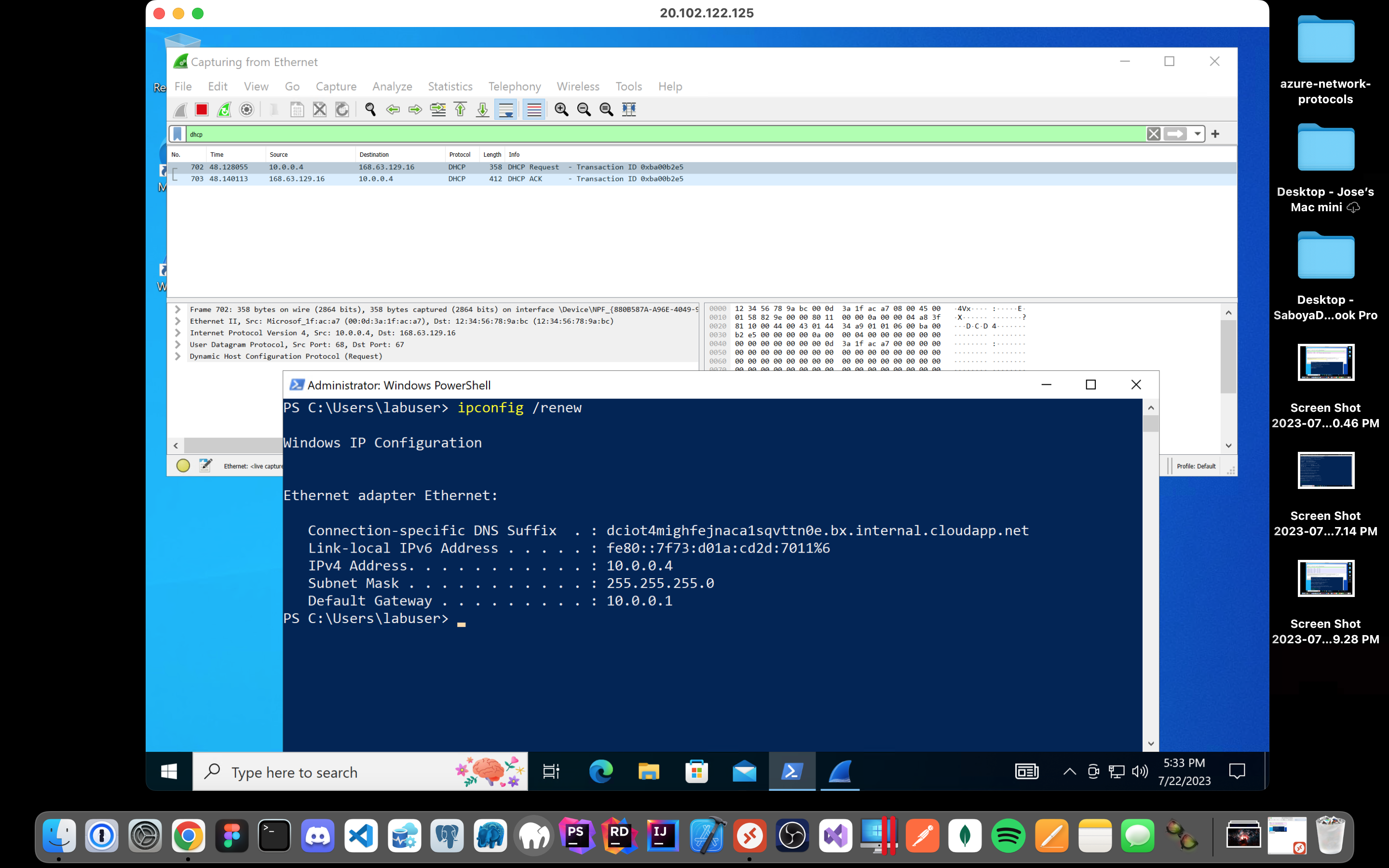
Back in Wireshark, filter for DHCP traffic only. From your Windows 10 VM, attempt to issue your VM a new IP address from the command line (ipconfig /renew)
Observe the DHCP traffic appearing in Wireshark:
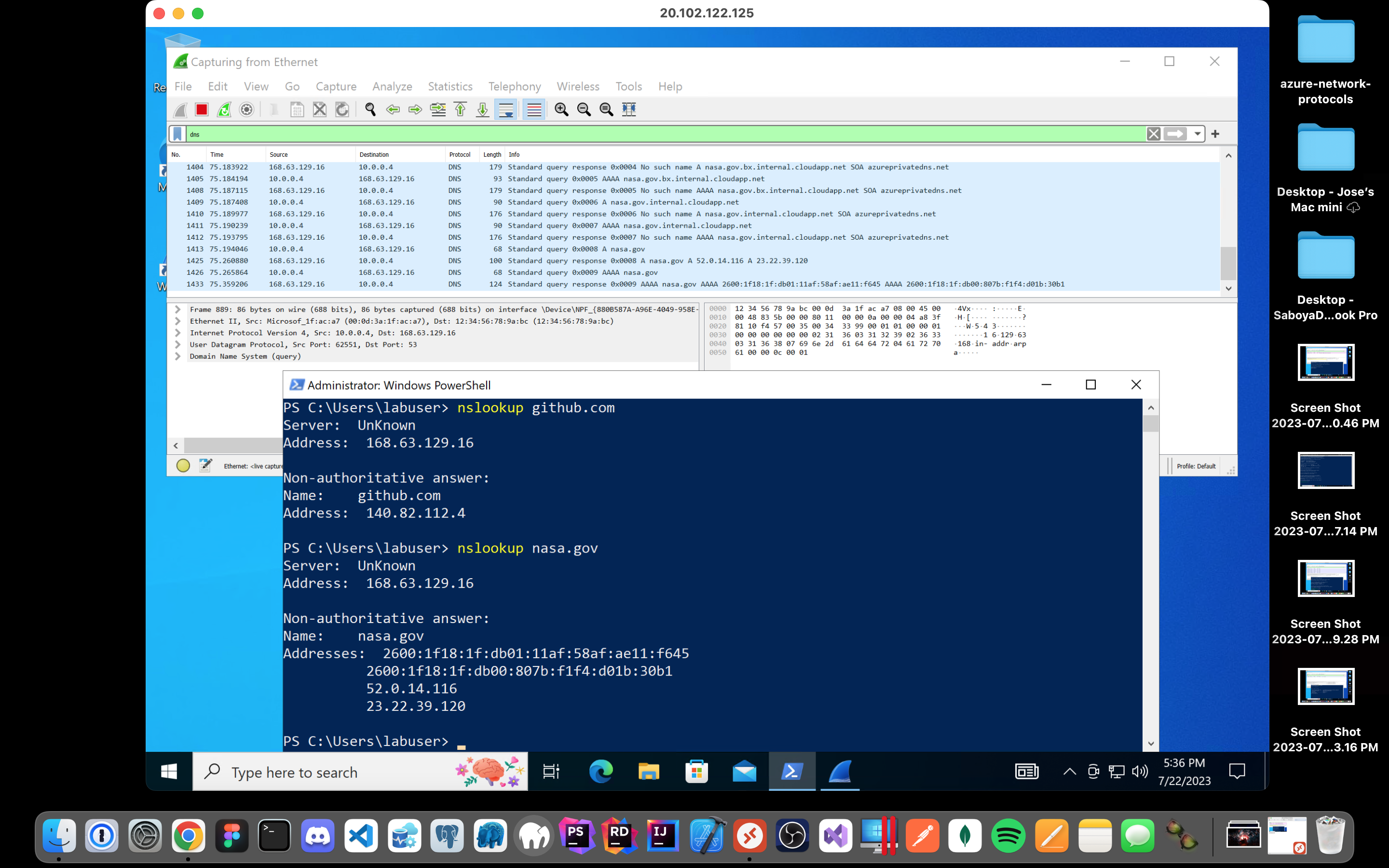
Back in Wireshark, filter for DNS traffic only.
From your Windows 10 VM within a command line, use nslookup to see what Github and Nasa's IP addresses are and observe the DNS traffic being shown in Wireshark:
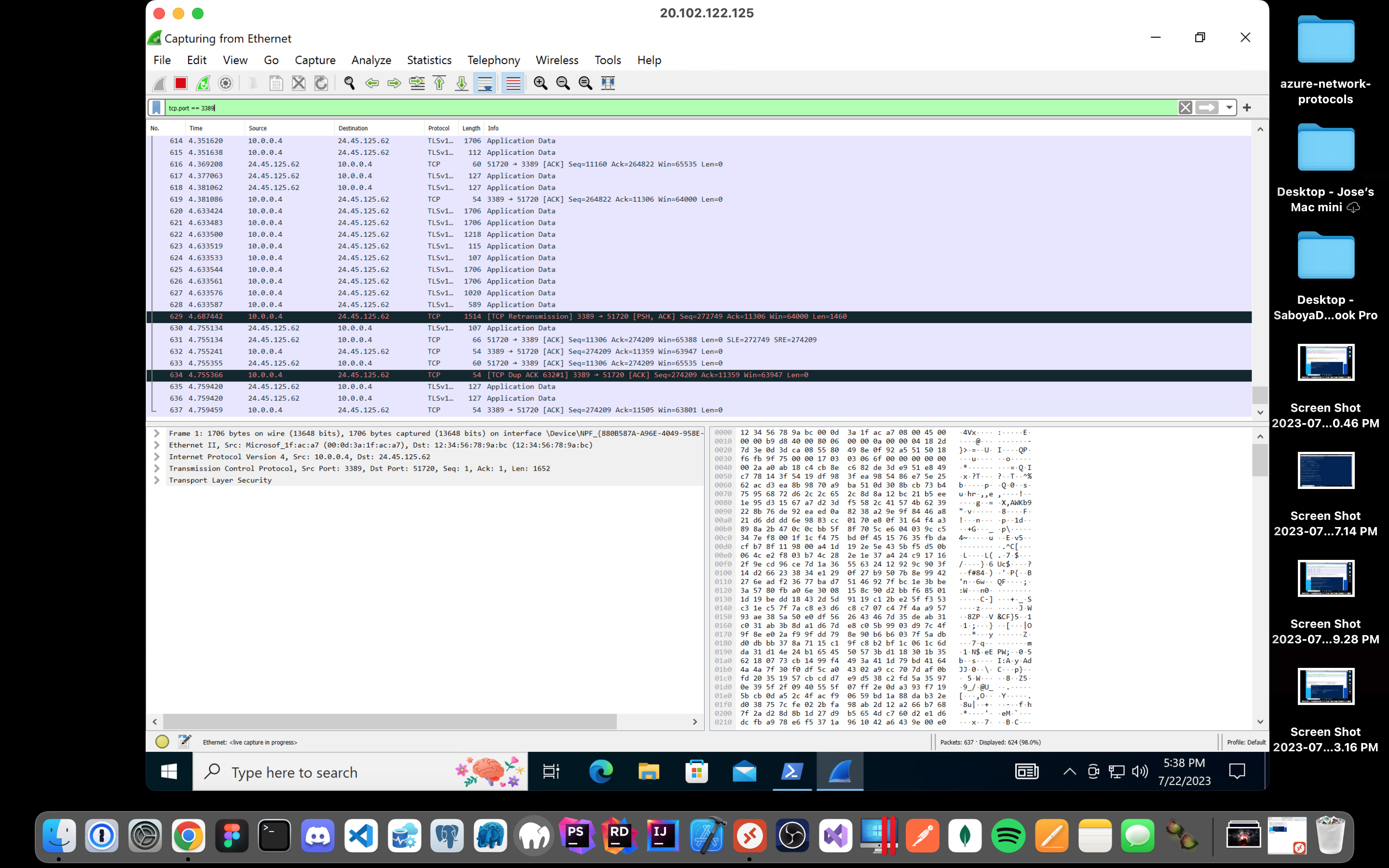
Back in Wireshark, filter for RDP traffic only (tcp.port == 3389).
Observe the immediate non-stop spam of traffic? Why is it non-stop spamming vs only showing traffic when a command is inputted?
The answer is because the RDP (protocol) is constantly showing you a live stream from one computer to another, therefor traffic is always being transmitted:
This tutorial intention is to help people learn a little bit about network security protocols and observe traffic between virtual machines. I ran this on a my Mac Mini, this can be easily done on a PC without having to download a remote desktop app since Windows provides that with it's software.DON'T FORGET TO CLEAN UP YOUR AZURE ENVIRONMENT so that you don't incur unnecessary charges.
Close your Remote Desktop connection, delete the Resource Group(s) created at the beginning of this tutorial, and verify Resource Group deletion.