A GitHub Action that analyses your web application for security and availability issues. When you add this to GitHub Actions we will analyze your web app everytime you deploy to a public endpoint and let you know if what you've just deployed is secure and meets your requirements. See below for what types of issues this action scans for.
name: Example Workflow Using SecureStack Web Vulnerability Exposure Action
on: push
jobs:
security:
runs-on: ubuntu-latest
steps:
- name: Web Vulnerability Exposure Analysis Step
id: exposure
uses: SecureStackCo/actions-exposure@v0.1.3
with:
securestack_api_key: ${{ secrets.SECURESTACK_API_KEY }}
securestack_app_id: ${{ secrets.SECURESTACK_APP_ID }}
severity: critical
flags: '--dom -r'
NOTE - to understand possible values for the action input flags, run the SecureStack cli locally:
$ bloodhound-cli code --help
- Log in to SecureStack with your GitHub credentials.
- Go to Settings in the lower left corner, and then select the 6th tab: API.
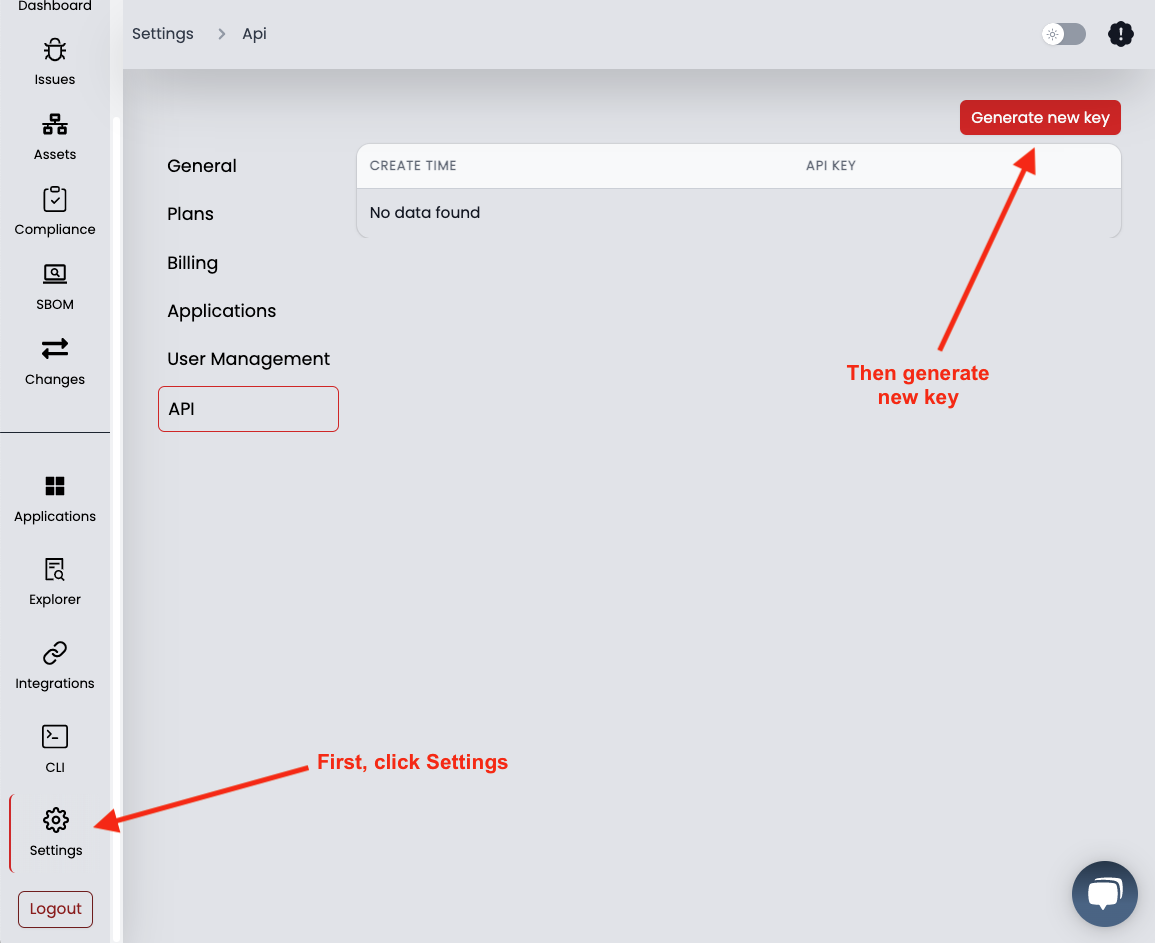
- Generate a new API key and copy the value.
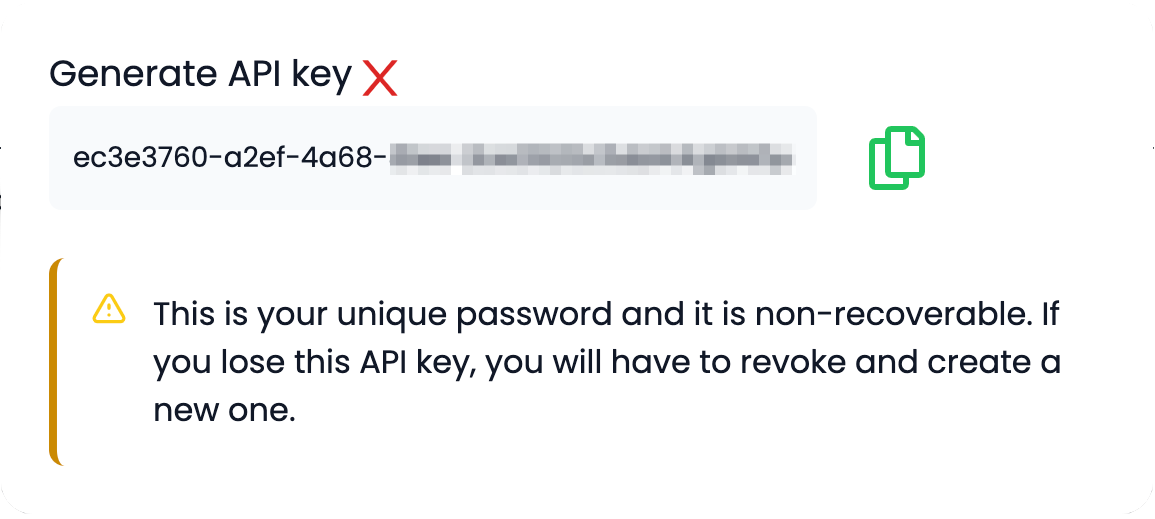
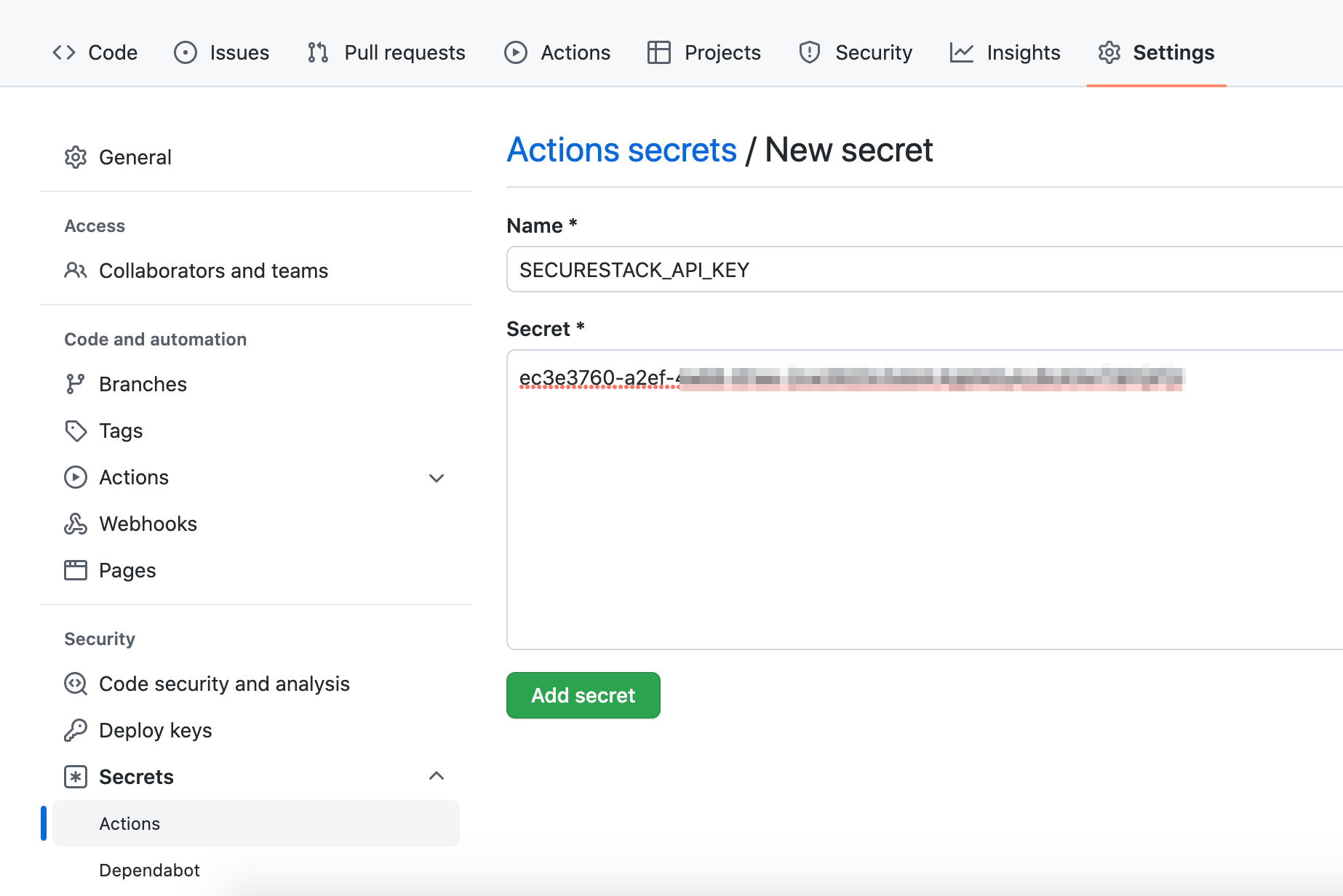
- Now back in GitHub, go to Settings for your GitHub repository and click on Secrets, and then Actions at the bottom left.
- Create a new secret named SECURESTACK_API_KEY and paste the value from step 2 into the field and click "Add secret".
- Log in to SecureStack.
- In the application drop down at the top left choose the application you want to use and click on "Copy Application ID"

- Create a new secret named SECURESTACK_APP_ID and paste the value from step 2 into the field and click "Add secret".
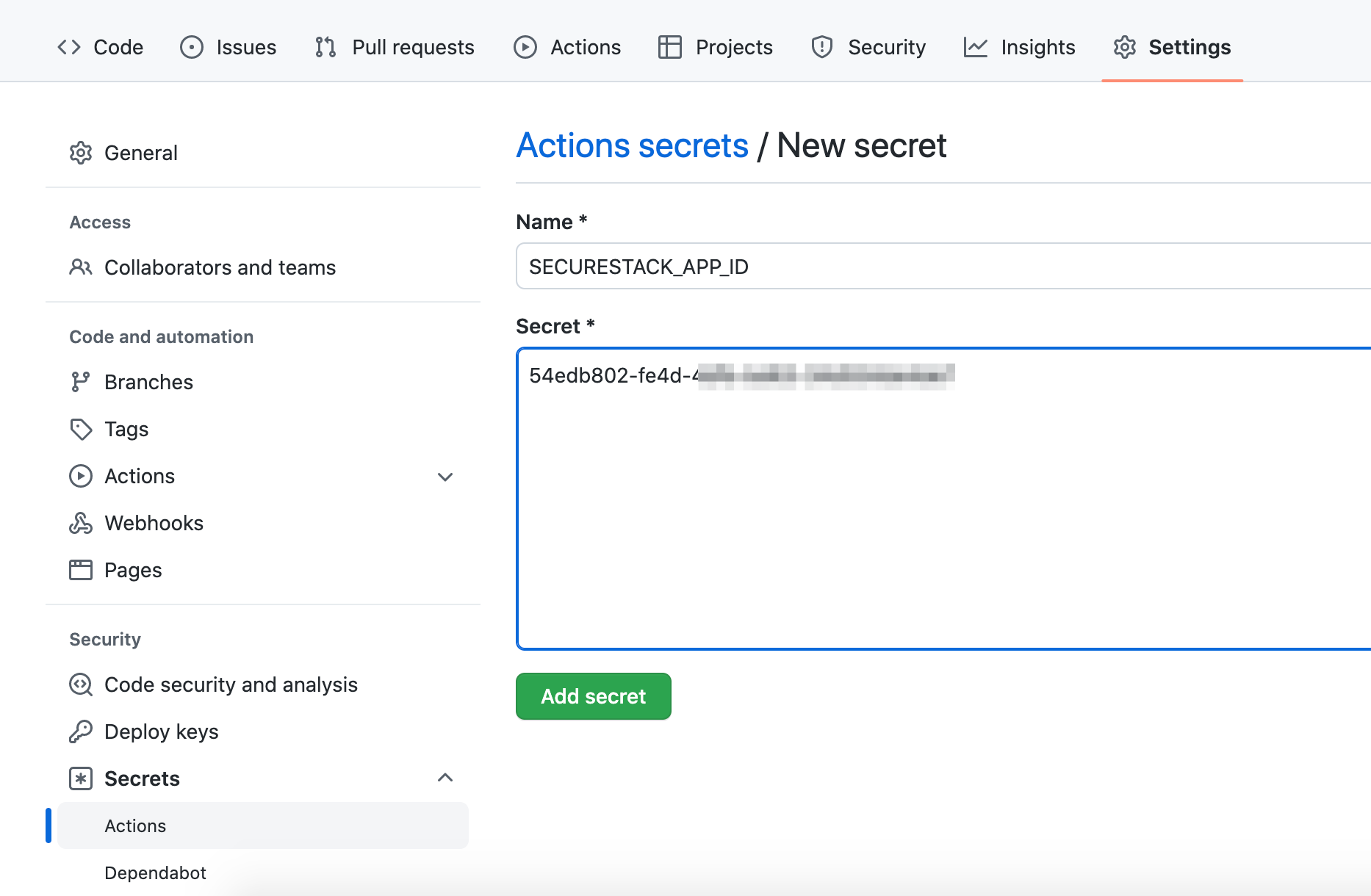
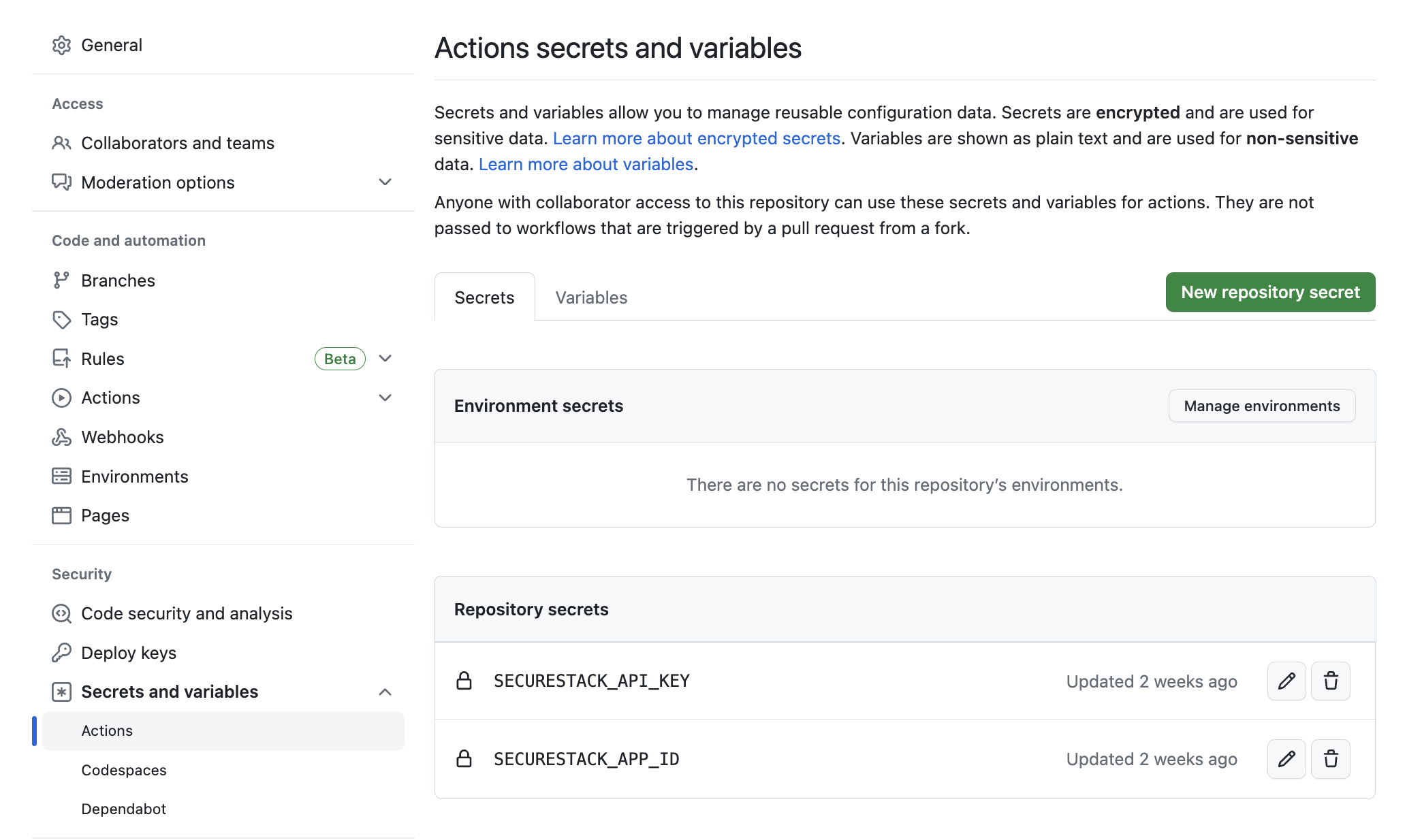
- When completed the two GitHub Secrets should look like this
- Scans web application for out of date and vulnerable application components
- Identifies whether basic security controls like WAF, firewalls, and security headers are being used
- Finds all public facing assets & helps you understand your application attack surface
- Identifies misconfigurations in existing WAF or CDN
- Identifies if app is using CSP or security headers and whether they're working
- Finds WAF bypass attacks for Akamai, Cloudflare & Imperva
-
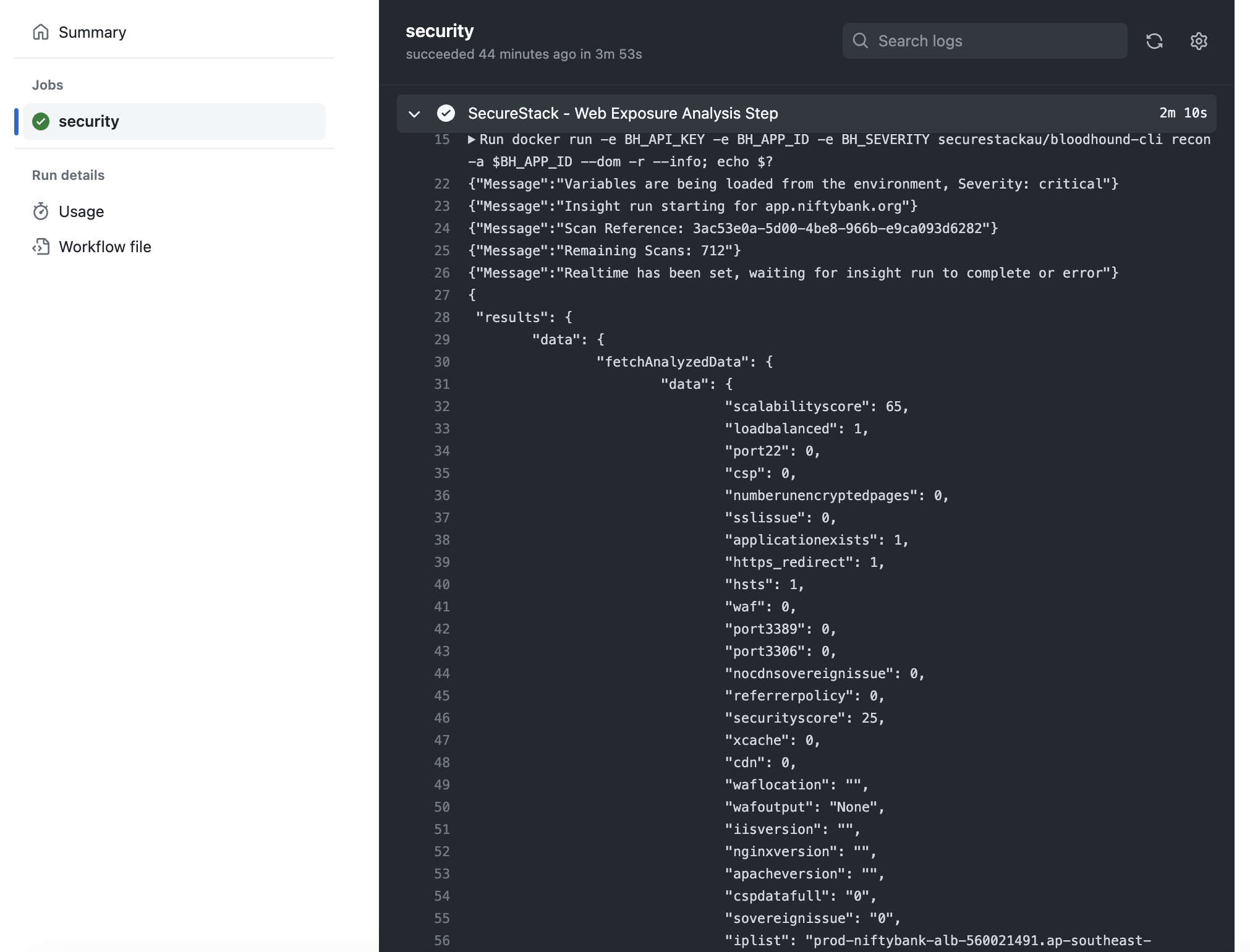
You can view the analysis output right in the GitHub Action workflow output
-
You can run a local secrets analysis with our bloodhound-cli :
bloodhound-cli recon -r -a <app_id> -
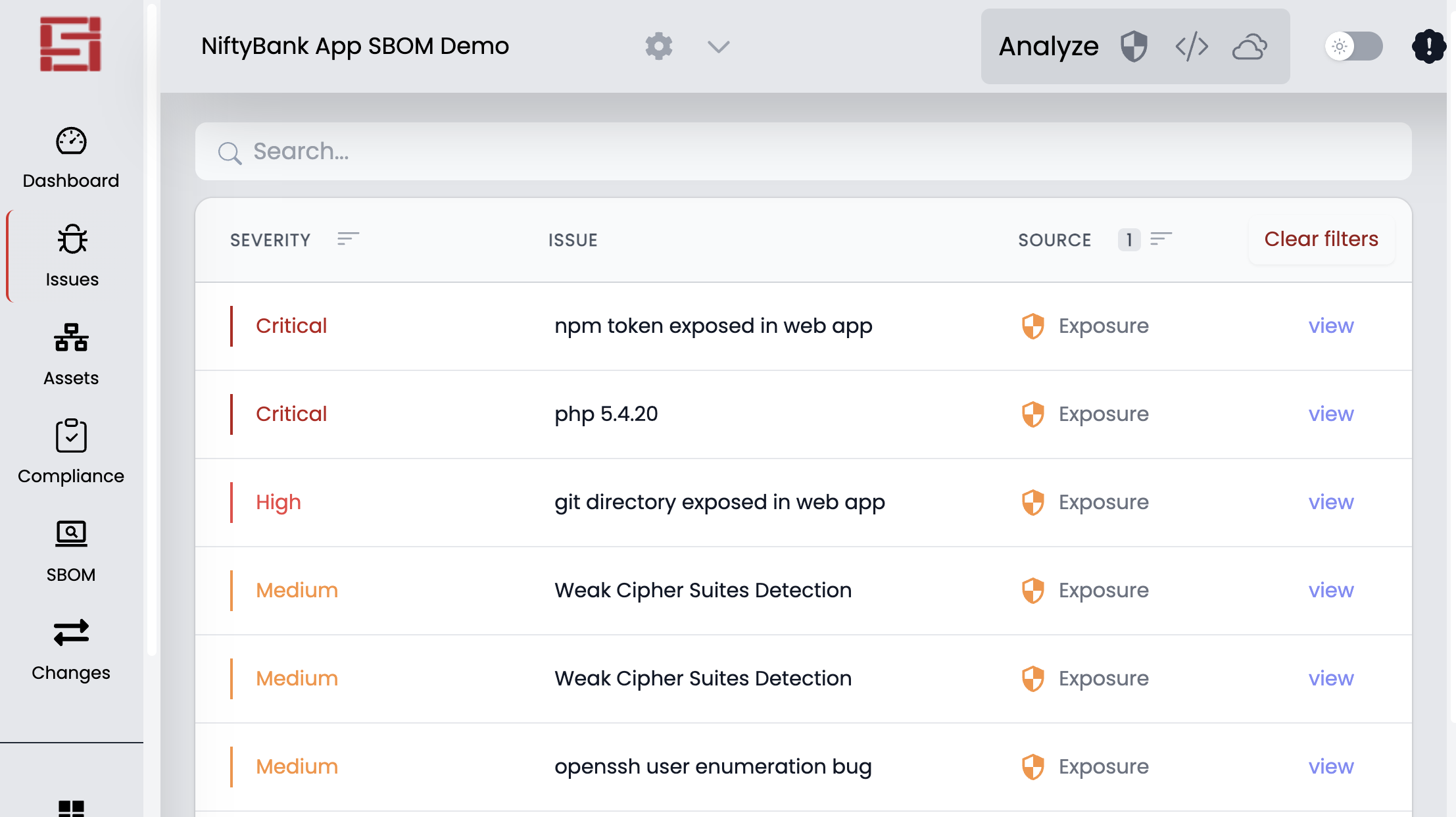
You can interact with the analysis output in the SecureStack SaaS
- SecureStack Software Composition Analysis (SCA) - Scan your application for vulnerable third-party and open source libraries.
- SecureStack Secret Scanning - Scan your application for embedded api keys, credentials and senstive data.
- SecureStack Web Vulnerability & Cloud Misconfiguration Analysis - Scan your running application url for cloud misconfigurations and web vulnerabilities.
- SecureStack Log4j Analysis - Scan your application for Log4j/Log4Shell vulnerabilities.
- SecureStack SBOM - Create a software bill of materials (SBOM) for your application.
- Or, our All-in-One GitHub Action - We've put all of our actions together into one "Action to rule them ALL"!
Made with 💜 by SecureStack